pptp問題除錯詳解
|
|||
|
|||
|
|||
|
|||
|
|||
|
-
Symptom: when installing ppp-mppe-2.4.0-4.*.rpm on Red Hat 7.2 or later, this message appears:
error: failed dependencies:
ppp <= 2.3.15 conflicts with kernel-2.4.7-10On Red Hat 7.3, the kernel version is usually 2.4.18-3.
Diagnosis: the 2.4.0-4 ppp-mppe package provides a ppp package without a version. The newer Red Hat kernel packages require a specific version, and so the conflict occurs. Since pptp-linux 1.1.0 there is no longer a dependency on ppp-mppe, as many people don't need to interoperate with a Microsoft VPN Server.
Solution 1: use the kernelmod instructions which are part of the Red Hat 9.0 HOWTO. This alleviates the problem. 2003-05-02 
Solution 2: Install the package with --nodeps.
rpm -Uvh --nodeps ppp-mppe-2.4.0-4.i386.rpm The installation script should tell you that you will have to build the kernel module yourself. Follow the instructions provided with the notice to build the kernel module, then follow the instructions provided from the kernel module build to install the new module. Note that the kernel-sources package for your kernel needs to be installed to complete the build.
On Red Hat 7.3, edit /etc/modules.conf and add these lines:
alias char-major-108 ppp_generic
alias ppp-compress-18 mppe
-
Symptom: trying to start pptpconfig results in an error;
Fatal error: php-gtk: Could not open display in /usr/bin/pptpconfig.php on line 31 which may be preceeded by
Xlib: connection to ":0.0" refused by server
Xlib: Invalid MIT-MAGIC-COOKIE-1 keyDiagnosis: you have used su to become root but that is insufficient to pass on the access to the graphics display. This is a security feature of X-Windows. Solution: see the command not found entry below, as it covers the same problem but from a different error message.
2006-08-21
-
The pptp-command script is using a Perl feature to enhance software security design, but newer Perl versions are more exacting.
Problem: pptp-command fails with a message about an insecure dependency and the -T switch.
Solution 1: Install pptpconfig, and start it by typing pptpconfig. If you are not root, you will be prompted for the root password. You may find it much easier to configure than pptp-command. Solution 2: upgrade to 1.2.0 or later of pptp-linux. If the problem continues, upgrade to the latest pptp-command from CVS.
2003-05-02
Workaround: remove the -T switch from the top of the pptp-command file. Report the version of Perl, and the exact text of the error message, so we can fix it.
-
Problem: pptp-command fails to enter setup mode, and emits a long stream of similar errors
WARNING: the line:
# whatever
contains unsafe characters!Solution 1: Install pptpconfig, and start it by typing pptpconfig. If you are not root, you will be prompted for the root password. You may find it much easier to configure than pptp-command. 2003-05-02 
Solution 2: check for carriage return characters in the drop-in configuration file and remove them.
% od -c /tmp/config|grep "\n"
% tr --delete '\r' < /tmp/config > /tmp/config.new -
Problem: pptp-command fails to start tunnel:
ERROR! Connection timed out Diagnosis: older versions of pptp-command did not check effectively for success. They waited for the network interface to be created. If this did not happen within the time allowed, the error would appear.
Solution: enable debug mode, start the tunnel manually, and look for the cause of the problem in the output. Check the rest of this document.
Upgrade to the pptp-command shipped in 1.2.0 to be told when the tunnel fails rather than wait for the timeout.
Consider an upgrade to pptpconfig. Synchronisation of the user interface with PPP is more straightforward, and it is easier to use. 2003-05-02 
-
Problem: pptp-command fails to start tunnel:
New interface not found. Diagnosis: pptp-command was told by pppd that the connection was established, but the network interface was no longer present. This is usually because pppd has failed after establishing the connection.
Solution: enable debug mode, start the tunnel manually, and look for the cause of the problem in the output. Check the rest of this document.
Upgrade to pptpconfig, and start it by typing pptpconfig. Re-enter your tunnel data. When it fails to establish the tunnel, more information is provided. 2003-05-02 
-
Symptom: when trying to start pptp, pptpconfig, or pptpsetup as a non-root user, this message appears: pptp: command not found Diagnosis: the program is not in your PATH, or you are not running the program as the root user. This is a normal security feature of most systems.
