Android O CTS 測試之Media相關測試小結(二)
CtsMediaTestCases
android.media.cts.VideoDecoderPerfTest failed
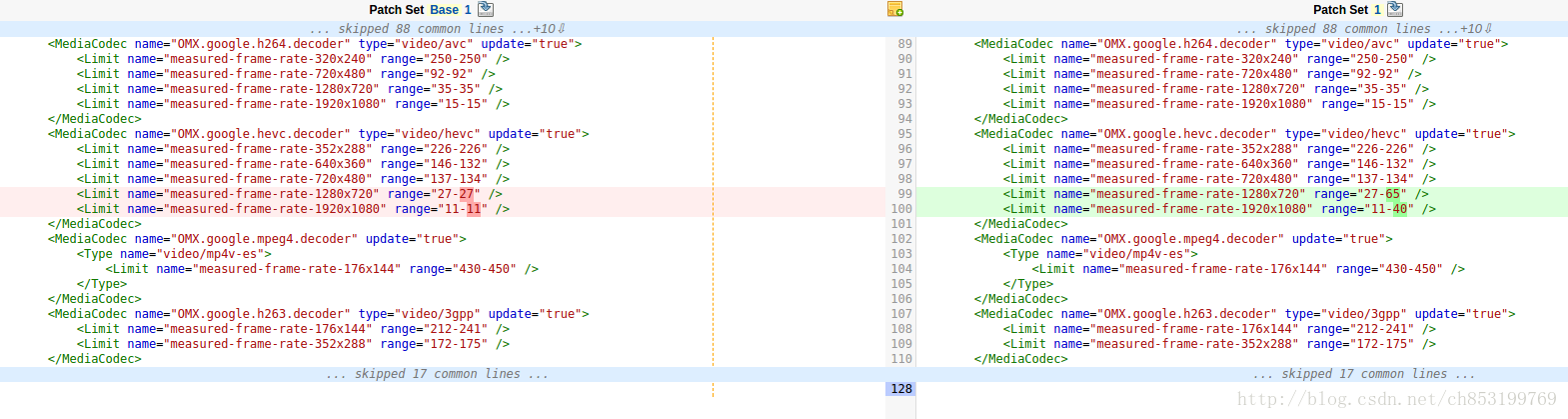
failed 項:android.media.cts.VideoDecoderPerfTest#testHevcGoog0Perf1280x0720 fail
failed information:junit.framework.AssertionFailedError: Expected achievable frame rates for OMX.google.hevc.decoder video/hevc 1280x720: [27.0, 27.0].
failed 項
failed information:junit.framework.AssertionFailedError: Expected achievable frame rates for OMX.google.hevc.decoder video/hevc 1920x1080: [11.0, 11.0].
對於此類failed項需要多跑幾次failed case,找到合適的codec performance limit 的範圍.在測試的log中可以找到當時測試時的值
相應的檔案media_codecs_performance.xml在android的system/vendor/etc目錄下
專案程式碼中的路徑是:
qcom/msm8937_32/media/media_codecs_performance_8937.xmlandroid.media.cts.AudioManagerTest#testAccessRingMode failed
Android 8.1
FAILED INFRAMATION:
01-02 01:45:09.530 7918 7935 I TestRunner: started: testAccessRingMode(android.media.cts.AudioManagerTest)
01-02 01:45:09.536 7918 7918 I MonitoringInstr: Activities that are still in isNotificationPolicyAccessGranted())返回了false與期望不符合;
protected static void toggleNotificationPolicyAccess(String packageName,
Instrumentation instrumentation, boolean on) throws IOException {
......
