mstsc儲存使用者名稱和密碼,實現自動登入遠端桌面
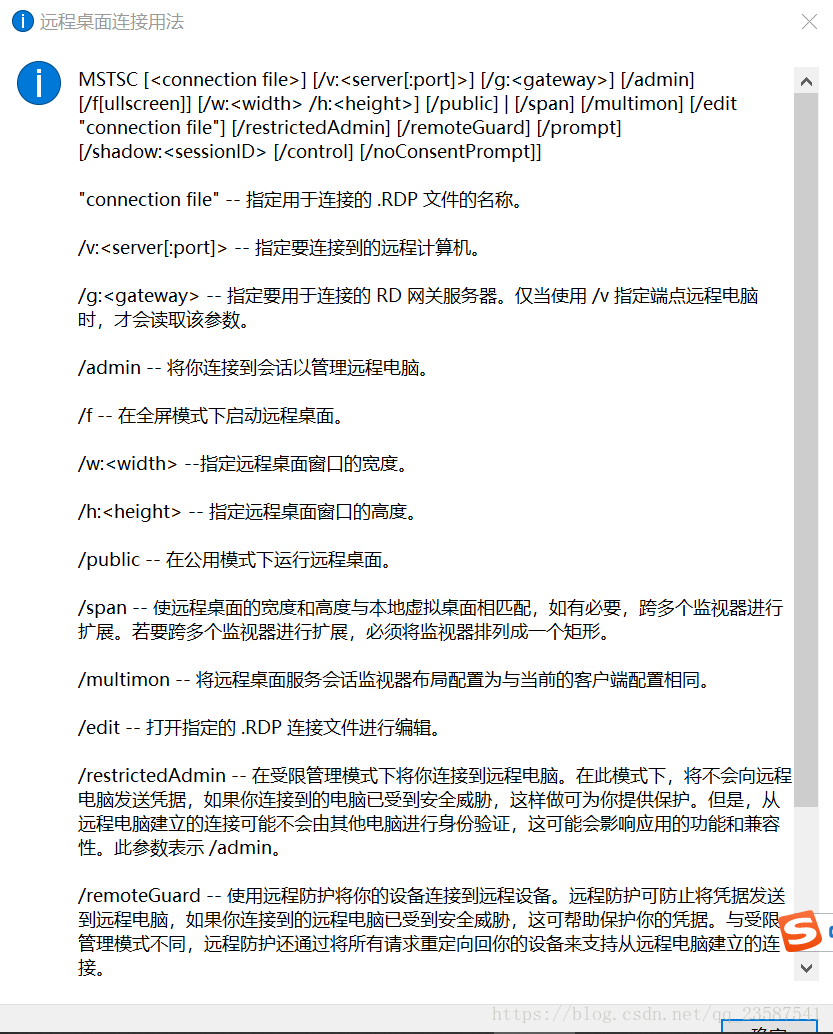
MSTSC引數說明
首先可以使用mstsc /?來檢視關於mstsc的引數說明
根據上述的命令說明,我這裡實現的bat檔案為
mstsc C:/a.rdp /console /v: xxx.xxx.xxx.xxx:3389
rdp檔案生成方法
最近由於專案需要,需要做一個rdp檔案上成,然後可以直接連遠端桌面的功能,在度娘和谷叔搜尋一番,所得甚少。閒話少說,來點乾貨:
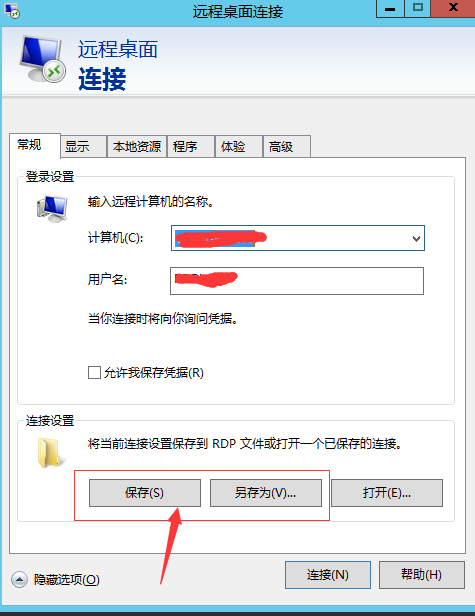
看看系統給提供的是啥樣的
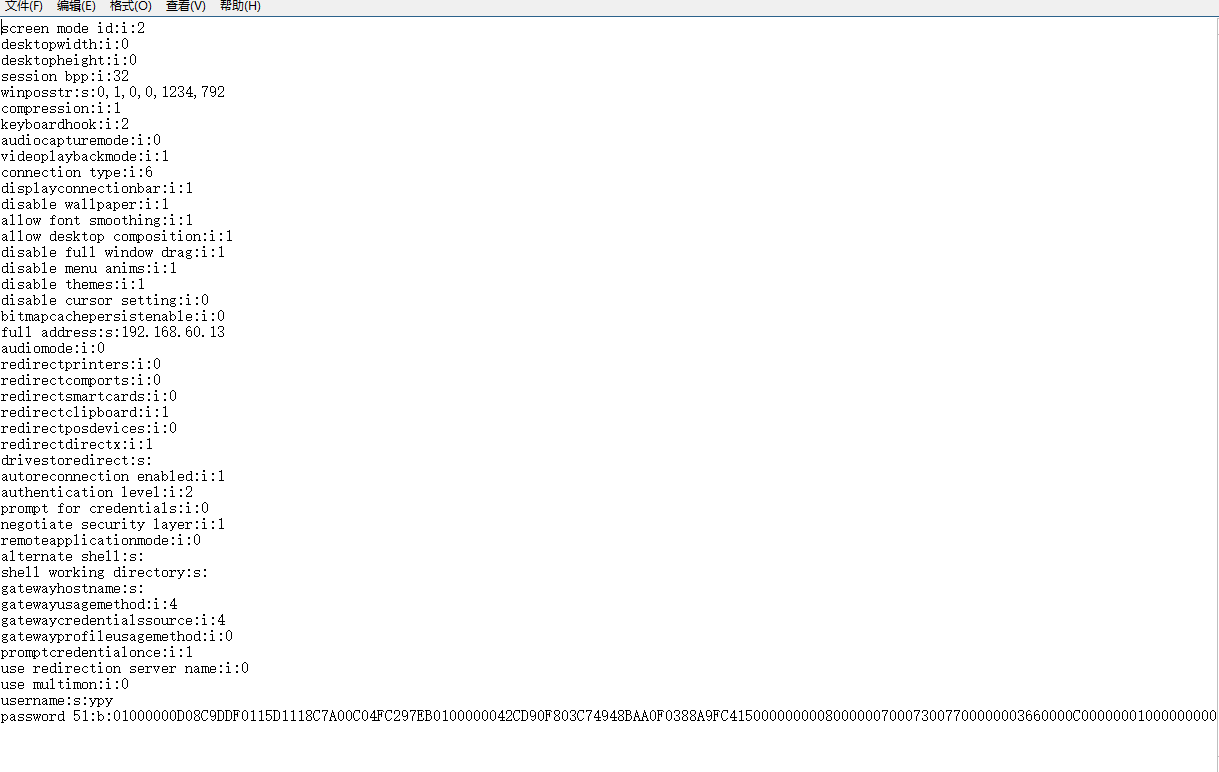
我們要關心得是 使用者名稱和密碼,其他引數可以慢慢了解,可是這個密碼是怎麼加密的呢?
使用的是一個win32裡面一個叫crypt32.dll的CryptProtectData方法,好了,關鍵的時候來咯~~~~
[StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)] internal struct DATA_BLOB { public int cbData; public IntPtr pbData; } [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)] internal struct CRYPTPROTECT_PROMPTSTRUCT { public int cbSize; public int dwPromptFlags; public IntPtr hwndApp; public string szPrompt; } [DllImport("crypt32.dll", CharSet = CharSet.Unicode, SetLastError = true)] private static extern bool CryptProtectData(ref DATA_BLOB pDataIn, string szDataDescr, ref DATA_BLOB pOptionalEntropy, IntPtr pvReserved, ref CRYPTPROTECT_PROMPTSTRUCT pPromptStruct, int dwFlags, ref DATA_BLOB pDataOut);
