實際NAT對IPSec ×××的影響
在實際部署的IPSec ×××中經常會遇到由於NAT的問題,而導致IPSec ×××無法建立的問題,例如,一個公司的總部通過運營商連接分支機構,雖然在邊界路由器都有固定的IP地址,而且雙方可達,但是,可能出現的問題是,如果在分支機構邊界路由器使用的IP地址是經過運營商時,被運營商做了一個NAT,那麽建立IPSec ×××的時候將會出現問題,部署人員可能並沒有考慮到運營商在中間有什麽操作。
例如如下拓撲:

針對上面的拓撲配置,先保證各設備的可達性,然後在R1和R4上創建IPSec ×××,在R2做NAT,將12.1.1.0/24網段的地址翻譯成23.1.1.0/24(範圍先設置為100-200),先在這樣的情況下去建立IPSec ×××。
二、查看debug信息
R1#debug cry isakmp
Crypto ISAKMP debugging is on
R1#debug crypto ipsec
Crypto IPSEC debugging is on
R1#
R1#
*Jun 15 21:34:51.731: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (N) NEW SA
*Jun 15 21:34:51.735: ISAKMP: Created a peer struct for 34.1.1.4, peer port 500
*Jun 15 21:34:51.735: ISAKMP: New peer created peer = 0x6B03E410 peer_handle = 0x80000002
*Jun 15 21:34:51.739: ISAKMP: Locking peer struct 0x6B03E410, refcount 1 for crypto_isakmp_process_block
*Jun 15 21:34:51.739: ISAKMP: local port 500, remote port 500
*Jun 15 21:34:51.743: ISAKMP:(0):insert sa successfully sa = 6B054290
*Jun 15 21:34:51.751: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Jun 15 21:34:51.751: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
*Jun 15 21:34:51.759: ISAKMP:(0): processing SA payload. message ID = 0
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
*Jun 15 21:34:51.759: ISAKMP (0): vendor ID is NAT-T RFC 3947
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 245 mismatch
*Jun 15 21:34:51.759: ISAKMP (0): vendor ID is NAT-T v7
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 157 mismatch
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID is NAT-T v3
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID is NAT-T v2
*Jun 15 21:34:51.759: ISAKMP:(0):found peer pre-shared key matching 34.1.1.4
*Jun 15 21:34:51.759: ISAKMP:(0): local preshared key found
*Jun 15 21:34:51.759: ISAKMP : Scanning profiles for xauth ...
*Jun 15 21:34:51.759: ISAKMP:(0):Checking ISAKMP transform 1 against priority 10 policy
*Jun 15 21:34:51.759: ISAKMP: encryption 3DES-CBC
*Jun 15 21:34:51.759: ISAKMP: hash MD5
*Jun 15 21:34:51.759: ISAKMP: default group 2
*Jun 15 21:34:51.759: ISAKMP: auth pre-share
*Jun 15 21:34:51.759: ISAKMP: life type in seconds
*Jun 15 21:34:51.759: ISAKMP: life duration (basic) of 28800
*Jun 15 21:34:51.759: ISAKMP:(0):atts are acceptable. Next payload is 0
*Jun 15 21:34:51.759: ISAKMP:(0):Acceptable atts:actual life: 0
*Jun 15 21:34:51.759: ISAKMP:(0):Acceptable atts:life: 0
*Jun 15 21:34:51.759: ISAKMP:(0):Basic life_in_seconds:28800
*Jun 15 21:34:51.759: ISAKMP:(0):Returning Actual lifetime: 28800
*Jun 15 21:34:51.759: ISAKMP:(0)::Started lifetime timer: 28800.
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
*Jun 15 21:34:51.759: ISAKMP (0): vendor ID is NAT-T RFC 3947
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 245 mismatch
*Jun 15 21:34:51.759: ISAKMP (0): vendor ID is NAT-T v7
R1#
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 157 mismatch
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID is NAT-T v3
*Jun 15 21:34:51.759: ISAKMP:(0): processing vendor id payload
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
*Jun 15 21:34:51.759: ISAKMP:(0): vendor ID is NAT-T v2
*Jun 15 21:34:51.759: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Jun 15 21:34:51.759: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
*Jun 15 21:34:51.759: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
*Jun 15 21:34:51.759: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Jun 15 21:34:51.759: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:34:51.759: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Jun 15 21:34:51.763: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
R1#
*Jun 15 21:35:01.711: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Jun 15 21:35:01.715: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet. >>>這是因為對端一致在ping產生感興趣流導致
*Jun 15 21:35:01.715: ISAKMP:(0): retransmitting due to retransmit phase 1 >>>>即便只ping一個包,在沒有收到對端的SA時,也會重傳5次!