NotificationManager nm = (NotificationManager) instrumentation.getContext()
.getSystemService(Context.NOTIFICATION_SERVICE);
Assert.assertEquals("Wrote setting should be the same as the read one", on,
nm.isNotificationPolicyAccessGranted());
}檢視:isNotificationPolicyAccessGranted
最終發現:
private boolean checkPolicyAccess(String pkg) {
2582 try {
2583 int uid = getContext().getPackageManager().getPackageUidAsUser(
2584 pkg, UserHandle.getCallingUserId());
2585 if (PackageManager.PERMISSION_GRANTED == ActivityManager.checkComponentPermission(
2586 android.Manifest.permission.MANAGE_NOTIFICATIONS, uid,
2587 -1, true)) {
2588 return true;
2589 }
2590 } catch (NameNotFoundException e) {
2591 return false;
2592 }
2593 return checkPackagePolicyAccess(pkg) || mListeners.isComponentEnabledForPackage(pkg);
2594 }cts media測試沒有android.Manifest.permission.MANAGE_NOTIFICATIONS的許可權
最終確認是已知的google issue,向Google申請豁免
同樣還有如下類似的failed項
failed項:
android.media.cts.AudioManagerTest#testAdjustVolumeInAlarmsOnlyMode fail
android.media.cts.AudioManagerTest#testAdjustVolumeInTotalSilenceMode fail
android.media.cts.AudioManagerTest#testSetStreamVolumeInAlarmsOnlyMode fail
android.media.cts.AudioManagerTest#testSetStreamVolumeInTotalSilenceMode fail
Information:
java.lang.SecurityException: Notification policy access denied
5604 5622 I TestRunner: failed: testAdjustVolumeInAlarmsOnlyMode(android.media.cts.AudioManagerTest)
01-02 01:30:29.822 5604 5622 I TestRunner: ----- begin exception -----
01-02 01:30:29.825 5604 5622 I TestRunner: java.lang.SecurityException: Notification policy access denied
01-02 01:30:29.825 5604 5622 I TestRunner: at android.os.Parcel.readException(Parcel.java:2004)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.os.Parcel.readException(Parcel.java:1950)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.app.INotificationManager$Stub$Proxy.setInterruptionFilter(INotificationManager.java:2247)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.app.NotificationManager.setInterruptionFilter(NotificationManager.java:1194)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.media.cts.AudioManagerTest.setInterruptionFilter(AudioManagerTest.java:919)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.media.cts.AudioManagerTest.testAdjustVolumeInAlarmsOnlyMode(AudioManagerTest.java:858)
01-02 01:30:29.825 5604 5622 I TestRunner: at java.lang.reflect.Method.invoke(Native Method)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.test.InstrumentationTestCase.runMethod(InstrumentationTestCase.java:220)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.test.InstrumentationTestCase.runTest(InstrumentationTestCase.java:205)
01-02 01:30:29.825 5604 5622 I TestRunner: at junit.framework.TestCase.runBare(TestCase.java:134)
01-02 01:30:29.825 5604 5622 I TestRunner: at junit.framework.TestResult$1.protect(TestResult.java:115)原因: 已知的google issue,向Google申請豁免
[STS] CtsSecurityTestCases
android.security.cts.StagefrightTest#testStagefright_bug_34896431
Test failed to run to completion. Reason: ‘Instrumentation run failed due to ‘Process crashed.”. Check device logcat for details
08-02 23:30:12.572 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.572 895 7081 F DEBUG : *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
