Cisco Packet Tracer NAT模擬實驗
阿新 • • 發佈:2020-12-17
# Cisco Packet Tracer NAT模擬實驗
by: 鐵樂貓
date: 2020-09-22
cisco packet tracer : 7.2.2
## NAT簡介
NAT允許將私有IP地址對映到公網(合法的Internet IP) 地址,以此來做到多個內網ip共用一個公網ip之類。
### NAT使用場景:
* 需要連線Internet,但是你的主機沒有公網IP地址
* 更換了一個新的ISP, 需要重新組織網路
* 需要合併兩個具有相同網路地址的內網
NAT一般應用在邊界路由器中,比如公司連線Internet的路由器上,其最顯著的優點是節約合法公網IP地址。
### NAT型別:
* 靜態NAT: 一對一對映,每臺主機對應一個真實的IP地址。或一個內網網段共同使用一個真實的外網ip。
* 動態NAT: 從設定好的公有ip的地址池中提供一個公網iP地址給來申請對映的私有IP地址使用。
* PAT: 通過埠區分內網主機,將多個私網IP地址對映到一個公網IP。
## 基礎拓撲
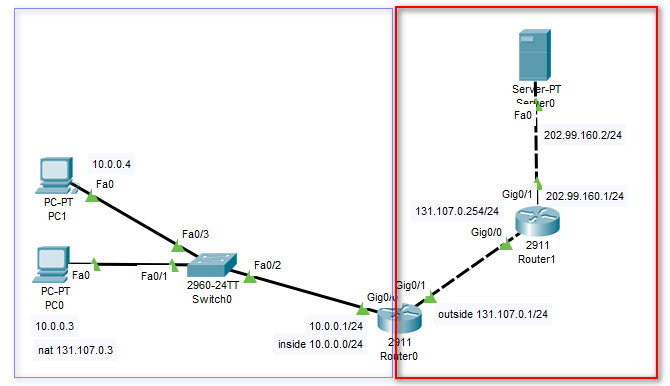
如圖,左半部分藍色框內的模擬內網環境,右半部分紅色框住的模擬為外網環境。
連好線後,開始配置,中間的route0配置如下:
### Route0
* 埠配置
```properties
interface GigabitEthernet0/0
ip address 10.0.0.1 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
ip address 131.107.0.1 255.255.255.0
duplex auto
speed auto
!
```
其中,ip address 配置ip地址例:
```bash
Router0(config)# int gig0/0
Router0(config-if)# ip add 10.0.0.1 255.255.255.0
Router0(config-if)# no shutdown
```
* 靜態路由配置
```properties
ip route 0.0.0.0 0.0.0.0 131.107.0.254
```
### Route1
* 埠配置
```properties
interface GigabitEthernet0/0
ip address 131.107.0.254 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
ip address 202.99.160.1 255.255.255.0
duplex auto
speed auto
!
```
* 靜態路由配置
```properties
ip route 131.107.0.0 255.255.255.0 131.107.0.1
ip route 0.0.0.0 0.0.0.0 202.99.160.2
```
### 模擬的客戶端pc0/pc1/Server0
直接點選開啟使用圖形介面配置上各自的ip和閘道器即可。不再詳說。
## 配置靜態NAT
### 模擬靜態地址規劃一
機器名稱 :pc0
私網ip地址: 10.0.0.3
對映公網地址: 131.107.0.3
第一個實驗我們先做一對一對映的模擬,簡單的就是將pc0訪問外網的時候映射出去變為131.107.0.3這個地址。
### Router0 配置nat inside和outside
```bash
Router0(config)# int gig0/0
Router0(config-if)# ip nat inside
Router0(config)# int gig0/1
Router0(config-if)# ip nat outside
```
主要是看`ip nat inside` 和` ip nat outside`
inside 可以理解為內網進入端(被轉換端),outside理解為公網出口端。
### 配置nat 一對一對映
```bash
Router0(config)# ip nat inside source static 10.0.0.3 131.107.0.3
```
主要看source來源,static的話就是精準的一對一對映。
* 驗證
開啟debug ip nat檢視
```bash
Router0# debug ip nat
```
pc0 ping 外網伺服器(server0)
```bash
C:\>ping 202.99.160.2
Pinging 202.99.160.2 with 32 bytes of data:
Reply from 202.99.160.2: bytes=32 time=1ms TTL=126
Reply from 202.99.160.2: bytes=32 time=7ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Ping statistics for 202.99.160.2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 7ms, Average = 2ms
```
debug中可看到
```bash
Router>
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [47]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [48]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [49]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [50]
NAT*: s=202.99.160.2, d=131.107.0.3->10.0.0.3 [93]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [51]
NAT*: s=202.99.160.2, d=131.107.0.3->10.0.0.3 [94]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [52]
NAT*: s=202.99.160.2, d=131.107.0.3->10.0.0.3 [95]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [53]
NAT*: s=202.99.160.2, d=131.107.0.3->10.0.0.3 [96]
NAT: s=10.0.0.3->131.107.0.3, d=202.99.160.2 [54]
NAT*: s=202.99.160.2, d=131.107.0.3->10.0.0.3 [97]
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 44 (44)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 45 (45)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 46 (46)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 47 (47)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 48 (48)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 49 (49)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 50 (50)
NAT: expiring 131.107.0.3 (10.0.0.3) icmp 51 (51)
```
### 配置範圍對映(PAT)
一組內網對映到一個公網ip(共用)
首先要先建立一個list
* access-list 配置
這裡配置地址表主要是應用於之後的nat轉發中,畢竟很多時候一整個網段對映到同一公網ip才方便。
```bash
access-list 7 permit 10.0.0.0 0.0.0.255
```
* ip nat inside source list 配置
```
ip nat inside source list 7 interface GigabitEthernet0/1 overload
```
list的話就是多個內網ip對映過載,所以後面跟的是介面。最主要的區別是後面跟了個overload。
* 驗證
用pc1 ping server0
```
C:\>ping 202.99.160.2 -n 16
Pinging 202.99.160.2 with 32 bytes of data:
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time=1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time=1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time=1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
Reply from 202.99.160.2: bytes=32 time=1ms TTL=126
