Docker私有倉庫Registry認證搭建
前言:
首先,Docker Hub是一個很好的用於管理公共鏡像的地方,我們可以在上面找到想要的鏡像(Docker Hub的下載量已經達到數億次);而且我們也可以把自己的鏡像推送上去。但是,有的時候我們的使用場景需要擁有一個私有的鏡像倉庫用於管理自己的鏡像,這個時候我們就通過Registry來實現此目的。本文詳細介紹了本地鏡像倉庫Docker Registry及Auth Server認證搭建。
集群環境:
系統 | 主機名 | IP地址(Host-Only) | 描述 |
Centos7.2.1511 | controller | 192.168.200.9 | Docker、Registry、Auth-server |
Centos7.2.1511 | compute | 192.168.200.10 | Docker |
1.下載所需要的鏡像
# controller節點: docker pull registry docker pull cesanta/docker_auth docker pull sspaas.net/renyf/mongodb:3.2
2.安裝所需軟件
# controller節點: yum -y install epel-release yum -y install nginx ntp httpd-tools
3.修改hosts文件
cat >> /etc/hosts << EOF 192.168.200.9 controller registry.testcloud.com 192.168.200.10 compute EOF
3.生成自簽證書(私鑰文件及根證書文件)
# controller節點: mkdir -p /auth_server/ssl cd /auth_server/ssl openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout server.key -out server.pem -subj"/C=CN/ST=state/L=city/O=xxx/OU=registry.testcloud.com"
4.使用htpasswd生成賬戶信息(密碼隨意指定,我這裏為123456)
# controller節點: cd /auth_server htpasswd -Bc.passwd renyf
5.啟動mongodb數據庫
這裏采用容器做了mongodb數據庫,當然你也可以本地去搭建使用mongodb(此處省略)
# controller節點: docker run -d -p 27017:27017 -p 28017:28017 --name mongo -e MONGODB_PASS=a123456 sspaas.net/renyf/mongodb:3.2
6.進入mongodb創建我們所需要的數據庫,用戶及其權限
# controller節點:
docker exec -it mongo mongo admin -u admin -p a123456
# 創建數據庫
MongoDB Enterprise> use registry_auth
# 創建數據庫用戶及授權
MongoDB Enterprise> db.createUser({user: ‘renyf‘, pwd: ‘a666666‘, roles:[{role:‘dbOwner‘,db:‘registry_auth‘}]})7.現在我們把之前使用htpasswd創建的用戶信息寫到數據庫中(密碼為:123456)
# controller節點: cat /auth_server/.passwd
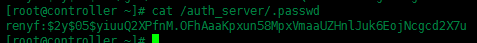
# controller節點:
# 在數據庫user表中創建用戶
MongoDB Enterprise > db.user.insert({username:‘renyf‘, password:‘$2y$05$yiuuQ2XPfnM.OFhAaaKpxun58MpxVmaaUZHnlJuk6EojNcgcd2X7u‘})
# 在數據庫acl表中設置用戶權限
MongoDB Enterprise> db.acl.insert({‘seq‘: 1, ‘match‘: {‘account‘: ‘/.+/‘, ‘name‘:‘${account}/*‘}, ‘actions‘: [‘*‘]})好的,到這裏我們就完成了對registry用戶及用戶權限的配置
8.編寫auth_server的config配置文件
# controller節點:
vim /auth_server/config/auth_config.yml
內容如下:
server: # Server settings.
# Address to listen on.
addr: ":5001"
# TLS certificate and key.
certificate: "/ssl/server.pem"
key: "/ssl/server.key"
token: # Settings for the tokens.
issuer: "Auth Service" # Must match issuer in the Registry config.
expiration: 900
# Static user map.
users:
"": {} # Allow anonymous (no "dockerlogin") access.