*Jun 15 21:35:02.215: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Jun 15 21:35:02.215: ISAKMP (0): incrementing error counter on sa, attempt 1 of 5: retransmit phase 1
*Jun 15 21:35:02.219: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Jun 15 21:35:02.219: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Jun 15 21:35:02.219: ISAKMP:(0):Sending an IKE IPv4 Packet.
R1#
*Jun 15 21:35:11.723: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Jun 15 21:35:11.723: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Jun 15 21:35:11.727: ISAKMP:(0): retransmitting due to retransmit phase 1
*Jun 15 21:35:12.227: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Jun 15 21:35:12.227: ISAKMP (0): incrementing error counter on sa, attempt 2 of 5: retransmit phase 1
*Jun 15 21:35:12.231: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Jun 15 21:35:12.231: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Jun 15 21:35:12.231: ISAKMP:(0):Sending an IKE IPv4 Packet.
R1#
*Jun 15 21:35:21.759: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Jun 15 21:35:21.763: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Jun 15 21:35:21.763: ISAKMP:(0): retransmitting due to retransmit phase 1
*Jun 15 21:35:22.263: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Jun 15 21:35:22.263: ISAKMP (0): incrementing error counter on sa, attempt 3 of 5: retransmit phase 1
*Jun 15 21:35:22.267: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Jun 15 21:35:22.267: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Jun 15 21:35:22.267: ISAKMP:(0):Sending an IKE IPv4 Packet.
R1#
*Jun 15 21:35:31.763: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Jun 15 21:35:31.763: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Jun 15 21:35:31.767: ISAKMP:(0): retransmitting due to retransmit phase 1
*Jun 15 21:35:32.267: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Jun 15 21:35:32.267: ISAKMP (0): incrementing error counter on sa, attempt 4 of 5: retransmit phase 1
*Jun 15 21:35:32.271: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Jun 15 21:35:32.271: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Jun 15 21:35:32.271: ISAKMP:(0):Sending an IKE IPv4 Packet.
R1#
*Jun 15 21:35:41.791: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Jun 15 21:35:41.791: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Jun 15 21:35:41.795: ISAKMP:(0): retransmitting due to retransmit phase 1
*Jun 15 21:35:42.295: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Jun 15 21:35:42.295: ISAKMP (0): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Jun 15 21:35:42.295: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Jun 15 21:35:42.295: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Jun 15 21:35:42.295: ISAKMP:(0):Sending an IKE IPv4 Packet.
R1#
*Jun 15 21:35:52.295: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Jun 15 21:35:52.295: ISAKMP:(0):peer does not do paranoid keepalives.
*Jun 15 21:35:52.299: ISAKMP:(0):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer 34.1.1.4)
*Jun 15 21:35:52.307: ISAKMP:(0):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer 34.1.1.4)
*Jun 15 21:35:52.307: ISAKMP: Unlocking peer struct 0x6B03E410 for isadb_mark_sa_deleted(), count 0
*Jun 15 21:35:52.311: ISAKMP: Deleting peer node by peer_reap for 34.1.1.4: 6B03E410
*Jun 15 21:35:52.319: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Jun 15 21:35:52.319: ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_DEST_SA
*Jun 15 21:35:52.323: IPSEC(key_engine): got a queue event with 1 KMI message(s)
R4#ping 1.1.1.1 so 4.4.4.4 re 20
Type escape sequence to abort.
Sending 20, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 4.4.4.4
*Jun 15 21:34:51.603: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 34.1.1.4:500, remote= 12.1.1.1:500,
local_proxy= 4.4.4.0/255.255.255.0/256/0,
remote_proxy= 1.1.1.0/255.255.255.0/256/0,
protocol= ESP, transform= esp-3des esp-sha256-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Jun 15 21:34:51.615: ISAKMP:(0): SA request profile is (NULL)
*Jun 15 21:34:51.619: ISAKMP: Created a peer struct for 12.1.1.1, peer port 500
*Jun 15 21:34:51.619: ISAKMP: New peer created peer = 0x6B0639F8 peer_handle = 0x80000002
*Jun 15 21:34:51.623: ISAKMP: Locking peer struct 0x6B0639F8, refcount 1 for isakmp_initiator
*Jun 15 21:34:51.623: ISAKMP: local port 500, remote port 500
*Jun 15 21:34:51.627: ISAKMP: set new node 0 to QM_IDLE
*Jun 15 21:34:51.639: ISAKMP:(0):insert sa successfully sa = 6B062F1C
*Jun 15 21:34:51.643: ISAKMP:(0):Can not start Aggressive mode, trying Main mode.
