springboot+security整合(3)
阿新 • • 發佈:2019-01-07
這篇講解如何自定義鑑權過程,實現根據資料庫查詢出的 url 和 method 是否匹配當前請求的 url 和 method 來決定有沒有許可權。security 鑑權過程如下:
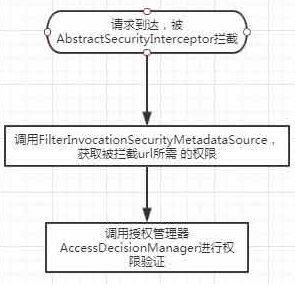
一、 重寫 metadataSource 類
- 編寫 MyGranteAuthority 類,讓許可權包含 url 和 method 兩個部分。
public class MyGrantedAuthority implements GrantedAuthority {
private String method;
private String url;
public - 編寫 MyConfigAttribute 類,實現 ConfigAttribute 介面,程式碼如下:
public class MyConfigAttribute implements ConfigAttribute {
private HttpServletRequest httpServletRequest;
private MyGrantedAuthority myGrantedAuthority;
public MyConfigAttribute(HttpServletRequest httpServletRequest) {
this.httpServletRequest = httpServletRequest;
}
public MyConfigAttribute(HttpServletRequest httpServletRequest, MyGrantedAuthority myGrantedAuthority) {
this.httpServletRequest = httpServletRequest;
this.myGrantedAuthority = myGrantedAuthority;
}
public HttpServletRequest getHttpServletRequest() {
return httpServletRequest;
}
@Override
public String getAttribute() {
return myGrantedAuthority.getUrl();
}
public MyGrantedAuthority getMyGrantedAuthority() {
return myGrantedAuthority;
}
}
- 編寫 MySecurityMetadataSource 類,獲取當前 url 所需要的許可權
@Component
public class MySecurityMetadataSource implements FilterInvocationSecurityMetadataSource {
private Logger log = LoggerFactory.getLogger(this.getClass());
@Autowired
private JurisdictionMapper jurisdictionMapper;
private List<Jurisdiction> jurisdictions;
private void loadResource() {
this.jurisdictions = jurisdictionMapper.selectAllPermission();
}
@Override
public Collection<ConfigAttribute> getAttributes(Object object) throws IllegalArgumentException {
if (jurisdictions == null) this.loadResource();
HttpServletRequest request = ((FilterInvocation) object).getRequest();
Set<ConfigAttribute> allConfigAttribute = new HashSet<>();
AntPathRequestMatcher matcher;
for (Jurisdiction jurisdiction : jurisdictions) {
//使用AntPathRequestMatcher比較可讓url支援ant風格,例如/user/*/a
//*匹配一個或多個字元,**匹配任意字元或目錄
matcher = new AntPathRequestMatcher(jurisdiction.getUrl(), jurisdiction.getMethod());
if (matcher.matches(request)) {
ConfigAttribute configAttribute = new MyConfigAttribute(request,new MyGrantedAuthority(jurisdiction.getMethod(),jurisdiction.getUrl()));
allConfigAttribute.add(configAttribute);
//這裡是獲取到一個許可權就返回,根據校驗規則也可獲取多個然後返回
return allConfigAttribute;
}
}
//未匹配到,說明無需許可權驗證
return null;
}
@Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
return null;
}
@Override
public boolean supports(Class<?> clazz) {
return FilterInvocation.class.isAssignableFrom(clazz);
}
}
二、 編寫 MyAccessDecisionManager 類
實現 AccessDecisionManager 介面以實現許可權判斷,直接 return 說明驗證通過,如不通過需要丟擲對應錯誤,程式碼如下:
@Component
public class MyAccessDecisionManager implements AccessDecisionManager{
private Logger log = LoggerFactory.getLogger(this.getClass());
@Override
public void decide(Authentication authentication, Object object, Collection<ConfigAttribute> configAttributes)
throws AccessDeniedException, InsufficientAuthenticationException {
//無需驗證放行
if(configAttributes==null || configAttributes.size()==0)
return;
if(!authentication.isAuthenticated()){
throw new InsufficientAuthenticationException("未登入");
}
Collection<? extends GrantedAuthority> authorities = authentication.getAuthorities();
for(ConfigAttribute attribute : configAttributes){
MyConfigAttribute urlConfigAttribute = (MyConfigAttribute)attribute;
for(GrantedAuthority authority: authorities){
MyGrantedAuthority myGrantedAuthority = (MyGrantedAuthority)authority;
if(urlConfigAttribute.getMyGrantedAuthority().equals(myGrantedAuthority))
return;
}
}
throw new AccessDeniedException("無許可權");
}
@Override
public boolean supports(ConfigAttribute attribute) {
return true;
}
@Override
public boolean supports(Class<?> clazz) {
return true;
}
}
三、 編寫 MyFilterSecurityInterceptor 類
該類繼承 AbstractSecurityInterceptor 類,實現 Filter 介面,程式碼如下:
@Component
public class MyFilterSecurityInterceptor extends AbstractSecurityInterceptor implements Filter {
//注入上面編寫的兩個類
@Autowired
private MySecurityMetadataSource mySecurityMetadataSource;
@Autowired
public void setMyAccessDecisionManager(MyAccessDecisionManager myAccessDecisionManager) {
super.setAccessDecisionManager(myAccessDecisionManager);
}
@Override
public void init(FilterConfig arg0) throws ServletException {
}
@Override
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws IOException, ServletException {
FilterInvocation fi = new FilterInvocation(request, response, chain);
invoke(fi);
}
public void invoke(FilterInvocation fi) throws IOException, ServletException {
//這裡進行許可權驗證
InterceptorStatusToken token = super.beforeInvocation(fi);
try {
fi.getChain().doFilter(fi.getRequest(), fi.getResponse());
} finally {
super.afterInvocation(token, null);
}
}
@Override
public void destroy() {
}
@Override
public Class<?> getSecureObjectClass() {
return FilterInvocation.class;
}
@Override
public SecurityMetadataSource obtainSecurityMetadataSource() {
return this.mySecurityMetadataSource;
}
}
四、 加入到 security 的過濾器鏈中
.addFilterBefore(urlFilterSecurityInterceptor,FilterSecurityInterceptor.class)
完成