The solutions depend on which program you are running.
pptpconfig
The pptpconfig program needs access to your X-Windows display, write access to /etc/ppp/peers, /etc/pptpconfig, and also needs to start pppd and pptp which themselves need root. Choose one of these methods:
- configure sudo to allow a user to run pptpconfig as root without any password prompt, for example:
# echo ALL ALL=NOPASSWD: /usr/sbin/pptpconfig >> /etc/sudoers add a desktop launcher item which runs this:
% sudo /usr/sbin/pptpconfig and since pptpconfig presumes both pptp and ip are in the PATH, either create symlinks:
% ln -s /usr/sbin/pptp /usr/bin/pptp
% ln -s /sbin/ip /bin/ipor augment PATH in the usual fashion.
- use kdesu if it is installed; type kdesu pptpconfig and press enter. You may be prompted for the root password, and then the pptpconfig window should appear.
- use gksu if it is installed; type gksu pptpconfig and press enter. You may be prompted for the root password, and then the pptpconfig window should appear.
- use gnomesu if it is installed; type gnomesu pptpconfig and press enter. You may be prompted for the root password, and then the pptpconfig window should appear.
- use ssh to forward the X11 connection; type ssh -X [email protected] pptpconfig and press enter. You may be prompted for the root password. The sshmethod may not work if your /etc/ssh/sshd_config file has X11Forwarding set to no. Another security feature.
- log in as root to begin with. On some distributions, you can configure the connection using pptpconfig as root, and then start the tunnel using pon tunnelname as an ordinary user.
- adjust the definition of the menu option for pptpconfig by adding whichever wrapper above worked for you.
The pptpsetup program needs write access to /etc/ppp/peers, /etc/pptpconfig, and also needs to start pppd and pptp. Choose one of these methods:
- configure sudo to allow you to start pptpsetup, as described in the section above,
- use ssh; type ssh [email protected] pptpsetup and press enter. You may be prompted for the root password.
- log in as root to begin with. On some distributions, you can configure the connection using pptpsetup as root, and then start the tunnel using pon tunnelname as an ordinary user.
- configure pptpsetup to be setuid root:
# chmod u+s `which pptpsetup`
pptp requires root privilege to create a raw socket for GRE packet transmission. pptp is in /usr/sbin, which is in the PATH for the root user. pptp is started bypppd. Follow this sequence:
- make sure you are using pptp-client 1.1.0 or later,
- as root, configure the tunnel with pptpconfig or pptpsetup, and test it, but then stop using pptpconfig or pptpsetup as the way to start it,
- make pptp setuid root:
# chmod u+s `which pptp` - test that a pppd command can be used to start the tunnel:
# pppd call tunnel where tunnel is the name of the tunnel configuration file. pppd knows to look in /etc/ppp/peers for the file.
If the tunnel does not start, enable debug logging, and try the pppd command again.
- return to non-root user mode, and then use a normal GUI or console utilities (e.g. pon and poff) to start or stop the pppd connection named 'tunnel'.
# pon tunnel - you may need to add a host route to the PPTP server first, which is something that pptpconfig does for PPTP Client 1.7.1 and earlier,
- if you used any special routing in pptpconfig then you will need to duplicate this at the command line. Enable debug logging in pptpconfig to see exactly what commands it is executing and when.

- configure sudo to allow a user to run pptpconfig as root without any password prompt, for example:
-
Symptom: on starting pptp, three messages appear, followed by a delay:
warn[open_inetsock:pptp_callmgr.c:305]: connect: Connection refused
fatal[callmgr_main:pptp_callmgr.c:128]: Could not open control connection to x.x.x.x
fatal[open_callmgr:pptp.c:278]: Call manager exited with error 256
Diagnosis: the host that you provided has refused connection.
Solution: check the IP address or name of the PPTP Server, and check that the PPTP Server is running properly. Work through the Fault Tree from the top.