mongo_auth:
dial_info:
addrs: ["192.168.200.9:27017"]
timeout: "10s"
database: "registry_auth"
username: "renyf"
password: "a666666"
collection: "user"
acl_mongo:
dial_info:
addrs: ["192.168.200.9:27017"]
timeout: "10s"
database: "registry_auth"
username: "renyf"
password: "a666666"
collection: "acl"
cache_ttl: "1m"9.現在我們啟動auth_server
# controller節點: docker run -d -p 5001:5001 --restart=always --name docker_auth -v /auth_server/config:/config:ro -v /var/log/docker_auth:/logs -v /auth_server/ssl:/ssl cesanta/docker_auth /config/auth_config.yml
10.啟動registry
# controller節點: docker run -d -p 5000:5000 --restart=always --name registry -e REGISTRY_STORAGE_FILESYSTEM_ROOTDIRECTORY=/var/lib/registry -e REGISTRY_AUTH=token -e REGISTRY_AUTH_TOKEN_REALM=https://registry.testcloud.com:5001/auth -e REGISTRY_AUTH_TOKEN_SERVICE="Docker registry" -e REGISTRY_AUTH_TOKEN_ISSUER="Auth Service" -e REGISTRY_AUTH_TOKEN_ROOTCERTBUNDLE=/ssl/server.pem -v /auth_server/ssl:/ssl -v /root/docker_registry/data:/var/lib/registry registry
11.現在我們再給registry加上nginx代理
# controller節點:
# 編輯nginx配置文件
vim /etc/nginx/nginx.conf
# 內容如下:
# For moreinformation on configuration, see:
# * Official English Documentation:http://nginx.org/en/docs/
# * Official Russian Documentation:http://nginx.org/ru/docs/
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamicmodules. See /usr/share/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
log_format main ‘$remote_addr - $remote_user[$time_local] "$request" ‘
‘$status $body_bytes_sent"$http_referer" ‘
‘"$http_user_agent" "$http_x_forwarded_for"‘;
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the/etc/nginx/conf.d directory.
# Seehttp://nginx.org/en/docs/ngx_core_module.html#include
# for more information.
include /etc/nginx/conf.d/*.conf;
upstream docker-registry{
server 192.168.200.9:5000;
}
server {
listen 80;
listen 443;
server_name registry.testcloud.com;
root /usr/share/nginx/html;
ssl on;
ssl_certificate /auth_server/ssl/server.pem;
ssl_certificate_key /auth_server/ssl/server.key;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
client_max_body_size 0; # disable any limits to avoid HTTP 413 forlarge image uploads
chunked_transfer_encoding on;
add_header‘Docker-Distribution-Api-Version‘ ‘registry/2.0‘ always;
# Load configuration files for thedefault server block.
include /etc/nginx/default.d/*.conf;
location / {
proxy_pass http://docker-registry;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_headerX-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_headerX-Forwarded-Proto $scheme;
proxy_read_timeout 900;
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
}12.啟動nginx
# controller節點: systemctl start nginx
好了,這裏我們服務已經基本搭建完成了。
客戶端
因為是自簽名證書,所以我們要在docker的配置裏面添加信任
# compute節點: vim /lib/systemd/system/docker.service # 添加內容如下: --insecure-registry registry.testcloud.com:5000

# compute節點: # 重新啟動docker服務 systemctl daemon-reload && systemctl restart docker
驗證:
registry登錄驗證:
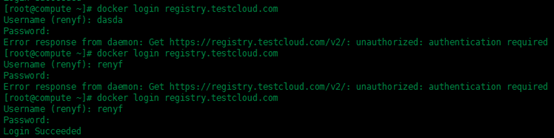
如上圖所示,你的用戶不存在數據庫中,或者用戶名存在但是密碼錯誤是登錄不上去的。
現在我們來更改鏡像名,來上傳鏡像驗證
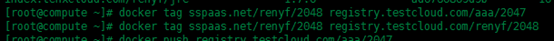
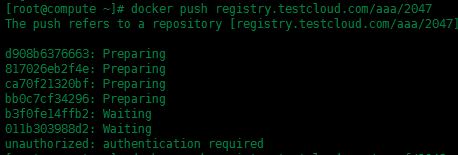
此時第一個tag更改的鏡像命名中用戶名為aaa並不是登錄成功的用戶名renyf,所以這裏上傳時會出現認證失敗的報錯,上傳不上去,接下來我們換成與用戶名相匹配的鏡像來上傳
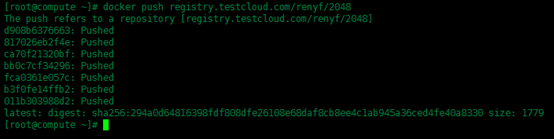
這次就上傳成功了。當然,下載鏡像也一樣,此處就不提供圖了。
參考文檔:https://github.com/cesanta/docker_auth/blob/master/docs/Backend_MongoDB.md
本文出自 “Renyf” 博客,請務必保留此出處http://renyongfan.blog.51cto.com/11693321/1955214
Docker私有倉庫Registry認證搭建
