IPSec的高可用性技術
IPSec VPN的高可用性技術:
①、DPD(Dead Peer Detection)對等體檢測
——旨在檢查有問題的IPSec VPN網路,並快速的切換到備用閘道器
②、RRI(Reverse Route Injection)反向路由注入
——解決高可用性的路由問題
****************DPD**************
DPD的工作模式:
週期性的工作模式——設定一個定時器,路由器會按照這個定時器所設定的時間週期性的傳送DPD資料包; 好處在於快速的檢測到對等體的問題;缺點是這樣週期的傳送DPD會消耗較多的裝置資源和網路資源
按需工作模式——DPD預設的工作模式,這樣的情況下,DPD資訊會基於流量形式的不同而採取不同的傳送方式。 好處是需要傳送DPD的時候才發,節約資源和網路頻寬;缺點是檢測到IPSec VPN閘道器故障所需時間稍長。
實驗拓撲: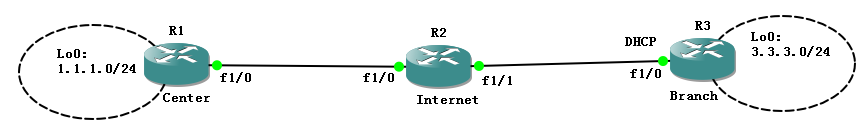
預設配置完成,此時是可以建立起IPSec VPN的:
Site2#sho cry en conn active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 10 13 23.1.1.3
2 IPsec DES+MD5 10 0 0 23.1.1.3
1001 IKE SHA+DES 0 0 0 23.1.1.3
那麼我們來看一下在沒有DPD功能的時候:
Site1#debug crypto isakmp
Crypto ISAKMP debugging is on
Internet(config)#int f1/0
Internet(config-if)#shu
Site1#ping 3.3.3.3 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.....
Success rate is 0 percent (0/5)
Site1#sho cry en conn active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 8 9 12.1.1.1
2 IPsec DES+MD5 19 0 0 12.1.1.1
1001 IKE SHA+DES 0 0 0 12.1.1.1
這說明沒有啟用DPD技術的時候,IPSec VPN無法探測有問題的閘道器,因此會繼續使用又問題的IPSec SA加密資料包,接下來再看啟用了DPD的情況:
Site1(config)#crypto isakmp keepalive ?
<10-3600> Number of seconds between keep alives
Site1(config)#crypto isakmp keepalive 10 periodic
Site2(config)#crypto isakmp keepalive 10 periodic
Site1/2#cle crypto isakmp
Site1/2#cle crypto sa
Internet(config)#int f1/0
Internet(config-if)#no shu
此時Site1和Site2之間又恢復了通訊:
Site1#ping 3.3.3.3 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 184/208/240 ms
那麼在來看一下DPD檢測失效閘道器的效果:
Apr 22 23:56:20.535: ISAKMP:(1002):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1746747408, message ID = 1135002381
*Apr 22 23:56:20.535: ISAKMP:(1002): seq. no 0x1B47B85D
*Apr 22 23:56:20.535: ISAKMP:(1002): sending packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:20.535: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:20.539: ISAKMP:(1002):purging node 1135002381
*Apr 22 23:56:20.539: ISAKMP:(1002):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_IM_ALIVE
*Apr 22 23:56:20.543: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Site1#
*Apr 22 23:56:20.767: ISAKMP:(1002):purging node 593664099
Site1#
*Apr 22 23:56:22.539: ISAKMP:(1002):DPD incrementing error counter (1/5)
*Apr 22 23:56:22.539: ISAKMP: set new node 511611758 to QM_IDLE
*Apr 22 23:56:22.539: ISAKMP:(1002):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1746747408, message ID = 511611758
*Apr 22 23:56:22.539: ISAKMP:(1002): seq. no 0x1B47B85E
*Apr 22 23:56:22.539: ISAKMP:(1002): sending packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:22.543: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:22.543: ISAKMP:(1002):purging node 511611758
*Apr 22 23:56:22.547: ISAKMP:(1002):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
Site1#
*Apr 22 23:56:22.547: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Site1#
*Apr 22 23:56:24.543: ISAKMP:(1002):DPD incrementing error counter (2/5)
*Apr 22 23:56:24.543: ISAKMP: set new node -2042738143 to QM_IDLE
*Apr 22 23:56:24.547: ISAKMP:(1002):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1746747408, message ID = -2042738143
*Apr 22 23:56:24.547: ISAKMP:(1002): seq. no 0x1B47B85F
*Apr 22 23:56:24.551: ISAKMP:(1002): sending packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:24.551: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:24.551: ISAKMP:(1002):purging node -2042738143
*Apr 22 23:56:24.555: ISAKMP:(1002):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
Site1#
*Apr 22 23:56:24.555: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Site1#
*Apr 22 23:56:26.555: ISAKMP:(1002):DPD incrementing error counter (3/5)
*Apr 22 23:56:26.555: ISAKMP: set new node 1264419706 to QM_IDLE
*Apr 22 23:56:26.559: ISAKMP:(1002):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1746747408, message ID = 1264419706
