Metasploit 一些重要模塊使用介紹
阿新 • • 發佈:2017-08-23
sftp ace nss left eating corrupt server closed sed
本文是"T00LS Metasploit(第一季)"的文檔版,是個人在觀看視頻動手操作的一個記錄,僅供學習。文中會介紹Metasploit的一些基本使用:端口掃描、smb掃描、服務識別、密碼嗅探等
一、端口掃描
關於端口掃描的話,我們首先想到的可能會是nmap,除此之外呢,Metasploit也內置了相應的掃描模塊。以目標:192.168.1.111為例
Nmap掃描
[email protected]:~# nmap -v -sV 192.168.1.111
Starting Nmap 7.50 ( https://nmap.org ) at 2017-08-22 07:56 EDT
NSE: Loaded 41 scripts for scanning.
Initiating ARP Ping Scan at 07:56
Scanning 192.168.1.111 [1 port]
Completed ARP Ping Scan at 07:56, 0.24s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 07:56
Completed Parallel DNS resolution of 1 host. at 07:56, 0.01s elapsed
Initiating SYN Stealth Scan at 07:56
Scanning 192.168.1.111 [1000 ports]
Discovered open port 443/tcp on 192.168.1.111
Discovered open port 445/tcp on 192.168.1.111
Discovered open port 139/tcp on 192.168.1.111
Discovered open port 135/tcp on 192.168.1.111
Discovered open port 3306/tcp on 192.168.1.111
Discovered open port 80/tcp on 192.168.1.111
Completed SYN Stealth Scan at 07:56, 7.16s elapsed (1000 total ports)
Initiating Service scan at 07:56
Scanning 6 services on 192.168.1.111
Completed Service scan at 07:57, 43.56s elapsed (6 services on 1 host)
NSE: Script scanning 192.168.1.111.
Initiating NSE at 07:57
Completed NSE at 07:57, 0.19s elapsed
Initiating NSE at 07:57
Completed NSE at 07:57, 0.00s elapsed
Nmap scan report for 192.168.1.111
Host is up (0.00058s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.3 ((Win32) OpenSSL/1.0.1c PHP/5.4.7)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/ssl Apache httpd (SSL-only mode)
445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:4B:66:A6 (VMware)
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.86 seconds
Raw packets sent: 1224 (53.840KB) | Rcvd: 1128 (45.152KB)Metasploit掃描
[email protected]:~# msfconsole msf > nmap -v -sV 192.168.1.111 【可以直接調用nmap】 [*] exec: nmap -v -sV 192.168.1.111 ... 結果同上,就不過多展示了 ... msf > search portscan Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/http/wordpress_pingback_access normal Wordpress Pingback Locator auxiliary/scanner/natpmp/natpmp_portscan normal NAT-PMP External Port Scanner auxiliary/scanner/portscan/acknormal TCP ACK Firewall Scanner auxiliary/scanner/portscan/ftpbounce normal FTP Bounce Port Scanner auxiliary/scanner/portscan/syn normal TCP SYN Port Scanner auxiliary/scanner/portscan/tcp normal TCP Port Scanner auxiliary/scanner/portscan/xmas normal TCP "XMas" Port Scanner auxiliary/scanner/sap/sap_router_portscanner normal SAPRouter Port Scanner
端口掃描模塊:可以看到有ack、syn、tcp等,以tcp端口掃描為例,目標機器:192.168.1.111。
auxiliary/scanner/portscan/tcp
msf > use auxiliary/scanner/portscan/tcp msf auxiliary(tcp) > show options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS yes The target address range or CIDR identifier THREADS 1 yes The number of concurrent threads TIMEOUT 1000 yes The socket connect timeout in milliseconds msf auxiliary(tcp) > set rhosts 192.168.1.111 【設置掃描目標】 rhosts => 192.168.1.111 msf auxiliary(tcp) > set threads 5 【設置掃描線程數】 threads => 5 msf auxiliary(tcp) > show options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS 192.168.1.111 yes The target address range or CIDR identifier THREADS 5 yes The number of concurrent threads TIMEOUT 1000 yes The socket connect timeout in milliseconds msf auxiliary(tcp) > run [*] 192.168.1.111: - 192.168.1.111:135 - TCP OPEN [*] 192.168.1.111: - 192.168.1.111:139 - TCP OPEN [*] 192.168.1.111: - 192.168.1.111:443 - TCP OPEN [*] 192.168.1.111: - 192.168.1.111:445 - TCP OPEN [*] 192.168.1.111: - 192.168.1.111:3306 - TCP OPEN
...
