kubernetes-ingress(十)
ingress
https://kubernetes.io/docs/concepts/services-networking/ingress/
pod與ingress的關係
•通過label-selector相關聯
•通過Ingress Controller實現Pod的負載均衡
-支援TCP/UDP 4層和HTTP 7層
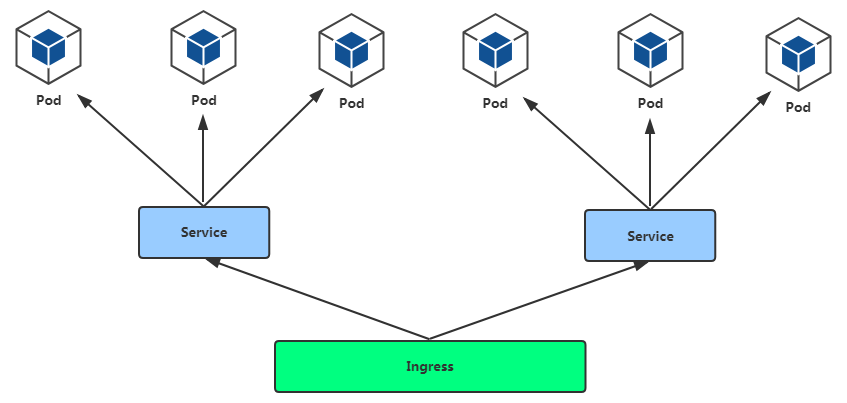
Ingress 組成?
ingress controller:將新加入的Ingress轉化成Nginx的配置檔案並使之生效
ingress服務:將Nginx的配置抽象成一個Ingress物件,每新增一個新的服務只需寫一個新的Ingress的yaml檔案即可
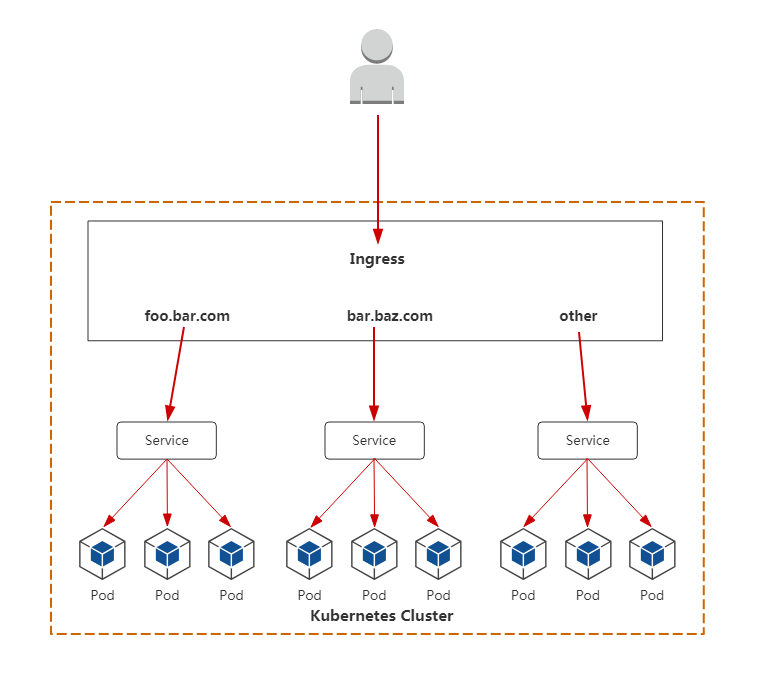
Ingress 工作原理?
