自簽名證書以及DNS服務器搭建
TLS: Transport Layer Security 安全傳輸協議,在應用層 傳輸層之間主要應用https 協議,ftps 協議等
https大體流程
客戶端A 服務端B
A ————》 (連接請求 ) B
A《———— (發送CA私鑰加密過B的公鑰,也就是安全證書)B
A (用CA公鑰解開證書得到B的公鑰)
A (生成對稱秘鑰key,並用B的公鑰加密)
A ————》(加密的秘鑰key) B
B (B用自己的私鑰解密得到對稱私鑰key)
A B後續通訊使用對稱私鑰加密通訊
2.自簽證書
搭建私有CA,用於自簽名
- 安裝openssl
- 生成CA 私鑰
[root@centos7 ~]#(umask 066; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) Generating RSA private key, 2048 bit long modulus .................................................................................................+++ ..........+++ e is 65537 (0x10001)註意生成文件必須與/etc/pki/tls/openssl.cnf配置文件定義一致
dir = /etc/pki/CA # Where everything is kept
private_key = $dir/private/cakey.pem# The private key
而且生成文件權限為600 - CA服務器用自己私鑰自簽名生成證書
[root@centos7 ~]#openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7200 -out /etc/pki/CA/cacert.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:gd Locality Name (eg, city) [Default City]:gz Organization Name (eg, company) [Default Company Ltd]:nvliu Organizational Unit Name (eg, section) []:dcrfan Common Name (eg, your name or your server‘s hostname) []:centos7 Email Address []:註意生成文件必須與/etc/pki/tls/openssl.cnf配置文件定義一致
certificate = $dir/cacert.pem # The CA certificate
定義一些國家省份信息 - 把該證書傳輸到windows客戶端添加信任
- 更改後綴為.cer
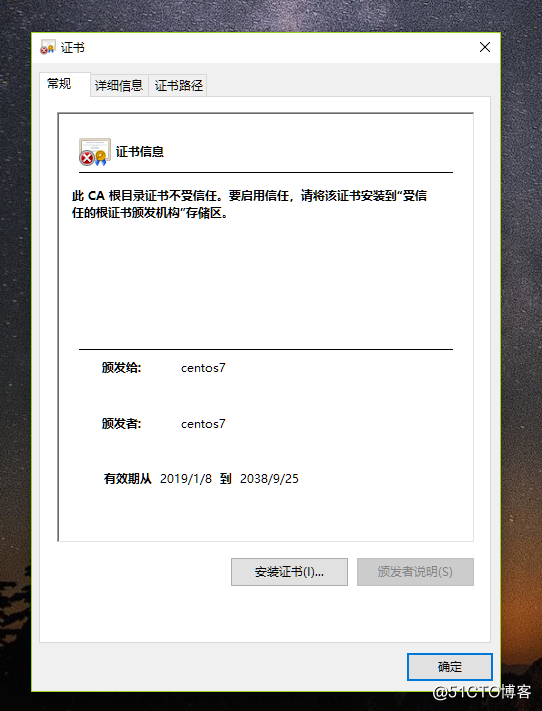
- 打開證書發現不受信任,點擊安裝證書
