5.深入Istio原始碼:Pilot-agent作用及其原始碼分析
阿新 • • 發佈:2020-12-12
> 轉載請宣告出處哦~,本篇文章釋出於luozhiyun的部落格:https://www.luozhiyun.com
>
> 本文使用的Istio原始碼是 release 1.5。
## 介紹
Sidecar在注入的時候會注入istio-init和istio-proxy兩個容器。Pilot-agent就是啟動istio-proxy的入口。通過kubectl命令我們可以看到啟動命令:
```sh
[root@localhost ~]# kubectl exec -it details-v1-6c9f8bcbcb-shltm -c istio-proxy -- ps -efww
UID PID PPID C STIME TTY TIME CMD
istio-p+ 1 0 0 08:52 ? 00:00:13 /usr/local/bin/pilot-agent proxy sidecar --domain default.svc.cluster.local --configPath /etc/istio/proxy --binaryPath /usr/local/bin/envoy --serviceCluster details.default --drainDuration 45s --parentShutdownDuration 1m0s --discoveryAddress istiod.istio-system.svc:15012 --zipkinAddress zipkin.istio-system:9411 --proxyLogLevel=warning --proxyComponentLogLevel=misc:error --connectTimeout 10s --proxyAdminPort 15000 --concurrency 2 --controlPlaneAuthPolicy NONE --dnsRefreshRate 300s --statusPort 15020 --trust-domain=cluster.local --controlPlaneBootstrap=false
istio-p+ 18 1 0 08:52 ? 00:01:11 /usr/local/bin/envoy -c /etc/istio/proxy/envoy-rev0.json --restart-epoch 0 --drain-time-s 45 --parent-shutdown-time-s 60 --service-cluster details.default --service-node sidecar~172.20.0.14~details-v1-6c9f8bcbcb-shltm.default~default.svc.cluster.local --max-obj-name-len 189 --local-address-ip-version v4 --log-format [Envoy (Epoch 0)] [%Y-%m-%d %T.%e][%t][%l][%n] %v -l warning --component-log-level misc:error --concurrency 2
```
Pilot-agent除了啟動istio-proxy以外還有以下能力:
* 生成Envoy的Bootstrap配置檔案;
* 健康檢查;
* 監視證書的變化,通知Envoy程序熱重啟,實現證書的熱載入;
* 提供Envoy守護功能,當Envoy異常退出的時候重啟Envoy;
* 通知Envoy優雅退出;
## 程式碼執行流程分析
```go
proxyCmd = &cobra.Command{
Use: "proxy",
Short: "Envoy proxy agent",
FParseErrWhitelist: cobra.FParseErrWhitelist{
UnknownFlags: true,
},
RunE: func(c *cobra.Command, args []string) error {
...
// 用於設定預設配置檔案的預設配置相關引數
proxyConfig := mesh.DefaultProxyConfig()
// set all flags
proxyConfig.CustomConfigFile = customConfigFile
proxyConfig.ProxyBootstrapTemplatePath = templateFile
proxyConfig.ConfigPath = configPath
proxyConfig.BinaryPath = binaryPath
proxyConfig.ServiceCluster = serviceCluster
proxyConfig.DrainDuration = types.DurationProto(drainDuration)
proxyConfig.ParentShutdownDuration = types.DurationProto(parentShutdownDuration)
proxyConfig.DiscoveryAddress = discoveryAddress
proxyConfig.ConnectTimeout = types.DurationProto(connectTimeout)
proxyConfig.StatsdUdpAddress = statsdUDPAddress
...
ctx, cancel := context.WithCancel(context.Background())
// 啟動 status server
if statusPort > 0 {
localHostAddr := localHostIPv4
if proxyIPv6 {
localHostAddr = localHostIPv6
}
prober := kubeAppProberNameVar.Get()
//健康探測
statusServer, err := status.NewServer(status.Config{
LocalHostAddr: localHostAddr,
AdminPort: proxyAdminPort,
//通過引數--statusPort 15020設定
StatusPort: statusPort,
KubeAppProbers: prober,
NodeType: role.Type,
})
if err != nil {
cancel()
return err
}
go waitForCompletion(ctx, statusServer.Run)
}
...
