hidden node and exposed node problem
-
Exposed node problem

In wireless networks, theexposed node problem occurs when a node is prevented from sending packets to other nodes because of a neighboring transmitter. Consider an example of 4 nodes labeled R1, S1, S2, and R2, where the two receivers (R1, R2) are out of range of each other, yet the two transmitters (S1, S2) in the middle are in range of each other. Here, if a transmission between S1 and R1 is taking place, node S2 is prevented from transmitting to R2 as it concludes after carrier sense that it will interfere with the transmission by its neighbor S1. However note that R2 could still receive the transmission of S2 without interference because it is out of range of S1.[1]
IEEE 802.11 RTS/CTS mechanism helps to solve this problem only if the nodes are synchronized and packet sizes and data rates are the same for both the transmitting nodes. When a node hears an RTS from a neighboring node, but not the corresponding CTS, that node can deduce that it is an exposed node and is permitted to transmit to other neighboring nodes.[1]
If the nodes are not synchronised (or if the packet sizes are different or the data rates are different) the problem may occur that the sender will not hear the CTS or the ACK during the transmission of data of the second sender.
暴露的節點問題

在無線網絡中,當由於鄰近的發射機阻止節點發送分組到其他節點時,出現暴露的節點問題
IEEE 802.11 RTS / CTS機制只有在節點同步並且發送節點的數據包大小和數據速率相同時才有助於解決此問題。當節點從相鄰節點聽到RTS而不是相應的CTS時,該節點可以推斷出它是一個暴露的節點,並被允許傳送到其他相鄰節點。[1]
如果節點不同步(或者如果分組大小不同或數據速率不同),則可能會發生發送方在傳送第二個發送者的數據期間不會聽到CTS或ACK的問題。
-
Hidden node problem
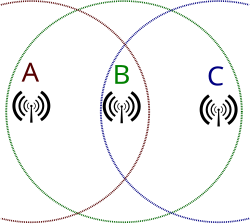 Station A can communicate with Station B. Station C can also communicate with Station B. However, Stations A and C cannot communicate with each other since they cannot sense each other on the network, because they are out of range of each other.
Station A can communicate with Station B. Station C can also communicate with Station B. However, Stations A and C cannot communicate with each other since they cannot sense each other on the network, because they are out of range of each other.
In wireless networking, the hidden node problem or hidden terminal problem occurs when a node is visible from a wireless access point (AP), but not from other nodes communicating with that AP.[1] This leads to difficulties in media access control sublayer.
Contents
[hide]- 1Background
- 2Solutions
- 2.1Increasing Transmitting Power From the Nodes
- 2.2Omnidirectional antennas
- 2.3Removing obstacles
- 2.4Moving the node
- 2.5Protocol enhancement software
- 3See also
- 4References
- 5External links
Background[edit]
Hidden nodes in a wireless network are nodes that are out of range of other nodes or a collection of nodes. Take a physical star topology with an access point with many nodes surrounding it in a circular fashion: Each node is within communication range of the AP, but the nodes cannot communicate with each other, as they do not have a physical connection to each other. In a wireless network, it is likely that the node at the far edge of the access point‘s range, which is known as A, can see the access point, but it is unlikely that the same node can see a node on the opposite end of the access point‘s range, C. These nodes are known as hidden. The problem is when nodes A and C start to send packetssimultaneously to the access point B. Because the nodes A and C are out of range of each other and so cannot detect a collision while transmitting, Carrier sense multiple access with collision detection (CSMA/CD) does not work, and collisions occur, which then corrupt the data received by the access point. To overcome the hidden node problem, RTS/CTS handshaking (IEEE 802.11 RTS/CTS) is implemented in conjunction with the Carrier sense multiple access with collision avoidance (CSMA/CA) scheme. The same problem exists in a MANET.
The hidden node problem can be observed easily in widespread (>50m radius) WLAN setups with many nodes that use directional antennas and have high upload. This is why IEEE 802.11 is suited for bridging the last mile for broadband access only to a very limited extent. Newer standards such as WiMAX assign time slots to individual stations, thus preventing multiple nodes from sending simultaneously and ensuring fairness even in over-subscription scenarios.
IEEE 802.11 uses 802.11 RTS/CTS acknowledgment and handshake packets to partly overcome the hidden node problem. RTS/CTS is not a complete solution and may decrease throughput even further, but adaptive acknowledgments from the base station can help too.
The comparison with hidden stations shows that RTS/CTS packages in each traffic class are profitable (even with short audio frames, which cause a high overhead on RTS/CTS frames).[2]
In the experimental environment following traffic classes are included: data (not time critical), data (time critical), video, audio. Examples for notations: (0|0|0|2) means 2 audio stations; (1|1|2|0) means 1 data station (not time critical), 1 data station (time critical), 2 video stations.