-
Symptom: on starting pptp, three messages appear:
warn[open_inetsock:pptp_callmgr.c:305]: connect: Network is unreachable
fatal[callmgr_main:pptp_callmgr.c:128]: Could not open control connection to x.x.x.x
fatal[open_callmgr:pptp.c:278]: Call manager exited with error 256
Diagnosis: the host that you provided cannot be reached via the network. This is usually caused by not having an active internet connection at all.
Solution: check the IP address or name of the PPTP Server, and check that the PPTP Server is running properly. Work through the Fault Tree from the top.
-
Symptom: on starting pptp, three messages appear:
warn[open_inetsock:pptp_callmgr.c:305]: connect: No route to host
fatal[callmgr_main:pptp_callmgr.c:128]: Could not open control connection to x.x.x.x
fatal[open_callmgr:pptp.c:278]: Call manager exited with error 256
Diagnosis: the host that you provided cannot be reached via the network.
Solution: check the IP address or name of the PPTP Server, and check that the PPTP Server is running properly. Work through the Fault Tree from the top.
-
Symptom: the following messages appear before the tunnel is established:
log[pptp_dispatch_ctrl_packet:pptp_ctrl.c:580]: Client connection established.
log[pptp_dispatch_ctrl_packet:pptp_ctrl.c:708]: Outgoing call established (call ID 0, peer's call ID 0).
log[decaps_hdlc:pptp_gre.c:129]: short read (4294967295): Input/output error
log[callmgr_main:pptp_callmgr.c:245]: Closing connection
log[pptp_conn_close:pptp_ctrl.c:307]: Closing PPTP connection
log[call_callback:pptp_callmgr.c:88]: Closing connection
Diagnosis: pppd was started by pptp but was unable to operate, and so terminated quickly. pptp tried to read data from pppd but found none. There are many reasons why pppd could have failed, but the most likely are configuration file errors.
Solution: Enable debug logging and check to see why pppd failed. Search this HOWTO for those messages.
Symptom: on a PPTP server running pptpd, the following message may appear when all incoming tunnel requests fail: pptpd[5740]: GRE: read(fd=5,buffer=804dc00,len=8196) from PTY failed: status = -1 error = Input/output error Diagnosis: pppd was started by pptpd but was unable to operate, and so terminated quickly. pptpd tried to read data from pppd but found none. There are many reasons why pppd could have failed, but the most likely are configuration file errors.
pptpd incorrectly hides all pppd error output. This is a defect and should be fixed. It apparently doesn't even wait for and report the pppd exit status.
Solution: check the configuration files. A simple typo will cause this error. It is easy to have pppd tell you where the typo is. Here is how:
Try running pppd against the configuration files in the same way that pptpd would run it. If you strace the pptpd, you can detect the command line given topppd (just after it says "launching pppd"), and then you can run that command manually in a shell to see what objections pppd has to the options.
When we did an strace just now, we got this line that was valuable;
12704 execve("/usr/sbin/pppd", ["/usr/sbin/pppd", "local", "file", "/etc/ppp/pptpd-options", "50", "10.0.1.1:10.0.1.3"], [/* 18 vars */]) = 0 This tells us that pptpd is trying to execute the following command to accept the tunnel connection from the client (we have speed 50 in our options file);
pppd local file /etc/ppp/pptpd-options 50 10.0.1.1:10.0.1.3 Running this command in a shell starts pppd negotiating with the keyboard and screen. After a while it times out. Adding the dryrun option allow us to test the syntax only. We added the word bogus to our pptpd-options file (your file name may differ), and the result was as follows:
pppd local file /etc/ppp/pptpd-options 50 10.0.1.1:10.0.1.3 dryrun
pppd: In file /etc/ppp/pptpd-options: unrecognized option 'bogus'pppd had returned an exit status of 2, which according to the manual page means "An error was detected in processing the options given, such as two mutually exclusive options being used."
Removing the word bogus caused pppd to exit with a status of 0. We used the shell command echo $? to check the exit status.
As to why the error messages from pppd are being ignored, the running pppd on our test server has file descriptor 2 (stderr) bound to a deleted pty. We presume this is a code fault in pptpd.