*Jun 15 21:34:51.643: ISAKMP:(0):found peer pre-shared key matching 12.1.1.1
*Jun 15 21:34:51.647: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
*Jun 15 21:34:51.647: ISAKMP:(0): constructed NAT-T vendor-07 ID
*Jun 15 21:34:51.651: ISAKMP:(0): constructed NAT-T vendor-03 ID
*Jun 15 21:34:51.651: ISAKMP:(0): constructed NAT-T vendor-02 ID
*Jun 15 21:34:51.651: ISAKMP:(0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Jun 15 21:34:51.651: ISAKMP:(0):Old State = IKE_READY New State = IKE_I_MM1
*Jun 15 21:34:51.651: ISAKMP:(0): beginning Main Mode exchange
*Jun 15 21:34:51.651: ISAKMP:(0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:34:51.651: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:34:51.783: ISAKMP (0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA
*Jun 15 21:34:51.783: %CRYPTO-4-IKMP_NO_SA: IKE message from 23.1.1.100 has no SA and is not an initialization offer.....
*Jun 15 21:35:01.651: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE...
*Jun 15 21:35:01.651: ISAKMP (0): incrementing error counter on sa, attempt 1 of 5: retransmit phase 1
*Jun 15 21:35:01.655: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE
*Jun 15 21:35:01.655: ISAKMP:(0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:35:01.655: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:35:02.259: ISAKMP (0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Jun 15 21:35:11.655: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE...
*Jun 15 21:35:11.655: ISAKMP (0): incrementing error counter on sa, attempt 2 of 5: retransmit phase 1
*Jun 15 21:35:11.659: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE
*Jun 15 21:35:11.659: ISAKMP:(0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:35:11.659: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:35:12.247: ISAKMP (0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Jun 15 21:35:21.603: IPSEC(key_engine): request timer fired: count = 1,
(identity) local= 34.1.1.4:0, remote= 12.1.1.1:0,
local_proxy= 4.4.4.0/255.255.255.0/256/0,
remote_proxy= 1.1.1.0/255.255.255.0/256/0
*Jun 15 21:35:21.607: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 34.1.1.4:500, remote= 12.1.1.1:500,
local_proxy= 4.4.4.0/255.255.255.0/256/0,
remote_proxy= 1.1.1.0/255.255.255.0/256/0,
protocol= ESP, transform= esp-3des esp-sha256-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Jun 15 21:35:21.623: ISAKMP: set new node 0 to QM_IDLE
*Jun 15 21:35:21.627: ISAKMP:(0):SA is still budding. Attached new ipsec request to it. (local 34.1.1.4, remote 12.1.1.1)
*Jun 15 21:35:21.627: ISAKMP: Error while processing SA request: Failed to initialize SA
*Jun 15 21:35:21.631: ISAKMP: Error while processing KMI message 0, error 2.
*Jun 15 21:35:21.663: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE...
*Jun 15 21:35:21.663: ISAKMP (0): incrementing error counter on sa, attempt 3 of 5: retransmit phase 1
*Jun 15 21:35:21.667: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE
*Jun 15 21:35:21.667: ISAKMP:(0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:35:21.667: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:35:22.315: ISAKMP (0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
Success rate is 0 percent (0/20)
R4#
*Jun 15 21:35:31.671: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE...
*Jun 15 21:35:31.671: ISAKMP (0): incrementing error counter on sa, attempt 4 of 5: retransmit phase 1
*Jun 15 21:35:31.675: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE
*Jun 15 21:35:31.675: ISAKMP:(0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:35:31.675: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:35:32.287: ISAKMP (0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA
R4#
*Jun 15 21:35:41.679: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE...
