基於External-DNS的多叢集Ingress DNS實踐
阿新 • • 發佈:2019-06-06
概要
External-DNS提供了程式設計方式管理Kubernetes Ingress資源的DNS的功能,方便使用者從Ingress管理DNS解析記錄。而在kubernetes federation v2環境中,使用External-DNS可以快速的管理多個聯邦叢集的Ingress DNS解析,降低使用者的操作成本。下面將簡單介紹在阿里雲容器服務環境中,如何使用External-DNS管理聯邦叢集的Ingress DNS解析。
聯邦叢集準備
參考阿里雲Kubernetes容器服務上體驗Federation v2 搭建兩個叢集組成的聯邦叢集(配置好kubeconfig,並完成兩個叢集的join)。
配置RAM資訊
選擇Kubernetes叢集節點列表內任意一個Worker節點,開啟對應的節點列表資訊頁面。
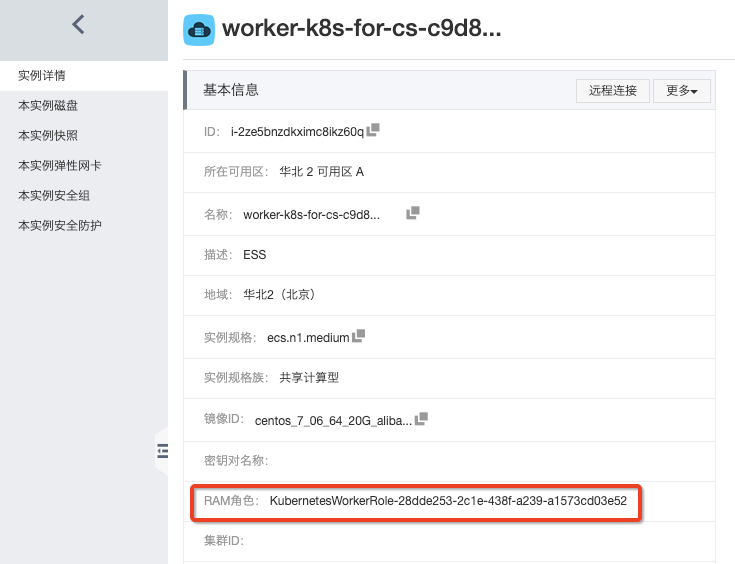
找到對應的 RAM 角色,開啟RAM控制檯,找到對應的角色名稱,新增【AliyunDNSFullAccess】許可權。
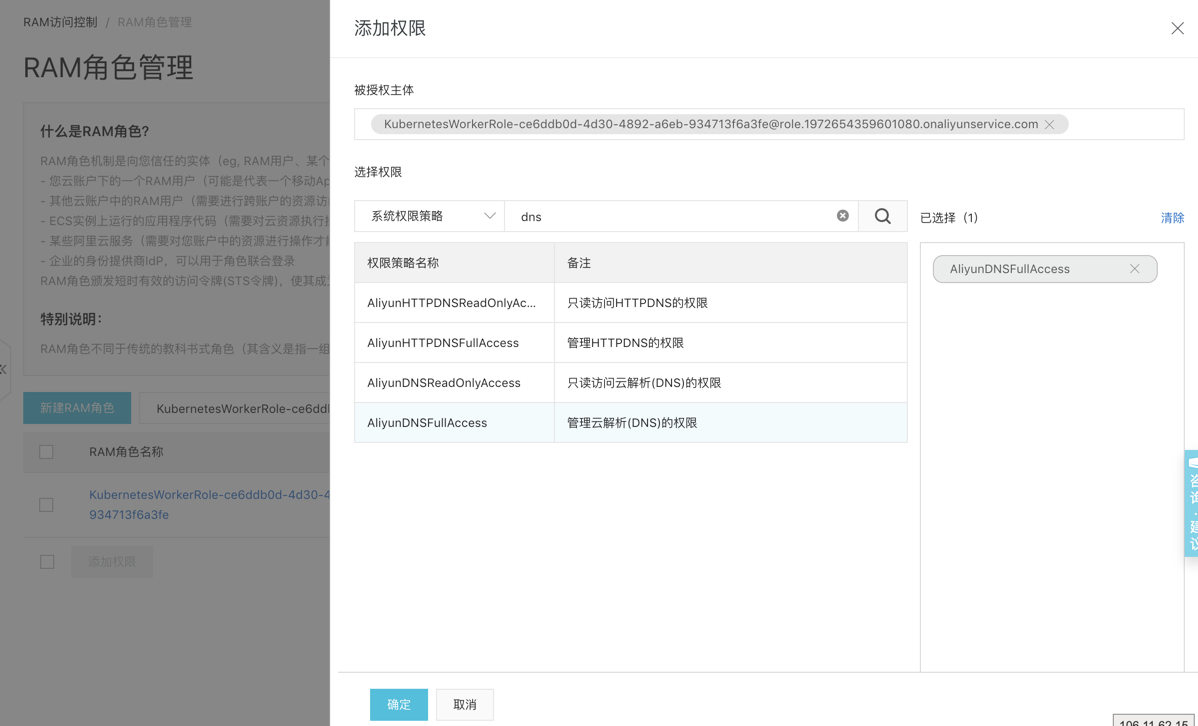
注意:每個叢集都需要配置RAM資訊。
部署External-DNS
配置RBAC
執行下面yaml:
apiVersion: v1 kind: ServiceAccount metadata: name: external-dns --- apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRole metadata: name: external-dns rules: - apiGroups: [""] resources: ["services"] verbs: ["get","watch","list"] - apiGroups: [""] resources: ["pods"] verbs: ["get","watch","list"] - apiGroups: ["extensions"] resources: ["ingresses"] verbs: ["get","watch","list"] - apiGroups: [""] resources: ["nodes"] verbs: ["list"] - apiGroups: ["multiclusterdns.federation.k8s.io"] resources: ["dnsendpoints"] verbs: ["get", "watch", "list"] --- apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: external-dns-viewer roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: external-dns subjects: - kind: ServiceAccount name: external-dns namespace: default
部署External-DNS服務
執行下面yaml:
apiVersion: extensions/v1beta1 kind: Deployment metadata: name: external-dns spec: strategy: type: Recreate template: metadata: labels: app: external-dns spec: serviceAccountName: external-dns containers: - name: external-dns image: registry.cn-beijing.aliyuncs.com/acs/external-dns:v0.5.8-27 args: - --source=crd - --crd-source-apiversion=multiclusterdns.federation.k8s.io/v1alpha1 - --crd-source-kind=DNSEndpoint - --provider=alibabacloud - --policy=sync # enable full synchronization - --registry=txt - --txt-prefix=cname - --txt-owner-id=my-identifier - --alibaba-cloud-config-file= # enable sts token volumeMounts: - mountPath: /usr/share/zoneinfo name: hostpath volumes: - name: hostpath hostPath: path: /usr/share/zoneinfo type: Directory
