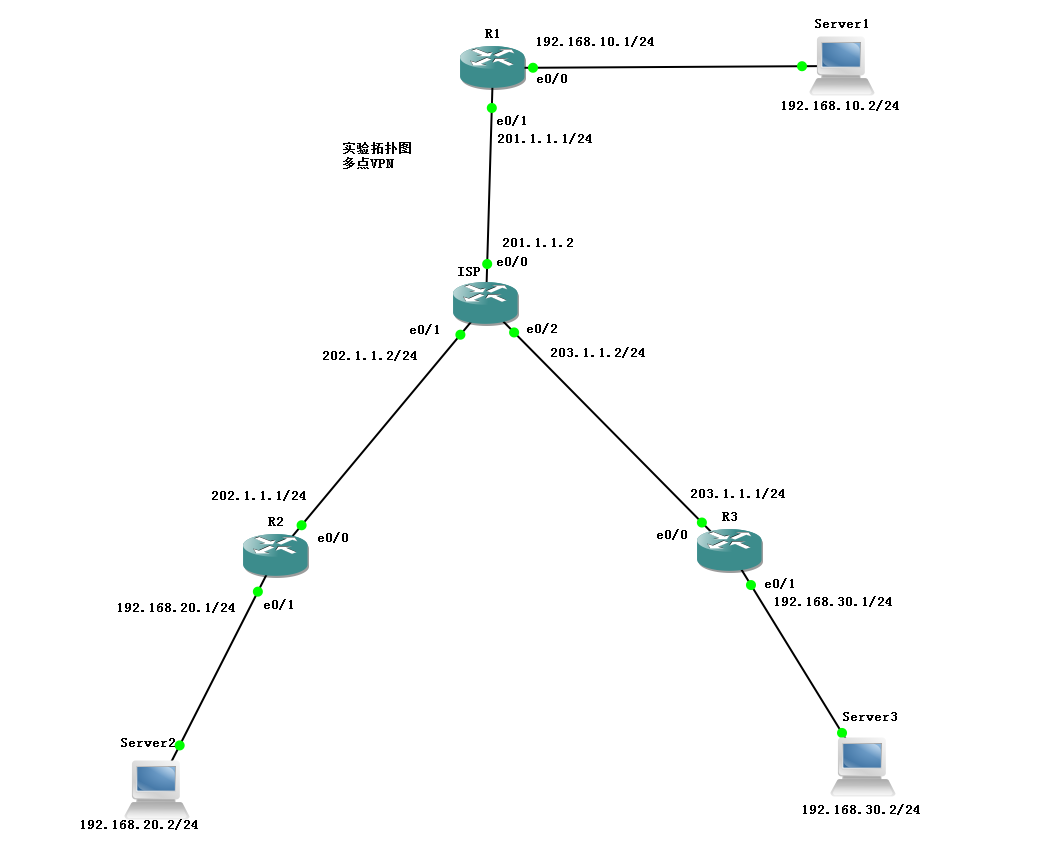
思科多點VPN
實驗拓撲圖
R1的配置
R1#
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#int e0/0
R1(config-if)#ip address 192.168.10.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#int e0/1
R1(config-if)#ip address 201.1.1.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 201.1.1.2
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encryption 3des
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
R1(config-isakmp)#lifetime 86400
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 0 benet-001 address 202.1.1.1
R1(config)#access-list 100 permit ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255
R1(config)#crypto ipsec transform-set benet-set esp-des esp-sha-hmac
R1(cfg-crypto-trans)#exit
R1(config)#crypto map benet-map 1 ipsec-isakmp
R1(config-crypto-map)#set peer 202.1.1.1
R1(config-crypto-map)#set transform-set benet-set
R1(config-crypto-map)#match address 100
R1(config-crypto-map)#exit
R1(config)#interface e0/1
R1(config-if)#crypto map benet-map
R1(config-if)#exit
R1(config)#crypto isakmp key 0 benet-002 address 203.1.1.1
R1(config)#access-list 101 permit ip 192.168.10.0 0.0.0.255 192.168.30.0 0.0.0.255
R1(config)#crypto map benet-map 2 ipsec-isakmp
R1(config-crypto-map)#set peer 203.1.1.1
R1(config-crypto-map)#set transform-set benet-set
R1(config-crypto-map)#match address 101
R1(config-crypto-map)#exit
R1(config)#do sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 201.1.1.2 to network 0.0.0.0
C 201.1.1.0/24 is directly connected, Ethernet0/1
C 192.168.10.0/24 is directly connected, Ethernet0/0
S* 0.0.0.0/0 [1/0] via 201.1.1.2
R1(config)#exit
R1#sh ip int br
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 192.168.10.1 YES manual up up
Ethernet0/1 201.1.1.1 YES manual up up
Ethernet0/2 unassigned YES unset administratively down down
Ethernet0/3 unassigned YES unset administratively down down
R1#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: Three key triple DES
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #2 (1024 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#sh crypto isakmp sa
dst src state conn-id slot status
201.1.1.1 203.1.1.1 QM_IDLE 1 0 ACTIVE
201.1.1.1 202.1.1.1 QM_IDLE 2 0 ACTIVE
R1#sh crypto ipsec transform-set
Transform set benet-set: { esp-des esp-sha-hmac }
will negotiate = { Tunnel, },
R1#sh crypto ipsec security-association lifetime
Security association lifetime: 4608000 kilobytes/3600 seconds
R1#sh crypto ipsec sa
interface: Ethernet0/1
Crypto map tag: benet-map, local addr 201.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0)
current_peer 202.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 201.1.1.1, remote crypto endpt.: 202.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/1
current outbound spi: 0x424460B1(1111777457)
inbound esp sas:
spi: 0xE63BFF4E(3862691662)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: SW:3, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4413320/275)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x424460B1(1111777457)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4413320/273)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.30.0/255.255.255.0/0/0)
current_peer 203.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 201.1.1.1, remote crypto endpt.: 203.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/1
current outbound spi: 0xC277F10B(3262640395)
inbound esp sas:
spi: 0xE626B38D(3861296013)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: SW:5, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4512342/3331)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC277F10B(3262640395)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: SW:6, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4512342/3329)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R1#
R2的配置
R2#