從上面可以看到tcp端口掃描的開放情況。
二、SMB掃描
可以用來獲取操作系統信息,請看...
msf auxiliary(tcp) > search smb_version Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/smb/smb_version normal SMB Version Detection msf auxiliary(tcp) > use auxiliary/scanner/smb/smb_version msf auxiliary(smb_version) > show options Module options (auxiliary/scanner/smb/smb_version): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target address range or CIDR identifier SMBDomain . no The Windows domain to use for authentication SMBPass no The password for the specified username SMBUser no The username to authenticate as THREADS 1 yes The number of concurrent threads msf auxiliary(smb_version) > set rhosts 192.168.1.111 【設置目標主機,單個主機】 rhosts => 192.168.1.111 msf auxiliary(smb_version) > set threads 5 【設置線程數】 threads => 5 msf auxiliary(smb_version) > run [*] 192.168.1.111:445 - Host is running Windows XP SP2+ (language:Chinese - Traditional) (name:CHINA-5D20EA9B7) (workgroup:WORKGROUP ) [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
上面展示的是掃描單個主機的情況,我們還可以用來掃描一個網段...
msf auxiliary(smb_version) > set rhosts 192.168.1.0/24 【當然也可以指定多個ip或一個ip範圍】 rhosts => 192.168.1.0/24 msf auxiliary(smb_version) > set threads 10 threads => 10 msf auxiliary(smb_version) > run [*] Scanned 30 of 256 hosts (11% complete) [*] Scanned 52 of 256 hosts (20% complete) [*] Scanned 77 of 256 hosts (30% complete) [*] 192.168.1.101:445 - Host is running Windows 10 Pro (build:15063) (name:TTCN-WYX) (workgroup:WORKGROUP ) [*] 192.168.1.103:445 - Host is running Windows XP SP0 / 1 (language:Chinese - Traditional) (name:STARNIGHT) (workgroup:WORKGROUP ) [*] Scanned 103 of 256 hosts (40% complete) [*] 192.168.1.111:445 - Host is running Windows XP SP2+ (language:Chinese - Traditional) (name:CHINA-5D20EA9B7) (workgroup:WORKGROUP ) [*] Scanned 128 of 256 hosts (50% complete) [*] Scanned 155 of 256 hosts (60% complete) [*] Scanned 180 of 256 hosts (70% complete) [*] Scanned 206 of 256 hosts (80% complete) [*] Scanned 231 of 256 hosts (90% complete) [*] Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed
三、服務識別
SSH服務識別
msf > search ssh_version Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/fuzzers/ssh/ssh_version_15 normal SSH 1.5 Version Fuzzer auxiliary/fuzzers/ssh/ssh_version_2 normal SSH 2.0 Version Fuzzer auxiliary/fuzzers/ssh/ssh_version_corrupt normal SSH Version Corruption auxiliary/scanner/ssh/ssh_version normal SSH Version Scanner msf > use auxiliary/scanner/ssh/ssh_version msf auxiliary(ssh_version) > show options Module options (auxiliary/scanner/ssh/ssh_version): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target address range or CIDR identifier RPORT 22 yes The target port (TCP) THREADS 1 yes The number of concurrent threads TIMEOUT 30 yes