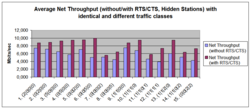 Benchmarks: Net Throughput with/without RTS/CTS (Pommer, p.179)
Benchmarks: Net Throughput with/without RTS/CTS (Pommer, p.179)
The other methods that can be employed to solve hidden node problem are :
- Increase Transmitting Power From the Nodes
- Use omnidirectional antennas
- Remove obstacles
- Move the node
- Use protocol enhancement software
- Use antenna diversity
Solutions[edit]
Increasing Transmitting Power From the Nodes[edit]
Increasing the transmission power of the nodes can solve the hidden node problem by allowing the cell around each node to increase in size, encompassing all of the other nodes. This configuration enables the non-hidden nodes to detect, or hear, the hidden node. If the non-hidden nodes can hear the hidden node, the hidden node is no longer hidden. Because wireless LANs use the CSMA/CA protocol, nodes will wait their turn before communicating with the access point.
This solution only works if one increases the transmission power on nodes that are hidden. In the typical case of a WiFi network, increasing transmission power on the access point only will not solve the problem because typically the hidden nodes are the clients (e.g. laptops, mobile devices), not the access point itself, and the clients will still not be able to hear each other. Increasing transmission power on the access point is actually likely to make the problem worse, because it will put new clients in range of the access point and thus add new nodes to the network that are hidden from other clients.
Omnidirectional antennas[edit]
Since nodes using directional antennas are nearly invisible to nodes that are not positioned in the direction the antenna is aimed at, directional antennas should be used only for very small networks (e.g., dedicated point-to-point connections). Use omnidirectional antennas for widespread networks consisting of more than two nodes.
Removing obstacles[edit]
Increasing the power on mobile nodes may not work if, for example, the reason one node is hidden is that there is a concrete or steel wall preventing communication with other nodes. It is doubtful that one would be able to remove such an obstacle, but removal of the obstacle is another method of remedy for the hidden node problem. Keep these types of obstacles in mind when performing a site survey.
Moving the node[edit]
Another method of solving the hidden node problem is moving the nodes so that they can all hear each other. If it is found that the hidden node problem is the result of a user moving his computer to an area that is hidden from the other wireless nodes, it may be necessary to have that user move again. The alternative to forcing users to move is extending the wireless LAN to add proper coverage to the hidden area, perhaps using additional access points.
Protocol enhancement software[edit]
