apache伺服器中openssl配置https
阿新 • • 發佈:2019-01-11
最近需要研究下apache的簽名問題,主要是利用openssl來實現,就對openssl研究了下。
理論基礎:
OpenSSL初接觸的人恐怕最難的在於先理解各種概念 公鑰/私鑰/簽名/驗證簽名/加密/解密/非對稱加密 我們一般的加密是用一個密碼加密檔案,然後解密也用同樣的密碼.這很好理解,這個是對稱加密.而有些加密時,加密用的一個密碼,而解密用另外一組密碼,這個叫非對稱加密,意思就是加密解密的密碼不一樣.初次接觸的人恐怕無論如何都理解不了.其實這是數學上的一個素數積求因子的原理的應用,如果你一定要搞懂,百度有大把大把的資料可以看,其結果就是用這一組金鑰中的一個來加密資料,可以用另一個解開.是的沒錯,公鑰和私鑰都可以用來加密資料,相反用另一個解開,公鑰加密資料,然後私鑰解密的情況被稱為加密解密,私鑰加密資料,公鑰解密一般被稱為簽名和驗證簽名.實現方法:
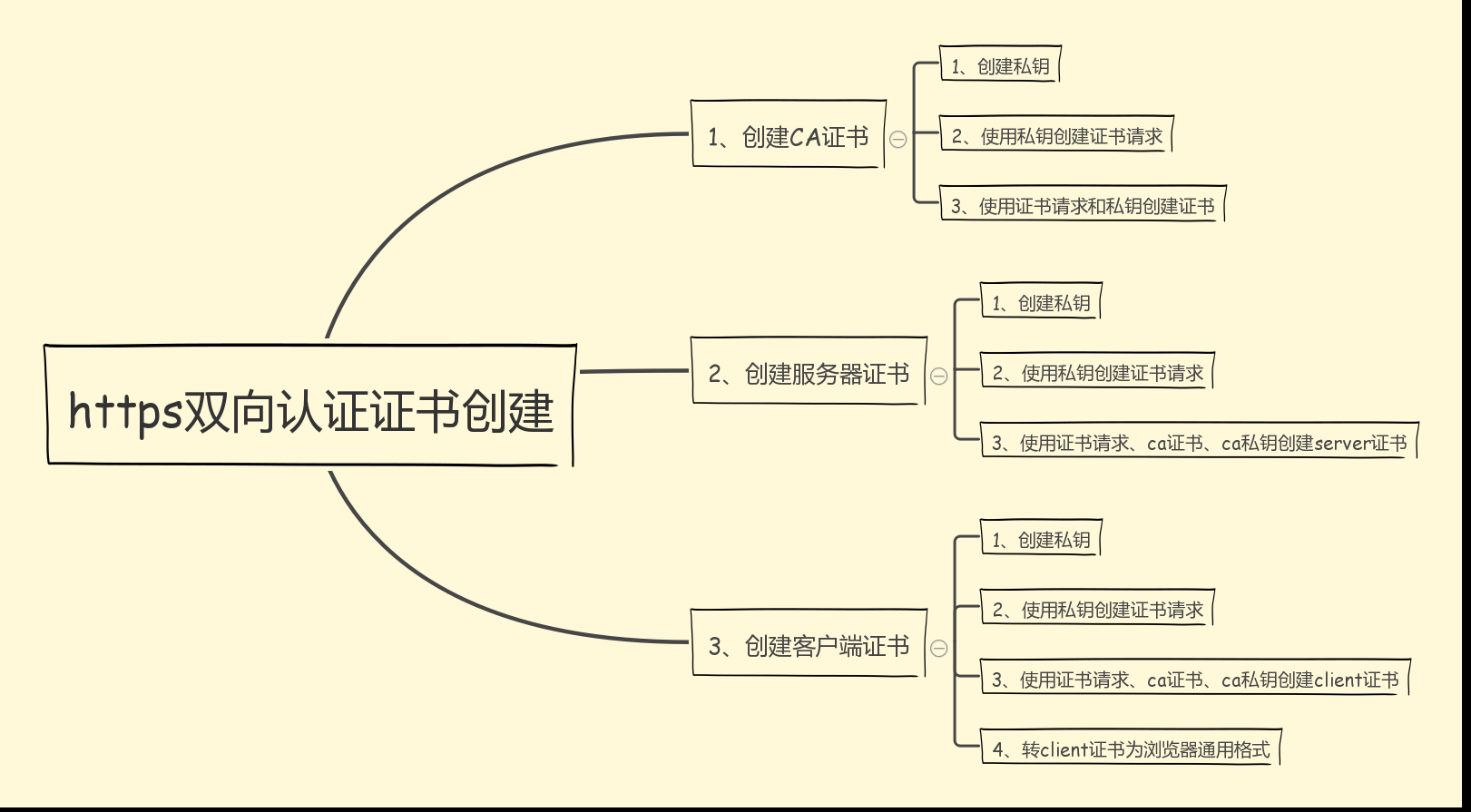
(1) 建立CA證書: # basedir="/data/webapps/apache/ca" # openssl genrsa -out private/ca.key 2048 # openssl req -new -key private/ca.key -out private/ca.csr # openssl x509 -req -days 365 -in private/ca.csr -signkey private/ca.key -out private/ca.crt # echo FACE > serial # touch index.txt # openssl ca -out ${basedir}/private/ca.crt -crldays 365 -config "${basedir}/conf/openssl.conf"(2) 建立伺服器證書 # openssl genrsa -out server/server.key 2048 # openssl req -new -key server/server.key -out server/server.csr # openssl ca -in server/server.csr -cert private/ca.crt -keyfile private/ca.key -out server/server.crt -config "${basedir}/conf/openssl.conf"(3) 建立client證書 # mkdir -p $base/users/ # openssl genrsa -des3 -out $base/users/client.key 1024 # openssl req -new -key $base/users/client.key -out $base/users/client.csr # openssl ca -in $base/users/client.csr -cert $base/private/ca.crt -keyfile $base/private/ca.key -out $base/users/client.crt -config "${base}/conf/openssl.conf" # openssl pkcs12 -export -clcerts -in $base/users/client.crt -inkey $base/users/client.key -out $base/users/client.p12過程中還會需要輸入一些註冊資訊。在執行之前需要注意openssl.conf的配置檔案,如下:
[ ca ]
default_ca = foo # The default ca section
[ foo ]
dir = /data/webapps/apache/ca # top dir
database = /data/webapps/apache/ca/index.txt # index file.
new_certs_dir = /data/webapps/apache/ca/newcerts # new certs dir
certificate = /data/webapps/apache/ca/private/ca.crt # The CA cert
serial = /data/webapps/apache/ca/serial # serial no file
private_key = /data/webapps/apache/ca/private/ca.key # CA private key
RANDFILE =/data/webapps/apache/ca/private/.rand # random number file
default_days = 365 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = md5 # message digest method to use
unique_subject = no # Set to 'no' to allow creation of
# several ctificates with same subject.
policy = policy_any # default policy
[ policy_any ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = match
localityName = optional
commonName = supplied
emailAddress = optionalSSLCertificateFile "/data/webapps/apache/ca/server/server.crt"
SSLCertificateKeyFile "/data/webapps/apache/ca/server/server.key"SSLCACertificateFile "/data/webapps/apache/ca/private/ca.crt"SSLVerifyClient require SSLVerifyDepth 10.
參考:
https://blog.csdn.net/qsj123one/article/details/53151412
https://blog.csdn.net/oldmtn/article/details/52208747