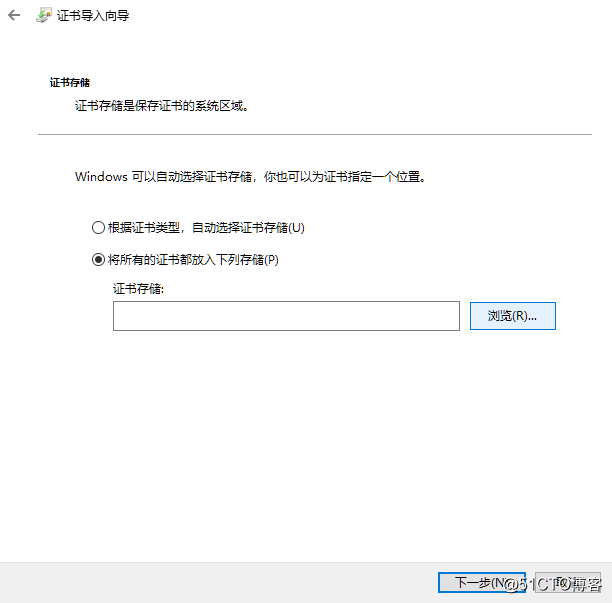
- 選擇證書存儲路徑
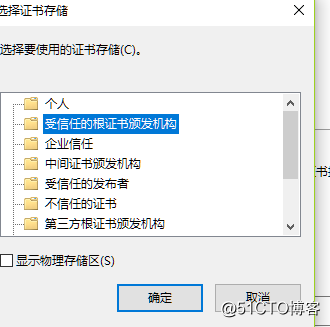
- 選擇受信任根證書
- 然後點擊是確定安裝
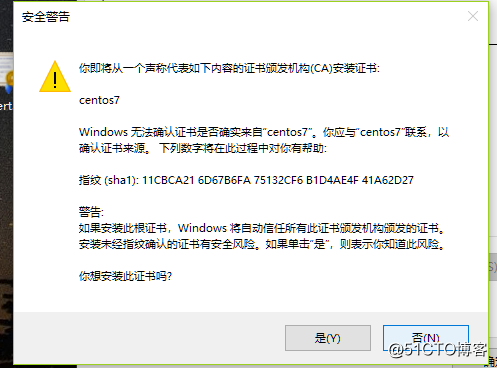
- 再次打開證書,已經被系統信任了
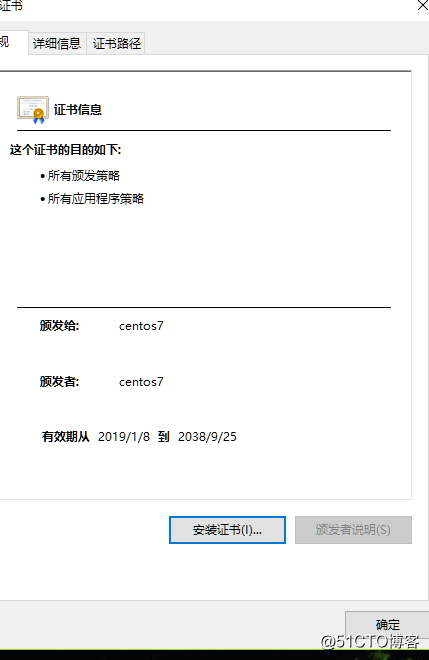
- 更改後綴為.cer
- 在應用服務器上生成密鑰,放在要使用應用文件下
[root@localhost ~]# (umask 066; openssl genrsa -out /data/app.key 2048) Generating RSA private key, 2048 bit long modulus ............................................+++ ........................+++ e is 65537 (0x10001)而且生成文件權限為600
[root@localhost ~]# (umask 066; openssl genrsa -out /data/app.key 2048)
Generating RSA private key, 2048 bit long modulus
............................................+++
........................+++
e is 65537 (0x10001) - 在應用服務器生成證書申請文件,然後上傳給CA服務器
[root@localhost ~]# openssl req -new -key /data/app.key -out /data/app.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:gd Locality Name (eg, city) [Default City]:gz Organization Name (eg, company) [Default Company Ltd]:nvliu Organizational Unit Name (eg, section) []:dcrfan1 Common Name (eg, your name or your server‘s hostname) []:centos7.1 Email Address []: Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: - 在CA服務器手動生成兩個文件
[root@centos7 ~]#echo 01 > /etc/pki/CA/serial [root@centos7 ~]#touch /etc/pki/CA/index.txt這兩個位置在/etc/pki/tls/openssl.cnf 均有定義
database = $dir/index.txt # database index file.
