Create Write-Once-Read-Many Archive Storage with Amazon Glacier
Many AWS customers use Amazon Glacier for long-term storage of their mission-critical data. They benefit from Glacier’s durability and low cost, along with the ease with which they can integrate it in to their existing backup and archiving regimen. To use Glacier, you create vaults and populate them with archives
In certain industries, long-term records retention is mandated by regulations or compliance rules, sometimes for periods of up to seven years. For example, in the financial services industry (including large banks, broker-dealers, and securities clearinghouses), SEC Rule 17a-4(f) specifies that “electronic records must be preserved exclusively in a non-rewriteable and non-erasable format.” Other industries are tasked with meeting similar requirements when they store mission-critical information.
Lock Your Vaults
Today we are introducing a new Glacier feature that allows you to lock your vault with a variety of compliance controls that are designed to support this important records retention use case. You can now create a Vault Lock policy on a vault and lock it down. Once locked, the policy cannot be overwritten or deleted. Glacier will enforce the policy and will protect your records according to the controls (including a predefined retention period) specified therein.
You cannot change the Vault Lock policy after you lock it. However, you can still alter and configure the access controls that are not related to compliance by using a separate vault access policy. For example, you can grant read access to business partners or designated third parties (as sometimes required by regulation).
The Locking Process
Because the locking policy cannot be changed or removed after it is locked down (in order to assure compliance), we have implemented a two-step locking process in order to give you an opportunity to test it before locking the vault down for good. Here’s what you need to do:
- Call
InitiateVaultLockand pass along your Vault Lock retention policy. Glacier will install the policy and set the vault’s lock state to InProgress, and then return a unique LockID (keep this value around for 24 hours, after which it will expire). - Test your retention policy thoroughly. The vault will behave as though subject to the policy during the testing period. During this period you should thoroughly test the operations that are prohibited by the policy and ensure that they fail as expected. For example, you will probably want to test
DeleteArchiveandDeleteVaultattempts from the root account, all IAM users, and from any users with cross-account access. You should also let the 24 hour testing period go by and then test that users with proper permissions can delete the archives. - If you are satisfied that the policy works as expected, call
CompleteVaultLockwith the LockID that you dutifully saved in step 1, dust off your hands and stroll off into the sunset. The vault’s state will be set to Locked, and the policy will remain in effect until the heat death of the universe. - If the policy does not work as expected, call
AbortVaultLockduring the 24 hour window (or wait until it passes) in order to remove the in-progress policy. Refine the policy and start over at step 1.
In most cases, you should plan to create a vault, apply your locking policy, and then upload archives to the vault where they will be governed by the policy. This is because Vault Lock does not backdate existing archives or other activities that were performed before the vault was locked. As such, there is no way to ensure that they are in compliance with the policy.
Here’s a sample policy that implements a 365 day retention rule:
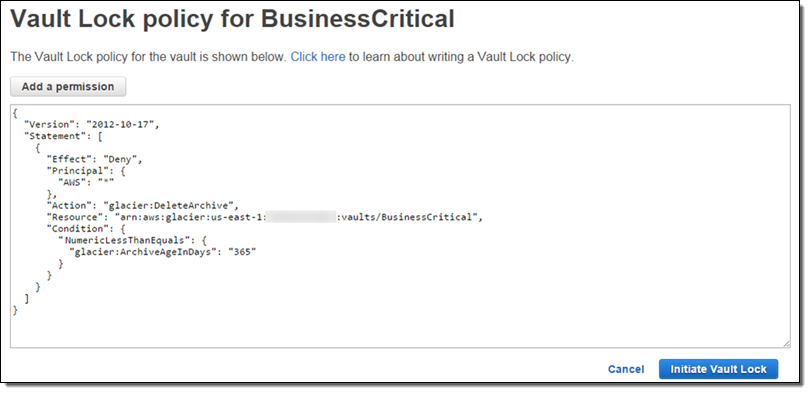
As you can see this policy denies everyone (AWS:*) the ability to use Glacier’s DeleteArchive function on the resource named vaults/BusinessCritical for a period of 365 days.