*Apr 22 23:56:26.559: ISAKMP:(1002): seq. no 0x1B47B860
*Apr 22 23:56:26.559: ISAKMP:(1002): sending packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:26.563: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:26.563: ISAKMP:(1002):purging node 1264419706
*Apr 22 23:56:26.567: ISAKMP:(1002):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
Site1#
*Apr 22 23:56:26.567: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Site1#
*Apr 22 23:56:28.007: ISAKMP:(1002):purging node 519630341
*Apr 22 23:56:28.567: ISAKMP:(1002):DPD incrementing error counter (4/5)
*Apr 22 23:56:28.567: ISAKMP: set new node 2041023417 to QM_IDLE
*Apr 22 23:56:28.571: ISAKMP:(1002):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1746747408, message ID = 2041023417
*Apr 22 23:56:28.571: ISAKMP:(1002): seq. no 0x1B47B861
*Apr 22 23:56:28.571: ISAKMP:(1002): sending packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:28.575: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:28.575: ISAKMP:(1002):purging node 2041023417
Site1#
*Apr 22 23:56:28.579: ISAKMP:(1002):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
*Apr 22 23:56:28.579: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Site1#
*Apr 22 23:56:30.579: ISAKMP:(1002):DPD incrementing error counter (5/5)
*Apr 22 23:56:30.579: ISAKMP:(1002):peer 23.1.1.3 not responding!
*Apr 22 23:56:30.583: ISAKMP:(1002):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
*Apr 22 23:56:30.583: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Apr 22 23:56:30.595: ISAKMP (1002): No more ipsec tunnels for this SA.
*Apr 22 23:56:30.599: ISAKMP: set new node 1589052764 to QM_IDLE
*Apr 22 23:56:30.603: ISAKMP:(1002): sending packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:30.603: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:30.607: ISAKMP:(1002):purging node 1589052764
*Apr 22 23:56:30.607: ISAKMP:(1002):Input = IKE_MESG_FROM_IPSEC, IKE_PHASE2_DEL
*Apr 22 23:56:30.611: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Apr 22 23:56:30.619: ISAKMP: set new node 1168250615 to QM_IDLE
*Apr 22 23:56:30.619: ISAKMP:(1002): send
Site1#ing packet to 23.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Apr 22 23:56:30.623: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Apr 22 23:56:30.623: ISAKMP:(1002):purging node 1168250615
*Apr 22 23:56:30.627: ISAKMP:(1002):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Apr 22 23:56:30.627: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_DEST_SA
*Apr 22 23:56:30.635: ISAKMP:(1002):deleting SA reason "No reason" state (I) QM_IDLE (peer 23.1.1.3)
*Apr 22 23:56:30.635: ISAKMP: Unlocking peer struct 0x68665020 for isadb_mark_sa_deleted(), count 0
*Apr 22 23:56:30.639: ISAKMP: Deleting peer node by peer_reap for 23.1.1.3: 68665020
*Apr 22 23:56:30.643: ISAKMP:(1002):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Apr 22 23:56:30.643: ISAKMP:(1002):Old State = IKE_DEST_SA New State = IKE_DEST_SA
*Apr 22 23:56:30.887: ISAKMP:(1002):purging node -1414911362
可以看到的是:Site1上的DPD中,如果Site1週期性的傳送的DPD資訊沒有得到遠端的確認,那麼會連續傳送5次,若5次都沒有遠端的確認。site1馬上就會清楚本地的IPSec和ISAKMP安全關聯:
Site1#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
Site2#sho cry en conn active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
以上的配置DPD會週期的傳送。DPD按需工作模式會基於流量形式的不同而採取不同的傳送方式,若IPSec VPN有持續的流量加密傳送,並且還能持續解密對端發來的資料,那麼此時,按需工作模式就會認為一切正常,不需要傳送DPD:而在當一個數據加密傳送出去,在一定的時間內沒有收到任何的解密資料包額情況下,DPD才會懷疑IPSec VPN出現問題,傳送DPD。若很快收到了DPD確認,那麼表示遠端正常,若一定的時間內沒有收到DPD確認,那麼也是5次之後,刪除所有安全連線。
下面是按需傳送的配置:
Site1(config)#no crypto isakmp keepalive 10 periodic
Site1(config)#crypto isakmp keepalive 10 //加密資料發出後10秒沒有收到解密資料包,就傳送DPD進行探測
Site2(config)#no crypto isakmp keepalive 10 periodic
Site2(config)#crypto isakmp keepalive 10
值得注意的是:在10秒後連續5次Site1刪除本地的所有安全關聯,但是在Site2上還是存在,除非Site2發出加密資料包,10秒內未得到解密資料包。
**************RRI********************
什麼時候注入(動態產生)這一條路由呢?
