2018-1-24 7周3次課 網絡、firewalld、netfilter、iptables語法
安裝:yum install -y net-tools
·查看網卡ip:ifconfig
[root@localhost ~]# ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.65.128 netmask 255.255.255.0 broadcast 192.168.65.255 inet6 fe80::7cd2:a780:c114:4d06 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:7e:8b:1b txqueuelen 1000 (Ethernet) RX packets 38578 bytes 19915225 (18.9 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 88936 bytes 20130502 (19.1 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1 (Local Loopback) RX packets 68 bytes 5916 (5.7 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 68 bytes 5916 (5.7 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
·查看所有網卡(包括沒有啟動的網卡):ifconfig -a
·啟動網卡:ifup 網卡名
·關閉網卡:ifdown 網卡名
[root@localhost ~]# ifdown ens33 && ifup ens33 成功斷開設備 'ens33'。 連接已成功激活(D-Bus 活動路徑:/org/freedesktop/NetworkManager/ActiveConnection/2)
·設定虛擬網卡:
[root@localhost network-scripts]# cd /etc/sysconfig/network-scripts/ [root@localhost network-scripts]# cp ifcfg-ens33 ifcfg-ens33\:0 [root@localhost network-scripts]# vim ifcfg-ens33\:0
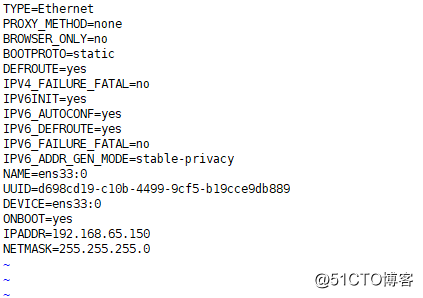
保存退出
[root@localhost network-scripts]# ifdown ens33 && ifup ens33 成功斷開設備 'ens33'。 連接已成功激活(D-Bus 活動路徑:/org/freedesktop/NetworkManager/ActiveConnection/3) [root@localhost network-scripts]# ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.65.128 netmask 255.255.255.0 broadcast 192.168.65.255 inet6 fe80::7cd2:a780:c114:4d06 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:7e:8b:1b txqueuelen 1000 (Ethernet) RX packets 39173 bytes 19967129 (19.0 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 89362 bytes 20190444 (19.2 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens33:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.65.150 netmask 255.255.255.0 broadcast 192.168.65.255 ether 00:0c:29:7e:8b:1b txqueuelen 1000 (Ethernet) lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1 (Local Loopback) RX packets 68 bytes 5916 (5.7 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 68 bytes 5916 (5.7 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
(可以看出,已經多了一個虛擬網卡ens33:0)
·查看網卡是否連接:
mii-tool 網卡名
ethtool 網卡名
[root@localhost ~]# mii-tool ens33
ens33: negotiated 1000baseT-FD flow-control, link ok ##連接正常
[root@localhost ~]# ethtool ens33
Settings for ens33:
Supported ports: [ TP ]
Supported link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
1000baseT/Full
Supported pause frame use: No
Supports auto-negotiation: Yes
Advertised link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
1000baseT/Full
Advertised pause frame use: No
Advertised auto-negotiation: Yes
Speed: 1000Mb/s
Duplex: Full
Port: Twisted Pair
PHYAD: 0
Transceiver: internal
Auto-negotiation: on
MDI-X: off (auto)
Supports Wake-on: d
Wake-on: d
Current message level: 0x00000007 (7)
drv probe link
Link detected: yes ##連接正常·更改主機名:hostnamectl
[root@localhost ~]# hostnamectl set-hostname alexis hostname配置文件:/etc/hostname
·DNS配置文件:/etc/resolv.conf
[root@localhost ~]# cat /etc/resolv.conf # Generated by NetworkManager nameserver 119.29.29.29
(參數由網卡配置文件所定義,哪怕更改,再重啟網卡,依然會被恢復為網卡內的參數)
/etc/hosts文件
[root@localhost ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
前面為IP,後面為域名
一行可以有多個域名
多個相同的域名不同的IP,默認使用最後一個IP
10.12 firewalld和netfilter

