EVE-NG之ASA Anyconnect 橋接VMWare ISE實驗
近日利用EVE-NG搭建了一個SSLVPN實驗,在此之前一個對VPN之類的玩意沒有接觸過,故實驗花了三天時間研究。以下為實驗的拓撲圖。
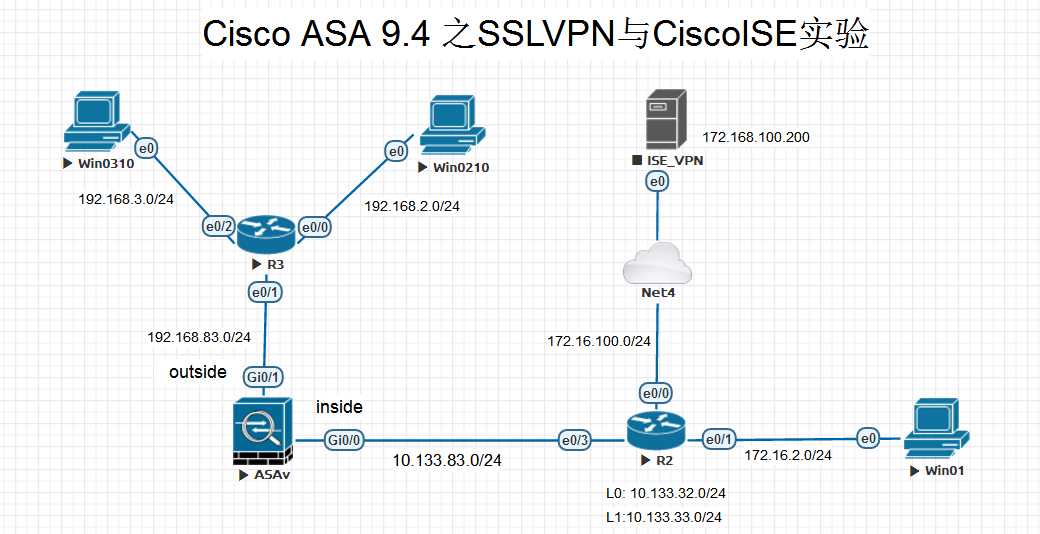
實驗說明:1. CiscoASA 9.4 用於SSLVPN Server,Outside 網關192.168.83.254
2. 主機ISE_VPN 用於拔入賬號認證授權,IP Address: 172.16.100.20,通過橋接連接進EVE-NG實驗平臺
3. 路由器R2新建L0: 10.133.32.0/24 、L1: 10.133.33.0/24模擬內網兩個網段
4. Outside的兩個主機Win0210 、Win0310分別模擬互聯網兩個用戶user01、user02
5. 互聯網用戶user01只可以防問內網網段10.133.32.0/24
6. 互聯網用戶user02只可以防問內網網段10.133.33.0/24
網絡設備基本設定
1. 路由器R3只設定三個接口的ip,路由不使用設定。
interface Ethernet0/0
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/1
ip address 192.168.83.1 255.255.255.0
!
interface Ethernet0/2
ip address 192.168.3.1 255.255.255.0
2.Win0210 與 Win0310設定IP,並且網關分別指向各自接口的IP。
3.路由器R2除了設定接口IP外,還要設定一條默認路由
interface Loopback0
ip address 10.133.32.1 255.255.255.0
!
interface Loopback1
ip address 10.133.33.1 255.255.255.0
!
interface Ethernet0/0
ip address 172.16.100.254 255.255.255.0
!
interface Ethernet0/1
ip address 172.16.2.254 255.255.255.0
!
interface Ethernet0/3
ip address 10.133.83.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.133.83.254
4. Cisco ASA基本設定
# 設定VPN用戶獲取的IP地址池
ip local pool ISE_POOL 10.133.83.32-10.133.83.64 mask 255.255.255.0
!
interface GigabitEthernet0/0
nameif inside
security-level 100
ip address 10.133.83.254 255.255.255.0
!
interface GigabitEthernet0/1
nameif outside
security-level 0
ip address 192.168.83.254 255.255.255.0
!