ingress controller通過和kubernetes api互動,動態的去感知叢集中ingress規則變化,
然後讀取它,按照自定義的規則,規則就是寫明瞭哪個域名對應哪個service,生成一段nginx配置,
再寫到nginx-ingress-control的pod裡,這個Ingress controller的pod裡執行著一個Nginx服務,控制器會把生成的nginx配置寫入/etc/nginx.conf檔案中,
然後reload一下使配置生效。
以此達到域名分配置和動態更新的問題。
ingress部署文件
https://github.com/kubernetes/ingress-nginx/blob/master/docs/deploy/index.md
下載yaml檔案,修改使用宿主機網路 hostNetwork: true
[[email protected] ingress]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/mandatory.yaml [[email protected] ingress]# kubectl apply -f mandatory.yaml namespace/ingress-nginx created configmap/nginx-configuration created configmap/tcp-services created configmap/udp-services created serviceaccount/nginx-ingress-serviceaccount created clusterrole.rbac.authorization.k8s.io/nginx-ingress-clusterrole created role.rbac.authorization.k8s.io/nginx-ingress-role created rolebinding.rbac.authorization.k8s.io/nginx-ingress-role-nisa-binding created clusterrolebinding.rbac.authorization.k8s.io/nginx-ingress-clusterrole-nisa-binding created deployment.extensions/nginx-ingress-controller created
檢視ingress部署的node節點,使用宿主機網路會在node監聽80和443埠
[[email protected]master1 ingress]# kubectl get ns NAME STATUS AGE default Active 6d20h ingress-nginx Active 27m kube-public Active 6d20h kube-system Active 6d20h [[email protected]-master1 ingress]# kubectl get pods -n ingress-nginx -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES nginx-ingress-controller-5c98c674b8-l9ft2 1/1 Running 0 28m 192.168.0.125 192.168.0.125 <none> <none>
[[email protected] ~]# netstat -tnlp |egrep "80|443" tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 2358/nginx: master tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 2358/nginx: master tcp 0 0 0.0.0.0:18080 0.0.0.0:* LISTEN 2358/nginx: master tcp6 0 0 :::80 :::* LISTEN 2358/nginx: master tcp6 0 0 :::443 :::* LISTEN 2358/nginx: master tcp6 0 0 :::18080 :::* LISTEN 2358/nginx: master
準備後端服務

[[email protected] ingress]# cat deploy-demo.yaml #建立service為myapp apiVersion: v1 kind: Service metadata: name: myapp namespace: default spec: selector: app: myapp release: canary ports: - name: http targetPort: 80 port: 80 --- #建立後端服務的deployment apiVersion: apps/v1 kind: Deployment metadata: name: myapp-backend-pod namespace: default spec: replicas: 3 selector: matchLabels: app: myapp release: canary template: metadata: labels: app: myapp release: canary spec: containers: - name: myapp image: ikubernetes/myapp:v2 ports: - name: http containerPort: 80 [[email protected]-master1 ingress]# kubectl apply -f deploy-demo.yaml service/myapp created deployment.apps/myapp-backend-pod created [[email protected]-master1 ingress]# kubectl get pod,svc NAME READY STATUS RESTARTS AGE pod/myapp-backend-pod-6b56d98b6b-27vvs 1/1 Running 0 12s pod/myapp-backend-pod-6b56d98b6b-6rq8w 1/1 Running 0 12s pod/myapp-backend-pod-6b56d98b6b-ndbm6 1/1 Running 0 12s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/kubernetes ClusterIP 10.0.0.1 <none> 443/TCP 6d21h service/myapp ClusterIP 10.0.0.79 <none> 80/TCP 12s [[email protected]-node01 ~]# curl 10.0.0.79 Hello MyApp | Version: v2 | <a href="hostname.html">Pod Name</a>View Code
配置ingress規則
[[email protected] ingress]# vim ingress-myapp.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: simple-fanout-example annotations: nginx.ingress.kubernetes.io/rewrite-target: / spec: rules: - host: foo.bar.com http: paths: - path: / backend: serviceName: myapp servicePort: 80 [[email protected]-master1 ingress]# kubectl apply -f ingress-myapp.yaml ingress.extensions/simple-fanout-example created [[email protected]-master1 ingress]# kubectl get ingress NAME HOSTS ADDRESS PORTS AGE simple-fanout-example foo.bar.com 80 10s
設定域名解析到ip,即可訪問域名
[[email protected]master1 ingress]# curl foo.bar.com Hello MyApp | Version: v2 | <a href="hostname.html">Pod Name</a>
檢視詳細資訊