Timeout for the SSH probe msf auxiliary(ssh_version) > set rhosts 165.227.29.209 rhosts => 165.227.29.209 msf auxiliary(ssh_version) > set threads 10 threads => 10 msf auxiliary(ssh_version) > run [*] 165.227.29.209:22 - SSH server version: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2 ( service.version=7.2p2 openssh.comment=Ubuntu-4ubuntu2.2 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.certainty=0.75 service.protocol=ssh fingerprint_db=ssh.banner ) [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
FTP服務識別
msf > search ftp_version Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/ftp/ftp_version normal FTP Version Scanner msf > use auxiliary/scanner/ftp/ftp_version msf auxiliary(ftp_version) > show options Module options (auxiliary/scanner/ftp/ftp_version): Name Current Setting Required Description ---- --------------- -------- ----------- FTPPASS [email protected] no The password for the specified username FTPUSER anonymous no The username to authenticate as RHOSTS yes The target address range or CIDR identifier RPORT 21 yes The target port (TCP) THREADS 1 yes The number of concurrent threads msf auxiliary(ftp_version) > set rhosts 112.86.69.175 【隨手在shodan上搜索到的一臺主機】 rhosts => 112.86.69.175 msf auxiliary(ftp_version) > set threads 10 threads => 10 msf auxiliary(ftp_version) > run [*] 112.86.69.175:21 - FTP Banner: ‘220 Microsoft FTP Service\x0d\x0a‘ [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
四、密碼嗅探
FTP密碼嗅探
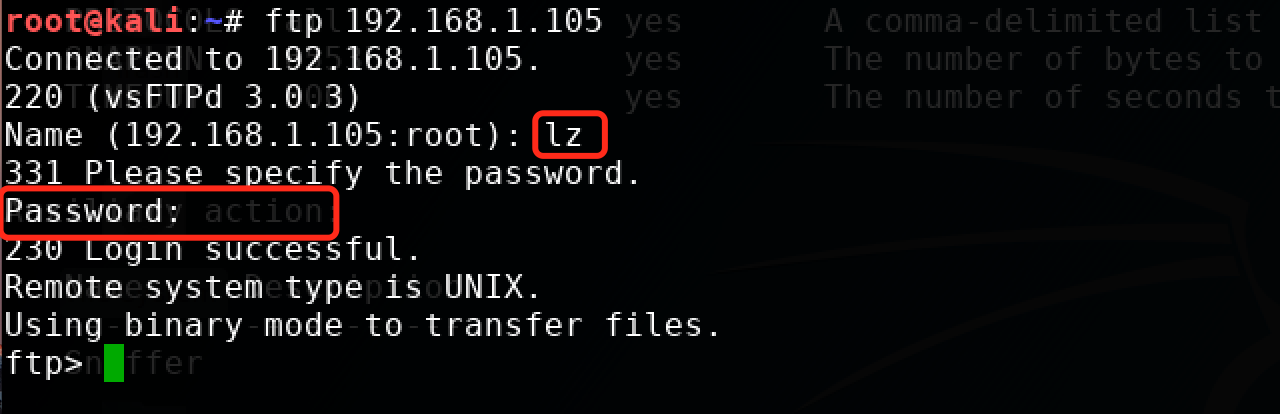
在測試機ubuntu16.04: 192.168.1.105安裝了一個vsftpd服務,kali:192.168.1.110進行登錄測試和嗅探密碼。
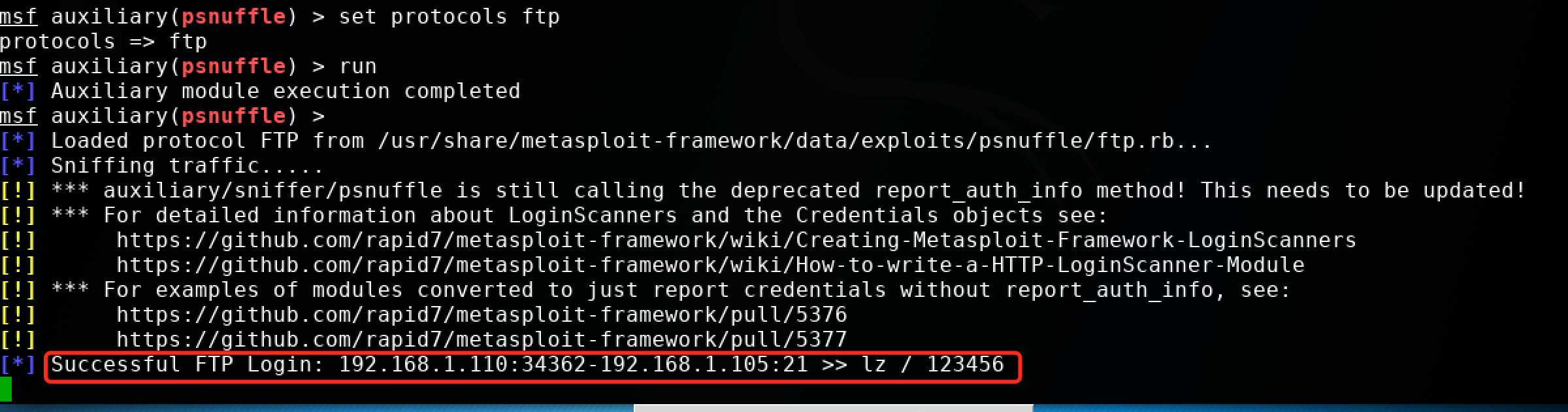
msf > search psnuffle Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/sniffer/psnuffle normal pSnuffle Packet Sniffer msf > use auxiliary/sniffer/psnuffle msf auxiliary(psnuffle) > show options Module options (auxiliary/sniffer/psnuffle): Name Current Setting Required Description ---- --------------- -------- ----------- FILTER no The filter string for capturing traffic INTERFACE no The name of the interface PCAPFILE no The name of the PCAP capture file to process PROTOCOLS all yes A comma-delimited list of protocols to sniff or "all". SNAPLEN 65535 yes The number of bytes to capture TIMEOUT 500 yes The number of seconds to wait for new data Auxiliary action: Name Description ---- ----------- Sniffer msf auxiliary(psnuffle) > set protocols ftp 【有必要設置一下監聽的協議】 protocols => ftp msf auxiliary(psnuffle) > run [*] Auxiliary module execution completed msf auxiliary(psnuffle) > [*] Loaded protocol FTP from /usr/share/metasploit-framework/data/exploits/psnuffle/ftp.rb... [*] Sniffing traffic..... [!] *** auxiliary/sniffer/psnuffle is still calling the deprecated report_auth_info method! This needs to be