More Control
After you apply and finalize your locking policy, you can continue to use the existing vault access policy as usual. However, the vault access policy cannot reduce the effect of the retention controls in the locking policy.
In certain situations you may be faced with the need to place a legal hold on your compliance archives for an indefinite period of time, generally until an investigation of some sort is concluded. You can do this by creating a vault access policy that denies the use of Glacier’s Delete functions if the vault is tagged in a particular way. For example, the following policy will deny deletes if the LegalHold tag is present and set to true:
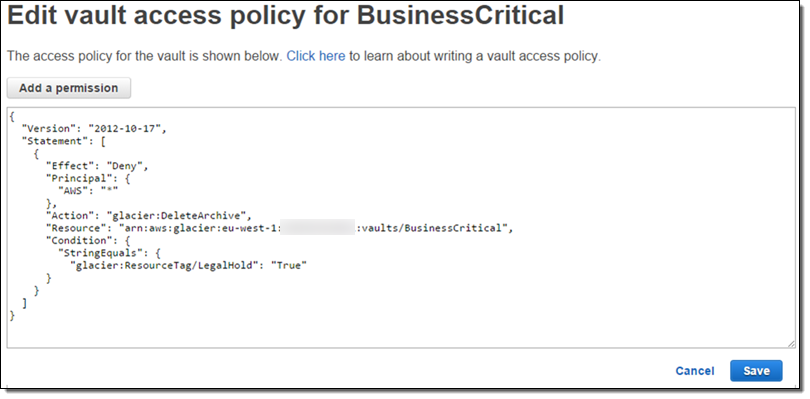
Once the investigation is over, you can remove the hold by changing the LegalHold tag to false.
From Our Customers
Records retention in the Financial Services industry is governed by strict regulatory requirements. In advance of today’s launch, several AWS Financial Services customers were given a sneak peek at Vault Lock to review the new features. Here’s what they had to say:
Lock up Today
This new feature is available now and you can start using it today. To learn more about this feature, read about Getting Started Amazon Glacier Vault Lock.
— Jeff;
相關推薦
Create Write-Once-Read-Many Archive Storage with Amazon Glacier
Many AWS customers use Amazon Glacier for long-term storage of their mission-critical data. They benefit from Glacier’s durability and low cost, a
32、【華為HCIE-Storage】--NAS特性 WORM(Write Once Read
HCIE Storage hostman ------------------------------------重要說明------------------------------------以下部分內容來網絡,部分自華為存儲官方教材具體教材內容請移步華為存儲官網進行教材下載 網絡引用內容
Multi-Tenant Storage with Amazon DynamoDB
Editor’s note: For the latest information, visit the . By Tod Golding, Partner Solutions Architect at AWS If you’re designing a tr
Write Once, Run Anywhere:這不是Java,這是C#
java註意,本文目的並非挑起語言之爭。雖然有為C#平反之意,但主要還是介紹Mono並進行簡單的測試。UPDATED: 25th August 2012更新了「Compile Once, Run Anywhere:跨平臺的終極目標」一節。 Conmajia 2012引言“Write once, run any
[AngularFire] Angular File Uploads to Firebase Storage with Angular control value accessor
state spa lec span tor event allow load loading The upload class will be used in the service layer. Notice it has a constructor for file
ERROR 1 (HY000): Can‘t create/write to file ‘/data
mariadb 數據導出 使用非DBA用戶進行load data 操作,發現報錯。MariaDB [temp_archive]> select * from t1 into outfile '/data/test.sql';ERROR 1 (HY000): Can't c
mysql啟動報can't create/write to file 'var/run/mysqld/mysqld.pid 錯誤解決辦法