2003-09-02
-
Symptom: the following messages appear before the tunnel is established:
log[pptp_dispatch_ctrl_packet:pptp_ctrl.c:580]: Client connection established.
log[pptp_dispatch_ctrl_packet:pptp_ctrl.c:708]: Outgoing call established (call ID 0, peer's call ID 0).
log[decaps_gre:pptp_gre.c:215]: short read (4294967295): Protocol not available
log[callmgr_main:pptp_callmgr.c:245]: Closing connection
log[pptp_conn_close:pptp_ctrl.c:307]: Closing PPTP connection
log[call_callback:pptp_callmgr.c:88]: Closing connection
Diagnosis: usually caused by the client not binding to the GRE socket early enough during the connection sequence. The first GRE packet from the server causes an ICMP protocol unreachable reply. This happens more frequently on high speed connections.
Workaround: load the ip_gre module. This prevents the ICMP protocol unreachable reply from being generated.
# modprobe ip_gre Solution: upgrade to pptp-linux 1.2.0, which binds the GRE socket prior to calling the server. Loading the ip_gre module should not be needed. 2003-05-02 
-
Symptom: write to the GRE socket fails with EPERM.
Diagnosis: iptables rules (such as for a firewall configuration) do not allow the interface to emit GRE packets.
Solution: locate the rule that prevents the write, or add a rule to cover it, and retry the tunnel.
-
Symptom: while running pptp, this message appears, which may or may not be associated with any other problem: log[decaps_gre:pptp_gre.c:397]: buffering out-of-order packet 272 (expecting 271)
Diagnosis: this is a normal situation. Many network links drop or re-order packets as a normal part of their operation. This message informs you that a packet was lost or re-ordered. The TCP network infrastructure above this level will retransmit the lost data.
(out-of-order in this context relates to the sequence of the packets, and should not be confused with the use of the phrase in some locales to warn that public equipment is not operating.)
Solution: if the loss is higher than the physical layer should provide, check the physical layer for problems.
You can also use the link statistics feature of pptp, see the man page for how to obtain and understand the statistics.
2004-02-16
-
Symptom: when starting PPTP Client on Red Hat 7.2 or 7.3, the pppd process cannot locate the appropriate module.
modprobe: modprobe: Can't locate module char-major-108
/usr/sbin/pppd: This system lacks kernel support for PPP. This could be because the PPP kernel module could not be loaded, or because PPP was not included in the kernel configuration.Diagnosis: the 2.4.0-4 ppp-mppe package adds entries to /etc/modules.conf that work only for Red Hat 6.2.
Solution 1: use the kernelmod instructions which are part of the Red Hat 9.0 HOWTO. This alleviates the problem. 2003-05-02 
Solution 2: Edit the /etc/modules.conf file and change the alias char-major-108 ppp to alias char-major-108 ppp_generic.
-
Symptom: the following messages appear before connection is established: Serial connection established.
Couldn't set tty to PPP discipline: Invalid argument
Hangup (SIGHUP)
Diagnosis: pppd has failed to change the pty over to run it in PPP mode. This may be because you have no ppp_async module built for your kernel. Most kernels are built with this already, but if you have customised your kernel you may not have built it.
Solution: rebuild your kernel with CONFIG_PPP_ASYNC set. While you are at it, you should set CONFIG_PPP as well, and both should be set to "m" so that they are built as modules. We've found they don't work compiled statically.
2004-02-02
-
Symptom: when using pptp started as a psuedo-tty from within pppd, the following messages appear before connection is established:
write: warning: Input/output error (5)
Modem hangup
Diagnosis: pptp is not running at the time pppd writes to the psuedo-tty. This may be because you have no pptp program, or it may have failed. Enablingdebug logging would show just one message, an LCP write, being sent prior to the write warning.
Solution: check that the pptp program is present, check that the --nolaunchpppd option is being used, and check the messages log for messages emitted bypptp.
-
Symptom: pppd fails during a connection attempt and issues this message:
The remote system (hostname) is required to authenticate itself
but I couldn't find any suitable secret (password) for it to use to do so.
(None of the available passwords would let it use an IP address.)
Note the last line. If this is not present, read the required to authenticate entry.
Diagnosis: No IP address listed in chap-secrets file. pptp-command adds entries to the file without an IP address, and the manual page for pppd says that this means no IP address will be considered valid. Not all versions of pppd require this.
Solution: Adjust the chap-secrets file to add an asterisk as the address, which is the fourth field.