updated! [!] *** For detailed information about LoginScanners and the Credentials objects see: [!] https://github.com/rapid7/metasploit-framework/wiki/Creating-Metasploit-Framework-LoginScanners [!] https://github.com/rapid7/metasploit-framework/wiki/How-to-write-a-HTTP-LoginScanner-Module [!] *** For examples of modules converted to just report credentials without report_auth_info, see: [!] https://github.com/rapid7/metasploit-framework/pull/5376 [!] https://github.com/rapid7/metasploit-framework/pull/5377 [*] Successful FTP Login: 192.168.1.110:34362-192.168.1.105:21 >> lz / 123456
登錄截圖:
嗅探密碼運行截圖:
五、幾個重要模塊
SNMP登錄
msf > search snmp_login Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/snmp/snmp_login normal SNMP Community Login Scanner msf > use auxiliary/scanner/snmp/snmp_login msf auxiliary(snmp_login) > show options Module options (auxiliary/scanner/snmp/snmp_login): Name Current Setting Required Description ---- --------------- -------- ----------- BLANK_PASSWORDS false no Try blank passwords for all users BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5 DB_ALL_CREDS false no Try each user/password couple stored in the current database DB_ALL_PASS false no Add all passwords in the current database to the list DB_ALL_USERS false no Add all users in the current database to the list PASSWORD no The password to test PASS_FILE /usr/share/metasploit-framework/data/wordlists/snmp_default_pass.txt no File containing communities, one per line RHOSTS yes The target address range or CIDR identifier RPORT 161 yes The target port STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host THREADS 1 yes The number of concurrent threads USER_AS_PASS false no Try the username as the password for all users VERBOSE true yes Whether to print output for all attempts VERSION 1 yes The SNMP version to scan (Accepted: 1, 2c, all)
SNMP枚舉
msf > search snmp_enum Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/snmp/cambium_snmp_loot normal Cambium ePMP SNMP Enumeration auxiliary/scanner/snmp/sbg6580_enum normal ARRIS / Motorola SBG6580 Cable Modem SNMP Enumeration Module auxiliary/scanner/snmp/snmp_enum normal SNMP Enumeration Module auxiliary/scanner/snmp/snmp_enum_hp_laserjet normal HP LaserJet Printer SNMP Enumeration auxiliary/scanner/snmp/snmp_enumshares normal SNMP Windows SMB Share Enumeration auxiliary/scanner/snmp/snmp_enumusers normal SNMP Windows Username Enumeration msf > use auxiliary/scanner/snmp/snmp_enum msf auxiliary(snmp_enum) > show options Module options (auxiliary/scanner/snmp/snmp_enum): Name Current Setting Required Description ---- --------------- -------- ----------- COMMUNITY public yes SNMP Community String RETRIES 1 yes SNMP Retries RHOSTS yes The target address range or CIDR identifier RPORT 161 yes The target port (UDP) THREADS 1 yes The number of concurrent threads TIMEOUT 1 yes SNMP Timeout VERSION 1 yes SNMP Version <1/2c>