msql啟動報錯,啟動不了。 進入mysql日誌預設的路徑為 /var/log/mysqld.log 檢視日誌,發現報錯資訊如下: can't create/write to file 'var/run/mysqld/mysqld.pid 解決辦法: 將 /var/run/my
Write and read opencv3.0 ml files(random forest)
using namespace cv; using namespace std; int main() { { auto rtrees = cv::ml::RTrees::create(); rtrees->setMaxDepth(10);
bug解決-核心C庫防寫(FORTIFY: write: prevented read past end of buffer)
備註:展訊平臺 1、問題描述 昨天同事問我一個問題,報的是一個native crash問題,問題log如下所示: 01-05 00:01:12.600 2794 6237 F libc : Fatal signal 6 (SIGABRT), code -6 in
TFrecord:write&read
參考了這位仁兄的部落格 概述 在訓練卷積神經網路時,將圖片提前處理好並快取在磁碟上,通過中間檔案隨機呼叫訪問可以明顯提高訓練速度,並且可以減少重複處理圖片的工作。 write 通過tf.train.Example Protocol Buffer 下面程式碼源於本人寫的一個函
【MySQL】MySQL5.7 匯入時報“cannot create a JSON value from a string with CHARACTER SET 'binary'.”錯誤的解決辦法
json是mysql 5.7版本才新增的資料型別,用mysql-front 6.0匯出時json欄位會自動轉換成十六進位制“X’7B226……227D”,而不是json格式。 所以在匯入時就會報錯。 我的解決辦法: 1.用notepad++等文字編輯器開啟.sql檔案;
Java的跨平臺實現原理(Write Once,Run Anywhere)
Java的跨平臺實現原理 為什麼要跨平臺 在不同點作業系統之間,使用不同的指令集對計算機進行控制。如果沒有跨平臺,我們需要對window,Linux,unix等作業系統的指令集分別進行特定的語言開發 Java如何實現 在不同的作業系統之間,提供不同的虛擬機器,讓虛擬機器實
java.sql.SQLException: Can't create/write to file '/root/apache-tomcat-7.0.42/webapps/AnationtSystem
java.sql.SQLException: Can’t get stat of ‘/root/apache-tomcat-7.0.42/webapps/AnationtSystem/upload/20180720093527_general.txt’ (Err
Hybrid collaborative tiered storage with Alluxio
應用程式從AWS S3或者阿里雲OSS讀取資料時,通常都會有嚴重的效能問題,畢竟是要通過遠端網路。 Alluxio可以提供一個透明的資料快取層,自動快取需要讀取遠端OSS/S3資料,但是Alluxio本身什麼時候拉取遠端資料呢?預設全部快取?還是按需快取?這個PPT裡將會介紹Alluxio的層次化儲存概念,結
mysql 啟動報錯 /usr/local/mysql//libexec/mysqld: Can't create/write to file '/var/run/mysqld/mysqld.pid'
centos檢視mysql日誌路徑:/var/log/mysqld.log 可能日誌過長,導致命令視窗檢視不方便,可以下載到本地,檢視ERROR 啟動mysql systemctl start mysqld 命令報錯看不出具體啟動失敗的原因,檢視日誌後發現如下錯誤:
linux中write和read函式的阻塞試驗
剛剛接觸網路程式設計時,很容易被客戶端和伺服器之間的互動搞暈,例如各種函式的阻塞和非阻塞就讓人頭疼。例如在我的印象中 linux中用於用於對檔案描述符進行讀寫的write()函式和read()函式是非阻塞函式,但是在一次網路通訊的試驗中發現它們又是阻 塞的,後
open、write、read函式及應用
#include <sys/types.h> #include <sys/stat.h> #include <fcntl.h> #include<stdio.h> #include<unistd.h> #include<stdli
解決:CentOS下MySQL執行select ... into outfile ...: Can't create/write to file '...' (Errcode: 13)
原因:selinux阻止寫入操作 解決:vi /etc/selinux/config # This file controls the state of SELinux on the system.
☕️ Write Once, Run Anywhere: 這不是 Java,這是 C#
注意,本文目的並非挑起語言之爭。雖然有為C#平反之意,但主要還是介紹Mono並進行簡單的測試。 UPDATED: 25th August 2012 更新了「Compile Once, Run Anywhere:跨平臺的終極目標」一節。 © Conmajia 2012 引言 “Write once,
Create a web app to visually interact with objects detected using machine learning
Summary The IBM Model Asset eXchange (MAX) has given application developers without data science experience easy access to prebuilt m