//構造Proxy例項,包括配置,啟動引數等
envoyProxy := envoy.NewProxy(envoy.ProxyConfig{
Config: proxyConfig,
Node: role.ServiceNode(),
LogLevel: proxyLogLevel,
ComponentLogLevel: proxyComponentLogLevel,
PilotSubjectAltName: pilotSAN,
MixerSubjectAltName: mixerSAN,
NodeIPs: role.IPAddresses,
DNSRefreshRate: dnsRefreshRate,
PodName: podName,
PodNamespace: podNamespace,
PodIP: podIP,
SDSUDSPath: sdsUDSPath,
SDSTokenPath: sdsTokenPath,
STSPort: stsPort,
ControlPlaneAuth: controlPlaneAuthEnabled,
DisableReportCalls: disableInternalTelemetry,
OutlierLogPath: outlierLogPath,
PilotCertProvider: pilotCertProvider,
})
//構造agent例項,實現了Agent介面
agent := envoy.NewAgent(envoyProxy, features.TerminationDrainDuration())
if nodeAgentSDSEnabled {
tlsCertsToWatch = []string{}
}
//構造watcher例項
watcher := envoy.NewWatcher(tlsCertsToWatch, agent.Restart)
//啟動 watcher
go watcher.Run(ctx)
// 優雅退出
go cmd.WaitSignalFunc(cancel)
//啟動 agent
return agent.Run(ctx)
},
}
```
執行流程大概分成這麼幾步:
1. 用於設定預設配置檔案的預設配置相關引數;
2. 啟動 status server進行健康檢測;
3. 構造Proxy例項,包括配置,啟動引數,並構造構造agent例項;
4. 構造watcher例項,並啟動;
5. 開啟執行緒監聽訊號,進行優雅退出;
6. 啟動 agent;
### 預設配置相關引數
```go
kubectl exec -it details-v1-6c9f8bcbcb-shltm -c istio-proxy -- /usr/local/bin/pilot-agent proxy --help
Envoy proxy agent
Usage:
pilot-agent proxy [flags]
Flags:
--binaryPath string Path to the proxy binary (default "/usr/local/bin/envoy")
--concurrency int number of worker threads to run
--configPath string Path to the generated configuration file directory (default "/etc/istio/proxy")
--connectTimeout duration Connection timeout used by Envoy for supporting services (default 1s)
--controlPlaneAuthPolicy string Control Plane Authentication Policy (default "NONE")
--controlPlaneBootstrap Process bootstrap provided via templateFile to be used by control plane components. (default true)
--customConfigFile string Path to the custom configuration file
--datadogAgentAddress string Address of the Datadog Agent
--disableInternalTelemetry Disable internal telemetry
--discoveryAddress string Address of the discovery service exposing xDS (e.g. istio-pilot:8080) (default "istio-pilot:15010")
--dnsRefreshRate string The dns_refresh_rate for bootstrap STRICT_DNS clusters (default "300s")
--domain string DNS domain suffix. If not provided uses ${POD_NAMESPACE}.svc.cluster.local
--drainDuration duration The time in seconds that Envoy will drain connections during a hot restart (default 45s)
--envoyAccessLogService string Settings of an Envoy gRPC Access Log Service API implementation
--envoyMetricsService string Settings of an Envoy gRPC Metrics Service API implementation
-h, --help help for proxy
--id string Proxy unique ID. If not provided uses ${POD_NAME}.${POD_NAMESPACE} from environment variables
--ip string Proxy IP address. If not provided uses ${INSTANCE_IP} environment variable.
--lightstepAccessToken string Access Token for LightStep Satellite pool
--lightstepAddress string Address of the LightStep Satellite pool
--lightstepCacertPath string Path to the trusted cacert used to authenticate the pool
--lightstepSecure Should connection to the LightStep Satellite pool be secure
--mixerIdentity string The identity used as the suffix for mixer's spiffe SAN. This would only be used by pilot all other proxy would get this value from pilot
--outlierLogPath string The log path for outlier detection
--parentShutdownDuration duration The time in seconds that Envoy will wait before shutting down the parent process during a hot restart (default 1m0s)
--pilotIdentity string The identity used as the suffix for pilot's spiffe SAN
--proxyAdminPort uint16 Port on which Envoy should listen for administrative commands (default 15000)
--proxyComponentLogLevel string The component log level used to start the Envoy proxy (default "misc:error")
--proxyLogLevel string The log level used to start the Envoy proxy (choose from {trace, debug, info, warning, error, critical, off}) (default "warning")
--serviceCluster string Service cluster (default "istio-proxy")
--serviceregistry string Select the platform for service registry, options are {Kubernetes, Consul, Mock} (default "Kubernetes")
--statsdUdpAddress string IP Address and Port of a statsd UDP listener (e.g. 10.75.241.127:9125)
--statusPort uint16 HTTP Port on which to serve pilot agent status. If zero, agent status will not be provided.