-
The usual cause of this is entering the wrong password. Passwords which contain odd characters, like hash (#) may need to be quoted in the chap-secrets file.
Other causes are: - specifying the wrong domain (E=691),
- restrictions on logon hours (E=646),
- account is disabled (E=647),
- account password expired (E=648),
- specifying the wrong password (E=691), (e.g. by not quoting special characters),
- using spaces or blanks as part of your password (E=691), (our tests show this doesn't work).

Often the E=nnn error number above is followed by a R=0 or R=1, which means the server is disallowing or allowing a retry respectively. pppd on Linux generally doesn't use the opportunity to retry. There may also be an opportunity to change the password, but this is not well understood here. 2006-01-24 
-
Problem: pppd displays an error: Remote message: Unknown authentication failure: E=649 R=0
CHAP authentication failedDiagnosis: error code 649 is ERROR_NO_DIALIN_PERMISSION, the account does not have dialin permission.
Solution: ask the server administrator to give your account dialin permission.
2003-12-15
-
Symptom: pppd fails during a connection attempt and issues this message:
sent [CHAP Response id=0x0 <...>, name = "domain\\\\username"]
rcvd [LCP EchoRep id=0x0 magic=0x15973814]
rcvd [CHAP Failure id=0x0 "E=691 R=1 C=... V=3"]
Remote message: E=691 R=1 C=... V=3
CHAP authentication failed
sent [LCP TermReq id=0x3 "Failed to authenticate ourselves to peer"]
rcvd [LCP TermAck id=0x3 "Failed to authenticate ourselves to peer"]
Diagnosis: four slashes have been used instead of two between the domain name and the username. This is a common error, due to the escaping and quoting rules of the shell versus the pppd options file.
Solution: remove two of the slashes.
-
Symptom: pppd fails during a connection attempt and issues this message:
The remote system (hostname) is required to authenticate itself
but I couldn't find any suitable secret (password) for it to use to do so.
If after this it says that none of the available passwords would let it use an IP address, read the previous entry.
Diagnosis 1: While normally the PPTP Server will require authentication from your client, your pppd configuration files can tell your client to require authentication from the PPTP Server. The message shows there is insufficient information to achieve this, and so pppd stops.
Solution 1: Usually it is not necessary to have the PPTP Server authenticate in this way. Make sure that noauth option is in the options file, or given to pppdvia the command line. Make sure that require-mschap-v2 require-mschap require-chap require-pap require-eap options are not used.
Diagnosis 2: You may have rebuilt the kernel after installing the modules for the PPTP Client. During "make modules_install", you will have overwritten themisc/mppe.o and kernel/drivers/net/ppp_generic.o modules.
Solution 2: reinstall the two modules.
We believe there may be other causes of this error. Please write to the mailing list if this solution does not fix your problem, so that we can work together to improve this HOWTO.
-
Problem: connection fails and the logs contain this message: Could not determine local IP address
sent [IPCP TermReq id=0x4 "Could not determine local IP address"]
Diagnosis: pppd has completed IPCP negotiation with the peer (e.g. the PPTP server) and was about to raise the new network interface, but found that neither the peer, the command line, or the hostname gave a valid IP address.
Usually, the peer provides the IP address during IPCP negotiation. You can examine the debug log to determine how this negotiation proceeded.
Solution: choose one:
- provide an IP address on the command line, (see man pppd in the section marked OPTIONS, or just add the IP address followed by a colon, e.g. 10.0.0.1:),
- change the peer configuration to suggest a local IP address,
- ensure that the noipdefault option is not being used, and that the system hostname translates to an IP address.
pppd tries to determine your local IP address using the host name. On systems installed without a hostname, this may fail. So set a hostname using thehostname command, and add the IP address to /etc/hosts. This change may require the restart of other processes.
2004-03-08
-
This is a general error condition that is common to a number of causes. It means that pppd did not receive any LCP configuration requests from the peer, or was unable to agree on LCP parameters. Enable debug
logging, try the connection again, and look at messages just prior to this message.
There are many causes for the timeout error:
Use tcpdump to check the flow of GRE packets.
