kubernetes系列之十八:使用helm安裝istio
一、前言
istio是Kubernetes平臺微服務管理的框架標準,是Service Mesh在Kubernetes平臺的標準實現。相比於其它的微服務框架,istio提供非程式碼介入的框架機制,使用sidecar機制將微服務的服務面和管理面連線起來,而且使用的sidecar envoy是一個高效的proxy。
Istio 輯上分為資料平面和控制平面。
- 資料平面由一組以 sidecar 方式部署的智慧代理(Envoy)組成。這些代理可以調節和控制微服務及 Mixer 之間所有的網路通訊。
- 控制平面負責管理和配置代理來路由流量。此外控制平面配置 Mixer 以實施策略和收集遙測資料
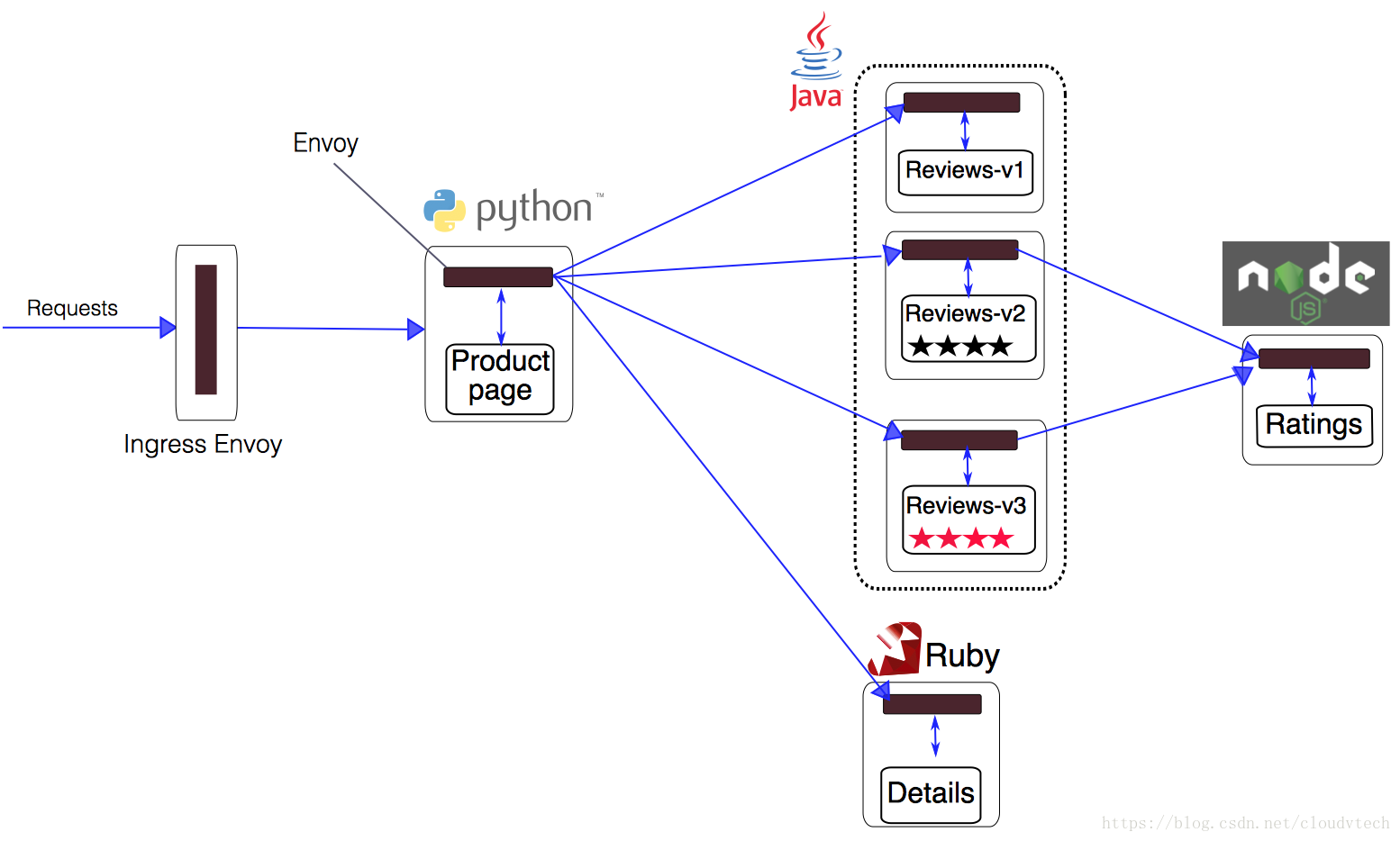
Istio 架構如下圖所示:

- Envoy用於分析和控制進出微服務容器的資料流量
- Mixer進行訪問控制策略的配置和下發
- Pilot將多種服務發現功能抽象化之後為Envoy提供服務發現功能
- Citadel為加密和認證提供支援
轉載自https://blog.csdn.net/cloudvtech
二、通過helm安裝istio
2.1 下載
curl -L https://git.io/getLatestIstio | sh -
export PATH="$PATH:/root/istio/istio-1.0.2/bin”
2.2 修改配置
install/kubernetes/helm/istio/values.yaml
