cisco VPN 第二天ikev2實驗筆記
阿新 • • 發佈:2017-08-27
ikev2
IKEv2 配置實驗
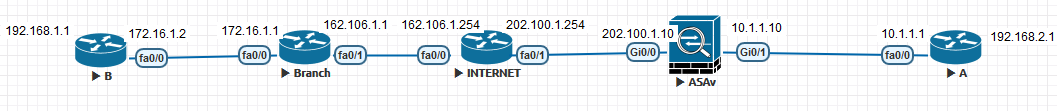
Branch:
1.配置proposal
crypto ikev2 proposal ikev2-proposal encryption 3des aes-cbc-256 integrity sha256 sha512 group 2 5 14
2.配置 policy(可選)
crypto ikev2 policy ikev2-policy proposal ikev2-proposal
3.配置keyring(必須)
crypto ikev2 keyring ikev2-keyring peer center-asa address 202.100.1.10 pre-shared-key pre-key
4.配置profile(必須)
crypto ikev2 profile ikev2-profile match identity remote address 202.100.1.10 255.255.255.255 identity local address 162.106.1.1 authentication remote pre-share authentication local pre-share keyring local ikev2-keyring
5.配置transform-set(可選)
crypto ipsec transform-set trans1 esp-des esp-md5-hmac mode tunnel crypto ipsec transform-set trans2 esp-3des esp-sha256-hmac mode tunnel show crypto ipsec transform-set
6.配置感興趣流(必須)
ip access-list extended vpn permit ip 192.168.1.0(本端) 0.0.0.255 192.168.2.0(對端) 0.0.0.255
7.配置crypto map(必須)
crypto map crypto-map 10 ipsec-isakmp set peer 202.100.1.10 set transform-set trans1 trans2 set ikev2-profile ikev2-profile match address vpn
8.接口調用map(必須)
interface f0/1 ip add 162.100.1.1 255.255.255.0 crypto map crypto-map
ASA:
1.相關接口激活ikev2
crypto ikev2 enable outside
2.配置policy
crypto ikev2 policy 10 encryption aes-256 des integrity sha256 sha group 2 1 prf sha256 sha lifetime seconds 86400 tunnel-group 162.106.1.1 type ipsec-l2l tunnel-group 162.106.1.1 ipsec-attributes ikev2 remote-authentication pre-shared-key pre-key ikev2 local-authentication pre-shared-key pre-key
3.配置transform-set
crypto ipsec ikev2 ipsec-proposal trans protocol esp encryption aes-192 des protocol esp integrity sha-1 md5
4.配置感興趣流
access-list vpn extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
5.配置crypto map
crypto map crypto-map 10 match address vpn crypto map crypto-map 10 set peer 162.106.1.1 crypto map crypto-map 10 set ikev2 ipsec-proposal trans crypto map crypto-map interface outside
--------------------------------
狀態檢查:
B#ping 192.168.2.1 so 192.168.1.1
*Mar 2 01:13:44.517: %SYS-5-CONFIG_I: Configured from console by console
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/30/40 ms
Branch#show crypto session
Crypto session current status
Interface: GigabitEthernet0/1
Profile: ikev2-profile
Session status: UP-ACTIVE
Peer: 202.100.1.10 port 500
Session ID: 1
IKEv2 SA: local 162.106.1.1/500 remote 202.100.1.10/500 Active
IPSEC FLOW: permit ip 192.168.1.0/255.255.255.0 192.168.2.0/255.255.255.0
Active SAs: 2, origin: crypto mapBranch#show crypto ipsec sa
interface: GigabitEthernet0/1
Crypto map tag: crypto-map, local addr 162.106.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer 202.100.1.10 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
Branch#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 162.106.1.1/500 202.100.1.10/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:2, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/156 sec
IPv6 Crypto IKEv2 SA
Branch#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 114 0 0 162.106.1.1
2 IPsec DES+MD5 0 114 114 162.106.1.1
1001 IKEv2 SHA256+AES256 0 0 0 162.106.1.1show crypto ipsec status
ASA# show crypto ipsec sa
interface: outside
Crypto map tag: crypto-map, seq num: 10, local addr: 202.100.1.10
access-list vpn extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
current_peer: 162.106.1.1
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9cisco VPN 第二天ikev2實驗筆記
