深入玩轉K8S之如何訪問業務應用(Traefik-ingress配置https篇)
前面一篇:traefik基礎部署記錄,介紹了最簡單的http訪問traefik,訪問過程參考見下:
client --- (via http) ---> traefik ---- (via http) ----> services
現在要實踐的是更安全也更復雜的https訪問traefik,有兩種訪問過程,參考見下:
後端service是普通http的
即client與traefik間采用https加密通信,但traefik與svc間則是明文的http通信
client --- (via https) ---> traefik ---- (via http) ----> services
後端service是https的
即client與traefik間采用https加密通信,但traefik與svc也是采用https通信
client --- (via https) ---> traefik ---- (via https) ----> services
下面我們來看看如何實現(偽)https,也就是上面說的第二種訪問流程。
首先創建證書,想開啟https,證書是少不了的。可以自己手動建一個證書,或者利用已經有的證書。這裏我自己創建了一個ssl證書,具體創建流程可參考網上。
[root@k8smaster ~]# cd /opt/k8s/ssl [root@k8smaster ssl]# ls ssl.crt ssl.csr ssl.key
上面這個/opt/k8s/ssl目錄是我創建的,路徑可以隨便只要和config文件裏面的路徑一致就行下面會說到。下面開始配置證書
[root@k8smaster ssl]# kubectl create secret generic traefik-cert --from-file=ssl.crt --from-file=ssl.key -n kube-system secret "traefik-cert" created
創建一個configmap,保存traefix的配置。這裏的traefix中配置了把所有http請求全部rewrite為https的規則,並配置相應的證書位置,同時我這裏也創建了一個目錄/opt/k8s/conf/。
[root@k8smaster conf]# cat traefik.toml
defaultEntryPoints = ["http","https"]
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.http.redirect]
entryPoint = "https"
[entryPoints.https]
address = ":443"
[entryPoints.https.tls]
[[entryPoints.https.tls.certificates]]
certFile = "/opt/k8s/ssl/ssl.crt"
keyFile = "/opt/k8s/ssl/ssl.key"
[root@k8smaster config]# kubectl create configmap traefik-conf --from-file=traefik.toml -n kube-system
configmap "traefik-conf" created由於之前配置的是http現在要換成https所以需要更新下Traefik,這裏主要是更新下關聯創建的secret和configMap,並掛載相對應的主機目錄。
安全起見操作之前先備份下(職場好習慣)
[root@k8smaster k8s]# cp traefik-deployment.yaml traefik-deployment.yaml.bk
[root@k8smaster k8s]# cat traefik-deployment.yaml
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: DaemonSet
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
selector:
matchLabels:
k8s-app: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
hostNetwork: true
volumes:
- name: ssl
secret:
secretName: traefik-cert
- name: config
configMap:
name: traefik-conf
containers:
- image: traefik
name: traefik-ingress-lb
volumeMounts:
- mountPath: "/opt/k8s/ssl/"
name: "ssl"
- mountPath: "/opt/k8s/conf/"
name: "config"
ports:
- name: http
containerPort: 80
- name: https
containerPort: 443
- name: admin
containerPort: 8080
args:
- --configFile=/opt/k8s/conf/traefik.toml
- --api
- --kubernetes
- --logLevel=INFO
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 443
name: https
- protocol: TCP
port: 8080
name: admin
type: NodePort
[root@k8smaster k8s]#
[root@k8smaster k8s]# kubectl apply -f traefik-deployment.yaml
serviceaccount "traefik-ingress-controller" created
daemonset.extensions "traefik-ingress-controller" created
service "traefik-ingress-service" created主要變化呢是更新了幾個方面:
kind: DaemonSet 官方默認是使用Deployment
hostNetwork: true 開啟Node Port端口轉發
volumeMounts: 新增volumes掛載點
ports: 新增https443
args: 新增configfile
以及Service層的443 ports
最後我們來測試下是否成功,這裏我們可以登陸traefik-ui界面,可以看到原本http的訪問,traefik會直接給我們重定向至https。
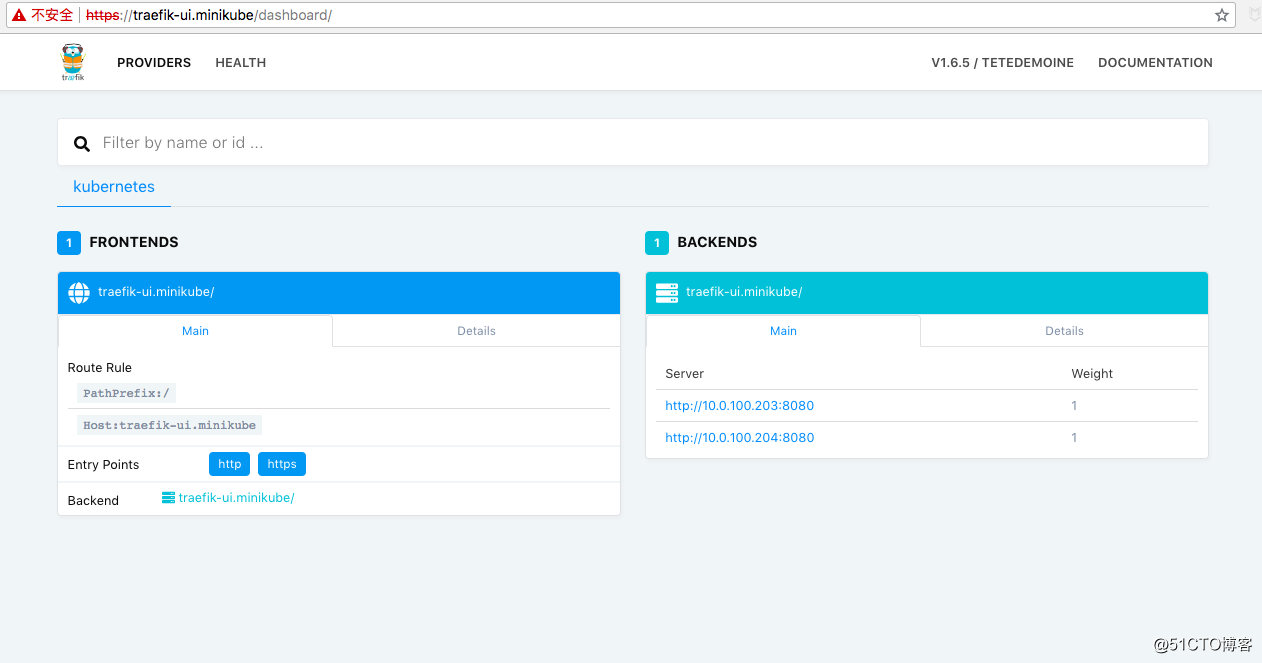
關於第三種https轉發https實現方式這裏就不再贅述了後續如果有需要可以在探討,如果需要的話可以看下am的博客也就是本文參考的資料,寫的很詳細。
本文博客參考資料:
http://blog.51cto.com/goome/2153703
深入玩轉K8S之如何訪問業務應用(Traefik-ingress配置https篇)