private static string Encrypt(string password) { byte[] bytes = Encoding.Unicode.GetBytes(password); DATA_BLOB dATA_BLOB = default(DATA_BLOB); DATA_BLOB dATA_BLOB2 = default(DATA_BLOB); DATA_BLOB dATA_BLOB3 = default(DATA_BLOB); dATA_BLOB.cbData = bytes.Length; dATA_BLOB.pbData = Marshal.AllocHGlobal(bytes.Length); Marshal.Copy(bytes, 0, dATA_BLOB.pbData, bytes.Length); dATA_BLOB3.cbData = 0; dATA_BLOB3.pbData = IntPtr.Zero; dATA_BLOB2.cbData = 0; dATA_BLOB2.pbData = IntPtr.Zero; CRYPTPROTECT_PROMPTSTRUCT cRYPTPROTECT_PROMPTSTRUCT = new CRYPTPROTECT_PROMPTSTRUCT { cbSize = Marshal.SizeOf(typeof(CRYPTPROTECT_PROMPTSTRUCT)), dwPromptFlags = 0, hwndApp = IntPtr.Zero, szPrompt = null }; if (CryptProtectData(ref dATA_BLOB, "psw", ref dATA_BLOB3, IntPtr.Zero, ref cRYPTPROTECT_PROMPTSTRUCT, 1, ref dATA_BLOB2)) { if (IntPtr.Zero != dATA_BLOB.pbData) { Marshal.FreeHGlobal(dATA_BLOB.pbData); } if (IntPtr.Zero != dATA_BLOB3.pbData) { Marshal.FreeHGlobal(dATA_BLOB3.pbData); } byte[] array = new byte[dATA_BLOB2.cbData]; Marshal.Copy(dATA_BLOB2.pbData, array, 0, dATA_BLOB2.cbData); return BitConverter.ToString(array).Replace("-", string.Empty); } return string.Empty; }
有密碼了,替換掉開始另存為的檔案裡的密碼,我們自己的rdp檔案就有咯!
