第一次使用acme.sh 手動生成證書(DNS手動模式)
阿新 • • 發佈:2018-12-13
參考:https://github.com/Neilpang/acme.sh/wiki/How-to-issue-a-cert
這種方法官方是不推薦的,不能自動續期(即需要手動續簽)
acme.sh的DNS手動模式生成證書
應該需要一個有公網ip的機器,至少我是這樣,回頭我再考證一下。
2018年12月10日測試:可以在虛擬機器上使用,不需要公網IP
一、安裝
curl https://get.acme.sh | sh二、確保伺服器的nginx和apache沒有執行,別佔用80埠(DNS手動模式不需要)
三、動手
命令就一行,出現了報錯,要求在dns解析里加入兩行txt解析
[email protected]:~/.acme.sh# acme.sh --issue -d bombstory.com -d *.bombstory.com --dns dns-01 [Wed Dec 5 11:58:54 UTC 2018] Multi domain='DNS:bombstory.com,DNS:*.bombstory.com' [Wed Dec 5 11:58:54 UTC 2018] Getting domain auth token for each domain [Wed Dec 5 11:58:56 UTC 2018] Getting webroot for domain='bombstory.com' [Wed Dec 5 11:58:56 UTC 2018] Getting webroot for domain='*.bombstory.com' [Wed Dec 5 11:58:57 UTC 2018] Can not find dns api hook for: dns-01 [Wed Dec 5 11:58:57 UTC 2018] You need to add the txt record manually. [Wed Dec 5 11:58:57 UTC 2018] Add the following TXT record: [Wed Dec 5 11:58:57 UTC 2018] Domain: '_acme-challenge.bombstory.com' [Wed Dec 5 11:58:57 UTC 2018] TXT value: 'nuV36UCKAvU3KiWLFkAxNIQAVahmmnC5witMoOrk7MQ' [Wed Dec 5 11:58:57 UTC 2018] Please be aware that you prepend _acme-challenge. before your domain [Wed Dec 5 11:58:57 UTC 2018] so the resulting subdomain will be: _acme-challenge.bombstory.com [Wed Dec 5 11:58:57 UTC 2018] Can not find dns api hook for: dns-01 [Wed Dec 5 11:58:57 UTC 2018] You need to add the txt record manually. [Wed Dec 5 11:58:57 UTC 2018] Add the following TXT record: [Wed Dec 5 11:58:57 UTC 2018] Domain: '_acme-challenge.bombstory.com' [Wed Dec 5 11:58:57 UTC 2018] TXT value: 'HKXRN73W33CZnDCsUgXxCDDrgsn5xMagUPaMZl4yjkU' [Wed Dec 5 11:58:57 UTC 2018] Please be aware that you prepend _acme-challenge. before your domain [Wed Dec 5 11:58:57 UTC 2018] so the resulting subdomain will be: _acme-challenge.bombstory.com [Wed Dec 5 11:58:57 UTC 2018] Please add the TXT records to the domains, and re-run with --renew. [Wed Dec 5 11:58:57 UTC 2018] Please add '--debug' or '--log' to check more details. [Wed Dec 5 11:58:57 UTC 2018] See: https://github.com/Neilpang/acme.sh/wiki/How-to-debug-acme.sh
四、解析DNS
如下圖:
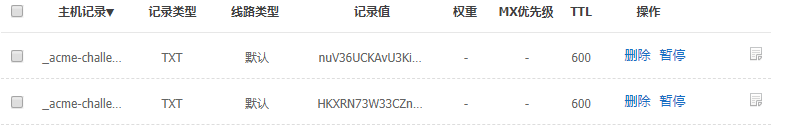
五、稍等一會兒,再次執行命令,這次執行後面要加--renew引數
[email protected]:~/.acme.sh# acme.sh --issue -d bombstory.com -d *.bombstory.com --dns dns-01 --renew [Wed Dec 5 12:02:09 UTC 2018] Renew: 'bombstory.com' [Wed Dec 5 12:02:10 UTC 2018] Multi domain='DNS:bombstory.com,DNS:*.bombstory.com' [Wed Dec 5 12:02:10 UTC 2018] Getting domain auth token for each domain [Wed Dec 5 12:02:10 UTC 2018] Verifying:bombstory.com [Wed Dec 5 12:02:14 UTC 2018] Success [Wed Dec 5 12:02:14 UTC 2018] Verifying:*.bombstory.com [Wed Dec 5 12:02:17 UTC 2018] Pending [Wed Dec 5 12:02:20 UTC 2018] Success [Wed Dec 5 12:02:20 UTC 2018] Verify finished, start to sign. [Wed Dec 5 12:02:22 UTC 2018] Cert success. -----BEGIN CERTIFICATE----- ......