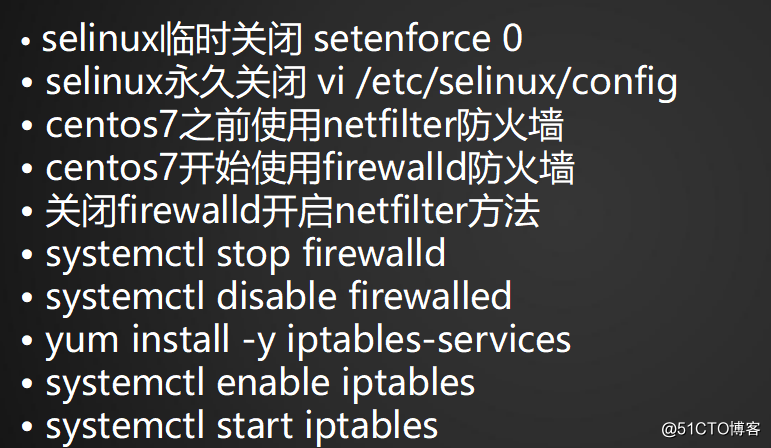
·臨時關閉selinux:setenforce 0
[root@localhost ~]# getenforce Permissive
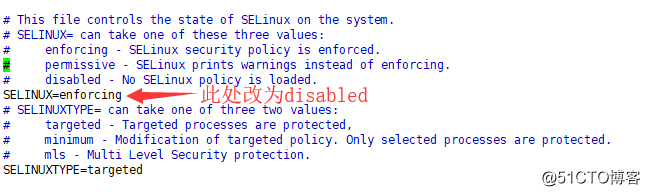
·永久關閉selinux:編輯/etc/selinux/config
[root@localhost ~]# vim /etc/selinux/config

·CentOS7之前使用netfilter防火墻,CentOS7開始使用firewalld防火墻
·關閉firewalld,開啟netfilter
[root@localhost ~]# systemctl disable firewalld ##禁用firewalld Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service. Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service. [root@localhost ~]# systemctl stop firewalld##停止firewalld [root@localhost ~]# yum install -y iptables-services (過程省略) [root@localhost ~]# systemctl enable iptables ##允許iptables Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service. [root@localhost ~]# systemctl start iptables ##開啟iptables [root@localhost ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 26 1716 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 14 packets, 1320 bytes) pkts bytes target prot opt in out source destination
(netfilter防火墻的名字而iptables是工具)
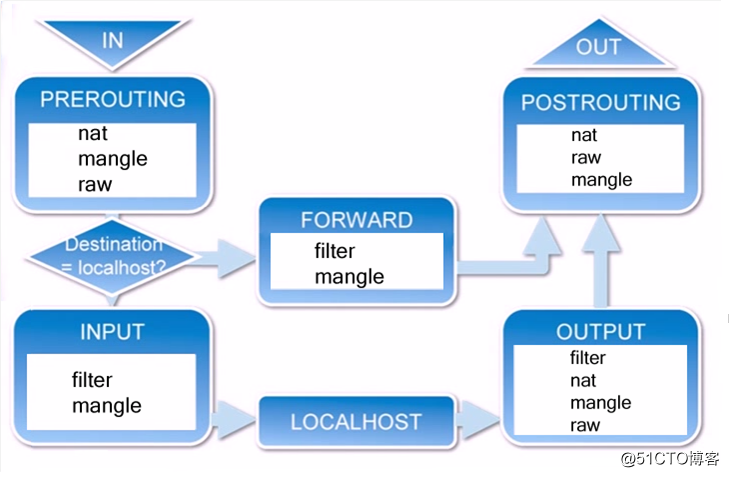
10.13 netfilter5表5鏈介紹