#設定路由
route outside 0.0.0.0 0.0.0.0 192.168.83.1 1
route inside 10.133.32.0 255.255.252.0 10.133.83.1 1
route inside 10.133.33.0 255.255.255.0 10.133.83.1 1
route inside 172.16.2.0 255.255.255.0 10.133.83.1 1
route inside 172.16.100.0 255.255.255.0 10.133.83.1 1
#設定AAA-SERVER 屬性
aaa-server ISE protocol radius
interim-accounting-update periodic 3
merge-dacl before-avpair
dynamic-authorization
#設定AAA-SERVER 服務器IP Address
aaa-server ISE (inside) host 172.16.100.200
key *****
user-identity default-domain LOCAL
#開啟HTTP防問服務
http server enable
http 0.0.0.0 0.0.0.0 outside
http 10.133.32.0 255.255.252.0 inside
ssh stricthostkeycheck
ssh 172.16.100.0 255.255.255.0 inside
#開啟WEBVPN
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-4.2.05015-k9.pkg 1
anyconnect enable
tunnel-group-list enable
error-recovery disable
group-policy ISE_VPN internal
group-policy ISE_VPN attributes
dns-server value 172.16.200.1
vpn-tunnel-protocol ssl-client
dynamic-access-policy-record DfltAccessPolicy
username admin password QCP00FvqVQRpzCZ/ encrypted privilege 15
# tunnel-group設定
tunnel-group ISE_AAA type remote-access
tunnel-group ISE_AAA general-attributes
address-pool ISE_POOL
