The Tech Jargon in Mueller's Russian Indictment, Explained
Spearphishing: how the hackers broke in
Deputy Attorney General Rod Rosenstein alleged in his wonderfully-concise press conference (worth watching!) that the Russian hackers used a technique called spearphishingto get access to the email account of the Clinton campaign chairman, John Podesta.
You might have heard of phishing
Based on the contents of the indictment (page 6, if you’re following along at home
According to the indictment, hackers sent Podesta a fake email designed to look like a Google security email. The hackers even made the email look like it came from an “@google.com” email address
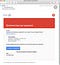
The email probably had a button that linked to a fake website designed to look exactly like Google’s sign-in page. (It’s very easy to make a copy of a webpage by copying its code.) Some of these forgeries look really, really similar to the real thing:
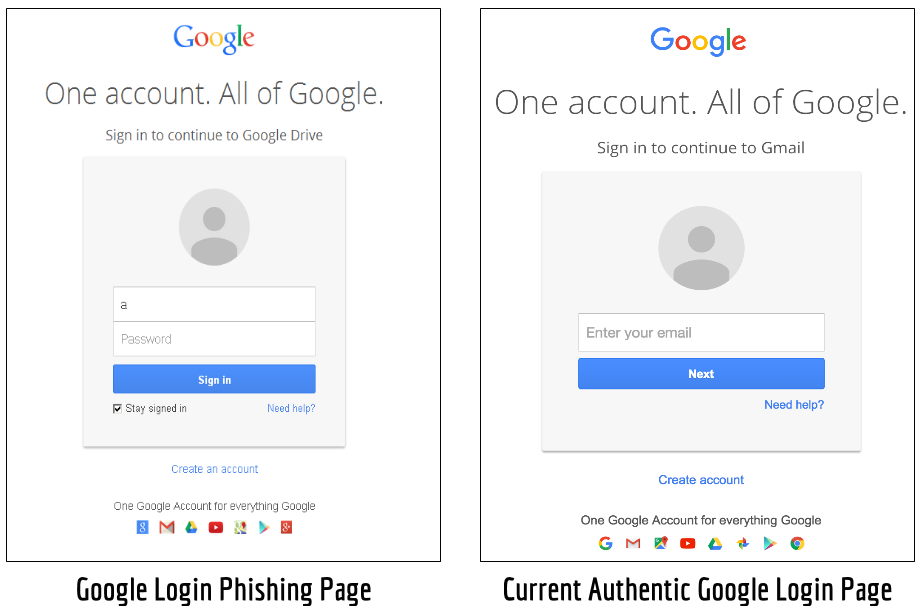
In these cases, the only way to tell the difference between a fake page and a real page is by looking at your web browser’s address bar. The authentic page would, of course, say “google.com”, but the faked page would say something else.
There’s no way to put something fake in the address bar, but the hackers still tried to fool people. There’s evidence that they bought “qooqle.com” — which looks so similar to the real thing that many people might not notice the difference!
The hackers then sent Podesta a fake Google email that led to a fake Google login page. Once Podesta typed in his username and password and hit submit, that information would have gone straight to the hackers’ computers. I imagine the fake page sent Podesta to the actual Google login page so he wouldn’t notice anything was wrong.
Armed with Podesta’s username and password, the hackers must have gone to the actual Google login page and typed in his information, thus breaking into his account and getting access to “over 50,000 emails,” per the indictment.
It’s way easier than you might think to make a fake email or webpage, and stressed campaign officials with hundreds of unread emails might not notice the forgeries.