SMB登錄
登錄驗證在實驗的時候,並沒有完美成功,而是出現一個這樣的錯誤"This system does not accept authentication with any credentials, proceeding with brute force"。故這裏不做過多演示:
msf auxiliary(smb_login) > search smb_login Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/fuzzers/smb/smb_ntlm1_login_corrupt normal SMB NTLMv1 Login Request Corruption auxiliary/scanner/smb/smb_login normal SMB Login Check Scanner msf auxiliary(smb_login) > use auxiliary/scanner/smb/smb_login msf auxiliary(smb_login) > show options Module options (auxiliary/scanner/smb/smb_login): Name Current Setting Required Description ---- --------------- -------- ----------- ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected BLANK_PASSWORDS false no Try blank passwords for all users BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5 DB_ALL_CREDS false no Try each user/password couple stored in the current database DB_ALL_PASS false no Add all passwords in the current database to the list DB_ALL_USERS false no Add all users in the current database to the list DETECT_ANY_AUTH true no Enable detection of systems accepting any authentication PASS_FILE no File containing passwords, one per line PRESERVE_DOMAINS true no Respect a username that contains a domain name. Proxies no A proxy chain of format type:host:port[,type:host:port][...] RECORD_GUEST false no Record guest-privileged random logins to the database RHOSTS 192.168.1.111 yes The target address range or CIDR identifier RPORT 445 yes The SMB service port (TCP) SMBDomain . no The Windows domain to use for authentication SMBPass 123456 no The password for the specified username SMBUser administrator no The username to authenticate as STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host THREADS 30 yes The number of concurrent threads USERPASS_FILE no File containing users and passwords separated by space, one pair per line USER_AS_PASS false no Try the username as the password for all users USER_FILE no File containing usernames, one per line VERBOSE true yes Whether to print output for all attempts
VNC身份驗證
msf > search vnc_none_auth Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/vnc/vnc_none_auth normal VNC Authentication None Detection msf > use auxiliary/scanner/vnc/vnc_none_auth msf auxiliary(vnc_none_auth) > show options Module options (auxiliary/scanner/vnc/vnc_none_auth): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target address range or CIDR identifier RPORT 5900 yes The target port (TCP) THREADS 1 yes The number of concurrent threads
視頻教程後面的幾個就不介紹了,整體來說,第一季的視頻比較雞肋,僅僅是操作上的一個簡單演示,第二季令人期待一些 ~
Metasploit 一些重要模塊使用介紹
