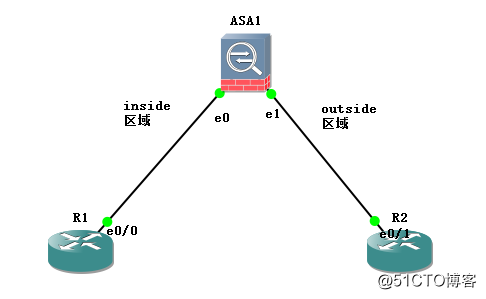
ASA 防火墻的 inside區域與outside區域
註:測試用telnet來測試
因為ASA默認之給TCP與UDP形成CONN表
icmp協議不能形成CONN表所以用ping方式
來測試是ping不通的是正常現象
ASA.配置:
ciscoasa# show running-config
: Saved
:
ASA Version 8.4(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif Intside
security-level 0
ip address 192.168.10.254 255.255.255.0
interface GigabitEthernet1
nameif outside
security-level 0
ip address 192.168.20.254 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
pager lines 24
mtu Intside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
crashinfo save disable
Cryptochecksum:715f838bf34db00a308a613eb31214ac
: end
ciscoasa# conf t
ciscoasa(config)# in g0
ciscoasa(config-if)# no na
ciscoasa(config-if)#no nameif Intside
ciscoasa(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ciscoasa(config-if)# --
^
ERROR: % Invalid input detected at ‘^‘ marker.
ciscoasa(config-if)#
ciscoasa(config-if)# qq
^
ERROR: % Invalid input detected at ‘^‘ marker.
ciscoasa(config-if)# q
ciscoasa(config)# q
ciscoasa# show rou
ciscoasa# show route
ciscoasa# show run
ciscoasa# show running-config
: Saved
:
ASA Version 8.4(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif inside
security-level 100
ip address 192.168.10.254 255.255.255.0
!
interface GigabitEthernet1
nameif outside
security-level 0
ip address 192.168.20.254 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
pager lines 24
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
crashinfo save disable
Cryptochecksum:b6be07c60b5c6f70fdd258745b715629
R1配置:
[Connection to 192.168.20.1 closed by foreign host]
R1#show run
R1#show running-config
Building configuration...
Current configuration : 1164 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip tcp synwait-time 5
!
ip cef
no ip domain lookup
!
interface Ethernet0/0
ip address 192.168.10.1 255.255.255.0
half-duplex
!
interface Ethernet0/1
no ip address
shutdown
half-duplex
!
interface Ethernet0/2
no ip address
shutdown
half-duplex
!
interface Ethernet0/3
no ip address
shutdown
half-duplex
!
interface Ethernet1/0
no ip address
shutdown
half-duplex
!
interface Ethernet1/1
no ip address
shutdown
half-duplex
!
interface Ethernet1/2
no ip address
shutdown
half-duplex
!
interface Ethernet1/3
no ip address
shutdown
half-duplex
!
no ip http server
no ip http secure-server
ip route 192.168.20.0 255.255.255.0 192.168.10.254
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R2配置:
R2#show running-config
Building configuration...
Current configuration : 1198 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
enable password 123
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip tcp synwait-time 5
!
!
ip cef
no ip domain lookup
!
interface Ethernet0/0
no ip address
shutdown
half-duplex
!
interface Ethernet0/1
ip address 192.168.20.1 255.255.255.0
half-duplex
!
interface Ethernet0/2
no ip address
shutdown
half-duplex
!
interface Ethernet0/3
no ip address
shutdown
half-duplex
!
interface Ethernet1/0
no ip address
shutdown
half-duplex
!
interface Ethernet1/1
no ip address
shutdown
half-duplex
!
interface Ethernet1/2
no ip address
shutdown
half-duplex
!
interface Ethernet1/3
no ip address
shutdown
half-duplex
!
no ip http server
no ip http secure-server
ip route 192.168.10.0 255.255.255.0 192.168.20.254
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
password asd
login
ASA 防火墻的 inside區域與outside區域