在產生IPSec SA 的同時也產生這條路由,在IPSec SA消失的時候,也隨之消失。由RRI產生的路由,其目的網路為遠端通訊網路,下一跳為遠端加密點(也可以認為是隧道的終點)。
下面是測試RRI的工作特性,拓撲如下: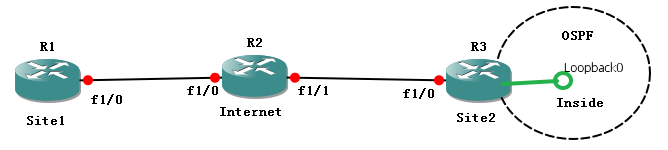
預設經典的IPSec VPN以及建立成功:
Site2#sho cry en connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 3 4 23.1.1.3
2 IPsec DES+MD5 3 0 0 23.1.1.3
1001 IKE SHA+DES 0 0 0 23.1.1.3
Site2(config)#crypto map cisco 10 ipsec-isakmp
Site2(config-crypto-map)#reverse-route
Site2(config-crypto-map)#set reverse-route tag 10
This will remove previously installed VPN routes and SAs
Site2(config-crypto-map)#exi
Site2(config)#route-map RRI permit 10
Site2(config-route-map)#match tag 10
Site2(config-route-map)#exi
Site2(config)#int f1/1
Site2(config-if)#ip add 35.1.1.3 255.255.255.0
Site2(config-if)#no shu
Site2(config-if)#int lo0
Site2(config-if)#no ip add
Site2(config-if)#end
Site2#conf t
Site2(config)#router os 1
Site2(config-router)#router-id 2.2.2.2
Site2(config-router)#net 35.1.1.0 0.0.0.255 a 0
Site2(config-router)#end
R5(config)#int f1/0
R5(config-if)#ip add 35.1.1.5 255.255.255.0
R5(config-if)#no sh
R5(config)#int lo0
R5(config-if)#ip add 3.3.3.3 255.255.255.0
R5(config-if)#router os 1
R5(config-router)#router-id 5.5.5.5
R5(config-router)#net 0.0.0.0 255.255.255.255 a 0
R5(config-router)#exi
現在的情況是在R5上沒有R1的1.1.1.1的路由,因為反向注入還沒有實施,所以即使匹配上了感興趣流,但是還是不能通訊
Site1#cle access-list counters
Site1#ping 3.3.3.3 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.....
Success rate is 0 percent (0/5)
Site2#sho access-lists
Extended IP access list vpn
10 permit ip 3.3.3.0 0.0.0.255 1.1.1.0 0.0.0.255 (4 matches)
下面是將RRI注入OSPF網路的配置:
Site2(config)#router os 1
Site2(config-router)#redistribute static route-map RRI subnets
Site2#sho ip ro static
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 23.1.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 23.1.1.2
1.0.0.0/24 is subnetted, 1 subnets
S 1.1.1.0 [1/0] via 12.1.1.1
可以看到的是這裡的RRI產生的靜態是下一跳為12.1.1.1的,就是peer的加密點的地址
Site1#ping 3.3.3.3 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 328/365/408 ms
Site1#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
7 IPsec DES+MD5 0 5 5 12.1.1.1
8 IPsec DES+MD5 5 0 0 12.1.1.1
1002 IKE SHA+DES 0 0 0 12.1.1.1
此時在R5的路由表中肯定有OE2的OSPF路由了:
R5#sho ip ro ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
O E2 1.1.1.0 [110/20] via 35.1.1.3, 00:00:03, FastEthernet1/0