08-02 23:30:12.572 895 7081 F DEBUG : Build fingerprint: 'WIKO/W-P220-OPE/W-P220:8.1.0/OPM1.171019.019/androi08021339:userdebug/release-keys'
08-02 23:30:12.572 895 7081 F DEBUG : Revision: '0'
08-02 23:30:12.572 895 7081 F DEBUG : ABI: 'arm'
08-02 23:30:12.572 895 7081 F DEBUG : pid: 895, tid: 7081, name: media.codec >>> [email protected]1.0-service <<<
08-02 23:30:12.573 895 7081 F DEBUG : signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x8
08-02 23:30:12.573 895 7081 F DEBUG : Cause: null pointer dereference
08-02 23:30:12.577 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.583 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.587 895 7081 F DEBUG : r0 00000000 r1 00000000 r2 f09830a0 r3 efc04014
08-02 23:30:12.587 895 7081 F DEBUG : r4 ffffc000 r5 efc05014 r6 00000000 r7 f0983378
08-02 23:30:12.587 895 7081 F DEBUG : r8 f0983000 r9 00000000 sl f09830a1 fp f0583000
08-02 23:30:12.587 895 7081 F DEBUG : ip 00000001 sp ef5633b0 lr efc00000 pc eff9aa6c cpsr 600f0010
08-02 23:30:12.588 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.593 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.599 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.604 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.609 895 7081 F DEBUG :
08-02 23:30:12.609 895 7081 F DEBUG : backtrace:
08-02 23:30:12.609 895 7081 F DEBUG : #00 pc 00019a6c /system/lib/libstagefright_soft_hevcdec.so (ihevcd_parse_slice_data+544)
08-02 23:30:12.609 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.610 895 7081 F DEBUG : #01 pc 0000f160 /system/lib/libstagefright_soft_hevcdec.so (ihevcd_decode+1596)
08-02 23:30:12.610 895 7081 F DEBUG : #02 pc 0000a619 /system/lib/libstagefright_soft_hevcdec.so (android::SoftHEVC::onQueueFilled(unsigned int)+252)
08-02 23:30:12.610 895 7081 F DEBUG : #03 pc 0003d9e7 /system/lib/libstagefright_omx.so (android::SimpleSoftOMXComponent::onMessageReceived(android::sp<android::AMessage> const&)+254)
08-02 23:30:12.610 895 7081 F DEBUG : #04 pc 0003e9e1 /system/lib/libstagefright_omx.so
08-02 23:30:12.610 895 7081 F DEBUG : #05 pc 00010909 /system/lib/libstagefright_foundation.so (android::AHandler::deliverMessage(android::sp<android::AMessage> const&)+24)
08-02 23:30:12.610 895 7081 F DEBUG : #06 pc 00012ba9 /system/lib/libstagefright_foundation.so (android::AMessage::deliver()+48)
08-02 23:30:12.610 895 7081 F DEBUG : #07 pc 000114c1 /system/lib/libstagefright_foundation.so (android::ALooper::loop()+468)
08-02 23:30:12.610 895 7081 F DEBUG : #08 pc 0000d2a9 /system/lib/vndk-sp/libutils.so (android::Thread::_threadLoop(void*)+180)
08-02 23:30:12.611 895 7081 F DEBUG : #09 pc 0004706b /system/lib/libc.so (__pthread_start(void*)+22)
08-02 23:30:12.611 895 7081 F DEBUG : #10 pc 0001af31 /system/lib/libc.so (__start_thread+32)
08-02 23:30:12.615 6812 6829 I StagefrightTest: no input buffer類似的failed項需要檢視Google bug_34896431 相關的security patch有沒有合入,這種failed case,一般是因為少合入的一部分security patch,或者就是是 平臺有關的庫的bug了,需平臺提供支援
解決的patch是:
diff --git a/drivers/media/platform/msm/vidc/msm_vdec.c b/drivers/media/platform/msm/vidc/msm_vdec.c
index 86b7b1b..579f032 100644
--- a/drivers/media/platform/msm/vidc/msm_vdec.c
+++ b/drivers/media/platform/msm/vidc/msm_vdec.c
@@ -1,4 +1,4 @@
-/* Copyright (c) 2012-2017, The Linux Foundation. All rights reserved.
+/* Copyright (c) 2012-2018, The Linux Foundation. All rights reserved.