serial = $dir/serial # The current serial number - 在CA服務器對剛剛應用服務器傳過來申請審批,生成證書
[root@centos7 ~]#openssl ca -in /data/app.csr -out /etc/pki/CA/certs/app.crt -days 160 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Jan 8 11:23:04 2019 GMT Not After : Jun 17 11:23:04 2019 GMT Subject: countryName = cn stateOrProvinceName = gd organizationName = nvliu organizationalUnitName = dcrfan1 commonName = centos7.1 X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 2C:54:95:C8:30:80:97:89:7E:4A:40:50:F9:64:CB:2F:2E:D9:97:EA X509v3 Authority Key Identifier: keyid:48:8F:FB:78:84:50:F0:B0:AB:6F:2C:10:B6:03:9F:21:03:03:20:70 Certificate is to be certified until Jun 17 11:23:04 2019 GMT (160 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated註意生成文件必須與/etc/pki/tls/openssl.cnf配置文件定義一致
certs = $dir/certs # Where the issued certs are kept - 把生成的app,crt 拷貝會應用服務器使用
3.搭建DNS架構
實驗分別準備8臺實驗機器,
192.168.0.108 遠程訪問客服端
192.168.0.109 緩存dns服務器
192.168.0.112 dcrfan.com dns主服務器
192.168.0.113 dcrfan.com dns 從服務器
192.168.0.114 com dns服務器
192.168.0.115 根dns 服務器
192.168.0.116 web 服務器
192.168.0.117 web 服務器
- 先搭建dns主服務器192.168.0.112 ,安裝bind服務
- 修改主配置文件/etc/named.conf中文件
options { //listen-on port 53 { 127.0.0.1; }; #註釋該行,讓本服務器ip監聽53端口 allow-query { 192.168.0.0/24; }; # 修改改行,允許該網段的ip使用dns服務器 allow-transfer { 192.168.0.113; }; #新增改行,只允許從dns服務器拉取數據 }; - 修改zone文件/etc/named.rfc1912.zones,新增一個zone,用於解析dcrfan.com域
zone "dcrfan.com" IN { type master;#定義類型為主dns服務器 file "dcrfan.com.zone";#定義該域數據文件位置 }; - 新增dns數據記錄文件dcrfan.com.zone,註意權限,讓named賬戶能讀取該文件,文件在/var/named 目錄下
-rw-r-----. 1 root named 152 Jun 21 2007 dcrfan.com.zone@ IN SOA dns1.dcrfan.com. admin.dcrfan.com. ( 0 1D 1H 1W 3H ) NS dns1 NS dns2 dns1 A 192.168.0.112 dns2 A 192.168.0.113 srv A 192.168.0.116 srv A 192.168.0.117 www CNAME srv - 啟動服務,在遠程客戶端使用dig 命令測試
[root@centos6 ~]# dig www.dcrfan.com @192.168.0.112 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.112 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 60001 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;www.dcrfan.com. IN A ;; ANSWER SECTION: www.dcrfan.com. 86400 IN CNAME srv.dcrfan.com. srv.dcrfan.com. 86400 IN A 192.168.0.117 srv.dcrfan.com. 86400 IN A 192.168.0.116 ;; AUTHORITY SECTION: dcrfan.com. 86400 IN NS dns2.dcrfan.com. dcrfan.com. 86400 IN NS dns1.dcrfan.com. ;; ADDITIONAL SECTION: dns1.dcrfan.com. 86400 IN A 192.168.0.112 dns2.dcrfan.com. 86400 IN A 192.168.0.113 ;; Query time: 1 msec ;; SERVER: 192.168.0.112#53(192.168.0.112) ;; WHEN: Thu Jan 10 16:09:29 2019 ;; MSG SIZE rcvd: 152 - 搭建從dns服務器192.168.0.113 ,安裝dns服務
- 修改主配置文件/etc/named.conf中文件
options { //listen-on port 53 { 127.0.0.1; }; #註釋該行,讓本服務器ip監聽53端口 allow-query { 192.168.0.0/24; }; # 修改改行,允許該網段的ip使用dns服務器 allow-transfer { none; }; #新增改行,不允許任何dns服務器拉取數據 }; - 修改zone文件/etc/named.rfc1912.zones,新增一個zone,用於解析dcrfan.com域