部署驗證資源
建立FederatedDeployment和FederatedService:
apiVersion: v1
kind: Namespace
metadata:
name: test-namespace
---
apiVersion: types.federation.k8s.io/v1alpha1
kind: FederatedNamespace
metadata:
name: test-namespace
namespace: test-namespace
spec:
placement:
clusterNames:
- cluster1
- cluster2
---
apiVersion: types.federation.k8s.io/v1alpha1
kind: FederatedDeployment
metadata:
name: test-deployment
namespace: test-namespace
spec:
template:
metadata:
labels:
app: nginx
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- image: nginx
name: nginx
resources:
limits:
cpu: 500m
requests:
cpu: 200m
placement:
clusterNames:
- cluster1
- cluster2
---
apiVersion: types.federation.k8s.io/v1alpha1
kind: FederatedService
metadata:
name: test-service
namespace: test-namespace
spec:
template:
spec:
selector:
app: nginx
type: ClusterIP
ports:
- name: http
port: 80
placement:
clusterNames:
- cluster2
- cluster1各個叢集ingress建立資訊如下:
kubectl get ingress -n test-namespace --context cluster1
NAME HOSTS ADDRESS PORTS AGE
test-ingress * 47.93.69.121 80 54m
kubectl get ingress -n test-namespace --context cluster2
NAME HOSTS ADDRESS PORTS AGE
test-ingress * 39.106.232.23 80 54m建立FederatedIngress和IngressDNSRecord
apiVersion: types.federation.k8s.io/v1alpha1
kind: FederatedIngress
metadata:
name: test-ingress
namespace: test-namespace
spec:
template:
spec:
backend:
serviceName: test-service
servicePort: 80
placement:
clusterNames:
- cluster2
- cluster1
---
apiVersion: multiclusterdns.federation.k8s.io/v1alpha1
kind: IngressDNSRecord
metadata:
name: test-ingress
namespace: test-namespace
spec:
hosts:
- ingress-example.example-domain.club
recordTTL: 600
其中【ingress-example.example-domain.club】為測試阿里雲託管的域名,請提前在阿里雲上購買域名,並注意替換。
DNS解析驗證
dig +short @dns7.hichina.com ingress-example.example-domain.club
47.93.69.121
39.106.232.23可以看到我們繫結的域名已經解析到了cluster1和cluster2的ingress IP上了。
訪問域名相應的服務:
curl ingress-example.sigma-host.club
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>總結
通過上面介紹,可以看到使用External-DNS可以非常方便的管理federation-v2環境下的Ingress DNS解析。
作者:鈞博
原文連結
本文為雲棲社群原創內容,未經