*
* This program is free software; you can redistribute it and/or modify
* it under the terms of the GNU General Public License version 2 and
@@ -22,6 +22,7 @@
#define MSM_VDEC_DVC_NAME "msm_vdec_8974"
#define MIN_NUM_OUTPUT_BUFFERS 4
#define MIN_NUM_OUTPUT_BUFFERS_VP9 6
+#define MIN_NUM_OUTPUT_BUFFERS_HEVC 5
#define MIN_NUM_CAPTURE_BUFFERS 6
#define MIN_NUM_THUMBNAIL_MODE_CAPTURE_BUFFERS 1
#define MAX_NUM_OUTPUT_BUFFERS VB2_MAX_FRAME
@@ -1494,6 +1495,10 @@ static int msm_vdec_queue_setup(struct vb2_queue *q,
V4L2_PIX_FMT_VP9 &&
*num_buffers < MIN_NUM_OUTPUT_BUFFERS_VP9)
*num_buffers = MIN_NUM_OUTPUT_BUFFERS_VP9;
+ else if (inst->fmts[OUTPUT_PORT].fourcc ==
+ V4L2_PIX_FMT_HEVC &&
+ *num_buffers < MIN_NUM_OUTPUT_BUFFERS_HEVC)
+ *num_buffers = MIN_NUM_OUTPUT_BUFFERS_HEVC;
for (i = 0; i < *num_planes; i++) {
sizes[i] = get_frame_size(inst,android.security.cts.StagefrightTest#testStagefright_bug_63522067
FAILED INFORMATION:
junit.framework.AssertionFailedError: Device *IS* vulnerable to BUG-63522067-3-HEVC
at junit.framework.Assert.fail(Assert.java:50)
at junit.framework.Assert.assertTrue(Assert.java:20)
at junit.framework.Assert.assertFalse(Assert.java:34)
at android.security.cts.StagefrightTest.doStagefrightTestRawBlob(StagefrightTest.java:1511)
at android.security.cts.StagefrightTest.testStagefright_bug_63522067(StagefrightTest.java:532) at java.lang.reflect.Method.invoke(Native Method)
at android.test.InstrumentationTestCase.runMethod(InstrumentationTestCase.java:220)
at android.test.InstrumentationTestCase.runTest(InstrumentationTestCase.java:205)
at junit.framework.TestCase.runBare(TestCase.java:134)
at junit.framework.TestResult$1.protect(TestResult.java:115)
at android.support.test.internal.runner.junit3.AndroidTestResult.runProtected(AndroidTestResult.java:77) at junit.framework.TestResult.run(TestResult.java:118)
at android.support.test.internal.runner.junit3.AndroidTestResult.run(AndroidTestResult.java:55) at junit.framework.TestCase.run(TestCase.java:124)
at android.support.test.internal.runner.junit3.NonLeakyTestSuite$NonLeakyTest.run(NonLeakyTestSuite.java:63)
at android.support.test.internal.runner.junit3.AndroidTestSuite$2.run(AndroidTestSuite.java:111) at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:457)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1162)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:636)
at java.lang.Thread.run(Thread.java:764)同上分析,檢查security 相關的patch全部合入,考慮使用的decoder是qcom hevc decoder,結合log看可能是平臺相關的hevc的解碼的庫的問題, 合入下面的patch驗證OK
