cisco NAT網路地址轉換
NAT(Network Address Translation)網路地址轉換,NAT提供一個連線網際網路簡單的方式,將內部網路使用者的私網地址轉換成外部公網地址,並在NAT地址轉換表中記錄轉換項。當外部網路資料返回時,將根據NAT轉換表項,將目標IP地址替換成初始的內部使用者的IP地址,把資料包轉發給內部網路的連線。
NAT術語:
Inside local: Host on the inside network
轉換之前內部源地址,一般使用的是私有地址
Inside global: Usually assigned by an ISP and allows the customer outside access
轉換之後內部主機的地址。需要申請才取得的IP地址
Outside local :Host on the outside network(多數情況下)
轉換之前目標主機的地址 ,分配給位於外部網路上的主機的IP地址,該地址是從全域性可尋路徑的地址或網路空間中分配的。
Outside global: Host on the outside network
轉換之後目標主機的名字,大多數情況下,外部本地地址等於外部全域性地址。
拓撲:
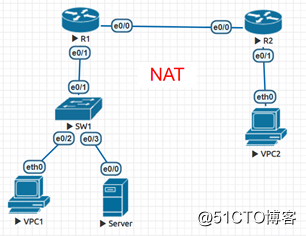
R1:--作為出口閘道器
interface Ethernet0/0
ip address 201.100.98.1 255.255.255.248
interface Ethernet0/1
no ip address
interface Ethernet0/1.10
encapsulation dot1Q 10
ip address 192.168.1.254 255.255.255.0
interface Ethernet0/1.20
encapsulation dot1Q 20
ip address 192.168.2.254 255.255.255.0
R1#show run | s ip route
ip route 0.0.0.0 0.0.0.0 201.100.98.6
R1#
SW1:
Vlan 10
Vlan 20
interface Ethernet0/1
switchport trunk encapsulation dot1q
switchport mode trunk
duplex auto
interface Ethernet0/2
switchport access vlan 10
switchport mode access
duplex auto
spanning-tree portfast
interface Ethernet0/3
switchport access vlan 20
switchport mode access
duplex auto
spanning-tree portfast
R2:---模擬ISP裝置
interface Ethernet0/0
ip address 201.100.98.6 255.255.255.248
interface Ethernet0/1
ip address 172.16.1.254 255.255.255.0
VPC1> ip 192.168.1.1 255.255.255.0 192.168.1.254
Checking for duplicate address...
PC1 : 192.168.1.1 255.255.255.0 gateway 192.168.1.254
VPC2:
Router(config)#host VPC2
VPC2(config)#no ip routing
VPC2(config)#ip default-gateway 172.16.1.254
VPC2(config)#int e0/0
VPC2(config-if)#ip add 172.16.1.1 255.255.255.0
VPC2(config-if)#no shut
Server:
Server(config)#no ip routing
Server(config)#ip default-gateway 192.168.2.254
Server(config)#int e0/0
Server(config-if)#ip add 192.168.2.1 255.255.255.0
Server(config-if)#no shut
靜態NAT:
手動建立一個內部IP地址到一個外部IP地址的對映關係
----該方式經常用於企業網的內部裝置需要能夠被外部網路訪問到的場合
需求:
(1)內網所有PC及伺服器均能訪問外網。
R1:
ip nat inside source static 192.168.1.1 201.100.98.1
ip nat inside source static 192.168.2.1 201.100.98.2
interface Ethernet0/0
ip nat outside
interface Ethernet0/1.10
ip nat inside
interface Ethernet0/1.20
ip nat inside
檢視NAT:
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 201.100.98.1 192.168.1.1 --- ---
--- 201.100.98.2 192.168.2.1 --- ---
R1#
R1#show ip nat statistics
Total active translations: 2 (2 static, 0 dynamic; 0 extended)
Peak translations: 15, occurred 00:29:56 ago
Outside interfaces:
Ethernet0/0
Inside interfaces:
Ethernet0/1.10, Ethernet0/1.20
Hits: 110 Misses: 0
CEF Translated packets: 110, CEF Punted packets: 0
Expired translations: 51
Dynamic mappings:
Total doors: 0
Appl doors: 0
Normal doors: 0