grafana: enabled: true replicaCount: 1 image: grafana persist: false storageClassName: "" security: enabled: false adminUser: admin adminPassword: admin service: annotations: {} externalPort: 32088 internalPort: 3000 nodePort: enabled: true port: 32088
2.3 安裝部署
helm install install/kubernetes/helm/istio \
--name istio \
--namespace istio-system \
--set tracing.enabled=true \
--set servicegraph.enabled=true \
--set prometheus.enabled=true \
--set tracing.jaeger.enabled=true \
--set grafana.enabled=true \
--set global.configValidation=false \
--set global.nodePort=true
安裝之後可以編輯各個service來暴露nodePort進行外部訪問,例如:
kubectl edit svc grafana -n istio-system
apiVersion: v1
kind: Service
metadata:
creationTimestamp: 2018-09-21T17:24:45Z
labels:
app: grafana
chart: grafana-1.0.1
heritage: Tiller
release: istio
name: grafana
namespace: istio-system
resourceVersion: "494980"
selfLink: /api/v1/namespaces/istio-system/services/grafana
uid: 3ba200b6-bdc3-11e8-99a0-08002763f94a
spec:
clusterIP: 10.108.169.84
externalTrafficPolicy: Cluster
ports:
- nodePort: 32088
port: 3000
protocol: TCP
targetPort: 3000
selector:
app: grafana
sessionAffinity: None
type: NodePort
status:
loadBalancer: {}
檢視POD和服務狀態
kubectl get pods -n istio-system
NAME READY STATUS RESTARTS AGE
grafana-6cd5644cb-wclpw 1/1 Running 0 10m
istio-citadel-746c765786-krbs6 1/1 Running 0 20m
istio-egressgateway-7b46794587-jz695 1/1 Running 0 20m
istio-galley-75c6976d79-9x72h 1/1 Running 0 20m
istio-ingressgateway-57f76dc4db-vp245 1/1 Running 0 20m
istio-pilot-7b96cfbf76-m7tnt 2/2 Running 0 20m
istio-policy-6677c87b9f-f55xg 2/2 Running 0 20m
istio-sidecar-injector-879fd9dfc-4tjhx 1/1 Running 0 20m
