openvpn部署賬號密碼登錄
1.開啟服務器端路由轉發功能;
修改配置文件/etc/sysctl.conf中
net.ipv4.ip_forward = 0 改為 net.ipv4.ip_forward = 1
[[email protected] ~]# sysctl -p #重讀配置文件
2.設置nat轉發;
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth0 -j MASQUERAD
#轉發內網192.168.1.0網段地址到eth0出口,MASQUERAD是動態地址,解決外網地址不固定;
3.時間同步;
ntpdate asia.pool.ntp.org
4.安裝OpenVPN 依賴的軟件包;
yum install -y openssl openssl-devel lzo lzo-devel pam pam-devel automake pkgconfig
5.安裝OpenVPN;
yum -y install openvpn
修改OpenVPN配置文件如下:
[[email protected] ~]# cat /etc/openvpn/server.conf
local 0.0.0.0
port 1194
proto tcp
dev tun
ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt
cert /etc/openvpn/easy-rsa/2.0/keys/ca.crt
key /etc/openvpn/easy-rsa/2.0/keys/ca.key
dh /etc/openvpn/easy-rsa/2.0/keys/dh2048.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /var/log/openvpn/ipp.txt
push "route 172.31.0.0 255.255.0.0"
client-to-client
keepalive 10 120
comp-lzo
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
log-append /var/log/openvpn.log
verb 3
client-cert-not-required #不使用客戶端證書,使用密碼進行驗證
username-as-common-name #使用認證用戶名,不使用證書
script-security 3
auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env #指定路徑,允許登陸的用戶名及密碼
6.添加檢測賬號密碼腳本
vim checkpsw.sh
#!/bin/sh
###########################################################
PASSFILE="/etc/openvpn/psw-file"
LOG_FILE="/var/log/openvpn-password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
###########################################################
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk ‘!/^;/&&!/^#/&&$1=="‘${username}‘"{print $2;exit}‘ ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username=\"${username}\"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
7.下載秘鑰生成工具easy-rsa:
wget https://github.com/OpenVPN/easy-rsa/archive/release/2.x.zip
下載完成的名字是這樣的2.x.zip ,用unzip解壓一下就變成了easy-rsa-release-2.x
然後cd到easy-rsa-release-2.x這個目錄下