Reply from 202.99.160.2: bytes=32 time<1ms TTL=126
```
debug中可以看到由於沒有一對一對映成具體的ip,所以直接使用的是出口的ip地址:131.107.0.1
```bash
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [47]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [98]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [48]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [99]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [49]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [100]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [50]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [101]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [51]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [102]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [52]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [103]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [53]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [104]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [54]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [105]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [55]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [106]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [56]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [107]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [57]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [108]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [58]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [109]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [59]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [110]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [60]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [111]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [61]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [112]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [62]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [113]
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 47 (47)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 48 (48)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 49 (49)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 50 (50)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 51 (51)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 52 (52)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 53 (53)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 54 (54)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 55 (55)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 56 (56)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 57 (57)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 58 (58)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 59 (59)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 60 (60)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 61 (61)
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 62 (62)
```
## 配置動態NAT
這種型別的Nat可以實現對映一個私有IP地址到註冊IP地址池中的一個註冊IP地址.但必須保證擁有足夠的真實IP,保證每個在因特網中收發包的使用者都有真實的IP可用.
比如: 你有3個外網IP,但內網有5臺機器,使用動態NAT,只能同時有3臺計算機訪問Internet.
將上面配置的靜態NAT儲存為static_nat.pkt,再另存一份為dynamic_nat.pkt
以下實驗在dynamicNAT.pkt上修改。
清除之前對route0路由器的靜態配置:
```bash
Router0(config)#no ip nat inside source static 10.0.0.3 131.107.0.3
Router0(config)#no ip nat inside source list 7 interface GigabitEthernet0/1
```
* 動態nat規劃
```bash
//配置動態NAT
//定義訪問控制列表,將網段新增到列表中
access-list 8 permit 10.0.0.0 0.0.0.255
//定義公網地址池,名稱定義為tielemao
ip nat pool tielemao 131.107.0.1 131.107.0.3 netmask 255.255.255.0
//將列表list 8 和 公網地址池tielemao 關聯
ip nat inside source list 8 pool todd
```
如下:
```bash
Router0(config)#access-list 8 permit 10.0.0.0 0.0.0.255
Router0(config)#ip nat pool tielemao 131.107.0.1 131.107.0.3 netmask 255.255.255.0
Router0(config)#ip nat inside source list 8 pool tielemao
ipnat_add_dynamic_cfg: id 2, flag 5, range 0
poolstart 131.107.0.1 poolend 131.107.0.3
id 2, flags 0, domain 0, lookup 0, aclnum 8 ,
aclname 8 , mapname idb 0
```
* 驗證
同時用pc0 和pc1 ping server0, debug資訊中可以看到分別自動從池中拿取了131.107.0.1和131.107.0.2
```bash
NAT: s=10.0.0.3->131.107.0.2, d=202.99.160.2 [57]
NAT*: s=202.99.160.2, d=131.107.0.2->10.0.0.3 [136]
NAT: s=10.0.0.4->131.107.0.1, d=202.99.160.2 [83]
NAT*: s=202.99.160.2, d=131.107.0.1->10.0.0.4 [137]
....