istio-statsd-prom-bridge-549d687fd9-tsbss 1/1 Running 0 20m
istio-telemetry-7d46d668db-c4w47 2/2 Running 0 20m
istio-tracing-7596597bd7-thqg5 1/1 Running 0 20m
prometheus-6ffc56584f-nb88n 1/1 Running 0 20m
servicegraph-676b468cbb-qqr72 1/1 Running 0 20m
kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana NodePort 10.108.169.84 <none> 3000:32088/TCP 20m
istio-citadel ClusterIP 10.103.37.166 <none> 8060/TCP,9093/TCP 20m
istio-egressgateway ClusterIP 10.104.76.248 <none> 80/TCP,443/TCP 20m
istio-galley ClusterIP 10.109.212.39 <none> 443/TCP,9093/TCP 20m
istio-ingressgateway LoadBalancer 10.98.29.30 <pending> 80:31380/TCP,443:31390/TCP,31400:31400/TCP,15011:32385/TCP,8060:32103/TCP,853:31575/TCP,15030:31684/TCP,15031:32170/TCP 20m
istio-pilot ClusterIP 10.103.77.42 <none> 15010/TCP,15011/TCP,8080/TCP,9093/TCP 20m
istio-policy ClusterIP 10.110.236.247 <none> 9091/TCP,15004/TCP,9093/TCP 20m
istio-sidecar-injector ClusterIP 10.96.108.99 <none> 443/TCP 20m
istio-statsd-prom-bridge ClusterIP 10.102.10.120 <none> 9102/TCP,9125/UDP 20m
istio-telemetry ClusterIP 10.109.168.53 <none> 9091/TCP,15004/TCP,9093/TCP,42422/TCP 20m
jaeger-agent ClusterIP None <none> 5775/UDP,6831/UDP,6832/UDP 20m
jaeger-collector ClusterIP 10.98.192.45 <none> 14267/TCP,14268/TCP 20m
jaeger-query ClusterIP 10.101.32.241 <none> 16686/TCP 20m
prometheus ClusterIP 10.100.123.211 <none> 9090/TCP 20m
prometheus-nodeport NodePort 10.102.78.159 <none> 9090:32090/TCP 20m
servicegraph ClusterIP 10.109.32.171 <none> 8088/TCP 20m
tracing ClusterIP 10.109.159.42 <none> 80/TCP 20m