需要把easy-rsa拷貝到/etc/openvpn目錄下
[[email protected] easy-rsa-release-2.x]# cp easy-rsa/ /etc/openvpn/
進入: cd easy-rsa/2.0
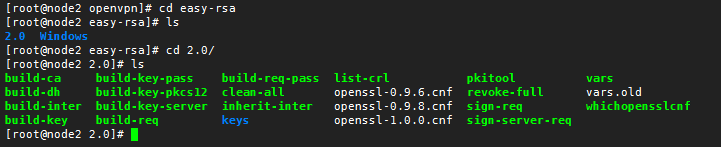
我們在來看一下真實路徑
有點亂,不知道有沒有寫明白;
修改vars為:
[[email protected] 2.0]# pwd
/etc/openvpn/easy-rsa/2.0
[[email protected] 2.0]#
[[email protected] 2.0]# cat vars
export EASY_RSA="`pwd`"
export OPENSSL="openssl"
export PKCS11TOOL="pkcs11-tool"
export GREP="grep"
export KEY_CONFIG=`$EASY_RSA/whichopensslcnf $EASY_RSA`
export KEY_DIR="$EASY_RSA/keys"
echo NOTE: If you run ./clean-all, I will be doing a rm -rf on $KEY_DIR
export PKCS11_MODULE_PATH="dummy"
export PKCS11_PIN="dummy"
export KEY_SIZE=2048
export CA_EXPIRE=3650
export KEY_EXPIRE=3650
export KEY_COUNTRY="US"
export KEY_PROVINCE="California"
export KEY_CITY="BJ"
export KEY_ORG="Fort-Funston"
export KEY_EMAIL="[email protected]"
export KEY_OU="MyOrganizationalUnit"
export KEY_NAME="EasyRSA"
給個執行權限:
chmod +x vars
./vars
./clean-all #清除文件
./build-ca #生成服務端 一路回車就行啦;
./build-dh
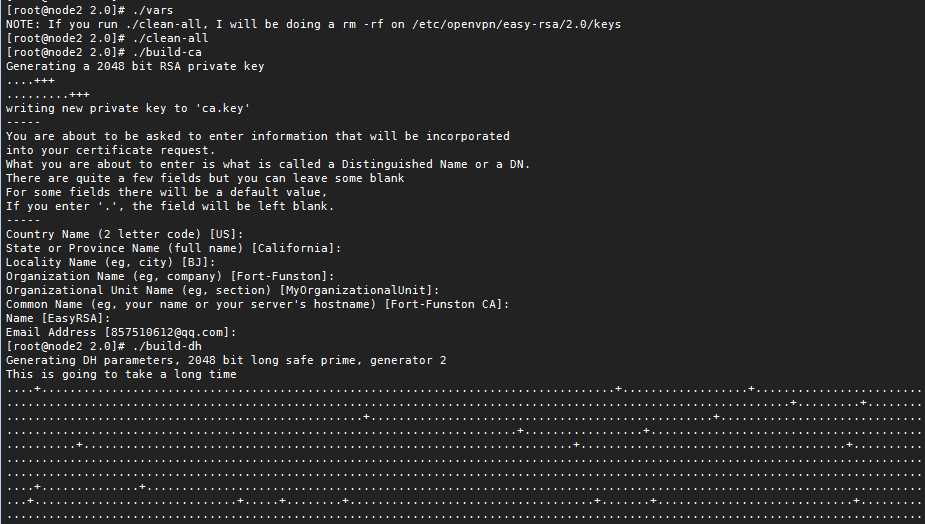
生成的文件在/etc/openvpn/easy-rsa/2.0/keys文件夾中
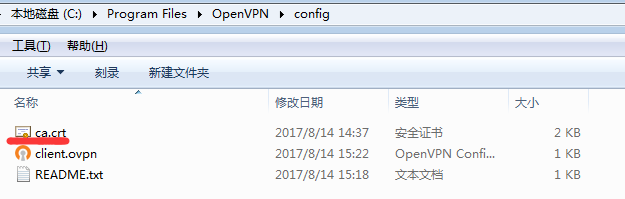
將ca.crt拷貝到本地(openvpn客戶端的config目錄中,我的位置是:C:\Program Files\OpenVPN\config)
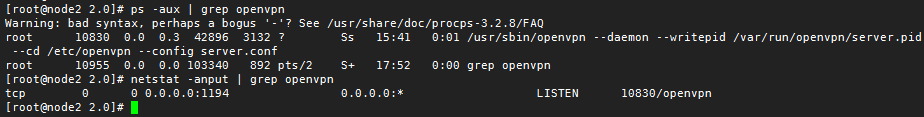
8.啟動服務,加入開機自啟動;
chkconfig openvpn on
/etc/init.d/openvpn start
9.clinet配置
https://openvpn.net/index.php/open-source/downloads.html
以上路徑下載客戶端 Windows版本(需要FQ)
安裝完畢後將路徑中sample-config的client.ovpn拷貝到config文件夾中
編輯config文件夾中的client.ovpn
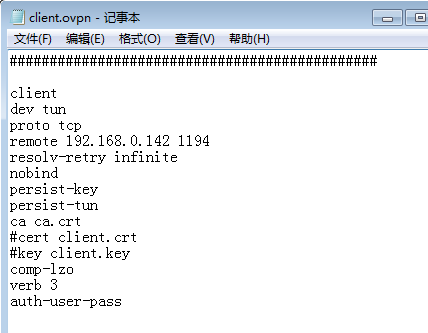
修改配置文件client.ovpn
##############################################
client
dev tun
proto tcp
remote 192.168.0.142 1194 #公網地址 公網端口
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
#cert client.crt
#key client.key
comp-lzo
verb 3
auth-user-pass
我的配置文件
10.編寫密碼文件;
vim
/etc/openvpn/psw-file
用戶名 密碼
chmod 777 psw-file
chown nobody.nobody psw-file
重新連接客戶端 輸入用戶名密碼即可登錄
openvpn部署賬號密碼登錄