authentication-server-group ISE
accounting-server-group ISE
default-group-policy ISE_VPN
#開啟tunnel對外服務IP Address
tunnel-group ISE_AAA webvpn-attributes
group-alias ISE_AAA enable
group-url https://192.168.83.254 enable
5.CiscoISE設定
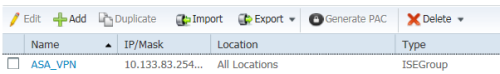
5.1 增加ASA的IP Addrss
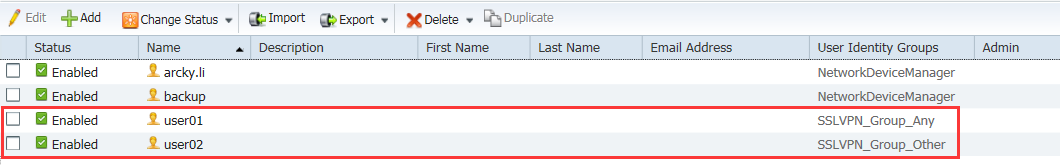
5.2增加兩個用戶並且放至不同的組
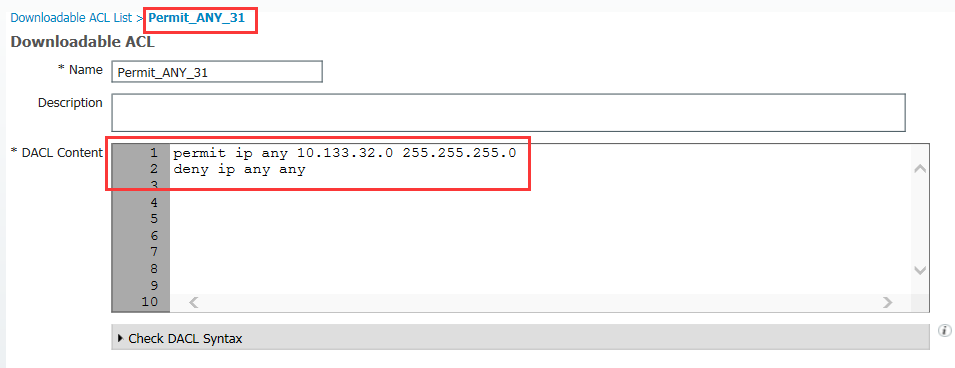
5.3 分別增加兩條ACL策略
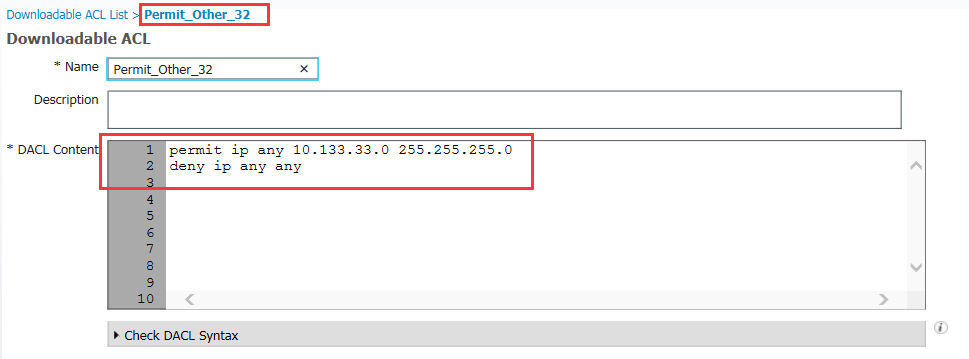
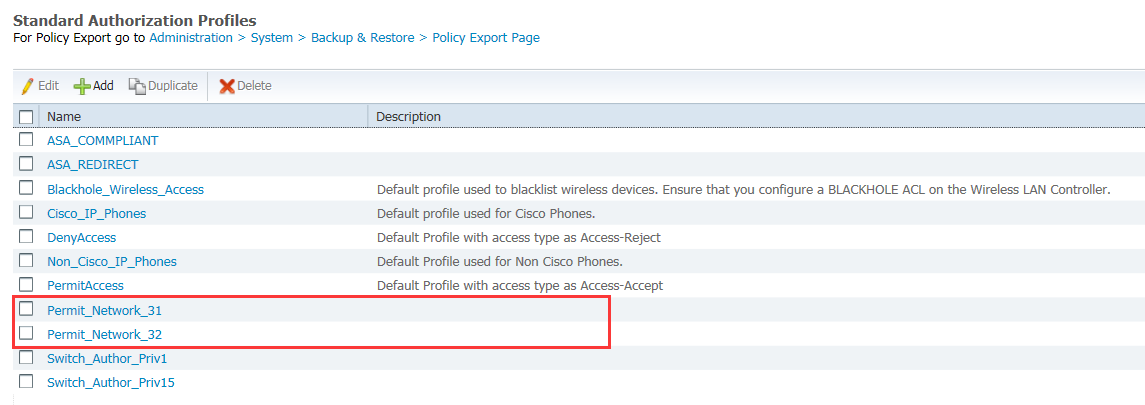
5.4 分另增加兩條授權策略,並分別調用上面的新增的ACL策略
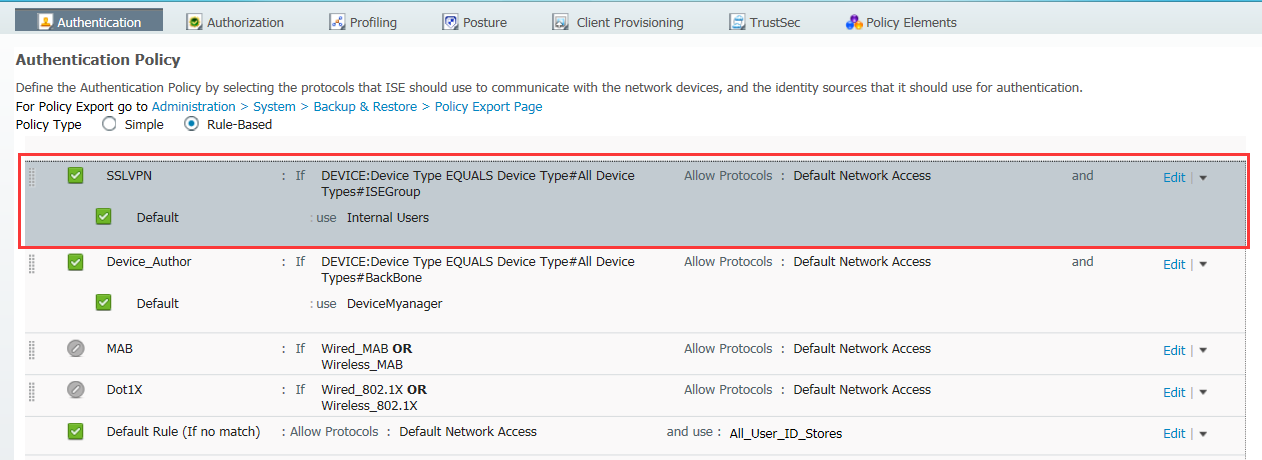
5.5 新增Authentication策略