diff --git a/decoder/ihevcd_decode.c b/decoder/ihevcd_decode.c
index 83f9b42..d2ea7a5 100755
--- a/decoder/ihevcd_decode.c
+++ b/decoder/ihevcd_decode.c
@@ -670,7 +670,6 @@ WORD32 ihevcd_decode(iv_obj_t *ps_codec_obj, void *pv_api_ip, void *pv_api_op)
if(IHEVCD_IGNORE_SLICE == ret)
{
- ps_codec->s_parse.i4_cur_slice_idx = MAX(0, (ps_codec->s_parse.i4_cur_slice_idx - 1));
ps_codec->pu1_inp_bitsbuf += (nal_ofst + nal_len);
ps_codec->i4_bytes_remaining -= (nal_ofst + nal_len);
diff --git a/decoder/ihevcd_parse_headers.c b/decoder/ihevcd_parse_headers.c
index b8ed252..fd8712b 100755
--- a/decoder/ihevcd_parse_headers.c
+++ b/decoder/ihevcd_parse_headers.c
@@ -2623,20 +2621,8 @@ void ihevcd_parse_sei_payload(codec_t *ps_codec,
case SEI_USER_DATA_REGISTERED_ITU_T_T35:
ps_parse->s_sei_params.i1_sei_parameters_present_flag = 1;
- if(ps_parse->s_sei_params.i4_sei_user_data_cnt >= USER_DATA_MAX)
- {
- for(i = 0; i < u4_payload_size / 4; i++)
- {
- ihevcd_bits_flush(ps_bitstrm, 4 * 8);
- }
-- ihevcd_bits_flush(ps_bitstrm, (u4_payload_size - i * 4) * 8);
- }
- else
- {
- ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
- u4_payload_size);
- }
+ ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
+ u4_payload_size);
break;
default:
@@ -2653,20 +2639,8 @@ void ihevcd_parse_sei_payload(codec_t *ps_codec,
{
case SEI_USER_DATA_REGISTERED_ITU_T_T35:
ps_parse->s_sei_params.i1_sei_parameters_present_flag = 1;
- if(ps_parse->s_sei_params.i4_sei_user_data_cnt >= USER_DATA_MAX)
- {
- for(i = 0; i < u4_payload_size / 4; i++)
- {
- ihevcd_bits_flush(ps_bitstrm, 4 * 8);
- }
-- ihevcd_bits_flush(ps_bitstrm, (u4_payload_size - i * 4) * 8);
- }
- else
- {
- ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
- u4_payload_size);
- }
+ ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
+ u4_payload_size);
break; 相關推薦
Android O CTS 測試之Media相關測試小結(二)
CtsMediaTestCases android.media.cts.VideoDecoderPerfTest failed failed 項:android.media.cts.VideoDecoderPerfTest#testHevcGoog
Android入門之文件系統操作(二)文件操作相關指令
-h tools strong abc his art 為什麽 重命名 path (一)獲取總根 [java] view plain copy File[] fileList=File.listRoots(); //返回fileList.length為1 /
2018-1-15性能測試之虛擬用戶開發(1)
base window 體系 工作 網絡 平臺 嵌入 class 神馬 1.1Vuser開發前的準備 1)深入了解系統功能:深入了解系統是進行性能需求分析的前提。2)深入了解系統架構:分析系統的架構弄清楚開展測試需要做哪些準備工作,系統潛在的壓力點在哪,確定重點模擬用戶的哪
軟體測試之實用小工具推薦(1)
1.Snipaste截圖工具 Snipaste是一款佔用記憶體很小而且免費的截圖軟體,在windows的商城中即可找到這款軟體並下載安裝,安裝後他會一直後臺執行,直到你喚醒他的時候再出現; 使用Snipaste截圖主要有兩種方式,一種是使用快捷鍵截圖,預設操作
Web安全測試之跨站請求偽造(CSRF)