*Jun 15 21:35:41.679: ISAKMP (0): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Jun 15 21:35:41.683: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE
*Jun 15 21:35:41.683: ISAKMP:(0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:35:41.683: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:35:42.347: ISAKMP (0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA
R4#
*Jun 15 21:35:51.607: IPSEC(key_engine): request timer fired: count = 2,
(identity) local= 34.1.1.4:0, remote= 12.1.1.1:0,
local_proxy= 4.4.4.0/255.255.255.0/256/0,
remote_proxy= 1.1.1.0/255.255.255.0/256/0
*Jun 15 21:35:51.687: ISAKMP:(0): retransmitting phase 1 MM_NO_STATE...
*Jun 15 21:35:51.687: ISAKMP:(0):peer does not do paranoid keepalives.
*Jun 15 21:35:51.691: ISAKMP:(0):deleting SA reason "Death by retransmission P1" state (I) MM_NO_STATE (peer 12.1.1.1)
*Jun 15 21:35:51.711: ISAKMP:(0):deleting SA reason "Death by retransmission P1" state (I) MM_NO_STATE (peer 12.1.1.1)
R4#
*Jun 15 21:35:51.715: ISAKMP: Unlocking peer struct 0x6B0639F8 for isadb_mark_sa_deleted(), count 0
*Jun 15 21:35:51.719: ISAKMP: Deleting peer node by peer_reap for 12.1.1.1: 6B0639F8
*Jun 15 21:35:51.723: ISAKMP:(0):deleting node -797028350 error FALSE reason "IKE deleted"
*Jun 15 21:35:51.727: ISAKMP:(0):deleting node 676799932 error FALSE reason "IKE deleted"
*Jun 15 21:35:51.727: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Jun 15 21:35:51.727: ISAKMP:(0):Old State = IKE_I_MM1 New State = IKE_DEST_SA
*Jun 15 21:35:51.735: IPSEC(key_engine): got a queue event with 1 KMI message(s)
R4#
*Jun 15 21:36:41.723: ISAKMP:(0):purging node -797028350
*Jun 15 21:36:41.727: ISAKMP:(0):purging node 676799932
R4#
*Jun 15 21:36:51.727: ISAKMP:(0):purging SA., sa=6B062F1C, delme=6B062F1C
分析一下如果流量是從R1到R4,那麽R1會向R4發起協商,R4收到的會是源為23.1.1.100的發來的SA協商報文,它和本地比較,發現本地沒有該Peer的策略,那麽會拒絕,效果如下:
R4#
*Jun 15 21:59:23.991: ISAKMP:(0):No pre-shared key with 23.1.1.100!
*Jun 15 21:59:23.991: ISAKMP : Scanning profiles for xauth ...
*Jun 15 21:59:23.991: ISAKMP:(0):Checking ISAKMP transform 1 against priority 10 policy
*Jun 15 21:59:23.991: ISAKMP: encryption 3DES-CBC
*Jun 15 21:59:23.991: ISAKMP: hash MD5
*Jun 15 21:59:23.991: ISAKMP: default group 2
*Jun 15 21:59:23.991: ISAKMP: auth pre-share
*Jun 15 21:59:23.991: ISAKMP: life type in seconds
*Jun 15 21:59:23.991: ISAKMP: life duration (basic) of 28800
*Jun 15 21:59:23.991: ISAKMP:(0):Preshared authentication offered but does not match policy!
*Jun 15 21:59:23.991: ISAKMP:(0):atts are not acceptable. Next payload is 0
*Jun 15 21:59:23.991: ISAKMP:(0):no offers accepted!
*Jun 15 21:59:23.991: ISAKMP:(0): phase 1 SA policy not acceptable! (local 34.1.1.4 remote 23.1.1.100)
*Jun 15 21:59:23.991: ISAKMP (0): incrementing error counter on sa, attempt 1 of 5: construct_fail_ag_init
*Jun 15 21:59:23.991: ISAKMP:(0): Failed to construct AG informational message.
*Jun 15 21:59:23.991: ISAKMP:(0): sending packet to 23.1.1.100 my_port 500 peer_port 500 (R) MM_NO_STATE
*Jun 15 21:59:23.991: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:59:23.991: ISAKMP:(0):peer does not do paranoid keepalives.
*Jun 15 21:59:23.995: ISAKMP:(0):deleting SA reason "Phase1 SA policy proposal not accepted" state (R) MM_NO_STA
而R1則會收到由於R4沒有對應的Peer的策略的信息告知沒有hash,拒絕建立×××,具體情況如下:
R1#
*Jun 15 21:59:23.947: ISAKMP:(0): beginning Main Mode exchange
*Jun 15 21:59:23.947: ISAKMP:(0): sending packet to 34.1.1.4 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jun 15 21:59:23.947: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jun 15 21:59:24.075: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (I) MM_NO_STATE
*Jun 15 21:59:24.079: ISAKMP:(0):Notify has no hash. Rejected.