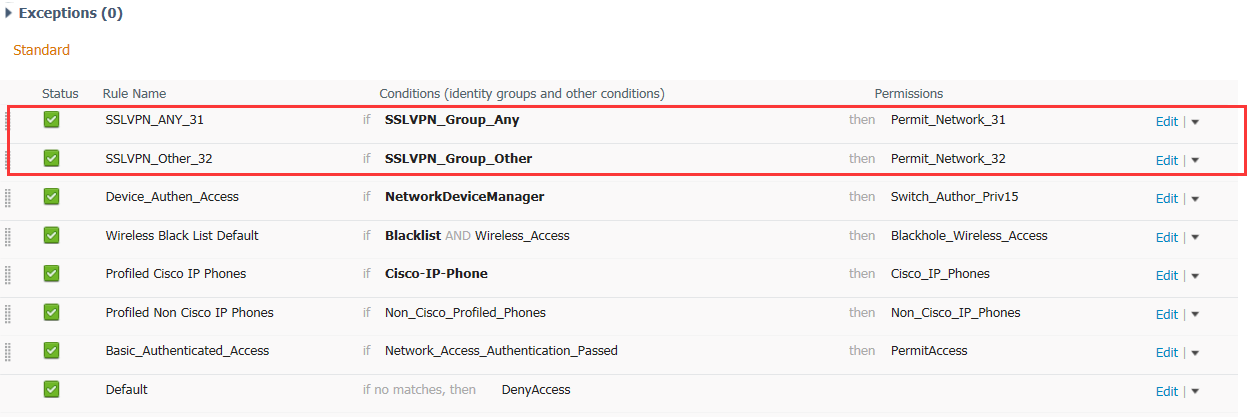
5.6 分別新增兩條Authorization策略
6. 以上完成後,使用user01賬號測試
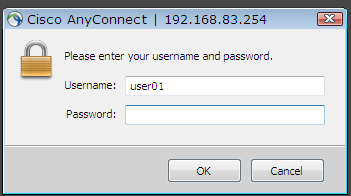
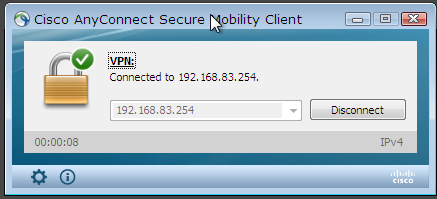
user01賬號登錄成功
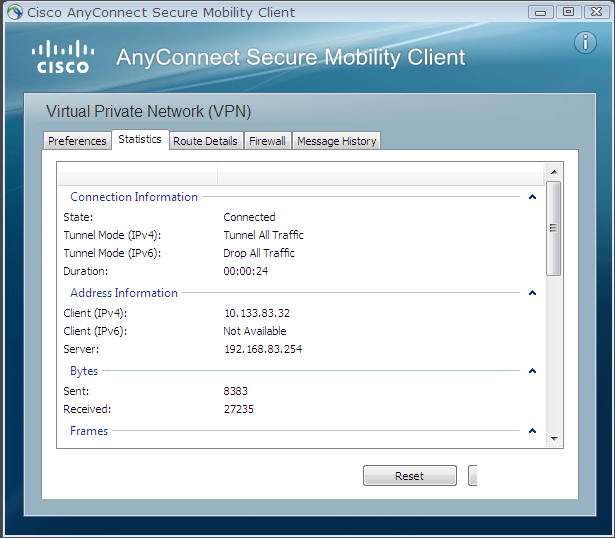
以下為ISE認證記錄信息
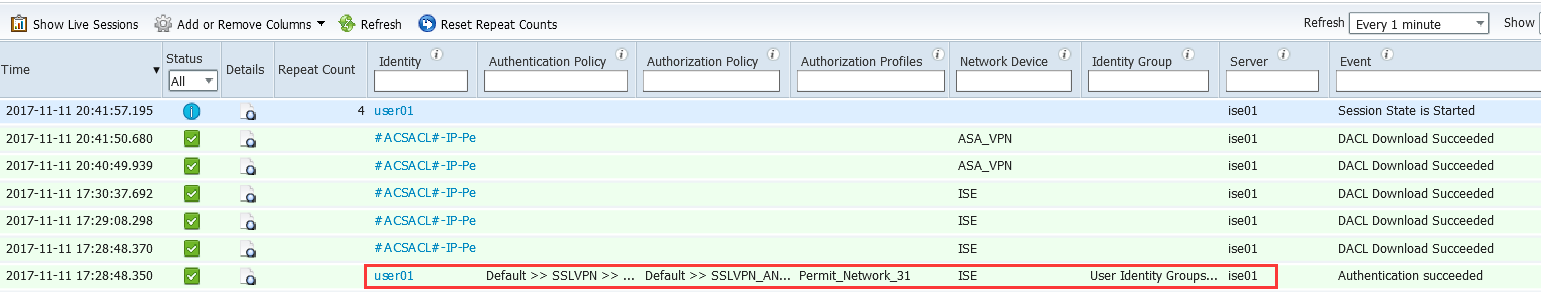
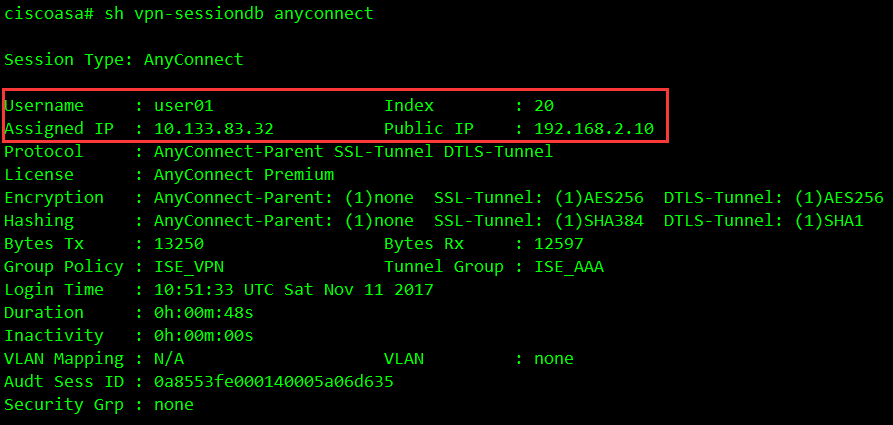
ASA上面的記錄
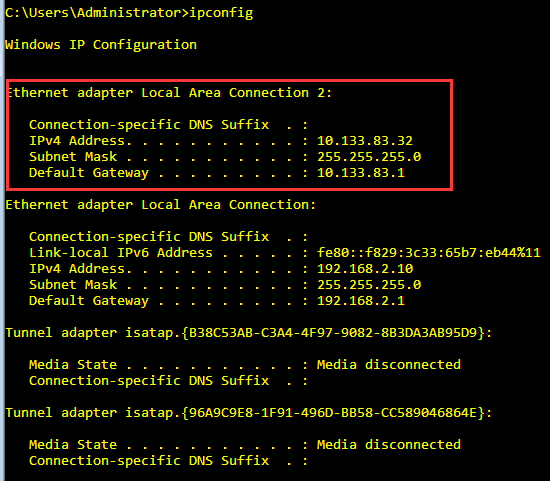
主機Win0210 登錄成功後的所獲取的IP Address
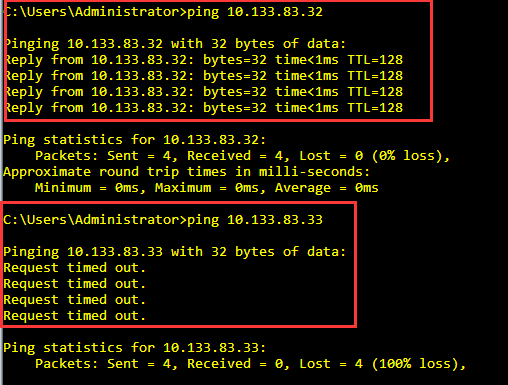
分別ping 內網兩個網段的IP,因User01只有防問10.133.32.0/24的權限故可以ping通;沒有10.133.33.0/24的防問權限,故不能ping通。
本文出自 “無心傷害” 博客,轉載請與作者聯系!
EVE-NG之ASA Anyconnect 橋接VMWare ISE實驗