跨站請求偽造(即CSRF)被Web安全界稱為諸多漏洞中“沉睡的巨人”,其威脅程度由此“美譽”便可見一斑。本文將簡單介紹該漏洞,並詳細說明造成這種漏洞的原因所在,以及針對該漏洞的黑盒測試與灰盒子測試具體方法和示例,最後提提了一些防範該攻擊的建議,希望本文對讀者的安全測試
小白學習安全測試——httrack的安裝和使用(二)
type mas track base launch 驗證 解決方案 我沒 ted httrack是一款免費的網站鏡像程序,簡單理解就是可以在網站結構(網頁及一些主要信息文件),下載到本地,可離線瀏覽,我是按照搭建成功後的console直譯過來的 下面說下安裝: 我都是在L
使用“數據驅動測試”之前你應該知道的(二)
clas back args ase 沒有 告訴 ... last 數據文件 我們繼續上期的話題,單純讀取數據文件來做自動化是有諸多問題的。那麽我們借助單元測試框架來做自動化就爽多了,因為它解決了測試中的幾問題。 如何定義一條測試用例,我們知道編程的世界裏並沒“用例”的概
Android開發技巧之:QQ第三方登入(二)
接 android QQ第三方登入(一) 獲取登入使用者名稱資訊,這邊先抱怨一下,官方API有點坑 Constants原始碼類下就是找不到GRAPH_SIMPLE_USER_INFO這個屬性!無語! 根據官方提供返回的的JSONObject資訊解析:
軟體測試工程師筆試題及答案(二)
測試人員考試試卷二(考試時間90分鐘,滿分100分) 一、 判斷題(每題2分,正確的“√”,錯誤的“╳”) 1 、 好的測試員不懈追求完美。(×) 2、 測試程式僅僅按預期方式執行就行了。(×) 3、 不存在質量很高
Android之開啟專案的經驗(二)
若你的專案開啟成功,但是在編譯執行的時候報出這個錯誤: annotations processors must be explicitly declared now 你只需要在gradle-defaultConfig中新增一句話就可以了: javaCompile
1128UI自動化測試經驗分享-顯式等待(二)expected_conditions模組、visibility_of_element_located(locator)
expected_conditions模組 提供的預期條件判斷類【模組包含一套預定義的條件集合】,大大方便了 WebDriverWait 的使用。 一)expected_conditions模組 這兒是官方文件 https://seleniumhq.github.io/s
Android火車票訂購軟體之註冊和檔案儲存(2)
上次我們做了app啟動時的延時頁,這次我們來做登陸註冊的頁面。 xml程式碼: <?xml version="1.0" encoding="utf-8"?> <LinearLayout xmlns:android="http://schemas.android.c
Android網路程式設計之傳遞資料給伺服器(二)
我曾在《Android網路程式設計之傳遞資料給伺服器(一) 》一文中介紹瞭如何通過GET方式傳遞資料給伺服器,通過GET方式傳遞資料主要適用於資料大小不超過2KB,且對安全性要求不高的情況下。下面就介紹通過POST方式傳遞資料主到伺服器。 一、通過P
從零開始學Android自定義View之動畫系列——屬性動畫(3)
屬性動畫對補間動畫進行了很大幅度的改進,之前補間動畫可以做到的屬性動畫也能做到,補間動畫做不到的現在屬性動畫也可以做到了。因此,今天我們就來學習一下屬性動畫的高階用法,看看如何實現一些補間動畫所無法實現的功能。 ValueAnimator的高階用法 補間
Android O(8.0)音訊write資料流程變化(HIDL)
簡單回顧下,Audio write資料流程, AudioTrack->write AudioFlinger::PlaybackThread::threadLoop_write() mNormalSink->write 而mNormalSink
Android中的多渠道打包之友盟統計篇(二)
上篇簡單瞭解了Android中的多渠道打包,這篇主要說正事了---》 如何多渠道打包: 首先,多渠道打包最重要的是可以統計不同渠道下的應用的情況,比如下載量,日活量等等.. 關於統計的話國內有兩個比較出名的第三方統計工具吧:友盟統計和百度移動統計 這篇說的是用友盟,如果想要
jmeter使用BeanShell Sampler測試自己寫的java介面(二)
上一篇藉助java程式測試SFTP還沒有完成這節繼續 使用BeamShell sampler的步驟和前面一節一樣,java程式碼如下,這裡只測試下載。有些多餘的程式碼沒有清理掉。懶人不想清理先留著了。 package test; import java
Android平臺藍芽程式設計之藍芽聊天分析(二)
接著上一篇沒有完成的任務,我們繼續分析這個藍芽聊天程式的實現,本文主要包括以下兩個部分的內容:其一,分析掃描裝置部分DeviceListActivity,其二,分析具體的聊天過程的完整通訊方案,包括埠監聽、連結配對、訊息傳送和接收等,如果有對上一篇文章不太熟悉的,可以返回
surefire 拉起testng單元測試類的原始碼流程閱讀(二)
這裡是基於surefire 2.19.1版本分析的。 還是根據surefire 拉起單元測試執行報錯的日誌展示的執行過程分析 java.lang.instrument.IllegalClassFormatException: Error while instrumenti
c++效能測試工具:google benchmark入門(二)
上一篇中我們初步體驗了google benchmark的使用,在本文中我們將更進一步深入瞭解google benchmark的常用方法。 本文索引 向測試用例傳遞引數 簡化多個類似測試用例的生成 使用引數生成器 向測試用例傳遞引數 之前我們的測試用例都只接受一個be