Queued Packets: 0
此時在VPC1 ping VPC2
R1# debug ip nat
R1#
*Oct 27 04:30:30.055: NAT*: s=192.168.1.1->201.100.98.1, d=172.16.1.1 [59878]
*Oct 27 04:30:30.057: NAT*: s=172.16.1.1, d=201.100.98.1->192.168.1.1 [59878]
*Oct 27 04:30:31.058: NAT*: s=192.168.1.1->201.100.98.1, d=172.16.1.1 [59879]
*Oct 27 04:30:31.058: NAT*: s=172.16.1.1, d=201.100.98.1->192.168.1.1 [59879]
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 201.100.98.1:59113 192.168.1.1:59113 172.16.1.1:59113 172.16.1.1:59113
icmp 201.100.98.1:59369 192.168.1.1:59369 172.16.1.1:59369 172.16.1.1:59369
icmp 201.100.98.1:59625 192.168.1.1:59625 172.16.1.1:59625 172.16.1.1:59625
icmp 201.100.98.1:59881 192.168.1.1:59881 172.16.1.1:59881 172.16.1.1:59881
icmp 201.100.98.1:60137 192.168.1.1:60137 172.16.1.1:60137 172.16.1.1:60137
--- 201.100.98.1 192.168.1.1 --- ---
--- 201.100.98.2 192.168.2.1 --- ---
Server 訪問VPC2:
Server#ping 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R1#
*Oct 27 04:31:56.025: NAT*: s=192.168.2.1->201.100.98.2, d=172.16.1.1 [10]
*Oct 27 04:31:56.025: NAT*: s=172.16.1.1, d=201.100.98.2->192.168.2.1 [10]
*Oct 27 04:31:56.026: NAT*: s=192.168.2.1->201.100.98.2, d=172.16.1.1 [11]
*Oct 27 04:31:56.026: NAT*: s=172.16.1.1, d=201.100.98.2->192.168.2.1 [11]
*Oct 27 04:31:56.026: NAT*: s=192.168.2.1->201.100.98.2, d=172.16.1.1 [12]
*Oct 27 04:31:56.027: NAT*: s=172.16.1.1, d=201.100.98.2->192.168.2.1 [12]
*Oct 27 04:31:56.027: NAT*: s=192.168.2.1->201.100.98.2, d=172.16.1.1 [13]
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 201.100.98.1 192.168.1.1 --- ---
icmp 201.100.98.2:2 192.168.2.1:2 172.16.1.1:2 172.16.1.1:2
icmp 201.100.98.2:3 192.168.2.1:3 172.16.1.1:3 172.16.1.1:3
--- 201.100.98.2 192.168.2.1 --- ---
思考:NAT 發生在路由之前還是之後?
處理被處理使用NAT的命令根據資訊包是否去從內部網路外部網路或從外部網路內部網路。內部到外部的轉換髮生在路由之後,外部到內部的轉換髮生在路由之前。
也就是內部到外部,先路由後轉換。外部到內部,先轉換後路由。
(2) 外網使用者能夠通過公網地址 201.100.98.3埠號8080訪問內網伺服器 192.168.2.1 的www服務。
Server(config)#ip http server
R1:
ip nat inside source static tcp 192.168.2.1 80 201.100.98.3 8080
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 201.100.98.1 192.168.1.1 --- ---
tcp 201.100.98.3:8080 192.168.2.1:80 --- ---
--- 201.100.98.2 192.168.2.1 --- ---
VPC2#telnet 201.100.98.3 8080
Trying 201.100.98.3, 8080 ... Open
get
HTTP/1.1 400 Bad Request
Date: Sat, 27 Oct 2018 04:56:23 GMT
Server: cisco-IOS
Accept-Ranges: none
400 Bad Request
[Connection to 201.100.98.3 closed by foreign host]
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 201.100.98.1 192.168.1.1 --- ---
tcp 201.100.98.3:8080 192.168.2.1:80 172.16.1.1:64618 172.16.1.1:64618
tcp 201.100.98.3:8080 192.168.2.1:80 --- ---
--- 201.100.98.2 192.168.2.1 --- ---
動態NAT:
將一個內部IP地址轉換為一組外部IP地址(地址池)中的一個IP地址
----常用於整個公司公用多個公網IP地址訪問Internet時
R1:
access-list 10 permit 192.168.1.0 0.0.0.255
access-list 10 permit 192.168.2.0 0.0.0.255
ip nat pool NAT 201.100.98.1 201.100.98.5 netmask 255.255.255.248
ip nat inside source list 10 pool NAT
R1#show ip nat translations //
Pro Inside global Inside local Outside local Outside global
--- 201.100.98.1 192.168.1.1 --- ---
tcp 201.100.98.3:8080 192.168.2.1:80 --- ---
--- 201.100.98.2 192.168.2.1 --- ---
R1#show ip nat statistics
Total active translations: 1 (1 static, 0 dynamic; 1 extended)
Peak translations: 15, occurred 02:35:19 ago
Outside interfaces:
Ethernet0/0
Inside interfaces:
Ethernet0/1.10, Ethernet0/1.20
Hits: 214 Misses: 0
CEF Translated packets: 214, CEF Punted packets: 0
Expired translations: 61
Dynamic mappings:
-- Inside Source
[Id: 1] access-list 10 pool NAT refcount 0
pool NAT: netmask 255.255.255.248
start 201.100.98.1 end 201.100.98.5
type generic, total addresses 5, allocated 0 (0%), misses 0
Total doors: 0
Appl doors: 0
Normal doors: 0
Queued Packets: 0
R1#
PAT:
動態NAT的一種特殊形式,利用不同埠號將多個內部IP地址轉換為一個外部IP地址,也稱為PAT、NAPT或埠複用NAT
----常用於整個公司公用1個公網IP地址訪問Internet時
複用內部的全域性地址
1.將一個內部全域性地址用於同時代表多個內部區域性地址
2.主要用IP地址和埠號的組合來唯一區分各個內部主機
配置NPAT轉換中,必須使用overload關鍵字,這樣路由器才會將源埠也進行轉換,已達到地址超載的目的。如果不指定overload關鍵字,路由器將執行動態NAT轉換
R1:
access-list 10 permit 192.168.1.0 0.0.0.255
ip nat inside source list 10 interface Ethernet0/0 overload
R1#show ip nat statistics
Total active translations: 1 (1 static, 0 dynamic; 1 extended)
Peak translations: 15, occurred 02:46:09 ago
Outside interfaces:
Ethernet0/0
Inside interfaces:
Ethernet0/1.10, Ethernet0/1.20
Hits: 234 Misses: 0
CEF Translated packets: 234, CEF Punted packets: 0
Expired translations: 67
Dynamic mappings:
-- Inside Source
[Id: 3] access-list 10 interface Ethernet0/0 refcount 0
Total doors: 0
Appl doors: 0
Normal doors: 0
Queued Packets: 0
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 201.100.98.1:13578 192.168.1.1:13578 172.16.1.1:13578 172.16.1.1:13578
icmp 201.100.98.1:13834 192.168.1.1:13834 172.16.1.1:13834 172.16.1.1:13834
icmp 201.100.98.1:14090 192.168.1.1:14090 172.16.1.1:14090 172.16.1.1:14090
icmp 201.100.98.1:14346 192.168.1.1:14346 172.16.1.1:14346 172.16.1.1:14346
icmp 201.100.98.1:14602 192.168.1.1:14602 172.16.1.1:14602 172.16.1.1:14602
tcp 201.100.98.3:8080 192.168.2.1:80 --- ---
R1#show ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
icmp 201.100.98.1:22030 192.168.1.1:22030 172.16.1.1:22030 172.16.1.1:22030
create 00:00:10, use 00:00:10 timeout:60000, left 00:00:49, Map-Id(In): 3,
flags:
extended, use_count: 0, entry-id: 84, lc_entries: 0
icmp 201.100.98.1:22286 192.168.1.1:22286 172.16.1.1:22286 172.16.1.1:22286
create 00:00:09, use 00:00:09 timeout:60000, left 00:00:50, Map-Id(In): 3,
flags:
從上面可以看出ICMP轉換條目的超時時間預設為1分鐘。