NAT: expiring 131.107.0.1 (10.0.0.4) icmp 90 (90)
NAT: expiring 131.107.0.2 (10.0.0.3) icmp 62 (62)
```
## 配置PAT
簡單來說就是類似將內網的服務通過埠映射出公網給外面的也能訪問。
儲存dynamic_nat.pkt後,另存一份pat_nat.pkt, 在pat_nat.pkt進行修改,
另外增加三臺server機器做為模擬. 拓撲如下:
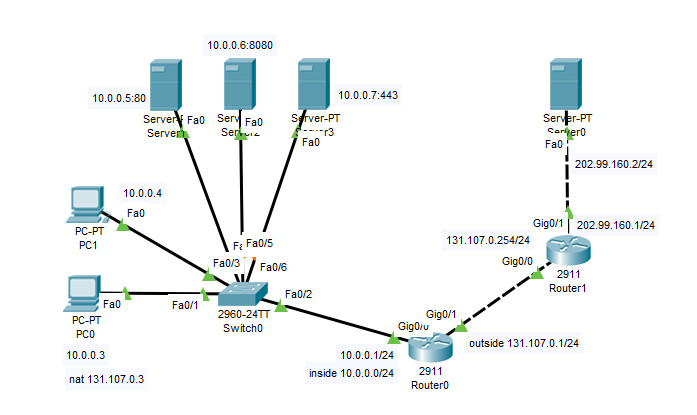
server1: 10.0.0.5 提供80埠web服務
server2: 10.0.0.6 8080 web
server3: 10.0.0.7 443 https
清除之前的nat配置
```bash
Router0(config)#no ip nat inside source list 8 pool tielemao
Router0(config)#no access-list 7 permit 10.0.0.0 0.0.0.255
```
啟用PAT,命令和之前的動態NAT命令極其相似, 規劃如下:
```
access-list 8 permit 10.0.0.0 0.0.0.255 # list可以不變
ip nat pool tielemao 131.107.0.1 131.107.0.3 netmask 255.255.255.0 # 仍然是有個pool池
//注意區別在後面加了個overload,即啟用PAT
ip nat inside source list 8 pool tielemao overload
```
配置如下,因list和pool都是在之前就有建立,所以其實就只敲一條命令就成了:
```bash
Router0(config)#ip nat inside source list 8 pool tielemao overload
ipnat_add_dynamic_cfg: id 3, flag 5, range 0
poolstart 131.107.0.1 poolend 131.107.0.3
id 3, flags 0, domain 0, lookup 0, aclnum 8 ,
aclname 8 , mapname idb 0
```
server1-3分別ping server0,可以ping通。
埠對映,要想讓內網的伺服器供外網訪問,還需要做埠對映:
```
//埠對映,將我們擁有的三個公網ip的80埠分別對映給三臺伺服器
ip nat inside source static tcp 10.0.0.5 80 131.107.0.3 80
ip nat inside source static tcp 10.0.0.6 443 131.107.0.2 443
ip nat inside source static tcp 10.0.0.7 80 131.107.0.1 8080
```
實際配置如下:
```bash
Router0(config)#ip nat inside source static tcp 10.0.0.5 80 131.107.0.3 80
```
```bash
Router0(config)#ip nat inside source static tcp 10.0.0.6 443 131.107.0.2 443
```
```bash
Router0(config)#ip nat inside source static tcp 10.0.0.7 80 131.107.0.1 8080
```
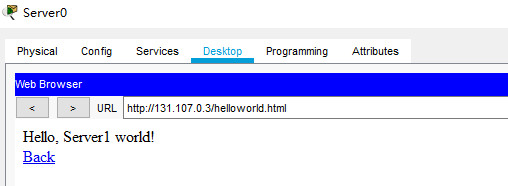
驗證,這次使用外網server0來訪問內網的三臺server
選擇Desktop中的Web Browser模擬瀏覽器訪問,如圖:
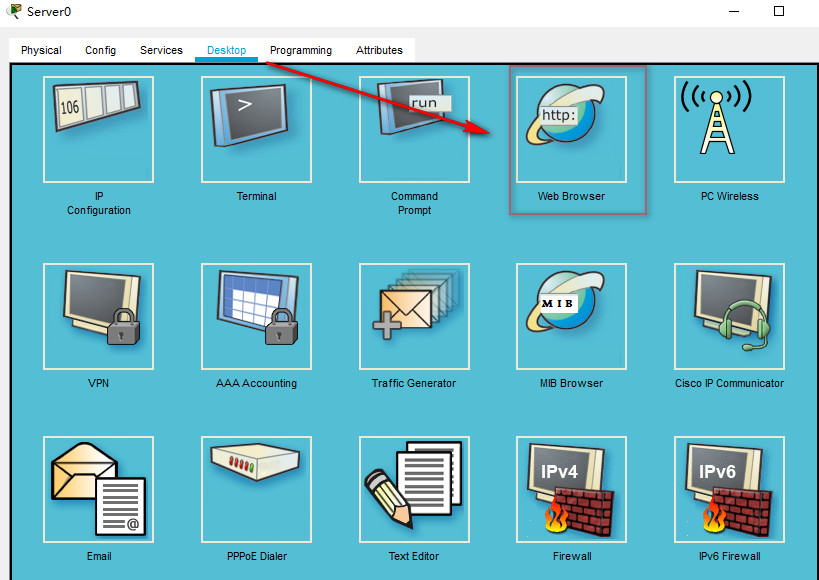
為了便於區別,可以分別在server1,2,3的Services上編輯一下hello world, 將相應的名字新增進去。
如圖,記得修改完成後點選save:
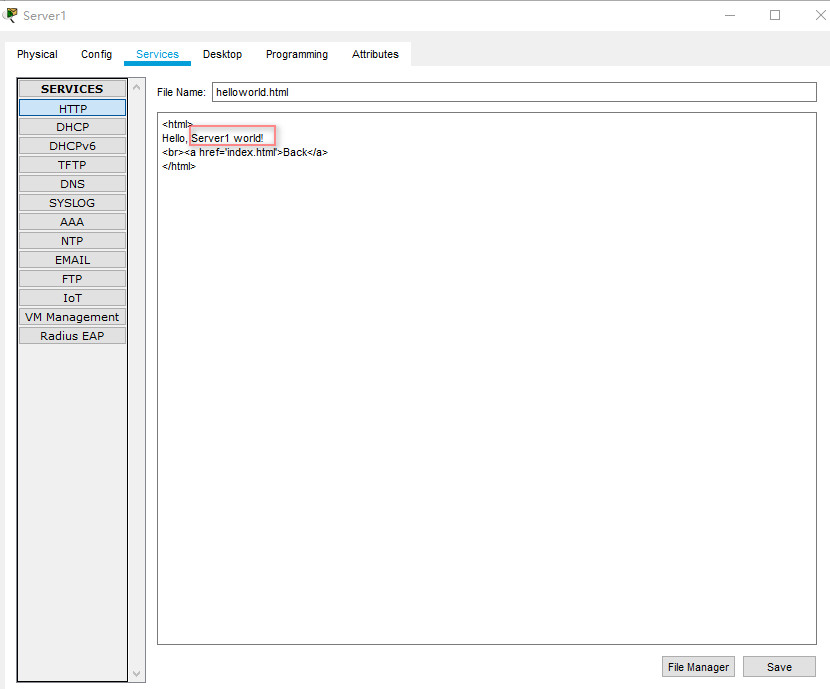
server1 80
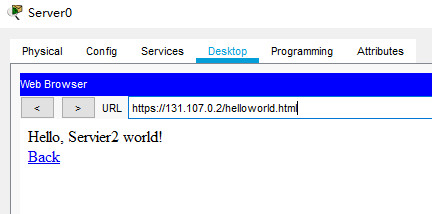
server2 443
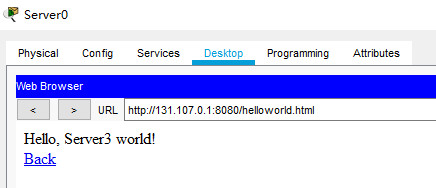
server3 8080
需要注意的是: 內網地址訪問外網地址時,PAT對外地址地址只有一個,
儘管這裡是用了3個外網地址做PAT,但其實所有機器訪問外網,路由器只會用一個外網地址,剩下兩個沒有用到.
但是,做埠對映的時候,是可以用到剩下的兩個IP的!
也就是,外網訪問內網伺服器時才會用到做過埠對映的IP.
所以,一般做PAT地址轉換,一組機器只用一個公網IP.
實驗至此,完美完成預期,也加深了對nat的理解