-
If you see a series of sent [LCP ConfReq ...] messages with no rcvd messages, then you may not have GRE connectivity to the PPTP Server. Prove this using the GRE step
in the Fault Tree.
-
Symptom: GRE packets are emitted by the client, but none are returned by the server, but a tunnel from another machine on the same LAN works fine. The client is behind a NAT gateway with respect to the server.
Diagnosis: PPTP servers will not allow a connection to start from the same IP address that they perceive an active connection on already.
Solution: use alternate PPTP server IP addresses.
-
Symptom: GRE packets are emitted by the client, GRE packets are returned by the server, but the client makes no sense of them, reporting in the debug log the following asynchronous PPP packet:
rcvd [proto=0x7eff] 7d 23 c0 21 7d 21 7d 21 7d 20 7d 39 7d 22 ...]
Diagnosis: you may be running pppd with the sync option, with a version of the GRE-to-PPP gateway that will recognise sync mode, but the server is returning asynchronous responses.
Solution: turn off sync and try again.
-
There are two known causes.
Symptom: tcpdump shows no GRE packets are being transmitted by the client. strace shows no write() on the GRE socket by the GRE-to-PPP gateway process.
Diagnosis: you may be running pppd with the sync option, which prevents older version of the GRE-to-PPP gateway from forwarding the packets.
Solution: turn off sync and try again.
Symptom: tcpdump shows no GRE packets are being transmitted by the client. However, strace shows a successful write() on the GRE socket by the GRE-to-PPP gateway process.
Diagnosis: your system may have iptables or ipchains rules that prevent GRE transmission. The GRE-to-PPP gateway sends the packets, but they are dropped by the packet filter before being transferred to the interface.
Solution: check the firewall rules, remove or add replacements, and try again. The following iptables rules may be added to allow GRE through eth0. Change eth0 to the name of the interface through which the PPTP Server is contacted.
iptables --insert OUTPUT 1 \
--source 0.0.0.0/0.0.0.0 \
--destination 0.0.0.0/0.0.0.0 \
--jump ACCEPT --protocol gre \
--out-interface eth0
iptables --insert INPUT 1 \
--source 0.0.0.0/0.0.0.0 \
--destination 0.0.0.0/0.0.0.0 \
--jump ACCEPT --protocol gre \
--in-interface eth0These rules can be refined further to constrain the GRE traffic.
-
Symptom: 10 or more GRE packets are emitted by the client in less than a second, and the number of GRE packets is far greater than the number of LCP requests logged.
Diagnosis: you may be running pppd with the pty option and the debug option but not the logfd 2 option. This can cause pppd to send the debug messages out the psuedo-tty file descriptor to the GRE-to-PPP gateway process, and then to the PPTP Server. The server refuses to respond once it sees random traffic like this.
Solution: Add the logfd 2 option.
-
Symptom: you are using PPP-MPPE 2.4.x and logs contain this sequence:
rcvd [LCP ConfReq id=0x0 <auth chap 81> <magic 0x7a73> <pcomp> <accomp>]
sent [LCP ConfRej id=0x0 <auth chap 81>
See next item below.
-
Symptom: you are using PPP 2.4.2 or later and logs contain this sequence: rcvd [LCP ConfReq id=0x0 <auth chap MS-v2> <magic 0x7a73> <pcomp> <accomp>]
No auth is possible
sent [LCP ConfRej id=0x0 <auth chap MS-v2>
Diagnosis: your pppd is refusing to perform MS-CHAP-V2 authentication. The PPTP Server requires it, and so it terminates the connection. The known causes are:
- pppd could not find a matching entry in the chap-secrets file, (see below for causes)
- pppd was built without MS-CHAP-V2 support (quite uncommon).
The search in the chap-secrets file uses the name and remotename options given to pppd. The name is usually the authentication domain and username. Theremotename is usually PPTP, or the name of the tunnel.
The chap-secrets file is a series of lines with blank separated fields. The file is searched for a line where:
- the first field matches the local name option value (e.g. domain\\username),
- the second field matches the remotename option value (e.g. tunnelname or PPTP), and
- the fourth field contains a valid IP address or asterisk.
Any spaces or special characters in the local name, password, or remote name must be properly quoted. The hash character (#) in a password is a definite cause of this; add quotes around the password to fix it. See man pppd section AUTHENTICATION for more details.