此處省略一大段無用輸出...... -----END CERTIFICATE----- [Wed Dec 5 12:02:22 UTC 2018] Your cert is in /root/.acme.sh/bombstory.com/bombstory.com.cer [Wed Dec 5 12:02:22 UTC 2018] Your cert key is in /root/.acme.sh/bombstory.com/bombstory.com.key [Wed Dec 5 12:02:22 UTC 2018] The intermediate CA cert is in /root/.acme.sh/bombstory.com/ca.cer [Wed Dec 5 12:02:22 UTC 2018] And the full chain certs is there: /root/.acme.sh/bombstory.com/fullchain.cer
六、其中,需要用到的檔案有兩個:
一個key:/root/.acme.sh/bombstory.com/bombstory.com.key
一個證書:/root/.acme.sh/bombstory.com/fullchain.cer
2018年12月10日更新
使用DNS手動模式生成的證書續簽:
一、兩條DNS解析記錄別刪
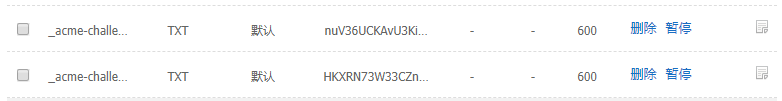
二、該證書是4天前做的,還有85天
[email protected]:~$ zabbix_get -s 127.0.0.1 -k https.remaining[bombstory.com]
85三、手動續簽:
[email protected]:~/.acme.sh# acme.sh --renew -d bombstory.com --force
[Mon Dec 10 05:14:54 UTC 2018] Renew: 'bombstory.com'
[Mon Dec 10 05:14:55 UTC 2018] Multi domain='DNS:bombstory.com,DNS:*.bombstory.com'
[Mon Dec 10 05:14:55 UTC 2018] Getting domain auth token for each domain
[Mon Dec 10 05:14:57 UTC 2018] Getting webroot for domain='bombstory.com'
[Mon Dec 10 05:14:57 UTC 2018] Getting webroot for domain='*.bombstory.com'
[Mon Dec 10 05:14:57 UTC 2018] bombstory.com is already verified, skip dns-01.
[Mon Dec 10 05:14:57 UTC 2018] *.bombstory.com is already verified, skip dns-01.
[Mon Dec 10 05:14:57 UTC 2018] Verify finished, start to sign.
[Mon Dec 10 05:15:00 UTC 2018] Cert success.
-----BEGIN CERTIFICATE-----
......
-----END CERTIFICATE-----
[Mon Dec 10 05:15:00 UTC 2018] Your cert is in /root/.acme.sh/bombstory.com/bombstory.com.cer
[Mon Dec 10 05:15:00 UTC 2018] Your cert key is in /root/.acme.sh/bombstory.com/bombstory.com.key
[Mon Dec 10 05:15:00 UTC 2018] The intermediate CA cert is in /root/.acme.sh/bombstory.com/ca.cer
[Mon Dec 10 05:15:00 UTC 2018] And the full chain certs is there: /root/.acme.sh/bombstory.com/fullchain.cer
[email protected]:~/.acme.sh# sz /root/.acme.sh/bombstory.com/fullchain.cer四、替換證書檔案,reload nginx
[email protected]:/etc/nginx/ssl# ls -l
total 12
-rw-r--r-- 1 root root 1675 Dec 5 19:51 bombstory.com.key
-rw-r--r-- 1 root root 3575 Dec 10 13:15 fullchain.cer
-rw-r--r-- 1 root root 3575 Dec 5 20:02 fullchain.cerbak
[email protected]:/etc/nginx/ssl# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[email protected]:/etc/nginx/ssl# nginx -s reload五、再次檢視,成功
[email protected]:~$ zabbix_get -s 127.0.0.1 -k https.remaining[bombstory.com]
89