--stsPort int HTTP Port on which to serve Security Token Service (STS). If zero, STS service will not be provided.
--templateFile string Go template bootstrap config
--tokenManagerPlugin string Token provider specific plugin name. (default "GoogleTokenExchange")
--trust-domain string The domain to use for identities
--zipkinAddress string Address of the Zipkin service (e.g. zipkin:9411)
```
從上面輸出我們也可以看到proxy引數的含義以及對應的預設值。
```go
func DefaultProxyConfig() meshconfig.ProxyConfig {
return meshconfig.ProxyConfig{
ConfigPath: constants.ConfigPathDir,
BinaryPath: constants.BinaryPathFilename,
ServiceCluster: constants.ServiceClusterName,
DrainDuration: types.DurationProto(45 * time.Second),
ParentShutdownDuration: types.DurationProto(60 * time.Second),
DiscoveryAddress: constants.DiscoveryPlainAddress,
ConnectTimeout: types.DurationProto(1 * time.Second),
StatsdUdpAddress: "",
EnvoyMetricsService: &meshconfig.RemoteService{Address: ""},
EnvoyAccessLogService: &meshconfig.RemoteService{Address: ""},
ProxyAdminPort: 15000,
ControlPlaneAuthPolicy: meshconfig.AuthenticationPolicy_NONE,
CustomConfigFile: "",
Concurrency: 0,
StatNameLength: 189,
Tracing: nil,
}
}
```
預設的啟動引數都在DefaultProxyConfig方法中設定,預設的啟動配置如下所示:
- ConfigPath:/etc/istio/proxy
- BinaryPath:/usr/local/bin/envoy
- ServiceCluster:istio-proxy
- DrainDuration:45s
- ParentShutdownDuration:60s
- DiscoveryAddress:istio-pilot:15010
- ConnectTimeout:1s
- StatsdUdpAddress:""
- EnvoyMetricsService:meshconfig.RemoteService
- EnvoyAccessLogService:meshconfig.RemoteService
- ProxyAdminPort:15000
- ControlPlaneAuthPolicy:0
- CustomConfigFile:""
- Concurrency:0
- StatNameLength:189
- Tracing:nil
### status server健康檢查
初始化status server:
```go
func NewServer(config Config) (*Server, error) {
s := &Server{
statusPort: config.StatusPort,
ready: &ready.Probe{
LocalHostAddr: config.LocalHostAddr,
AdminPort: config.AdminPort,
NodeType: config.NodeType,
},
}
...
return s, nil
}
```
初始化完成之後會開啟一個執行緒呼叫statusServer的 Run方法:
```go
go waitForCompletion(ctx, statusServer.Run)
func (s *Server) Run(ctx context.Context) {
log.Infof("Opening status port %d\n", s.statusPort)
mux := http.NewServeMux()
// Add the handler for ready probes.
// 初始化探針的回撥處理器
// /healthz/ready
mux.HandleFunc(readyPath, s.handleReadyProbe)
mux.HandleFunc(quitPath, s.handleQuit)
//應用埠檢查
mux.HandleFunc("/app-health/", s.handleAppProbe)
//埠通過引數--statusPort 15020設定
l, err := net.Listen("tcp", fmt.Sprintf(":%d", s.statusPort))
if err != nil {
log.Errorf("Error listening on status port: %v", err.Error())
return
}
...