zone "dcrfan.com" IN { type slave;#定義類型是從dns服務器 masters { 192.168.0.112; }; #指定主dns服務器 file "slaves/dcrfan.com.slave.zone"; #dns記錄數據存放位置 }; - 啟動dns服務,查看dns數據文件已經同步到slaves文件夾下
[root@localhost ~]# ll /var/named/slaves/dcrfan.com.slave.zone -rw-r--r--. 1 named named 371 Jan 10 16:38 /var/named/slaves/dcrfan.com.slave.zone - 在遠程客戶端使用dig 命令測試
[root@centos6 ~]# dig www.dcrfan.com @192.168.0.113 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.113 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38752 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;www.dcrfan.com. IN A ;; ANSWER SECTION: www.dcrfan.com. 86400 IN CNAME srv.dcrfan.com. srv.dcrfan.com. 86400 IN A 192.168.0.117 srv.dcrfan.com. 86400 IN A 192.168.0.116 ;; AUTHORITY SECTION: dcrfan.com. 86400 IN NS dns2.dcrfan.com. dcrfan.com. 86400 IN NS dns1.dcrfan.com. ;; ADDITIONAL SECTION: dns1.dcrfan.com. 86400 IN A 192.168.0.112 dns2.dcrfan.com. 86400 IN A 192.168.0.113 ;; Query time: 4 msec ;; SERVER: 192.168.0.113#53(192.168.0.113) ;; WHEN: Thu Jan 10 16:41:18 2019 ;; MSG SIZE rcvd: 152 - 配置com dns服務器192.168.0.114 ,安裝dns服務
- 修改主配置文件/etc/named.conf中文件
options { //listen-on port 53 { 127.0.0.1; }; #註釋該行,讓本服務器ip監聽53端口 //allow-query { 192.168.0.0/24; }; # 註釋改行,允許所有ip使用dns服務器 dnssec-enable no; dnssec-validation no; #都修改為no }; - 修改zone文件/etc/named.rfc1912.zones,新增一個zone,用於解析com域和指派dcrfan.com域(使用dns轉發)
zone "dcrfan.com" IN { type forward; forward first; forwarders { 192.168.0.112; 192.168.0.113;}; }; - 啟動服務,在遠程客戶端使用dig 命令測試
[root@centos6 ~]# dig www.dcrfan.com @192.168.0.114 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.114 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26492 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;www.dcrfan.com. IN A ;; ANSWER SECTION: www.dcrfan.com. 86400 IN CNAME srv.dcrfan.com. srv.dcrfan.com. 86400 IN A 192.168.0.117 srv.dcrfan.com. 86400 IN A 192.168.0.116 ;; AUTHORITY SECTION: dcrfan.com. 86400 IN NS dns2.dcrfan.com. dcrfan.com. 86400 IN NS dns1.dcrfan.com. ;; ADDITIONAL SECTION: dns1.dcrfan.com. 86400 IN A 192.168.0.112 dns2.dcrfan.com. 86400 IN A 192.168.0.113 ;; Query time: 14 msec ;; SERVER: 192.168.0.114#53(192.168.0.114) ;; WHEN: Thu Jan 10 17:18:21 2019 ;; MSG SIZE rcvd: 152 - 配置根 dns服務器192.168.0.115 ,安裝dns服務
- 修改主配置文件/etc/named.conf中文件
options { //listen-on port 53 { 127.0.0.1; }; #註釋該行,讓本服務器ip監聽53端口 //allow-query { 192.168.0.0/24; }; # 註釋改行,允許所有ip使用dns服務器 dnssec-enable no; dnssec-validation no; #都修改為no }; zone "." IN { #刪除這個根zone type hint; file "named.ca"; }; - 修改zone文件/etc/named.rfc1912.zones,新增一個zone,用於解析根域
zone "." IN { type master;#定義類型為主dns服務器 file "root.zone";#定義該域數據文件位置 }; - 新增dns數據記錄文件root.zone,註意權限,讓named賬戶能讀取該文件
文件在新增dns數據記錄文件dcrfan.com.zone,註意權限,讓named賬戶能讀取該文件,文件在/var/named下
$TTL 1D@ IN SOA dns1. admin. ( 0 1D 1H 1W 3H ) NS dns1 com NS dns2 #指派com域到192.168.0.114管理 dns1 A 192.168.0.115 dns2 A 192.168.0.114 - 啟動服務,在遠程客戶端使用dig 命令測試
