記一次網路實踐課程的悶騷操作
阿新 • • 發佈:2019-01-01
一、實驗目的:
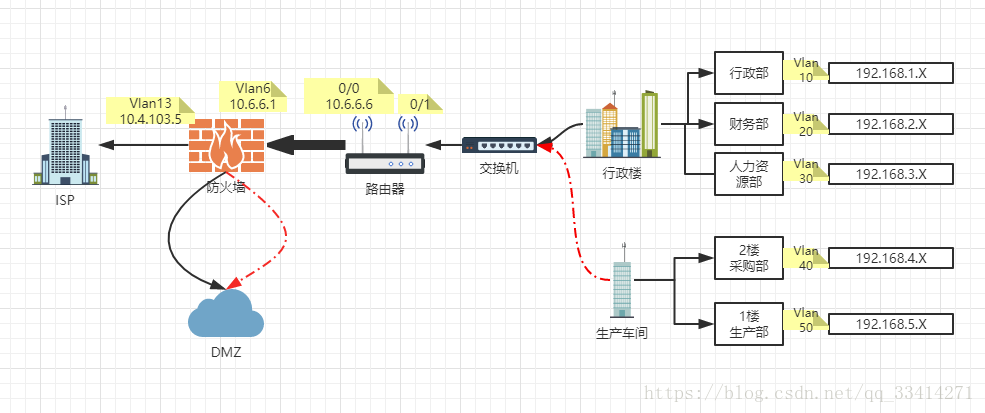
- 搭建企業網站,根據實際進行網路拓撲與IP段規劃:
行政樓:人力資源部【1樓】
財務部【2樓】
行政部【3樓】
生產車間:生產部【1樓】
採購部【2樓】 - 只有行政樓各部門通過NAT訪問公網,生產樓各部門只能訪問內網
- 使用DHCP自動獲取IP
二、實驗裝置:
交換機(二層)、路由器、防火牆
網線若干
電腦5臺
三、實驗步驟:
- 連線交換機、路由器、防火牆
- 配置DHCP池,排除預設閘道器
- 配置防火牆名稱,啟用防火牆結口VLAN
- 配置NAT轉換:內網到外網
- 配置ACL:外網到內網
四、實驗拓撲:
五、配置命令:
**交換機**
vlan database
vlan 10
vlan 20
vlan 30
vlan 40
vlan 50
int fa0/1
sw acc vlan 10
exit
int fa0/2
sw acc vlan 20
exit
int fa0/3
sw acc vlan 30
exit
int fa0/4
sw acc vlan 40
exit
int fa0/5
sw acc vlan 50
exit
配置交換機上聯埠
config terminal
interface fa0/24
switchport mode trunk
end
**路由器**
interface 六、實驗結果:
可以使用DHCP自動獲取IP,只有行政樓各部門通過NAT訪問公網,生產樓各部門只能訪問內網。