最終還是重傳5次而刪除準備協商起來的SA。
三、解決方法
將R4的Peer設置為NAT翻譯後的地址,這裏是23.1.1.100/24
R4(config)#no crypto isakmp key 0 cisco address 12.1.1.1
R4(config)#crypto isakmp key 0 cisco address 23.1.1.100
R4(config)#crypto map cisco 10 ipsec-isakmp
R4(config-crypto-map)#no set peer 12.1.1.1
R4(config-crypto-map)#set peer 23.1.1.100
四、測試效果
發一個包觸發一下流量
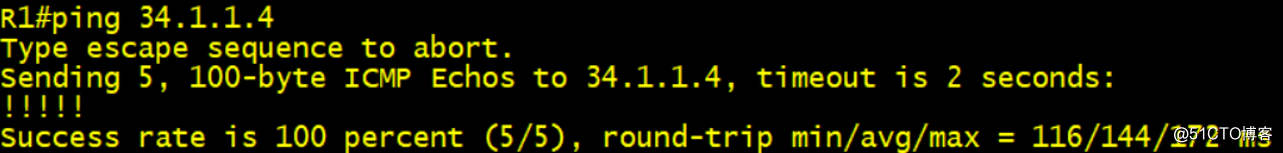
R1#ping 4.4.4.4 so 1.1.1.1 re 1
第一階段的SA協商成功
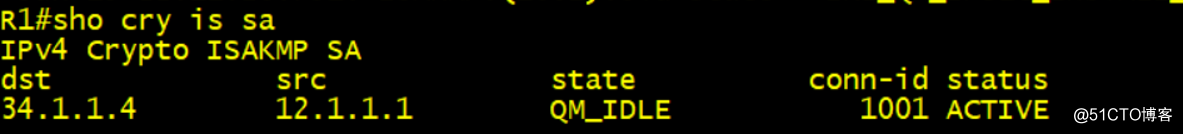
IPSec ×××會話建立成功
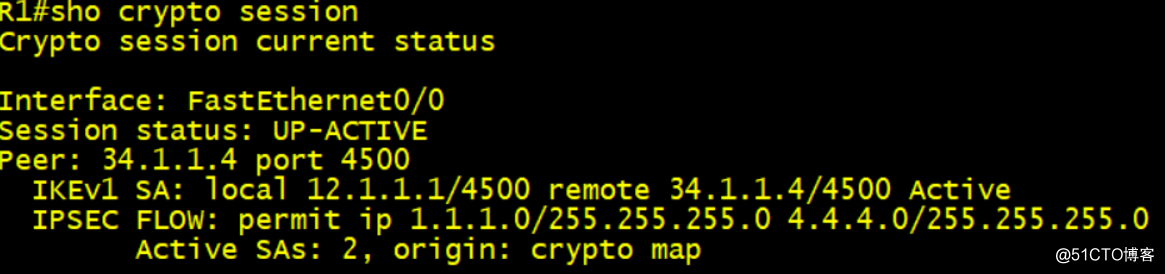
查看show crypto engine connection active
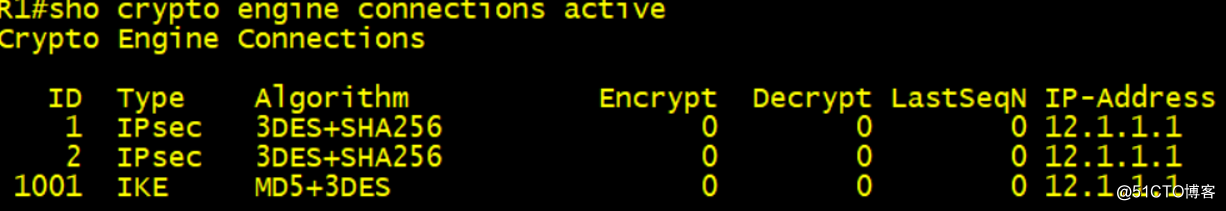
在建立IPSec ×××的過程中,本端會意識到自己是NAT inside,然後以UDP 4500發起IKE報文
*Jun 15 22:22:11.479: ISAKMP (0): received packet from 34.1.1.4 dport 500 sport 500 Global (I) MM_SA_SETUP
*Jun 15 22:22:11.487: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Jun 15 22:22:11.487: ISAKMP:(0):Old State = IKE_I_MM3 New State = IKE_I_MM4
*Jun 15 22:22:11.495: ISAKMP:(0): processing KE payload. message ID = 0
*Jun 15 22:22:11.543: ISAKMP:(0): processing NONCE payload. message ID = 0
*Jun 15 22:22:11.543: ISAKMP:(0):found peer pre-shared key matching 34.1.1.4
*Jun 15 22:22:11.543: ISAKMP:(1002): processing vendor id payload
*Jun 15 22:22:11.543: ISAKMP:(1002): vendor ID is Unity
*Jun 15 22:22:11.547: ISAKMP:(1002): processing vendor id payload
*Jun 15 22:22:11.547: ISAKMP:(1002): vendor ID is DPD
*Jun 15 22:22:11.551: ISAKMP:(1002): processing vendor id payload
*Jun 15 22:22:11.551: ISAKMP:(1002): speaking to another IOS box!