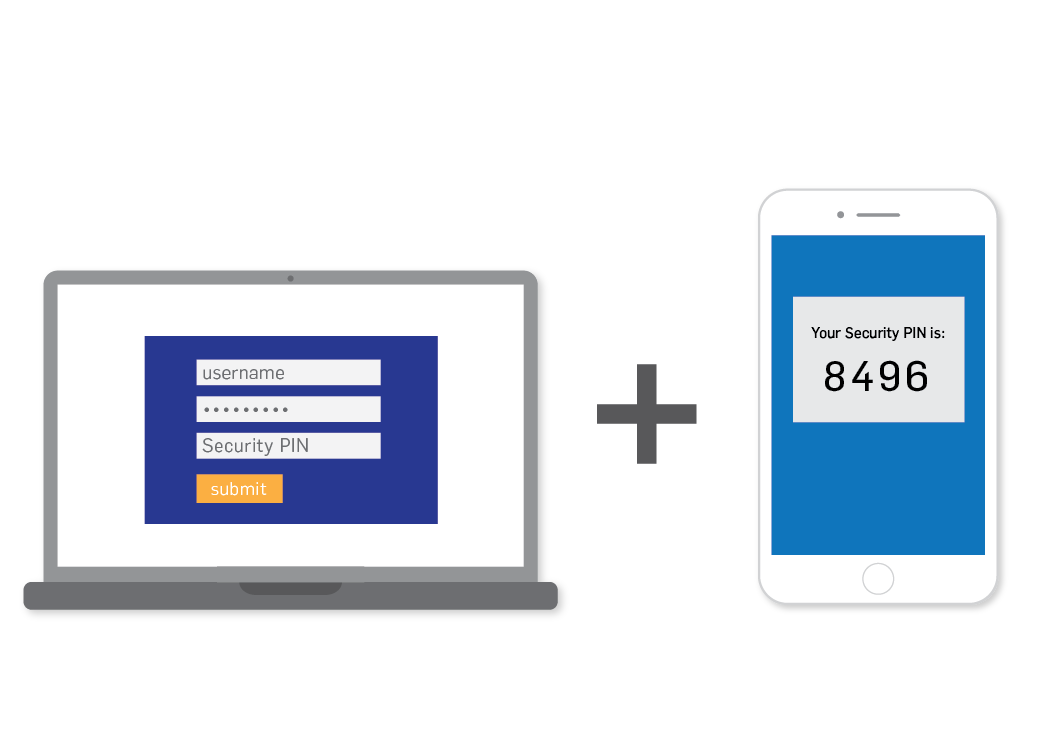
What could Podesta have done to protect himself? Two things. One, he could have looked at the address bar, as I mentioned earlier. Two, he could have used two-factor authentication. If you use two-factor authentication, your username and password are no longer enough to log into a website. Instead, you have to also approve the login from your phone or enter a code that’s sent to your phone.
If you turn on two-factor authentication, that essentially means that someone needs both your username/password and your phone to log in. It’s much harder — and more obvious — to steal a phone than a password. In short, had Podesta used two-factor authentication, the hackers would have been unable to break into his account — even though they had his password.

For more details about the phishing, read page 7 of the indictment.
Malware: how the hackers broke into the Democrats’ computers
According to page 8 of the indictment, the hackers also spearphished an employee of the Democratic Congressional Campaign Committee, the group that helps Democrats running for Congress.
Once they got this employee’s login info, they used it to log into the “DCCC network” — like how you log into your official computer at work. And just like your work computers, the DCCC’s computers were all connected and could access some of each other’s files. Once in, the hackers installed a harmful app, or malware (malicious software), called X-Agent on all the DCCC computers.
This app ran behind-the-scenes on all DCCC computers, sending records of every keyboard key employees pressed (keylogging), as well as screenshots of every computer, to a Russian-owned server in Arizona. With this information, it wouldn’t be hard for the hackers to “read” employees’ messages or steal their passwords: whenever the screenshot shows a login page, just look at the keys pressed and you can easily figure out the username and password.
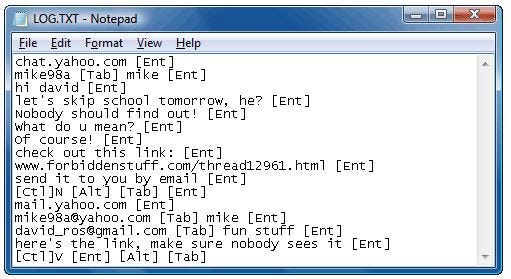
Page 10 of the indictment says that the hackers used the keylogger to figure out one DCCC employee’s username and password for the DNC’s computer network. They then used that to break into the DNC’s network.
Compression, Exchange, the cloud: how the hackers got the Democrats’ documents
Once the hackers got into the DCCC and DNC, here’s how they stole documents and emails.
First, they found the files they wanted on the computers and used “a publicly available tool to gather and compress multiple documents on the… networks,” according to page 11 of the indictment. That’s just a fancy way of saying they zipped up a bunch of documents into a .zip file. (Sending a single .zip file would, I imagine, appear less suspicious than sending thousands of files individually.)
The hackers then used malware called X-Tunnel to send the .zip files back to the Russian intelligence office, called GRU. X-Tunnel encrypted these files, meaning that the contents were scrambled so that nobody besides the GRU could figure out what was inside the files.
You probably use encryption every day, by the way. Whenever you send your credit card details or password to websites like Amazon or Google, your information is encrypted to keep it safe. That’s why you see the “https” instead of the normal “http” in the address bar — the “S” stands for “secure.”


The hackers also stole the DNC’s emails (page 11). They got these in a slightly different way than the Podesta emails. Whereas the Clinton campaign stored its emails on Google’s computers (so they could be accessed through a website), the DNC stored its emails on its own computers, using a tool called Microsoft Exchange Server.