defer l.Close()
//開啟監聽
go func() {
if err := http.Serve(l, mux); err != nil {
log.Errora(err)
notifyExit()
}
}()
<-ctx.Done()
log.Info("Status server has successfully terminated")
}
```
Run方法會開啟一個執行緒並監聽15020埠,呼叫路徑為 /healthz/ready,並通過呼叫handleReadyProbe處理器來呼叫Envoy的15000埠判斷Envoy是否已經 ready 接受相對應的流量。呼叫過程如下:
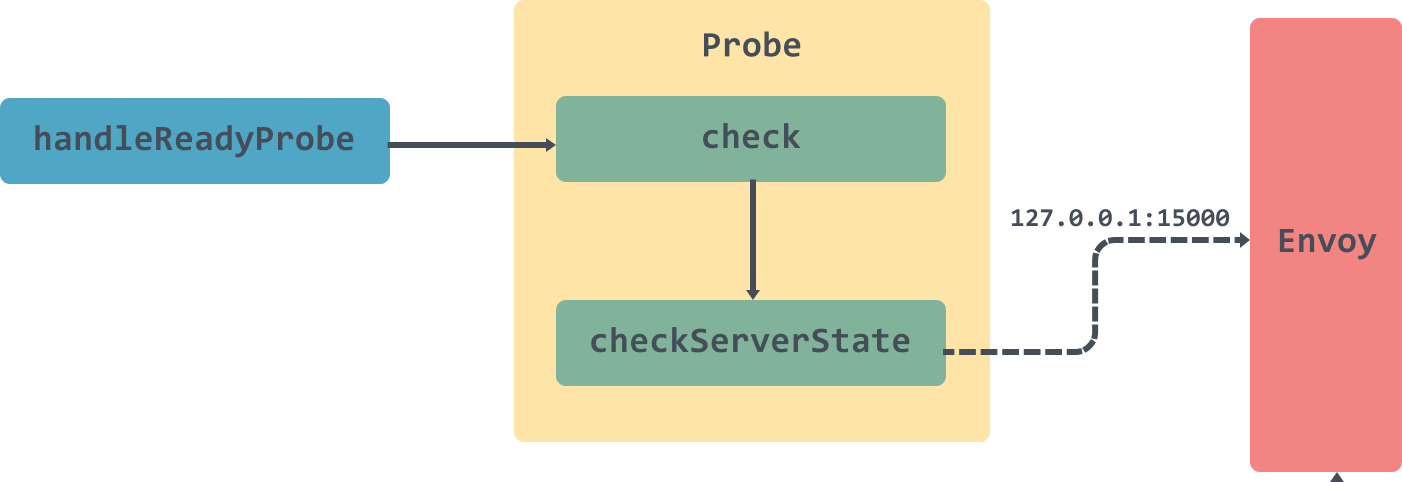
### watcher監控管理
在進行watcher監控之前會通過NewAgent生成agent例項:
```go
func NewAgent(proxy Proxy, terminationDrainDuration time.Duration) Agent {
return &agent{
proxy: proxy,
//用於管理啟動 Envoy 後的狀態通道,用於監視 Envoy 程序的狀態
statusCh: make(chan exitStatus),
//活躍的Epoch 集合
activeEpochs: map[int]chan error{},
//預設5s
terminationDrainDuration: terminationDrainDuration,
//當前的Epoch
currentEpoch: -1,
}
}
```
然後構建watcher例項:
```go
//構造watcher例項
watcher := envoy.NewWatcher(tlsCertsToWatch, agent.Restart)
type watcher struct {
//證書列表
certs []string
//envoy 重啟函式
updates func(interface{})
}
func NewWatcher(certs []string, updates func(interface{})) Watcher {
return &watcher{
certs: certs,
updates: updates,
}
}
```
watcher裡面總共就兩個引數certs是監聽的證書列表,updates是envoy 重啟函式,如果證書檔案發生變化則呼叫updates來reload envoy。
啟動watcher:
```go
go watcher.Run(ctx)
func (w *watcher) Run(ctx context.Context) {
//啟動envoy
w.SendConfig()
//監聽證書變化
go watchCerts(ctx, w.certs, watchFileEvents, defaultMinDelay, w.SendConfig)
<-ctx.Done()
log.Info("Watcher has successfully terminated")
}
```
watcher的Run方法首先會呼叫SendConfig啟動Envoy,然後啟動一個執行緒監聽證書的變化。
```go
func (w *watcher) SendConfig() {
h := sha256.New()
generateCertHash(h, w.certs)
w.updates(h.Sum(nil))
}
```
SendConfig方法會獲取當前的證書集合hash之後傳入到updates方法中,updates方法就是在初始化NewWatcher的時候傳入的,這裡是會呼叫到agent的Restart方法的:
```go
func (a *agent) Restart(config interface{}) {
a.restartMutex.Lock()
defer a.restartMutex.Unlock()
a.mutex.Lock()
//校驗傳入的引數是否產生了變化
if reflect.DeepEqual(a.currentConfig, config) {
// Same configuration - nothing to do.
a.mutex.Unlock()
return
}
//活躍的Epoch
hasActiveEpoch := len(a.activeEpochs) >