zipkin ClusterIP 10.99.239.123 <none> 9411/TCP 20m
2.4 獲取訪問URL
export INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http")].nodePort}')
export SECURE_INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="https")].nodePort}')
export INGRESS_HOST=$(kubectl get po -l istio=ingressgateway -n istio-system -o 'jsonpath={.items[0].status.hostIP}')
export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT
轉載自https://blog.csdn.net/cloudvtech
三、安裝應用
3.1 部署bookinfo服務
kubectl apply -f <(istioctl kube-inject -f samples/bookinfo/platform/kube/bookinfo.yaml)
kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
3.2 檢視狀態
kubectl get pods
[root@k8s-install-node istio-1.0.2]# kubectl get pods
NAME READY STATUS RESTARTS AGE
details-v1-7db64f6477-vkj54 2/2 Running 0 20m
productpage-v1-8998997b9-p759l 2/2 Running 0 20m
ratings-v1-754ffd9d5c-c7gc9 2/2 Running 0 20m
reviews-v1-5fb89c7d9-ch279 2/2 Running 0 20m
reviews-v2-5748d654d9-l689q 2/2 Running 0 20m
reviews-v3-5dd59fc497-mwg9p 2/2 Running 0 20m
[root@k8s-install-node istio-1.0.2]# kubectl describe pods productpage-v1-8998997b9-p759l | grep Image:
Image: docker.io/istio/proxy_init:1.0.2
Image: istio/examples-bookinfo-productpage-v1:1.8.0
Image: docker.io/istio/proxyv2:1.0.2
kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
details ClusterIP 10.109.1.224 <none> 9080/TCP 21m
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 15d
productpage ClusterIP 10.100.156.148 <none> 9080/TCP 21m
ratings ClusterIP 10.104.230.106 <none> 9080/TCP 21m
reviews ClusterIP 10.110.149.101 <none> 9080/TCP 21m