附一個檔案內容方法
private static void rdpProfile(string filename, string address, string username, string password, string colordepth)
{
if (File.Exists(filename))
{
File.Delete(filename);
}
using (StreamWriter streamWriter = new StreamWriter(filename, true))
{
streamWriter.WriteLine("screen mode id:i:2");
streamWriter.WriteLine("desktopwidth:i:0");
streamWriter.WriteLine("desktopheight:i:0");
streamWriter.WriteLine("session bpp:i:" + colordepth);
streamWriter.WriteLine("winposstr:s:0,1,0,0,1234,792");
streamWriter.WriteLine("compression:i:1");
streamWriter.WriteLine("keyboardhook:i:2");
streamWriter.WriteLine("audiocapturemode:i:0");
streamWriter.WriteLine("videoplaybackmode:i:1");
streamWriter.WriteLine("connection type:i:6");
streamWriter.WriteLine("displayconnectionbar:i:1");
streamWriter.WriteLine("disable wallpaper:i:1");
streamWriter.WriteLine("allow font smoothing:i:1");
streamWriter.WriteLine("allow desktop composition:i:1");
streamWriter.WriteLine("disable full window drag:i:1");
streamWriter.WriteLine("disable menu anims:i:1");
streamWriter.WriteLine("disable themes:i:1");
streamWriter.WriteLine("disable cursor setting:i:0");
streamWriter.WriteLine("bitmapcachepersistenable:i:0");
streamWriter.WriteLine("full address:s:" + address);
streamWriter.WriteLine("audiomode:i:0");
streamWriter.WriteLine("redirectprinters:i:0");
streamWriter.WriteLine("redirectcomports:i:0");
streamWriter.WriteLine("redirectsmartcards:i:0");
streamWriter.WriteLine("redirectclipboard:i:1");
streamWriter.WriteLine("redirectposdevices:i:0");
streamWriter.WriteLine("redirectdirectx:i:1");
streamWriter.WriteLine("drivestoredirect:s:");
streamWriter.WriteLine("autoreconnection enabled:i:1");
streamWriter.WriteLine("authentication level:i:2");
streamWriter.WriteLine("prompt for credentials:i:0");
streamWriter.WriteLine("negotiate security layer:i:1");
streamWriter.WriteLine("remoteapplicationmode:i:0");
streamWriter.WriteLine("alternate shell:s:");
streamWriter.WriteLine("shell working directory:s:");
streamWriter.WriteLine("gatewayhostname:s:");
streamWriter.WriteLine("gatewayusagemethod:i:4");
streamWriter.WriteLine("gatewaycredentialssource:i:4");
streamWriter.WriteLine("gatewayprofileusagemethod:i:0");
streamWriter.WriteLine("promptcredentialonce:i:1");
streamWriter.WriteLine("use redirection server name:i:0");
streamWriter.WriteLine("use multimon:i:0");
if (!string.IsNullOrEmpty(username))
{
streamWriter.WriteLine("username:s:" + username);
}
if (!string.IsNullOrEmpty(password))
{
streamWriter.WriteLine("password 51:b:" + password);
}
}
}————————————————————————————————————————————————————————————————————————————————————————————————————————————————
更改mstsc遠端埠方法
Windows 系統中的遠端終端服務是一項功能非常強大的服務,同時也成了入侵者長駐主機的通道,入侵者可以利用一些手段得到管理員賬號和密碼併入侵主機。下面,我們來看看如何通過修改預設埠,防範黑客入侵。
眾所周知,遠端終端服務基於埠3389。入侵者一般先掃描主機開放埠,一旦發現其開放了3389埠,就會進行下一步的入侵,所以我們只需要修改該務預設埠就可以避開大多數入侵者的耳目。
步驟:
1、開啟“開始→執行”,輸入“regedit”,開啟登錄檔,進入以下路徑:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds\tcp,看見PortNamber值了嗎?其預設值是3389,修改成所希望的埠即可,例如6111。
2、再開啟
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentContro1Set\Control\Tenninal Server\WinStations\RDP\Tcp,將PortNumber的值(預設是3389)修改成埠6111。
3、修改完畢,重新啟動電腦,以後遠端登入的時候使用埠6111就可以了。