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#int e0/0
R2(config-if)#ip address 202.1.1.1 255.255.255.0
R2(config-if)#no sh
R2(config-if)#int e0/1
R2(config-if)#ip address 192.168.20.1 255.255.255.0
R2(config-if)#no sh
R2(config-if)#exit
R2(config)#ip route 0.0.0.0 0.0.0.0 202.1.1.2
R2(config)#crypto isakmp policy 1
R2(config-isakmp)#encryption 3des
R2(config-isakmp)#hash sha
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#group 2
R2(config-isakmp)#lifetime 86400
R2(config-isakmp)#exit
R2(config)#crypto isakmp key 0 benet-001 address 201.1.1.1
R2(config)#access-list 100 permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
R2(config)#crypto ipsec transform-set benet-set esp-des esp-sha-hmac
R2(cfg-crypto-trans)#exit
R2(config)#crypto map benet-map 1 ipsec-isakmp
R2(config-crypto-map)#set peer 201.1.1.1
R2(config-crypto-map)#set transform-set benet-set
R2(config-crypto-map)#match address 100
R2(config-crypto-map)#exit
R2(config)#int e0/0
R2(config-if)#crypto map benet-map
R2(config-if)#exit
R2(config)#crypto isakmp key 0 benet-003 address 203.1.1.1
R2(config)#access-list 101 permit ip 192.168.20.0 0.0.0.255 192.168.30.0 0.0.0.255
R2(config)#crypto map benet-map 2 ipsec-isakmp
R2(config-crypto-map)#set peer 203.1.1.1
R2(config-crypto-map)#set transform-set benet-set
R2(config-crypto-map)#match address 101
R2(config-crypto-map)#exit
R2(config)#do sh ip int br
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 202.1.1.1 YES manual up up
Ethernet0/1 192.168.20.1 YES manual up up
Ethernet0/2 unassigned YES unset administratively down down
Ethernet0/3 unassigned YES unset administratively down down
R2#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 202.1.1.2 to network 0.0.0.0
C 202.1.1.0/24 is directly connected, Ethernet0/0
C 192.168.20.0/24 is directly connected, Ethernet0/1
S* 0.0.0.0/0 [1/0] via 202.1.1.2
R2#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: Three key triple DES
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #2 (1024 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R2#sh crypto isakmp sa
dst src state conn-id slot status
203.1.1.1 202.1.1.1 QM_IDLE 4 0 ACTIVE
201.1.1.1 202.1.1.1 QM_IDLE 3 0 ACTIVE
R2#sh crypto ipsec transform-set
Transform set benet-set: { esp-des esp-sha-hmac }
will negotiate = { Tunnel, },
R2#sh crypto ipsec security-association lifetime
Security association lifetime: 4608000 kilobytes/3600 seconds
R2#sh crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: benet-map, local addr 202.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.30.0/255.255.255.0/0/0)
current_peer 203.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 6, #recv errors 0
local crypto endpt.: 202.1.1.1, remote crypto endpt.: 203.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x917A166A(2440697450)
inbound esp sas:
spi: 0x1DE765BF(501704127)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4385147/3215)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x917A166A(2440697450)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4385147/3213)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
current_peer 201.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 202.1.1.1, remote crypto endpt.: 201.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xE5873DD8(3850845656)
inbound esp sas:
spi: 0x98029446(2550305862)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: SW:5, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4542471/3039)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xE5873DD8(3850845656)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: SW:6, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4542471/3037)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R2#
R3的配置
R3#
R3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#int e0/0
R3(config-if)#ip address 203.1.1.1 255.255.255.0
