docker 搭建registry
Docke官方提供了Docker Hub網站來作為一個公開的集中倉庫。然而,本地訪問Docker Hub速度往往很慢,並且很多時候我們需要一個本地的私有倉庫只供網內使用。
Docker倉庫實際上提供兩方面的功能,一個是映象管理,一個是認證。前者主要由docker-registry專案來實現,通過http服務來上傳下載;後者可以通過docker-index(閉源)專案或者利用現成認證方案(如nginx)實現http請求管理。
系統環境:CentOS 7.2
主機IP:192.168.116.148
1、安裝docker-registry
?| 1 |
docker run -d -p 5000:5000 --restart=always --name registry -
v
/opt/registry
:
/var/lib/registry
registry:2
|
2、上傳映象
檢視系統已有的映象:
?| 1 2 3 4 |
# docker images
REPOSITORY TAG IMAGE ID CREATED SIZEcentos latest 8140d0c64310 7 days ago 193MB
registry 2 9d0c4eabab4d 8 days ago 33.2MB
|
使用docker tag將centos映象打個標記
?| 1 |
# docker tag centos 192.168.116.148:5000/centos
|
| 1 |
# docker push 192.168.116.148:5000/centos
|

在/etc/docker/目錄下,建立daemon.json檔案。在檔案中寫入:
?| 1 |
{
"insecure-registries"
:[
"192.168.116.148:5000"
] }
|
| 1 |
# systemctl restart docker
|
重新上傳:
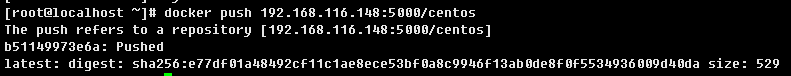
接下來開始配置https
3、配置SSL證書及nginx反向代理docker registry
搭建私有CA,初始化CA環境,在/etc/pki/CA/下建立證書索引資料庫檔案index.txt和序列號檔案serial,併為證書序列號檔案提供初始值。
?| 1 2 |
# touch /etc/pki/CA/{index.txt,serial}
# echo 01 > /etc/pki/CA/serial
|
生成金鑰並儲存到/etc/pki/CA/private/cakey.pem
?| 1 |
# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
|
生成根證書
?| 1 |
# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 3650
|
需要填寫的資訊:
?| 1 2 3 4 5 6 7 |
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:China
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:wts
Organizational Unit Name (eg, section) []:sysops
Common Name (eg, your name or your server's
hostname
) []:hub.wts.com
Email Address []:[email protected]
|
使系統信任根證書
?| 1 |
# cat /etc/pki/CA/cacert.pem >> /etc/pki/tls/certs/ca-bundle.crt
|
| 1 |
# mkdir /app/nginx/conf/ssl
|
建立金鑰檔案和證書申請檔案
?| 1 2 |
# (umask 077;openssl genrsa -out /app/nginx/conf/ssl/docker.key 2048)
# openssl req -new -key /app/nginx/conf/ssl/docker.key -out /app/nginx/conf/ssl/docker.csr
|
填寫的申請資訊前四項要和私有CA的資訊一致
?| 1 2 3 4 5 6 7 8 9 10 11 12 |
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:China
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:wts
Organizational Unit Name (eg, section) []:sysops
Common Name (eg, your name or your server's
hostname
) []:hub.wts.com
Email Address []:[email protected]
Please enter the following
'extra'
attributes
to be sent with your certificate request
A challenge password []:
#直接回車
An optional company name []:
#直接回車
|
簽署,證書
?| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
# openssl ca -in /app/nginx/conf/ssl/docker.csr -out /app/nginx/conf/ssl/docker.crt -days 3650
Using configuration from
/etc/pki/tls/openssl
.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: May 19 19:03:55 2017 GMT
Not After : May 17 19:03:55 2027 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = wts
organizationalUnitName = sysops
commonName = hub.wts.com
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
69:F0:D7:BF:B2:CE:6D:53:AA:1A:CD:E8:73:47:A7:9F:30:EA:17:F7
X509v3 Authority Key Identifier:
keyid:AF:E5:48:44:A3:18:59:38:D5:17:07:1B:1D:6F:32:F4:EC:1E:E0:E2
Certificate is to be certified
until
May 17 19:03:55 2027 GMT (3650 days)
Sign the certificate? [y
/n
]:y
1 out of 1 certificate requests certified, commit? [y
/n
]y
Write out database with 1 new entries
Data Base Updated
|
配置nginx反向代理docker registry
新增認證
?| 1 2 |
# yum -y install httpd-tools
# htpasswd -cb /app/nginx/conf/docker-registry.htpasswd admin admin
|
nginx相關配置:
?| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
upstream docker-registry {
server 127.0.0.1:5000;
}
server {
listen 443;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
ssl on;
ssl_certificate
/app/nginx/conf/ssl/docker
.crt;
ssl_certificate_key
/app/nginx/conf/ssl/docker
.key;
client_max_body_size 0;
chunked_transfer_encoding on;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
add_header
'Docker-Distribution-Api-Version'
'registry/2.0'
always;
location / {
auth_basic
"Docker registry"
;
auth_basic_user_file
/app/nginx/conf/docker-registry
.htpasswd;
proxy_pass http:
//docker-registry
;
}
location
/_ping
{
auth_basic off;
proxy_pass http:
//docker-registry
;
}
location
/v2/_ping
{
auth_basic off;
proxy_pass http:
//docker-registry
;
}
}
|
重啟nginx
?| 1 |
# /app/nginx/sbin/nginx -s reload
|
| 1 2 3 |
# cat >>/etc/hosts <<EOF
192.168.116.148 hub.wts.com
EOF
|
| 1 2 |
# systemctl daemon-reload
# systemctl restart docker
|
登入
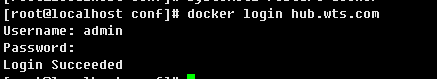
上傳映象
?| 1 2 3 |
# docker pull nginx
# docker tag nginx 192.168.116.148:5000/nginx
# docker push 192.168.116.148:5000/nginx
|
檢視
?| 1 2 |
# curl --user admin:admin https://hub.wts.com/v2/_catalog
{
"repositories"
:[
"centos"
,
"nginx"
]}
|
區域網內其他機器認證(192.168.116.147 系統版本:CentOS6.5)
修改hosts檔案 ?| 1 2 3 |
# cat >>/etc/hosts <<EOF
192.168.116.148 hub.wts.com
EOF
|
把CA的金鑰傳送到客戶機,並新增到ca-bundle.crt
?| 1 2 3 |
# scp -p /etc/pki/tls/certs/ca-bundle.crt [email protected]:/etc/pki/tls/certs/ca-bundle.crt
# scp -p /etc/pki/CA/cacert.pem [email protected]:/etc/pki/CA/cacert.pem
# cat /etc/pki/CA/cacert.pem >> /etc/pki/tls/certs/ca-bundle.crt
|
| 1 |
# /etc/init.d/docker restart
|
登入