[[email protected] ingress]# kubectl describe ingress simple-fanout-example Name: simple-fanout-example Namespace: default Address: Default backend: default-http-backend:80 (<none>) Rules: Host Path Backends ---- ---- -------- foo.bar.com / myapp:80 (<none>) Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"extensions/v1beta1","kind":"Ingress","metadata":{"annotations":{"nginx.ingress.kubernetes.io/rewrite-target":"/"},"name":"simple-fanout-example","namespace":"default"},"spec":{"rules":[{"host":"foo.bar.com","http":{"paths":[{"backend":{"serviceName":"myapp","servicePort":80},"path":"/"}]}}]}} nginx.ingress.kubernetes.io/rewrite-target: / Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 3m58s nginx-ingress-controller Ingress default/simple-fanout-example
進入nginx-ingress-controller進行檢視是否注入了nginx的配置
[[email protected] ingress]# kubectl get pod -n ingress-nginx NAME READY STATUS RESTARTS AGE nginx-ingress-controller-5c98c674b8-l9ft2 1/1 Running 0 67m [[email protected]-master1 ingress]# kubectl exec -n ingress-nginx -it nginx-ingress-controller-5c98c674b8-l9ft2 bash www[email protected]:/etc/nginx$ cat nginx.conf ........ ## start server foo.bar.com server { server_name foo.bar.com ; listen 80; listen [::]:80; set $proxy_upstream_name "-"; location / { set $namespace "default"; set $ingress_name "simple-fanout-example"; set $service_name "myapp"; set $service_port "80"; set $location_path "/"; rewrite_by_lua_block { balancer.rewrite() } access_by_lua_block { } header_filter_by_lua_block { }
構建TLS站點
準備證書
[[email protected] ingress]# openssl genrsa -out tls.key 2048 Generating RSA private key, 2048 bit long modulus ..................................................................................+++ ........................+++ e is 65537 (0x10001) [[email protected]-master1 ingress]# openssl req -new -x509 -key tls.key -out tls.crt -subj /C=CN/ST=Beijing/L=Beijing/O=DevOps/CN=sslexample.foo.com
建立secret
[[email protected] ingress]# kubectl create secret tls sslexample-foo-com --cert=tls.crt --key=tls.key secret/sslexample-foo-com created [[email protected]master1 ingress]# kubectl get secret NAME TYPE DATA AGE default-token-7vs6s kubernetes.io/service-account-token 3 6d22h registry-pull-secret kubernetes.io/dockerconfigjson 1 5d1h sslexample-foo-com kubernetes.io/tls 2 28s
[[email protected] ingress]# kubectl describe secret sslexample-foo-com Name: sslexample-foo-com Namespace: default Labels: <none> Annotations: <none> Type: kubernetes.io/tls Data ==== tls.crt: 1298 bytes tls.key: 1675 bytes
建立ingress
[[email protected] ingress]# vim ingress-https.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: tls-example-ingress spec: tls: - hosts: - sslexample.foo.com secretName: sslexample-foo-com rules: - host: sslexample.foo.com http: paths: - path: / backend: serviceName: myapp servicePort: 80 [[email protected]-master1 ingress]# kubectl apply -f ingress-https.yaml ingress.extensions/tls-example-ingress created [[email protected]-master1 ingress]# kubectl get ingress NAME HOSTS ADDRESS PORTS AGE simple-fanout-example foo.bar.com 80 59m tls-example-ingress sslexample.foo.com 80, 443 29s [[email protected]-master1 ingress]# kubectl describe ingress tls-example-ingress Name: tls-example-ingress Namespace: default Address: Default backend: default-http-backend:80 (<none>) TLS: sslexample-foo-com terminates sslexample.foo.com Rules: Host Path Backends ---- ---- -------- sslexample.foo.com / myapp:80 (<none>) Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"extensions/v1beta1","kind":"Ingress","metadata":{"annotations":{},"name":"tls-example-ingress","namespace":"default"},"spec":{"rules":[{"host":"sslexample.foo.com","http":{"paths":[{"backend":{"serviceName":"myapp","servicePort":80},"path":"/"}]}}],"tls":[{"hosts":["sslexample.foo.com"],"secretName":"sslexample-foo-com"}]}} Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 72s nginx-ingress-controller Ingress default/tls-example-ingress
訪問測試