*Jun 15 22:22:11.555: ISAKMP:received payload type 20
*Jun 15 22:22:11.555: ISAKMP (1002): NAT found, both nodes inside NAT
*Jun 15 22:22:11.555: ISAKMP:received payload type 20
*Jun 15 22:22:11.555: ISAKMP (1002): My hash no match - this node inside NAT
*Jun 15 22:22:11.555: ISAKMP:(1002):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Jun 15 22:22:11.555: ISAKMP:(1002):Old State = IKE_I_MM4 New State = IKE_I_MM4
*Jun 15 22:22:11.555: ISAKMP:(1002):Send initial contact
*Jun 15 22:22:11.555: ISAKMP:(1002):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Jun 15 22:22:11.555: ISAKMP (1002): ID payload
next-payload : 8
type : 1
address : 12.1.1.1
protocol : 17
port : 0
length : 12
*Jun 15 22:22:11.555: ISAKMP:(1002):Total payload length: 12
*Jun 15 22:22:11.555: ISAKMP:(1002): sending packet to 34.1.1.4 my_port 4500 peer_port 4500 (I) MM_KEY_EXCH
*Jun 15 22:22:11.555: ISAKMP:(1002):Sending an IKE IPv4 Packet.
*Jun 15 22:22:11.555: ISAKMP:(1002):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Jun 15 22:22:11.559: ISAKMP:(1002):Old State = IKE_I_MM4 New State = IKE_I_MM5
*Jun 15 22:22:11.651: ISAKMP (1002): received packet from 34.1.1.4 dport 4500 sport 4500 Global (I) MM_KEY_EXCH
*Jun 15 22:22:11.655: ISAKMP:(1002): processing ID payload. message ID = 0
*Jun 15 22:22:11.659: ISAKMP (1002): ID payload
next-payload : 8
type
R1# : 1
address : 34.1.1.4
protocol : 17
port : 0
length : 12
*Jun 15 22:22:11.663: ISAKMP:(0):: peer matches *none* of the profiles
*Jun 15 22:22:11.663: ISAKMP:(1002): processing HASH payload. message ID = 0
*Jun 15 22:22:11.667: ISAKMP:(1002):SA authentication status:
authenticated
*Jun 15 22:22:11.667: ISAKMP:(1002):SA has been authenticated with 34.1.1.4
*Jun 15 22:22:11.671: ISAKMP:(1002):Setting UDP ENC peer struct 0x6AF764AC sa= 0x6B08E61C
*Jun 15 22:22:11.671: ISAKMP: Trying to insert a peer 12.1.1.1/34.1.1.4/4500/, and inserted successfully 6B08F0F8.
*Jun 15 22:22:11.675: ISAKMP:(1002):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Jun 15 22:22:11.675: ISAKMP:(1002):Old State = IKE_I_MM5 New State = IKE_I_MM6
*Jun 15 22:22:11.683: ISAKMP:(1002):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Jun 15 22:22:11.683: ISAKMP:(1002):Old State = IKE_I_MM6 New State = IKE_I_MM6
*Jun 15 22:22:11.683: ISAKMP:(1002):Input = IKE_MESG
R1#_INTERNAL, IKE_PROCESS_COMPLETE
*Jun 15 22:22:11.683: ISAKMP:(1002):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
後續就以UDP 4500端口去進行QM了。
實際NAT對IPSec ×××的影響