R3(config-if)#no sh
R3(config-if)#int e0/1
R3(config-if)#ip address 192.168.30.1 255.255.255.0
R3(config-if)#no sh
R3(config-if)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 203.1.1.2
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#hash sha
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#group 2
R3(config-isakmp)#lifetime 86400
R3(config-isakmp)#exit
R3(config)#crypto isakmp key 0 benet-002 address 201.1.1.1
R3(config)#access-list 100 permit ip 192.168.30.0 0.0.0.255 192.168.10.0 0.0.0.255
R3(config)#crypto ipsec transform-set benet-set esp-des esp-sha-hmac
R3(cfg-crypto-trans)#exit
R3(config)#crypto map benet-map 1 ipsec-isakmp
R3(config-crypto-map)#set peer 201.1.1.1
R3(config-crypto-map)#set transform-set benet-set
R3(config-crypto-map)#match address 100
R3(config-crypto-map)#exit
R3(config)#int e0/0
R3(config-if)#crypto map benet-map
R3(config-if)#exit
R3(config)#cry
R3(config)#crypto isakmp key 0 benet-003 address 202.1.1.1
R3(config)#access-list 101 permit ip 192.168.30.0 0.0.0.255 192.168.20.0 0.0.0.255
R3(config)#crypto map benet-map 2 ipsec-isakmp
R3(config-crypto-map)#set peer 202.1.1.1
R3(config-crypto-map)#set transform-set benet-set
R3(config-crypto-map)#match address 101
R3(config-crypto-map)#exit
R3(config)#exit
R3#sh ip int br
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 203.1.1.1 YES manual up up
Ethernet0/1 192.168.30.1 YES manual up up
Ethernet0/2 unassigned YES unset administratively down down
Ethernet0/3 unassigned YES unset administratively down down
R3#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 203.1.1.2 to network 0.0.0.0
C 192.168.30.0/24 is directly connected, Ethernet0/1
C 203.1.1.0/24 is directly connected, Ethernet0/0
S* 0.0.0.0/0 [1/0] via 203.1.1.2
R3#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: Three key triple DES
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #2 (1024 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R3#sh crypto isakmp sa
dst src state conn-id slot status
201.1.1.1 203.1.1.1 QM_IDLE 1 0 ACTIVE
203.1.1.1 202.1.1.1 QM_IDLE 2 0 ACTIVE
R3#sh crypto ipsec transform-set
Transform set benet-set: { esp-des esp-sha-hmac }
will negotiate = { Tunnel, },
R3#sh crypto ipsec security-association lifetime
Security association lifetime: 4608000 kilobytes/3600 seconds
R3#sh crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: benet-map, local addr 203.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.30.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0)
current_peer 202.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 30, #recv errors 0
local crypto endpt.: 203.1.1.1, remote crypto endpt.: 202.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x1DE765BF(501704127)
inbound esp sas:
spi: 0x917A166A(2440697450)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4427598/2792)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x1DE765BF(501704127)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4427598/2791)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.30.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
current_peer 201.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 10, #recv errors 0
local crypto endpt.: 203.1.1.1, remote crypto endpt.: 201.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xE626B38D(3861296013)
inbound esp sas:
spi: 0xC277F10B(3262640395)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: SW:5, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4406309/2269)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xE626B38D(3861296013)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: SW:6, crypto map: benet-map
sa timing: remaining key lifetime (k/sec): (4406309/2267)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R3#
ISP的配置
ISP#
ISP#conf t
Enter configuration commands, one per line. End with CNTL/Z.