下載映象
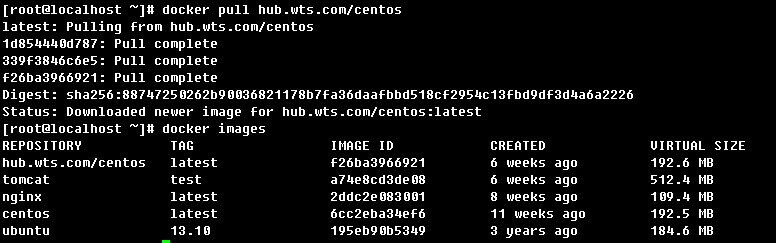
至此,私服基本上可以使用了。
轉載:http://www.cnblogs.com/Eivll0m/p/7089675.html
Docke官方提供了Docker Hub網站來作為一個公開的集中倉庫。然而,本地訪問Docker Hub速度往往很慢,並且很多時候我們需要一個本地的私有倉庫只供網內使用。
Docker倉庫實際上提供兩方面的功能,一個是映象管理,一個是認證。前者主要由docker-registry專案來實現,通過http服務來上傳下載;後者可以通過docker-index(閉源)專案或者利用現成認證方案(如nginx)實現http請求管理。
系統環境:CentOS 7.2
主機IP:192.168.116.148
1、安裝docker-registry
?| 1 |
docker run -d -p 5000:5000 --restart=always --name registry -
v
/opt/registry
:
/var/lib/registry
registry:2
|
2、上傳映象
檢視系統已有的映象:
?| 1 2 3 4 |
# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
centos latest 8140d0c64310 7 days ago 193MB
registry 2 9d0c4eabab4d 8 days ago 33.2MB
|
使用docker tag將centos映象打個標記
?| 1 |
# docker tag centos 192.168.116.148:5000/centos
|
| 1 |
# docker push 192.168.116.148:5000/centos
|

在/etc/docker/目錄下,建立daemon.json檔案。在檔案中寫入:
?| 1 |
{
"insecure-registries"
:[
"192.168.116.148:5000"
] }
|
| 1 |
# systemctl restart docker
|
重新上傳:

接下來開始配置https
3、配置SSL證書及nginx反向代理docker registry
搭建私有CA,初始化CA環境,在/etc/pki/CA/下建立證書索引資料庫檔案index.txt和序列號檔案serial,併為證書序列號檔案提供初始值。
?| 1 2 |
# touch /etc/pki/CA/{index.txt,serial}
# echo 01 > /etc/pki/CA/serial
|
生成金鑰並儲存到/etc/pki/CA/private/cakey.pem
?| 1 |
# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
|
生成根證書
?| 1 |
# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 3650
|
需要填寫的資訊:
?| 1 2 3 4 5 6 7 |
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:China
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:wts
Organizational Unit Name (eg, section) []:sysops
Common Name (eg, your name or your server's
hostname
) []:hub.wts.com
Email Address []:[email protected]
|
使系統信任根證書
?| 1 |
# cat /etc/pki/CA/cacert.pem >> /etc/pki/tls/certs/ca-bundle.crt
|