There are several software implementations of additional protocols that essentially implement a polling or token passing strategy. Then, a master (typically the access point) dynamically polls clients for data. Clients are not allowed to send data without the master‘s invitation. This eliminates the hidden node problem at the cost of increased latency and less maximum throughput.
隱藏節點問題
 站A可以與站B通信。站C也可以與站B進行通信。但是,由於它們彼此超出範圍,因此站A和C不能彼此通信,因為它們不能在網絡上彼此感知。
站A可以與站B通信。站C也可以與站B進行通信。但是,由於它們彼此超出範圍,因此站A和C不能彼此通信,因為它們不能在網絡上彼此感知。
在無線網絡中,當節點從無線接入點(AP)可見時,而不是與該AP通信的其他節點發生時,會發生隱藏節點問題或隱藏終端問題。[1]這導致媒體訪問控制子層的困難。
內容
[ 隱藏 ]- 1背景
- 2解決方案
- 2.1從節點增加發射功率
- 2.2全向天線
- 2.3拆除障礙物
- 2.4移動節點
- 2.5協議增強軟件
- 3另見
- 4參考文獻
- 5外部鏈接
背景[ 編輯]
無線網絡中的隱藏節點是超出其他節點或節點集合的節點。以具有多個節點的接入點進行物理星形拓撲結構,循環方式:每個節點位於AP的通信範圍內,但節點之間無法進行通信,因為它們之間沒有物理連接。在無線網絡中,接入點範圍的遠端(被稱為A)的節點很可能能夠看到接入點,但是同一節點不太可能看到相對端的節點接入點的範圍,C。這些節點被稱為隱藏。問題是當節點A和C開始同時向接入點B發送數據包時。因為節點A和C彼此超出範圍,因此在發送時不能檢測到沖突,具有沖突檢測(CSMA / CD)的載波偵聽多路訪問不起作用,並且發生沖突,從而使由切入點。為了克服隱藏節點問題,RTS / CTS握手(IEEE 802.11 RTS / CTS)與具有沖突避免(CSMA / CA)方案的載波偵聽多路訪問一起實現。
在具有許多使用定向天線並具有高上傳的節點的廣泛(> 50m半徑)WLAN設置中,可以容易地觀察到隱藏節點問題。這就是為什麽IEEE 802.11適用於僅在非常有限的範圍內橋接最後一公裏寬帶接入的原因。較新的標準如WiMAX將時隙分配給各個站,從而防止多個節點同時發送,並確保即使在超訂購情況下也能公平。
IEEE 802.11使用802.11 RTS / CTS確認和握手包來部分克服隱藏節點問題。RTS / CTS不是一個完整的解決方案,並且可以進一步降低吞吐量,但來自基站的自適應確認也可以幫助。
與隱藏站的比較顯示,每個流量類別中的RTS / CTS軟件包都是有利可圖的(即使是短幀音頻,導致RTS / CTS幀的高開銷)。[2]
在包括流量類別在內的實驗環境中:數據(不是時間關鍵),數據(時間關鍵),視頻,音頻。符號示例:(0 | 0 | 0 | 2)表示2個音頻電臺; (1 | 1 | 2 | 0)表示1個數據站(不是時間關鍵),1個數據站(時間關鍵),2個視頻站。
 基準:具有/不具有RTS / CTS的凈吞吐量(Pommer,p.179)
基準:具有/不具有RTS / CTS的凈吞吐量(Pommer,p.179)
可用於解決隱藏節點問題的其他方法有:
- 從節點增加發射功率
- 使用全向天線
- 去除障礙物
- 移動節點
- 使用協議增強軟件
- 使用天線多樣性
解決方案[ 編輯]
從節點增加發射功率[ 編輯]
增加節點的傳輸功率可以通過允許每個節點周圍的小區來增加大小,從而解決隱藏節點的問題,包括所有其他節點。該配置使得非隱藏節點能夠檢測或聽到隱藏節點。如果非隱藏節點可以聽到隱藏節點,則隱藏節點不再隱藏。由於無線局域網使用CSMA / CA協議,所以在與接入點進行通信之前,節點將等待轉機。
該解決方案僅在增加隱藏節點的傳輸功率時有效。在典型情況下的WiFi網絡,在增加發射功率接入點只將不會因為通常隱藏節點是客戶端(例如筆記本電腦,移動設備)解決問題,而不是接入點本身和客戶意願依然不能夠聽到對方 增加接入點的傳輸功率實際上可能會使問題變得更糟,因為它會將新客戶端置於接入點的範圍內,從而將新節點添加到隱藏於其他客戶端的網絡。
全向天線[ 編輯]
由於使用定向天線的節點對於天線未定位的節點幾乎不可見,所以定向天線只能用於非常小的網絡(例如,專用點對點連接)。對於由兩個以上節點組成的廣泛網絡,使用全向天線。
刪除障礙[ 編輯]
如果一個節點隱藏的原因是有一個混凝土或鋼制墻壁阻止與其他節點的通信,則增加移動節點的功率可能不起作用。令人懷疑的是,能夠消除這樣的障礙,但是去除障礙物是對隱藏節點問題的另一種補救方法。在進行現場調查時,請牢記這些障礙。
移動節點[ 編輯]
解決隱藏節點問題的另一種方法是移動節點,使它們都可以相互聽到。如果發現隱藏節點問題是用戶將其計算機移動到與其他無線節點隱藏的區域的結果,則可能需要使該用戶再次移動。迫使用戶移動的替代方法是擴展無線局域網,以便為隱藏區域添加適當的覆蓋範圍,也許使用其他接入點。
協議增強軟件[ 編輯]
附加協議的幾種軟件實現基本上實現輪詢或令牌傳遞策略。然後,主(通常是接入點)動態輪詢客戶端的數據。客戶不允許在沒有主人邀請的情況下發送數據。這消除了隱藏節點問題,代價是增加延遲和較小的最大吞吐量。
在以太網中,所有計算機都可以聽到互相發送的信息;發送方只需發送一個廣播表明他要發送消息即可。
而在無線網絡中,並不能覆蓋所有範圍,分區域傳播。
有三臺電腦,A、B、C
A的發送範圍覆蓋B但是無法覆蓋C,B的接收範圍同時覆蓋A、B
A、希望向B發送信息,這時A、B希望在發送信息的時沒有人在B接收範圍內發送信息,因為那樣會幹擾接受。就像在以太網中一樣,A發送了一個廣播,表明他要向B發送信息,但是在這時恰巧C也希望向B發送信息,由於 A的發送範圍覆蓋B但是無法覆蓋C,所以C誤以為沒有人會向B發送信息,A也誤以為所有人都聽到了他要發送信息,於是兩臺計算機同時開始發送,互相幹擾導致傳送失敗。
暴露站問題
C的發送範圍不能覆蓋B但是A的發送範圍覆蓋A和B,A發送了一個廣播,C誤以為他的發送會,於是幹擾成本,降低了網絡利用率
解決方案:
發送方首先發送RTS,這時所有聽到的計算機靜默一段時間等待CTS,接收方收到CTS後立即回復CTS,受到CTS的計算機立即安靜下來(不包括發送信息的計算機),而沒有受到CTS的計算機繼續發送信息
instance:

hidden node and exposed node problem