Solution: fix the chap-secrets file or the pppd options so that they match.
2005-06-02
-
The pppd did not complete CCP configuration within the timeout period. Usually caused by a conflict between the client and the PPTP Server. Enable debug logging,
try the connection again, and look at messages just prior to this message.
See below for the most likely cause.
-
Symptom: debug logs contain this sequence:
sent [CCP ConfReq id=0x5]
rcvd [CCP ConfNak id=0x5 ]
sent [CCP ConfReq id=0x6]
rcvd [CCP ConfNak id=0x6 <mppe 0 0 0 0>]
sent [CCP ConfReq id=0xa]
rcvd [CCP TermReq id=0x3 00 00 02 dc]
sent [CCP TermAck id=0x3]
sent [LCP EchoReq id=0x1
CCP: timeout sending Config-Requests
sent [LCP EchoReq id=0x2
No response to 4 echo-requests
Serial link appears to be disconnected.
sent [LCP TermReq id=0x3 "Peer not responding"]
Diagnosis: your pppd is refusing to accept MPPE encryption. The PPTP Server requires MPPE, and so it terminates the connection.
Solution: make sure the MPPE module loads successfully. Prove this using the MPPE step in the Fault Tree.
- Your pppd could not negotiate authentication. Enable debug logging, try the connection again, and look for rejection packets just prior to this message. Decide what to do based on the rejection packets.
-
Your pppd could not negotiate encryption. Enable debug logging, try the connection again, and look for rejection packets just prior to this message. Decide
what to do based on the rejection packets.
See the next two sections below for the most likely causes.
-
Symptom: an LCP TermReq occurs immediately after an EAP Response, as per this example log: rcvd [EAP Request id=0x0 Identity <No message>]
sent [EAP Response id=0x0 Identity <Name "username">]
rcvd [LCP TermReq id=0x3 0e a3 45 cf 00 3c cd 74 00 00 02 89]
LCP terminated by peer (^NM-#EM-O^@<m-mt^@^@^bm- )="" <="" small="">Diagnosis: this may be an indication that EAP authentication failed.
Solution: either correct the cause of the authentication failure, or direct the client to refuse EAP authentication by adding refuse-eap to the list of pppdoptions.
2003-05-26
-
Compression negotiation has failed. Occurs after a CCP ConfRej. See below for likely cause. If that doesn't fix it, enable debug logging, try the connection again, and look for rejection packets just prior to this message. Decide what to do based on the rejection packets.
2003-05-26
-
Symptom: logs contain this sequence:
sent [IPCP ConfReq id=0x1 <addr 0.0.0.0> <compress VJ 0f 01>]
sent [CCP ConfReq id=0x1 <mppe 1 0 0 60>]
rcvd [CCP ConfReq id=0x3 <mppe 1 0 0 e1>]
sent [CCP ConfNak id=0x3 <mppe 1 0 0 60>]
rcvd [CCP ConfNak id=0x1 <mppe 1 0 0 40>]
sent [CCP ConfReq id=0x2]
rcvd [CCP ConfReq id=0x5 <mppe 1 0 0 40>]
sent [CCP ConfRej id=0x5 <mppe 1 0 0 40>]
rcvd [CCP ConfNak id=0x2 <mppe 1 0 0 40>]
sent [CCP ConfReq id=0x3]
rcvd [LCP TermReq id=0x6 "#\37777777776U\37777777621\000<..."]
LCP terminated by peer (#M-~UM-^Q^@<M-Mt^@^@^BM-f)
sent [LCP TermAck id=0x6]
Diagnosis 1: your pppd is refusing to accept the level of MPPE encryption required by the PPTP Server. The PPTP Server insists on that level, and so it terminates the connection.
Solution 1: make sure the require-mppe option is provided to the pppd command, such as in the options file. For versions of pppd prior to and including 2.4.0, provide the options mppe-40, mppe-128 and mppe-stateless. See also Why are the pppd options different?.
Make sure the MPPE module loads successfully. Prove this using the MPPE step in the Fault Tree.
