數字簽名演算法
阿新 • • 發佈:2018-12-09
數字簽名演算法主要包含RSA、DSA、ECDSA三種演算法
1. 它的訊息傳遞操作是:
- 由訊息傳送方構建密匙對,
- 由訊息傳送的一方公佈公鑰至訊息接收方,
- 訊息傳送方對訊息用私鑰做簽名處理
- 訊息接收方用公鑰對訊息做驗證
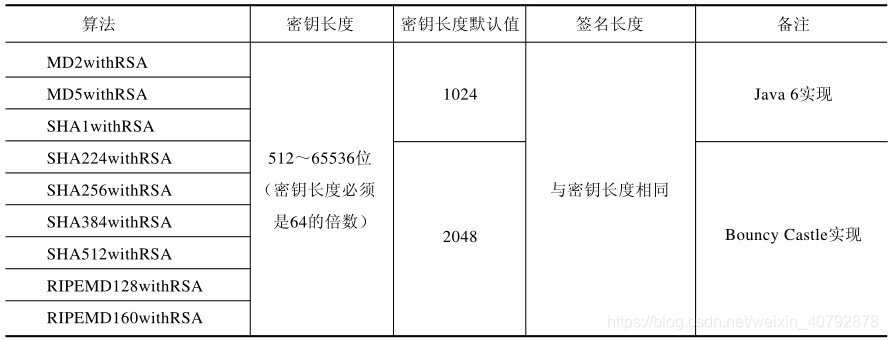
2. RSA簽名演算法主要分為MD系列和SHA系列。具體實現如下:
3. RSA的數字簽名程式碼實現:
DSA簽名實現類似,ECDSA實現相比前兩者在密匙對成功的方式上存在差別。
import org.apache.commons.codec.binary.Base64;
import java.security.