CentOS7 Firewall NAT 及端口映射
本節介紹用CentOS7的Firewalll來做NAT以及端口映射
實驗拓撲:
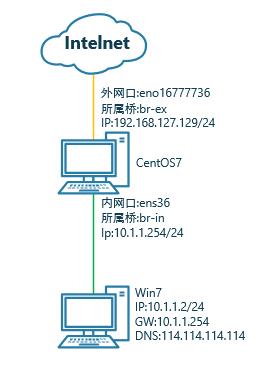
因為我的環境裏CentOS7上有KVM虛擬機需要共享網卡上網,所以我把網卡都添加到了橋裏面,當然這裏也可以不用橋,直接用物理網口;
用nmcli創建橋,並添加網口到橋;然後給橋設置IP地址:
先創建兩個橋"br-ex"和"br-in"
[[email protected] ~]# nmcli con add type bridge con-name br-ex ifname br-ex autoconnect yes Connection ‘br-ex‘ (2b823432-af25-497a-9b59-8b63709ef8ad) successfully added. [[email protected] ~]# nmcli con add type bridge con-name br-in ifname br-in autoconnect yes Connection ‘br-in‘ (e9c07ace-4182-41db-8208-7b93c139842f) successfully added. [[email protected]