cisco VPN 實驗筆記
阿新 • • 發佈:2017-07-25
vpn
加密點不等於通訊點為Tunnel Mode
IKEv1 配置實例
VPN觸發的過程:
1.包進入VPN設備,檢查遠端通訊點的路由,路由引導流量出適當的接口 2.包在出接口過程中撞擊上MAP 3.流量匹配上MAP的ACL(感興趣流),觸發加密 4.發起和PEER的IKE協商,VPN設備檢查去忘PEER(遠端加密點)的路由
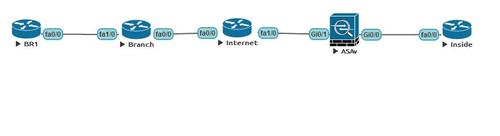
1.設備配置基礎配置
BR1#show ip int b
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 172.16.1.2 YES manual up up
Loopback0 192.168.1.1 YES manual up up
靜態路由:ip route 192.168.2.0 255.255.255.0 172.16.1.1
------------------------------------------------
Branch#show ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 162.106.1.1 YES manual up up
FastEthernet1/0 172.16.1.1 YES manual up up
靜態路由
ip route 192.168.1.0 255.255.255.0 172.16.1.2
ip route 192.168.2.0 255.255.255.0 162.106.1.254
ip route 202.100.1.0 255.255.255.0 162.106.1.254
-------------------------------------------------
Internet#show ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 162.106.1.254 YES manual up up
FastEthernet1/0 202.100.1.254 YES manual up up
------------------------------------------------------
ciscoasa(config)# show int ip br
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 10.1.1.10 YES manual up up
GigabitEthernet0/1 202.100.1.10 YES manual up up
route outside 0.0.0.0 0.0.0.0 202.100.1.254 1
route inside 192.168.2.0 255.255.255.0 10.1.1.1 1
route inside 0.0.0.0 0.0.0.0 10.1.1.1 tunneled
------------------------------------------------------
Inside#show ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.1.1.1 YES manual up up
Loopback0 192.168.2.1 YES manual up
靜態路由:ip route 192.168.1.0 255.255.255.0 10.1.1.10
-----------------------------------------------------------------------
2.激活ISAKMP
IOS:crypto isakmp enable
ASA:crypto ikev1 enable outside
3.配置ISAKMP策略:
crypto isakmp policy 10
encryption 3des
hash md5
authentication Pre-Share
group 2
-----------------------------------------
ciscoasa(config)# crypto ikev1 policy 10
ciscoasa(config-ikev1-policy)# encryption 3des
ciscoasa(config-ikev1-policy)# hash md5
ciscoasa(config-ikev1-policy)# authentication pre-share
ciscoasa(config-ikev1-policy)# group 2
4.配置ISAKMP預共享密碼
crypto isakmp key vpnkey address 202.100.1.10
-----------------
ciscoasa(config)# tunnel-group 162.106.1.1 type ipsec-l2l
ciscoasa(config)# tunnel-group 162.106.1.1 ipsec-attributes
ciscoasa(config-tunnel-ipsec)# ikev1 pre-shared-key vpnkey
5.配置感興趣流
ip access-list extended vpn
permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
--------------
access-list vpn extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
6.配置IPSec策略(轉換集)
crypto ipsec transform-set transvpn esp-des esp-md5-hmac
----------------------------------------------
crypto ipsec ikev1 transform-set tranvpn esp-des esp-md5-hmac
7.配置crypto map(第二階段)
crypto map cry-map 10 ipsec-isakmp
set peer 202.100.1.10
set transform-set transvpn
match address vpn
--------------------------------------------
ciscoasa(config)# crypto map cry-map 10 match address vpn
ciscoasa(config)# crypto map cry-map 10 set peer 162.106.1.1
ciscoasa(config)# crypto map cry-map 10 set ikev1 transform-set transvpn
8.調用crypto map
interface FastEthernet0/0
ip address 162.106.1.1 255.255.255.0
crypto map cry-map
-----------------------------------------------------
ciscoasa(config)# crypto map cry-map interface outside
9.ping測試
BR1#ping 192.168.2.1 so 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/43/60 ms
10.查看IKE SA
Branch#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
202.100.1.10 162.106.1.1 QM_IDLE 1001 ACTIVE
10.查看IPSec SA
show crypto ipsec sa
11.
Branch#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 110 110 162.106.1.1
2 IPsec DES+MD5 114 0 0 162.106.1.1
1001 IKE MD5+3DES 0 0 0 162.106.1.1cisco VPN 實驗筆記
