win下SSDT-Hook
阿新 • • 發佈:2018-06-23
inf fff ESS api tpi asm .com urn number 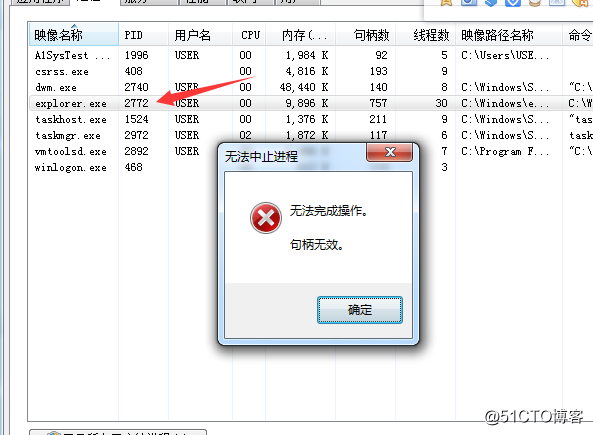

#include <ntifs.h> #pragma pack(1) //SSDTHook中,我們有2個關鍵問題: //1 怎麽找到SSDT,這個表是導出的,所以直接聲明就可以 //2 SSDT是只讀的,怎麽改 // 2.1 通過修改CR0 去掉內核層的頁保護 // 2.2 可以通過MDL重映射的方式,去修改。 typedef struct _ServiceDesriptorEntry { ULONG *ServiceTableBase; // 服務表基址 ULONG *ServiceCounterTableBase; // 計數表基址 ULONG NumberOfServices; // 表中項的個數 UCHAR *ParamTableBase; // 參數表基址 }SSDTEntry, *PSSDTEntry; #pragma pack() ULONG g_uProtectPID; // 導入SSDT NTSYSAPI SSDTEntry KeServiceDescriptorTable; VOID DriverUnload(PDRIVER_OBJECT pDriver); typedef NTSTATUS(NTAPI *NTOPENPROCESS)(__out PHANDLE ProcessHandle, __in ACCESS_MASK DesiredAccess, __in POBJECT_ATTRIBUTES ObjectAttributes, __in_opt PCLIENT_ID ClientId ); NTOPENPROCESS g_OldOpenProcess = NULL; NTSTATUS NTAPI MyNtOpenProcess(__out PHANDLE ProcessHandle, __in ACCESS_MASK DesiredAccess, __in POBJECT_ATTRIBUTES ObjectAttributes, __in_opt PCLIENT_ID ClientId ) { if ((ULONG)ClientId->UniqueProcess == g_uProtectPID) { return STATUS_ABANDONED; } return g_OldOpenProcess(ProcessHandle, DesiredAccess, ObjectAttributes, ClientId); } void InitInfo() { g_uProtectPID = 2772; g_OldOpenProcess = (NTOPENPROCESS) KeServiceDescriptorTable.ServiceTableBase[0xBE]; } void OffProtect() { __asm { //關閉內存保護 push eax; mov eax, cr0; and eax, ~0x10000; mov cr0, eax; pop eax; } } void OnProtect() { __asm { //恢復內存保護 push eax; mov eax, cr0; or eax, 0x10000; mov cr0, eax; pop eax; } } void OnHook() { //關掉頁保護 OffProtect(); KeServiceDescriptorTable.ServiceTableBase[0xBE] = (ULONG)MyNtOpenProcess; //開啟頁保護 OnProtect(); } void OffHook() { //關掉頁保護 OffProtect(); KeServiceDescriptorTable.ServiceTableBase[0xBE] = (ULONG)g_OldOpenProcess; //開啟頁保護 OnProtect(); } NTSTATUS DriverEntry(PDRIVER_OBJECT pDriver, PUNICODE_STRING pPath) { UNREFERENCED_PARAMETER(pPath); DbgBreakPoint(); InitInfo(); OnHook(); pDriver->DriverUnload = DriverUnload; return STATUS_SUCCESS; } VOID DriverUnload(PDRIVER_OBJECT pDriver) { OffHook(); UNREFERENCED_PARAMETER(pDriver); }
win下SSDT-Hook