Once into the DNC’s network, the hackers could grab the emails — which likely lived as text files on one computer — and send them back to headquarters.
Finally, on page 13, the indictment alleges that the hackers “gained access to DNC computers hosted on a third-party cloud computing service.” This means the DNC was renting out another company’s computers and storing data files and analytics apps on them. Amazon Web Services and Microsoft Azure are well-known examples of cloud computing services — think of it as a company’s version of Dropbox or Google Drive.
Once the hackers logged into the DNC’s account on this service, they just had to make a backup — creating copies of these files — and put the copies on their own accounts.
VPNs: how the hackers leaked their findings
I’ve just explained how the hackers allegedly stole the documents and emails. They then leaked the documents and emails on a website called dcleaks.com and used fake personas (including the infamous “Guccifer 2.0”) to publicize and share the documents.
The hackers were savvy, though, and recognized that any action you do online leaves a sort of “fingerprint” behind, called your IP address. Each computer has its own IP address, and whenever you visit a website, that website sees your IP address. It’s possible to track an IP address back to a specific city, and often to a specific street.
So, as seen on page 17 of the indictment, the Russians used a virtual private network (VPN). VPNs send all your internet communications through another computer, which is usually in some far-off city. Websites can only see the middle computer’s IP address, not your own, thus letting you use the internet anonymously.
The hackers used a French VPN, so the authorities’ efforts to trace the dcleaks.com website or the Guccifer 2.0 Twitter account always led them to a dead end in France. Always? Well, not quite. See, Guccifer 2.0 was a Russian-created persona that claimed to be a lone Romanian hacker who stole and leaked the documents as a political statement. (It was actually, of course, a front for GRU officers who needed a fake account to spread the leaks.)
Usually, the Russian hackers used their VPN when logging into Guccifer’s Twitter account, so nobody could tell that Guccifer was logging in from Russia, not Romania.


Bitcoin: how the hackers paid for it
The hackers had to pay for their website, VPNs, and other activities. But they couldn’t pay with credit cards, bank transfers, or even PayPal, because that would leave a paper trail and bankers would know that Russian intelligence officers were making the payments. (Your name is printed on your credit card, after all!)
To “avoid direct relationships with traditional financial institutions, allowing them to evade greater scrutiny of their identities and sources of funds,” as the indictment says on page 22, the hackers turned to a mostly-anonymous online currency, or cryptocurrency, called Bitcoin. In the indictment, Bitcoin is mentioned on page 16 and explained in impressive depth on pages 21–23.
Bitcoin lets you send and receive money without any bank, government, or company in between. Bitcoin accounts are identified by nothing more than a long string of random letters or numbers, called an address. (Bitcoin addresses are pretty similar to usernames.) Thus, when you send money, outsiders only know the sender’s and receiver’s addresses.
Bitcoin had several other useful features for the hackers. You can earn Bitcoins by mining, where you have your computer solve computational puzzles for the chance to win small amounts of Bitcoin. You can also obscure where your Bitcoins came from by buying other competing cryptocurrencies and immediately selling them, mixing your funds with other people’s, and sending coins between “shell” accounts. (If that sounds like money laundering, that’s because it is! One of the 11 counts the Russians were charged with was money laundering; see page 10.)


If Bitcoin is anonymous, how did the authorities trace the hackers’ Bitcoin purchases back to them? Well, remember how I said that Bitcoin is only mostly anonymous. Each account is only identified by a random string of letters, but every Bitcoin transaction is stored publicly forever on a ledger — like a giant Excel spreadsheet — called the blockchain. Every time Bitcoins are sent, the sender’s and receiver’s addresses — as well as the amount of money sent — are recorded on the blockchain. So anybody can track who a particular account is sending money to or getting money from.
It appears that American authorities were able to use the blockchain records to figure out which addresses belonged to the Russians. For example, an email account known as “gfadel47” got an email to send 0.026043 Bitcoin (about $9.50 in February 2016, when the email was sent, but over $1600 today) to a certain Bitcoin address. “Shortly thereafter, a transaction matching those exact instructions was added to the Blockchain,” says page 22 of the indictment. So the sender address of that transaction must have belonged to “gfadel47,” and the recipient address must have belonged to the person who wrote that email. The authorities could then have looked at all the other payments made by gfadel47’s account, and so on.
In another instance, a particular Bitcoin address paid someone to buy dcleaks.com, where some of the original documents were leaked. That same address also bought websites known to belong to the GRU’s spearphishing operation. This, then, is evidence that links dcleaks.com with the GRU. I’m sure authorities did a lot more snooping like this.
Bitcoin is theoretically anonymous — but, in practice, it’s possible for a savvy investigator to follow the money.