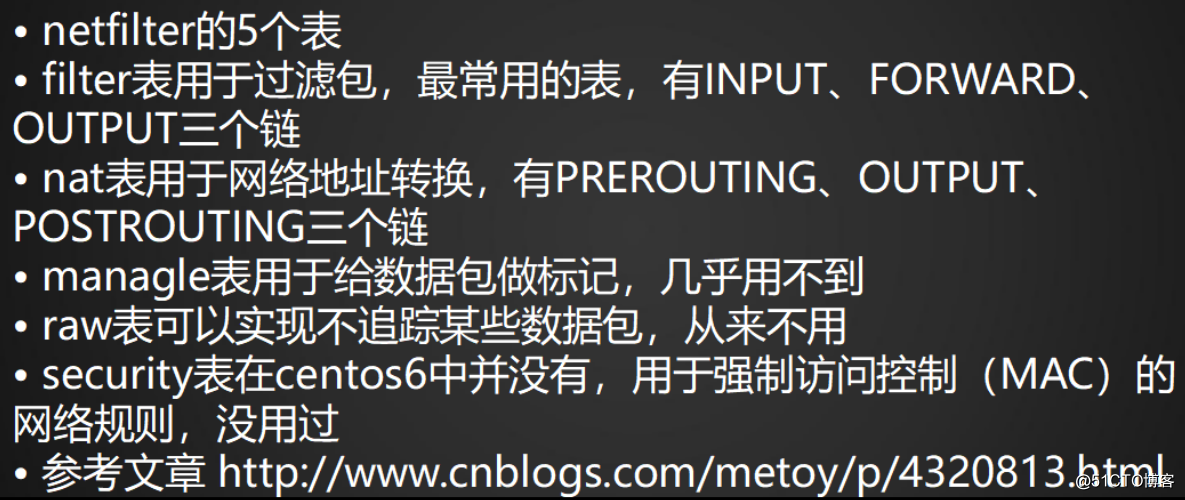
netfilter的5個表:(1)filter (2)nat (3)managle (4)raw (5)security
netfilter的5個鏈:(1)INPUT(2)OUTPUT(3)FORWARD(4)PREROUTING(5)POSTROUTING
managle,raw,security表基本用不到,因此不用關註,只需要關註filter和nat即可
·iptables傳輸數據包的過程:

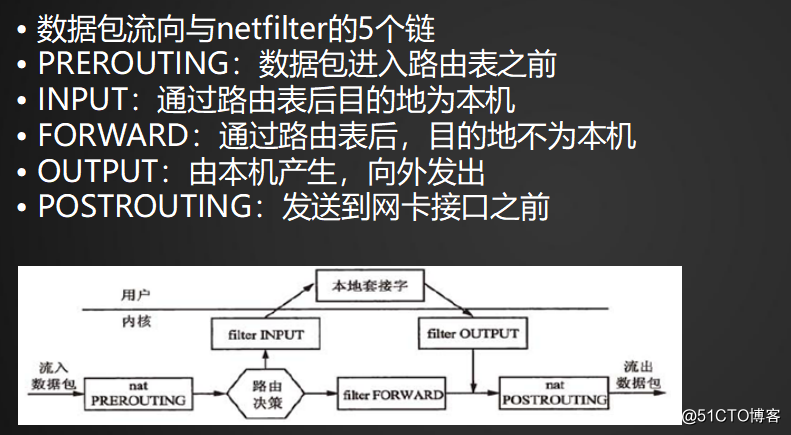
數據包進入本機:PREROUTING—>INPUT—>OUTPUT—>POSTROUTING
數據包不經過本機,而是轉發出去:PREROUTING—>FORWARD—>POSTROUTING