ISP(config)#int e0/0
ISP(config-if)#ip address 201.1.1.2 255.255.255.0
ISP(config-if)#no sh
ISP(config-if)#int e0/1
ISP(config-if)#ip address 202.1.1.2 255.255.255.0
ISP(config-if)#no sh
ISP(config-if)#int e0/2
ISP(config-if)#ip address 203.1.1.2 255.255.255.0
ISP(config-if)#no sh
ISP(config-if)#exit
ISP(config)#do sh ip int br
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 201.1.1.2 YES manual up up
Ethernet0/1 202.1.1.2 YES manual up up
Ethernet0/2 203.1.1.2 YES manual up up
Ethernet0/3 unassigned YES unset administratively down down
ISP(config)#do sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 201.1.1.0/24 is directly connected, Ethernet0/0
C 203.1.1.0/24 is directly connected, Ethernet0/2
C 202.1.1.0/24 is directly connected, Ethernet0/1
ISP(config)#
驗證Server
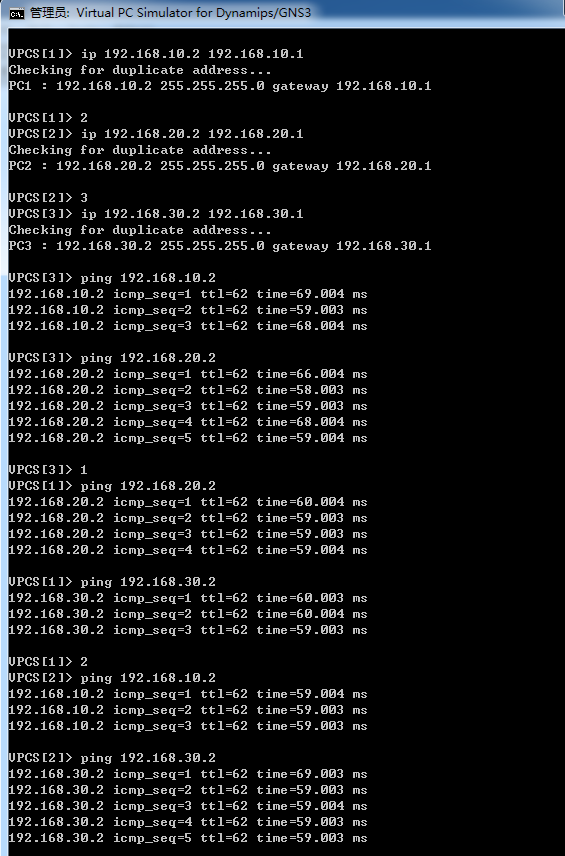
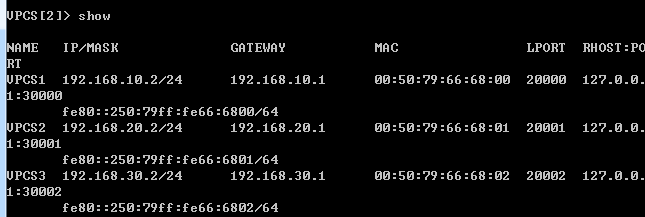
Server都能互相訪問PING通 實驗成功完成。
本文出自 “DY” 博客,請務必保留此出處http://guochenyong.blog.51cto.com/11367898/1980722
思科多點VPN
