Docker倉庫建立安全認證
阿新 • • 發佈:2018-11-19
一、Docker證書
1、建立certs證書,生成伺服器私鑰
[[email protected] docker]# cd /tmp/docker/
[[email protected] docker]# mkdir certs
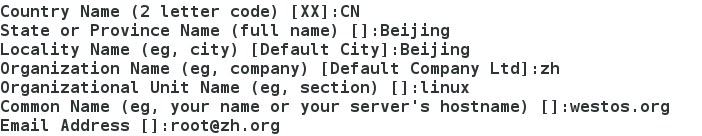
[[email protected] docker]# openssl req -newkey rsa:4096 -nodes -sha256 -keyout certs/westos.org.key -x509 -days 365 -out certs/westos.org.crt
- 填寫證書資訊
- 檢視證書、私鑰

2、啟動倉庫
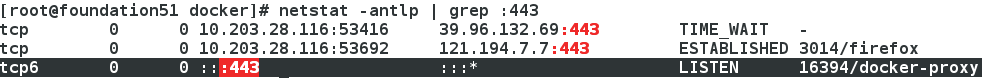
[[email protected] docker]# docker run -d \ > --restart=always \ > --name registry \ > -v `pwd`/certs:/certs \ > -e REGISTRY_HTTP_ADDR=0.0.0.0:443 \ > -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt \ > -e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key \ > -p 443:443 \ > registry:2.3.1
- 檢視443埠(https)
3、上傳westos.org/rhel7
[[email protected] docker]# docker tag rhel7 westos.org/rhel7
[[email protected] ~]# cd /etc/docker/
[[email protected] docker]# mkdir certs.d
[[email protected] docker]# cd certs.d/
[[email protected] certs.d]# mkdir westos.org
[[email protected] 4、更新CA證書
[[email protected] ~]# cd /etc/pki/ca-trust/source/anchors/
[[email protected] anchors]# cp /tmp/docker/certs/westos.org.crt .
[[email protected] anchors]# ls
westos.org.crt
[[email protected] anchors]# update-ca-trust
5、域名解析
[[email protected] ~]# vim /etc/hosts
172.25.51.250 westos.org
6、測試:訪問 https
[[email protected] anchors]# curl https://westos.org/v2/_catalog

二、Docker生產環境安全性——證書驗證倉庫客戶端
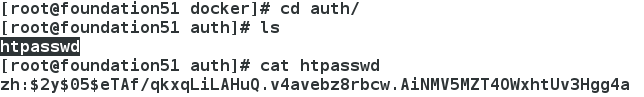
1、生成鑑權密碼檔案
[[email protected] ~]# cd /tmp/docker/
[[email protected] docker]# mkdir auth
[[email protected] docker]# docker run --entrypoint htpasswd registry:2.3.1 -Bbn zh westos > auth/htpasswd ##使用者zh,密碼westos
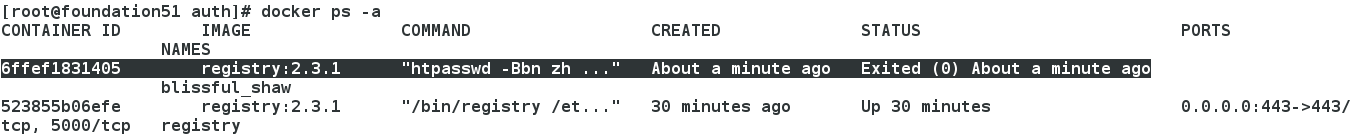
2、關閉之前的倉庫,防止衝突
[[email protected] docker]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
523855b06efe registry:2.3.1 "/bin/registry /et..." 34 minutes ago Up 34 minutes 0.0.0.0:443->443/tcp, 5000/tcp registry
[[email protected] docker]# docker rm -f registry
registry
3、啟動Registry
[[email protected] docker]# docker run -d --restart=always --name registry -v `pwd`/auth:/auth -e "REGISTRY_AUTH=htpasswd" -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd -v `pwd`/certs:/certs -e REGISTRY_HTTP_ADDR=0.0.0.0:443 -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt -e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key -p 443:443 registry:2.3.1
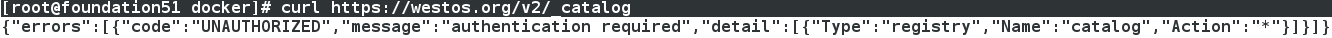
登陸驗證,curl無法看到
[[email protected] docker]# curl https://westos.org/v2/_catalog
4、使用者登入
登入認證成功後,才可進行push等操作
[[email protected] docker]# docker login westos.org
Username (zh): zh
Password:
Login Succeeded
5、上傳成功
完成registry伺服器的搭建,可以嘗試pull image到registry:
[[email protected] docker]# docker tag nginx westos.org/nginx
[[email protected] docker]# docker push westos.org/nginx
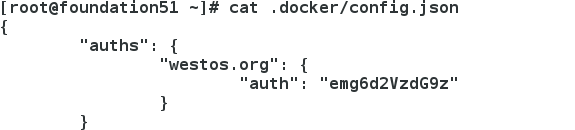
認證成功後,認證資訊儲存在當前檔案下
三、docker安全
1、一般情況,容器中操作許可權受限
[[email protected] ~]# docker run -it --name vm1 ubuntu bash
[email protected]:/# ip addr add 172.17.0.120/24 dev eth0
2、授予所有許可權
[[email protected] ~]# docker run -it --name vm2 --privileged=true ubuntu bash
[email protected]:/# ip addr add 172.17.0.120/24 dev eth0
3、授予指定許可權
[[email protected] ~]# docker run -it --name vm3 --cap-add=NET_ADMIN ubuntu bash
[email protected]:/# ip link set down eth0
[email protected]:/# ip link set up eth0
4、檢視相應許可權
[[email protected] ~]# docker inspect -f {{.HostConfig.Privileged}} vm1
false
[[email protected] ~]# docker inspect -f {{.HostConfig.Privileged}} vm2
true
[[email protected] ~]# docker inspect -f {{.HostConfig.CapAdd}} vm3
[NET_ADMIN]
[[email protected] ~]# docker inspect -f {{.HostConfig.CapAdd}} vm2
[]