參考:http://www.cnblogs.com/metoy/p/4320813.html
10.14 iptables語法

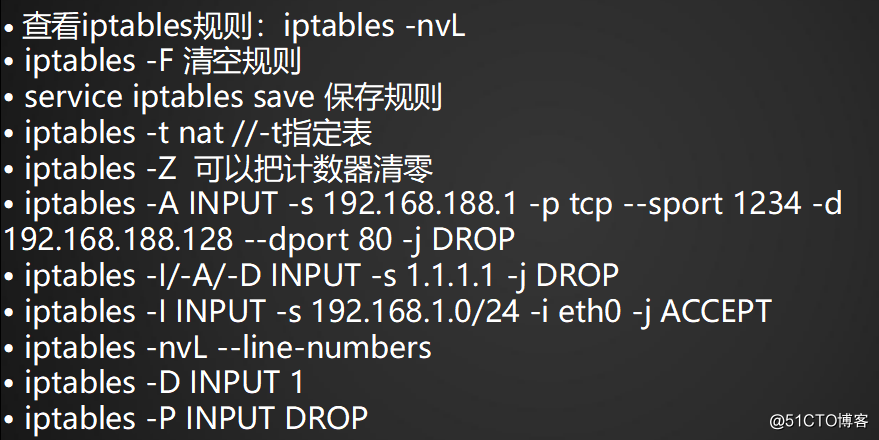
·查看iptables規則:iptables -nvL
[root@localhost ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 26 1716 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 14 packets, 1320 bytes) pkts bytes target prot opt in out source destination
·iptables規則保存在 /etc/sysconfig/iptables 中
[root@localhost ~]# cat /etc/sysconfig/iptables # sample configuration for iptables service # you can edit this manually or use system-config-firewall # please do not ask us to add additional ports/services to this default configuration *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT -A INPUT -j REJECT --reject-with icmp-host-prohibited -A FORWARD -j REJECT --reject-with icmp-host-prohibited COMMIT
·清空iptables規則:iptables -F
[root@localhost ~]# iptables -F [root@localhost ~]# iptables -nvL ##清空規則後,實際配置文件並沒有變化 Chain INPUT (policy ACCEPT 12 packets, 792 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 7 packets, 900 bytes) pkts bytes target prot opt in out source destination
·保存iptables規則:service iptables save
[root@localhost ~]# service iptables save
·加載iptables規則:重啟服務器或者重新啟動服務service iptables restart
[root@localhost ~]# service iptables restart Redirecting to /bin/systemctl restart iptables.service [root@localhost ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 12 792 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 7 packets, 884 bytes) pkts bytes target prot opt in out source destination
(重啟服務器或者重啟iptables規則,都會去加載配置文件 /etc/sysconfig/iptables 中的規則)
·默認iptables查看的時netfilter表的規則 iptables -t netfilter -nvL(不加 -t 就是filter表)
·查看nat表的規則:iptables -t nat -nvL
[root@localhost ~]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
·計數器清零:iptables -Z
[root@localhost ~]# iptables -Z;iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
·iptables:
-A 增加一條規則 INPUT:針對的鏈
-s 指定來源ip
-p 指定協議(tcp、udp、icmp)
--sport 來源端口
-d 目標ip
--dport 目標端口
-j 操作 (DROP扔掉 / REJECT 拒絕)
-I 插入
-i 指定網卡
·增加規則:iptables -A
[root@localhost ~]# iptables -A INPUT -s 192.168.188.1 -p tcp --sport 1234 -d 192.168.188.128 --dport 80 -j DROP

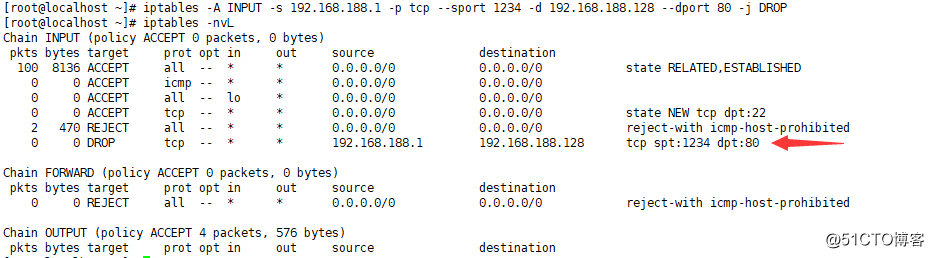
·插入規則:iptables -I
iptables -I INPUT -p tcp --dport 80 -j DROP## -I 直接插隊到最前面,-A只是添加 [root@localhost ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 128 10156 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 2 470 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 5 packets, 636 bytes) pkts bytes target prot opt in out source destination
·刪除規則:iptables -D
[root@localhost ~]# iptables -D INPUT -p tcp --dport 80 -j DROP [root@localhost ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 201 15908 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 3 705 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes) pkts bytes target prot opt in out source destination
·刪除規則(簡便方法):
1,先給規則一個規則號;2,再刪除規則號對應的規則
[root@localhost ~]# iptables -nvL --line-number ##指定規則號 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 2 337 25080 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 6 3 705 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 7 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 67 packets, 6092 bytes) num pkts bytes target prot opt in out source destination [root@localhost ~]# iptables -D INPUT 1 ##刪除第一個規則 [root@localhost ~]# iptables -nvL ##之前的第一條規則已經被刪除 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 477 34948 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 4 940 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 55 packets, 6900 bytes) pkts bytes target prot opt in out source destination
·指定網卡:iptables -I INPUT -s 192.168.1.0/24 -i eth0 -j ACCEPT
·默認規則:(數據包如果沒有具體規則來匹配,那麽就走默認的策略 policy)
更改默認策略:iptables -P OUTPUT DROP(運行的話,遠程連接就會被禁掉,只能到主機去修改規則)
改回策略:iptables -P OUTPUT ACCEPT (放行)、
DROP / REJECT / ACCEPT
2018-1-24 7周3次課 網絡、firewalld、netfilter、iptables語法
