istio 0.8 TLS 簡單測試
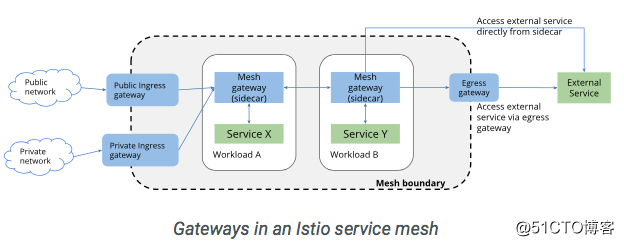
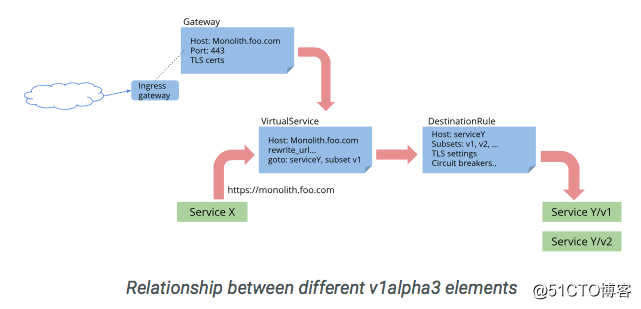
0.8版本采用了新的流量管理配置模型v1alpha3 Route API。新版本的模型添加了一些新的特性,並改善了之前版本模型:
1.Gateway
2.Virtualservice
3.DestinationRule
4.ServiceEntry
測試環境:
svc: nginx
deployment: nginx-web-de1 nginx-web-de2
gateway: nginx-gateway
Virtualservice: nginx-virtual
DestinationRule: nginx
一、先可以訪問,正常工作(訪問gateway的時候能夠跳轉到nginx的POD)
1.創建svc和deployment,一個svc引用兩個deployment,規則在virtualservice配置,比如v1百分之20,v2百分之80,或者根據cookie、user、ip等訪問v1或者v2
apiVersion: v1 kind: Service metadata: name: nginx labels: app: nginx spec: ports: - port: 80 name: http selector: app: nginx-web-de --- apiVersion: extensions/v1beta1 kind: Deployment metadata: name: nginx-web-de1 spec: replicas: 1 template: metadata: labels: app: nginx-web-de version: v1 spec: containers: - name: nginx image: nginx:v1 imagePullPolicy: IfNotPresent ports: - containerPort: 80 --- apiVersion: extensions/v1beta1 kind: Deployment metadata: name: nginx-web-de2 spec: replicas: 1 template: metadata: labels: app: nginx-web-de version: v2 spec: containers: - name: nginx image: nginx:v2 imagePullPolicy: IfNotPresent ports: - containerPort: 80
2.創建的gateway是通過api到etcd中,然後istio-ingressgateway的實例獲取,這個就相當於treafic或者nginx-ingress,然後直接訪問istio-ingressgateway
apiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: nginx-gateway spec: selector: istio: ingressgateway # use istio default controller servers: - port: number: 80 name: http protocol: HTTP hosts: - "*"
2.創建virtualservice,綁定到gateway,可以想像成nginx的虛擬主機,訪問的ip地址想象成istio-gateway
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: nginx-virtual
spec:
hosts:
- "*"
gateways:
- nginx-gateway
http:
- match:
- uri:
exact: /nginx/
route:
- destination:
host: nginx.default.svc.cluster.local
port:
number: 803.修改ingressgateway的訪問吧方式
kubectl edit svc/istio-ingressgateway -n istio-system 改成NodePort
curl 192.168.99.100:31380/nginx/ 這樣的話就是nginx-web-de1和nginx-web-de2 負載均衡,一次111一次222
docker鏡像就是簡單的 創建 nginx/index.html目錄,然後v1是"111",v2是"222",
----------------------------------------------------PS:功能實現只是能夠訪問-------------------------------------------------------------------------
我學習istio的主要要求就是 A/B test或者金絲雀發布
(1)金絲雀:利用分流 ,比如新上v2之後,我只把百分之5的流量給v2,其余還是訪問v1,根據數據分析,用戶反饋在加大流量訪問
(2)AB 根據cookie、ip、user等引流,訪問定義的版本
二、利用istio把v1百分之20 v2百分之80
1.添加DestinationRule
iapiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: nginx
spec:
host: nginx.default.svc.cluster.local
subsets:
- name: v1
labels:
version: v1 - name: v2
labels:
version: v2
2.更改virtualserviceapiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: nginx-gateway spec: selector: istio: ingressgateway # use istio default controller servers: - port:
number: 80
name: http
protocol: HTTP
hosts:-
"*"
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: nginx-virtual
spec:
hosts:
-
- "*"
"nginxgateway.yaml" 41L, 753C
hosts:
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: nginx-gateway
spec:
selector:
istio: ingressgateway # use istio default controller
servers: - port:
number: 80
name: http
protocol: HTTP
hosts:-
"*"
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: nginx-virtual
spec:
hosts:
-
- "*"
"nginxgateway.yaml" 41L, 753C
spec:
hosts: - "*"
gateways: - nginx-gateway
http: - match:
- uri:
exact: /nginx/
route: - destination:
host: nginx.default.svc.cluster.local
port:
number: 80
subset: v1
weight: 30 - destination:
host: nginx.default.svc.cluster.local
port:
number: 80
subset: v2
weight: 703.更改replace的配置 istioctl replace -f nginxgateway.yaml
- uri:
4.再次訪問的時候就是十次只有兩次到v1,virtualserver的規則可以自己隨便修改,證明配置是否生效
istio 0.8 TLS 簡單測試