3.3 測試通過istio API閘道器測試bookinfo服務
curl -o /dev/null -s -w "%{http_code}\n" http://${GATEWAY_URL}/productpage
200
轉載自https://blog.csdn.net/cloudvtech
四、通過瀏覽器訪問Bookinfo服務和istio的服務
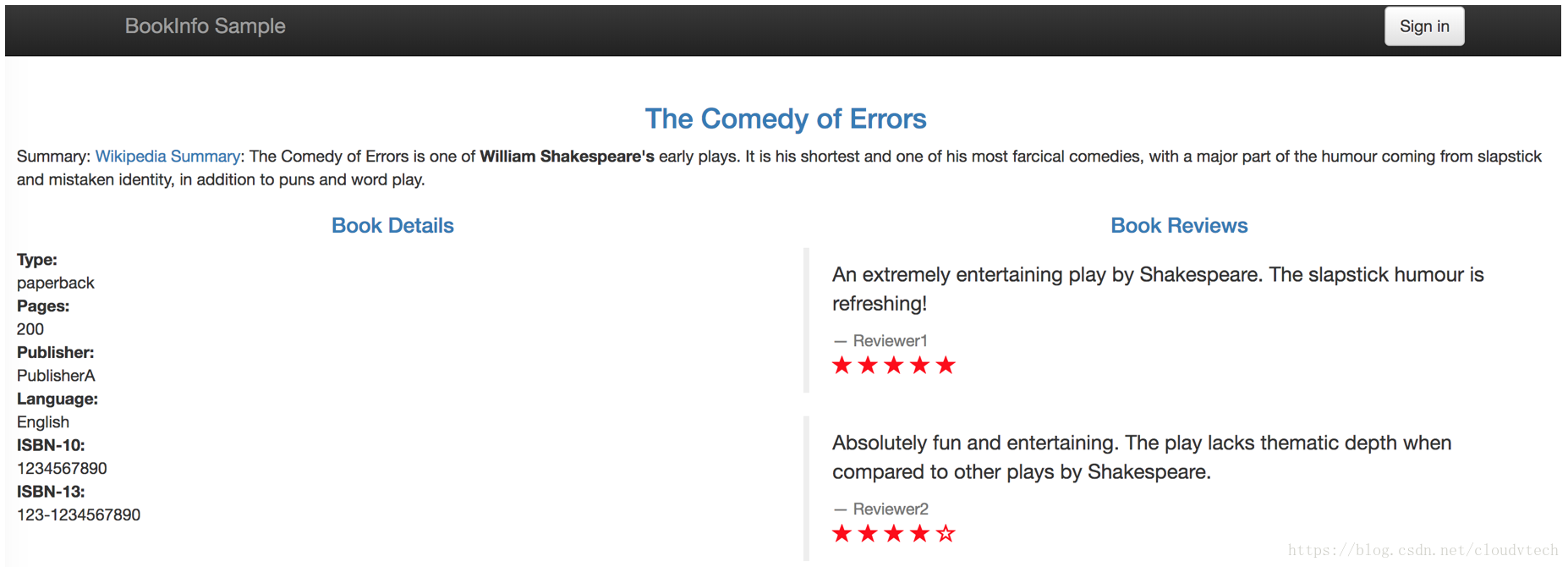
4.1 訪問bookinfo服務
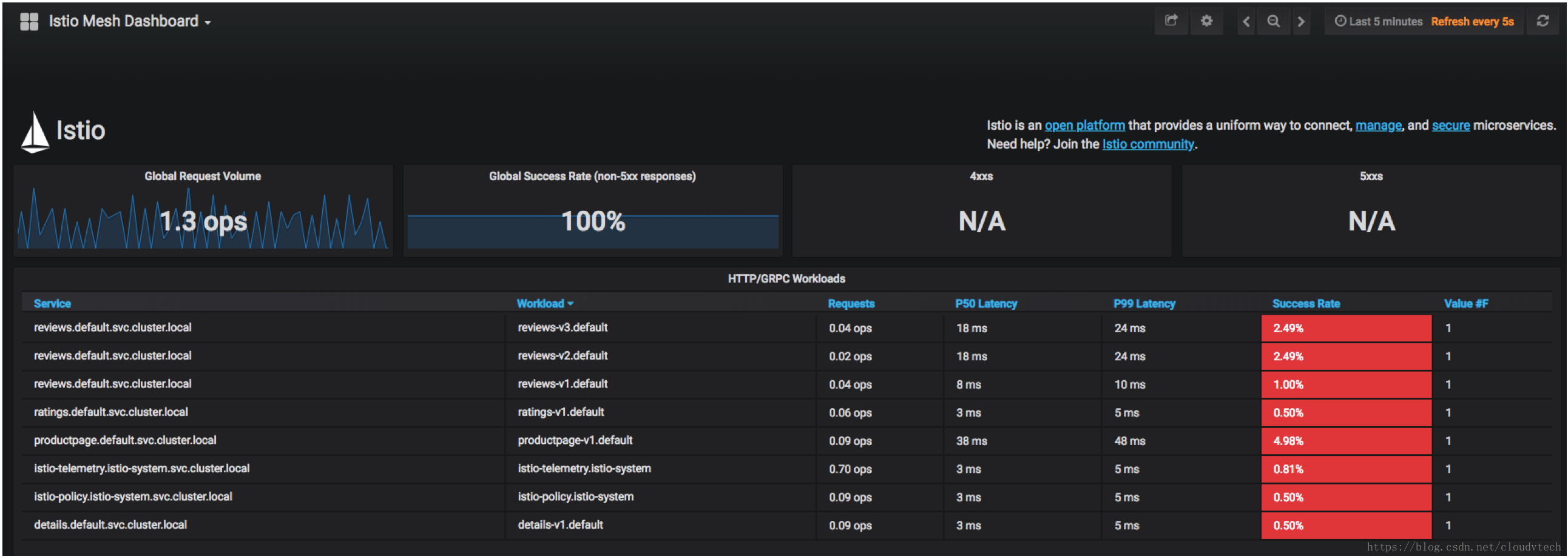
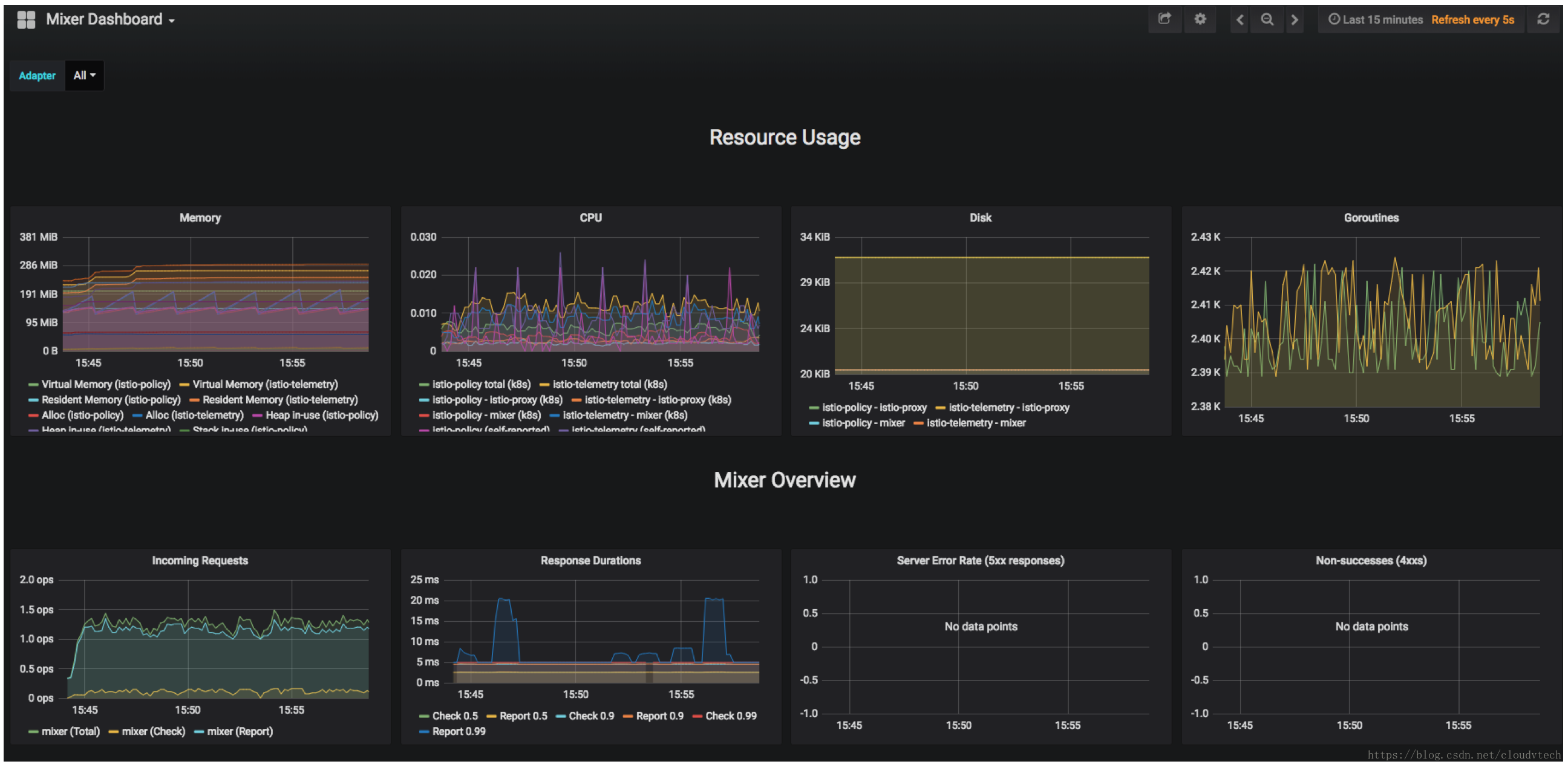
4.2 檢視Grafana
kubectl edit svc grafana -n istio-system
Istio Mesh Dashboard
Mixer Dashboard
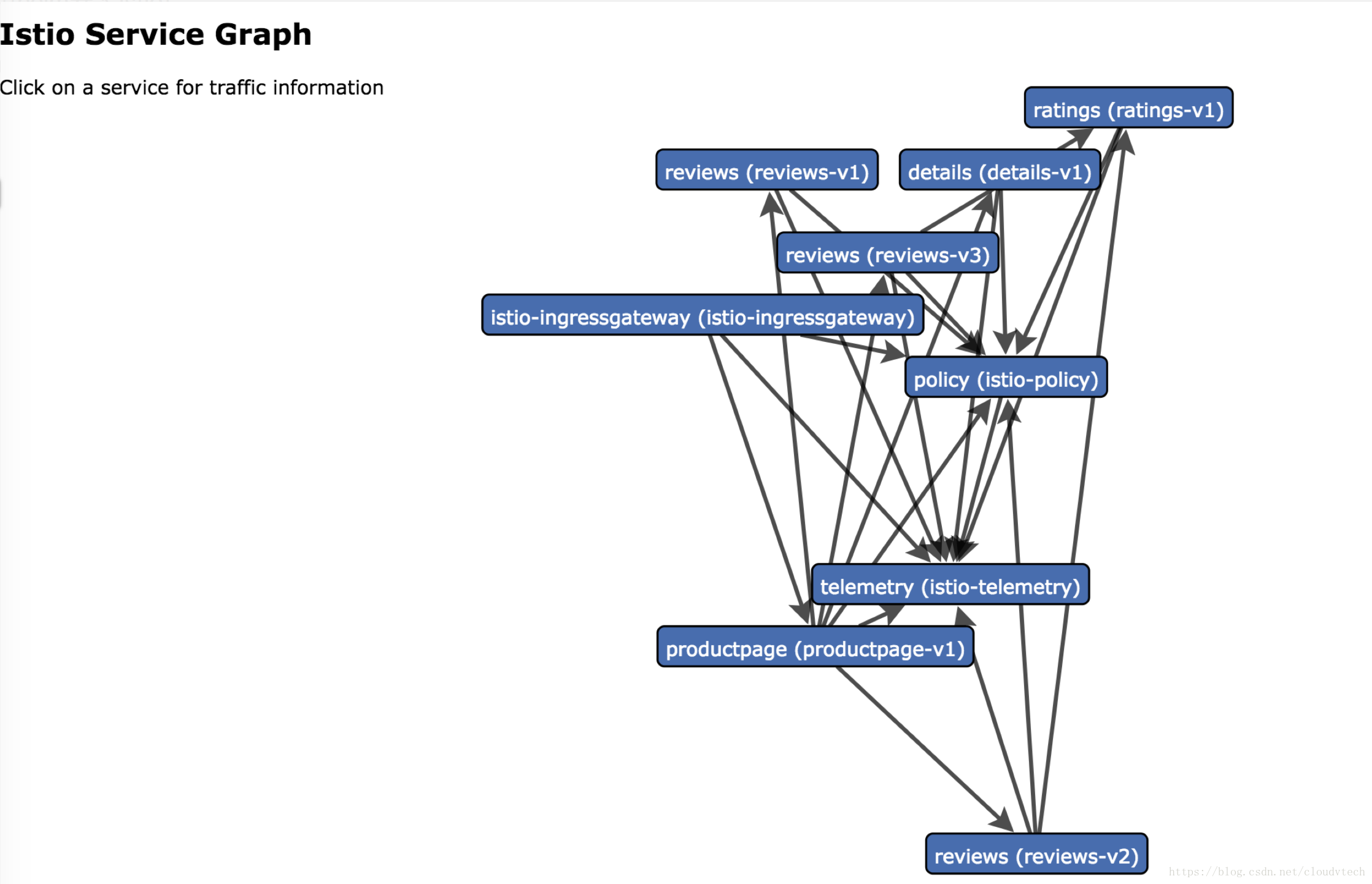
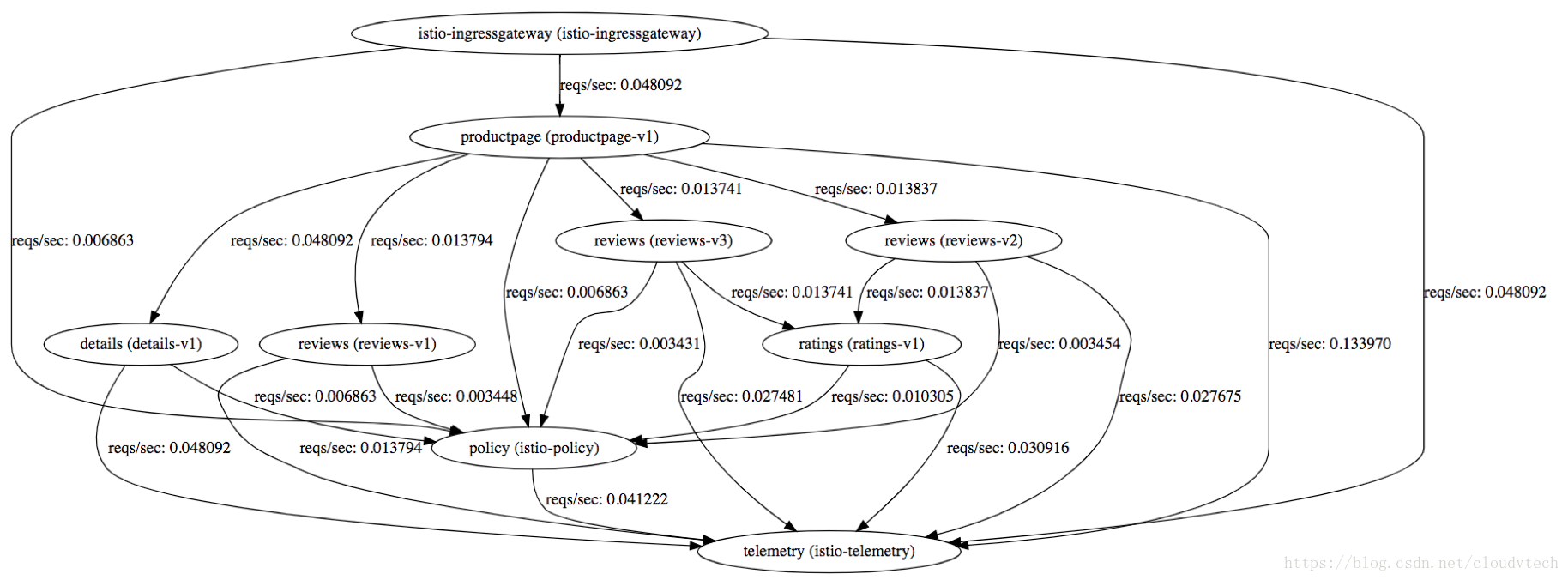
4.3 檢視servicegraph
kubectl edit svc servicegraph -n istio-system
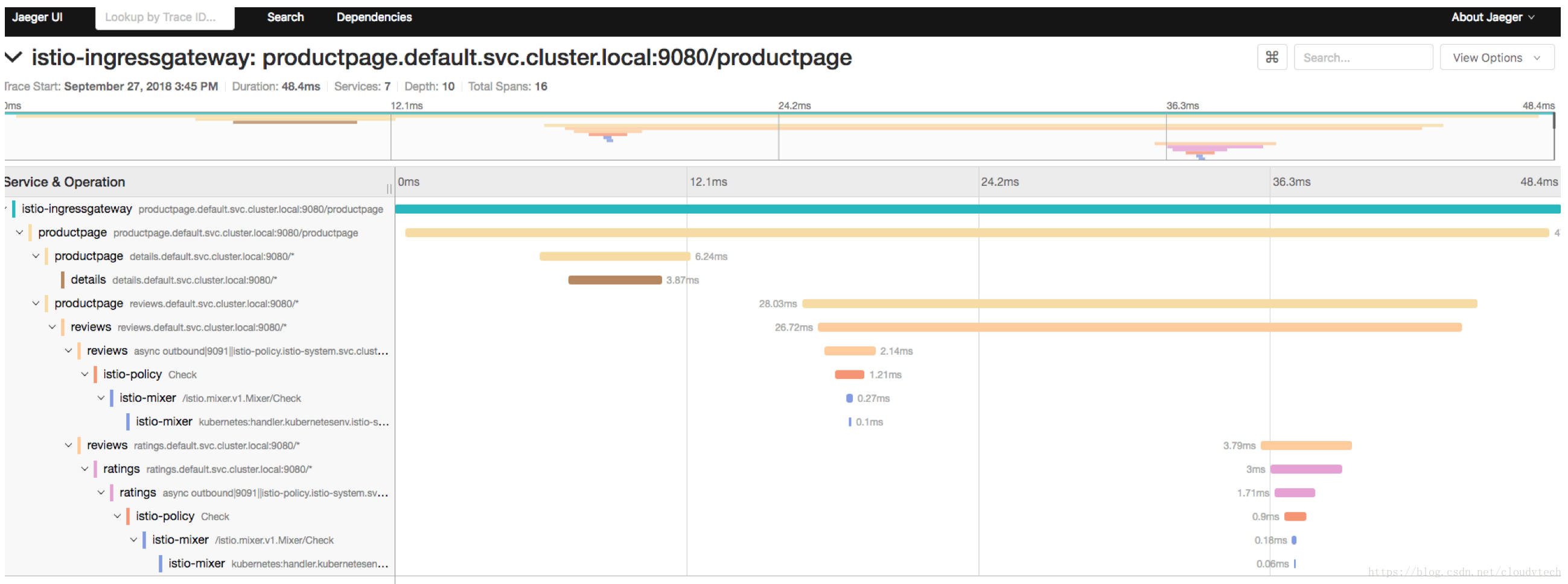
4.4 檢視trace
kubectl edit svc tracing -n istio-system
轉載自https://blog.csdn.net/cloudvtech
五、刪除服務和istio
samples/bookinfo/platform/kube/cleanup.sh
helm del --purge istio
轉載自https://blog.csdn.net/cloudvtech