[root@centos6 ~]# dig www.dcrfan.com @192.168.0.115 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.115 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51669 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;www.dcrfan.com. IN A ;; ANSWER SECTION: www.dcrfan.com. 84281 IN CNAME srv.dcrfan.com. srv.dcrfan.com. 86400 IN A 192.168.0.117 srv.dcrfan.com. 86400 IN A 192.168.0.116 ;; AUTHORITY SECTION: dcrfan.com. 84281 IN NS dns2.dcrfan.com. dcrfan.com. 84281 IN NS dns1.dcrfan.com. ;; ADDITIONAL SECTION: dns1.dcrfan.com. 84281 IN A 192.168.0.112 dns2.dcrfan.com. 84281 IN A 192.168.0.113 ;; Query time: 14 msec ;; SERVER: 192.168.0.115#53(192.168.0.115) ;; WHEN: Thu Jan 10 17:53:40 2019 ;; MSG SIZE rcvd: 152 ` - 配置緩存服務器192.168.0.108 ,安裝named服務
- 修改主配置文件/etc/named.conf中文件
options { //listen-on port 53 { 127.0.0.1; }; #註釋該行,讓本服務器ip監聽53端口 //allow-query { 192.168.0.0/24; }; # 註釋改行,允許所有ip使用dns服務器 dnssec-enable no; dnssec-validation no; #都修改為no }; - 修改named.ca文件,讓它的根指向我們搭建跟服務器192.168.0.115
. 518400 IN NS a.root-servers.net. a.root-servers.net. 3600000 IN A 192.168.0.115 - 啟動服務,在遠程客戶端使用dig 命令測試
[root@centos6 ~]# dig www.dcrfan.com @192.168.0.109 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.109 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41909 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;www.dcrfan.com. IN A ;; ANSWER SECTION: www.dcrfan.com. 83143 IN CNAME srv.dcrfan.com. srv.dcrfan.com. 86400 IN A 192.168.0.116 srv.dcrfan.com. 86400 IN A 192.168.0.117 ;; AUTHORITY SECTION: dcrfan.com. 83143 IN NS dns1.dcrfan.com. dcrfan.com. 83143 IN NS dns2.dcrfan.com. ;; ADDITIONAL SECTION: dns2.dcrfan.com. 83143 IN A 192.168.0.113 dns1.dcrfan.com. 83143 IN A 192.168.0.112 ;; Query time: 16 msec ;; SERVER: 192.168.0.109#53(192.168.0.109) ;; WHEN: Thu Jan 10 18:12:37 2019 ;; MSG SIZE rcvd: 152 - 然後搭建兩個web服務器測試,分別安裝httpd服務,並修改主頁,啟動服務測試
echo dcrfan1 > /var/www/html/index.html
echo dcrfan2 > /var/www/html/index.html - 分別用ip正常訪問
[root@centos6 ~]# curl 192.168.0.116
dcrfan1
[root@centos6 ~]# curl 192.168.0.117
dcrfan2 - 修改客服端的dns指向緩存dns服務器192.168.0.109
網卡中加入DNS1=192.168.0.109,重啟網絡服務測試[root@centos6 ~]# curl www.dcrfan.com dcrfan2 [root@centos6 ~]# curl www.dcrfan.com dcrfan1 - 清理dns緩存,在各個dns服務器執行rndc flush命令
停掉主dns的服務,繼續測試,從服務器可以使用[root@centos6 ~]# curl www.dcrfan.com dcrfan2 [root@centos6 ~]# curl www.dcrfan.com dcrfan2 [root@centos6 ~]# curl www.dcrfan.com dcrfan1
4.dnspod解析類型
- 在dnspod中的記錄,一般有主機記錄,記錄類型,線路類型,記錄值,MX優先值,TTL
主機記錄:
www 表示 解析後域名為 www
@表示 直接解析主域名
表示泛解析 .域名 - 記錄類型
A記錄:用來指定域名的IPv4地址,如果需要將域名指向一個IP地址需要一個A記錄
CNAME:(別名) 如果需要將域名指向另一個域名,再由另一個域名提供ip地址,就需要添加CNAME記錄。
TXT:在這裏可以填寫任何東西,長度限制255。絕大多數的TXT記錄是用來做SPF記錄(反垃圾郵件)。
NS:dns服務器記錄,如果需要把子域名交給其他DNS服務器解析,就需要添加NS記錄。
AAAA:ipv6 的A記錄
MX:設置郵箱服務器地址解析,就需要添加MX記錄。
顯性URL:從一個地址301重定向到另一個地址的時候,就需要添加顯性URL記錄(註:DNSPod目前只支持301重定向)。
隱性URL:類似於顯性URL,區別在於隱性URL不會改變地址欄中的域名。
SRV:記錄了哪臺計算機提供了哪個服務。格式為:服務的名字、點、協議的類型 - 記錄值:
A記錄填寫相應ip地址
CNAME 填寫別名的域名
MX 郵件服務器ip地址
NS dns服務器域名(需要配合A記錄來指定ip地址) - MX郵件記錄還要記錄MX優先值
自簽名證書以及DNS服務器搭建
