LNMP-Nginx配置SSL
SSL證書是數字證書的一種,因為配置在服務器上,也稱為SSL服務器證書。它遵守SSL協議,由受信任的數字證書頒發機構CA,在驗證服務器身份後頒發,具有服務器身份驗證和數據傳輸加密功能。
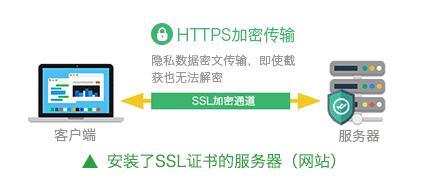
SSL證書通過在客戶端瀏覽器和Web服務器之間建立一條SSL安全通道,通過它可以激活SSL協議,實現數據信息在客戶端和服務器之間的加密傳輸,可以防止數據信息的泄露。保證了雙方傳遞信息的安全性,而且用戶可以通過服務器證書驗證他所訪問的網站是否是真實可靠。
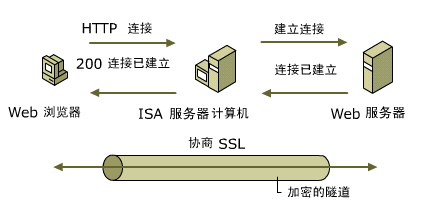
下面將演示在nginx環境下ssl的配置方式。
一、產生SSL密鑰對
1、安裝openssl
[[email protected] ~]# cd /usr/local/nginx/conf/ [[email protected] conf]# rpm -qf `which openssl` openssl-1.0.1e-60.el7_3.1.x86_64 [[email protected]
2、設置私鑰
[[email protected] conf]# openssl genrsa -des3 -out tmp.key 2048 Generating RSA private key, 2048 bit long modulus ..........................+++ ...........................................................................................................................................................+++ e is 65537 (0x10001) Enter pass phrase for tmp.key: Verifying - Enter pass phrase for tmp.key: [[email protected]