Diagnosis 2: You may have rebuilt the kernel after installing the modules for the PPTP Client. During "make modules_install", you will have overwritten themisc/mppe.o and kernel/drivers/net/ppp_generic.o modules.
Solution 2: reinstall the two modules.
-
Symptom: debug logs contain this sequence:
sent [CCP ConfReq id=0x1 <deflate 15> <deflate(old#) 15> <bsd v1 15>]
rcvd [CCP ConfRej id=0x1 <deflate 15> <deflate(old#) 15> <bsd v1 15>]
sent [CCP ConfReq id=0x2]
sent [CCP ConfReq id=0x2]
rcvd [CCP TermAck id=0x2]
sent [CCP TermReq id=0x3"No compression negotiated"]
rcvd [CCP TermAck id=0x3]
Diagnosis: your pppd is suggesting only deflate and bsdcomp compression options, and not MPPE. The PPTP Server rejects the suggestions and disconnects.
Solution: make sure the require-mppe option is provided to the pppd command, such as in the options file. For versions of pppd prior to and including 2.4.0, provide the options mppe-40, mppe-128 and mppe-stateless. See also Why are the pppd options different?. Make sure the nobsdcomp and nodeflate options are provided, so that pppd does not suggest them.
-
Symptom: logs contain this message: MPPE required, but MS-CHAP[v2] auth not performed. Diagnosis: you have given pppd the option require-mppe which forces the use of encryption, but the authentication phase did not use MS-CHAP[v2], it used something else. MPPE requires the use of MS-CHAP[v2] for establishing initial encryption keys. pppd terminates once it detects this conflict.
Solution: either fix the authentication or remove require-mppe.
To find out how authentication happens, enable debug logging, try the connection again to determine what method the peer is offering for authentication. Then configure pppd to refuse that method.
Or, add the following pppd options:
- refuse-eap
- refuse-pap
- refuse-chap
- refuse-mschap
These options configure pppd to refuse to authenticate using certain protocols. As a result, the peer will attempt other protocols, hopefully MS-CHAP[v2]. Do not use require-mschap-v2 because this asks pppd to authenticate the peer, a reversal of what is normally done.
2006-03-27
-
Symptom 1: logs contain this sequence: LCP terminated by peer (MPPE required but peer refused) or
Symptom 2: debug logs contain this sequence:
sent [CCP ConfReq id=0x1]
rcvd [CCP ConfReq id=0x1 <mppe +H -M +S -L -D -C>]
rcvd [CCP ConfAck id=0x1]
sent [CCP ConfRej id=0x1 <mppe +H -M +S -L -D -C>]
rcvd [LCP TermReq id=0x2 "MPPE required but peer refused"]
Diagnosis: the local pppd is refusing to accept the level of MPPE encryption required by the peer. The peer insists on that level, and so it terminates the connection.
In the case above, the local pppd has proposed no encryption or compression, but the peer has requested stateless 128-bit encryption. The local pppd rejects the proposal from the peer.
Solution: if you are using the GUI, select the tunnel, click on on the Encryption tab, turn on Require Microsoft Point-to-Point Encryption (MPPE), and Update, and try to Start the tunnel again.
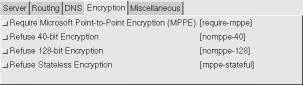
Otherwise, make sure the require-mppe option is provided to the pppd command, such as in the options file or the command line.
2003-06-17
-
Symptom: require-mppe-128 option is set, and debug logs contain this sequence: sent [CCP ConfReq id=0x1 <mppe +H -M +S +L -D -C>]
rcvd [CCP ConfReq id=0x4 <mppe +H -M -S -L -D +C>]
MPPE required but peer negotiation failed
sent [LCP TermReq id=0x4 "MPPE required but peer negotiation failed"]with the essential component being the immediate termination by the local host on receipt of a CCP ConfReq that has the encryption bits turned off (-M -S -L).
Diagnosis: this is a defect of pppd on your system. It is terminating the connection on the basis that the peer started to suggest no encryption. Your pppd is not first negotiating to achieve encryption. The version of pppd you are using takes the require-mppe-128 option pedantically; refusing to connect if the peer is configured to allow no encryption, even if the peer may allow encryption after negotiation.
2005-01-19
Soluti
