華為HCNA技術應用
一、設計目的
利用華為HCNA網路技術設計經典網路例項,模擬實現日常生活中小型網路的基本需求。
二、設計原理
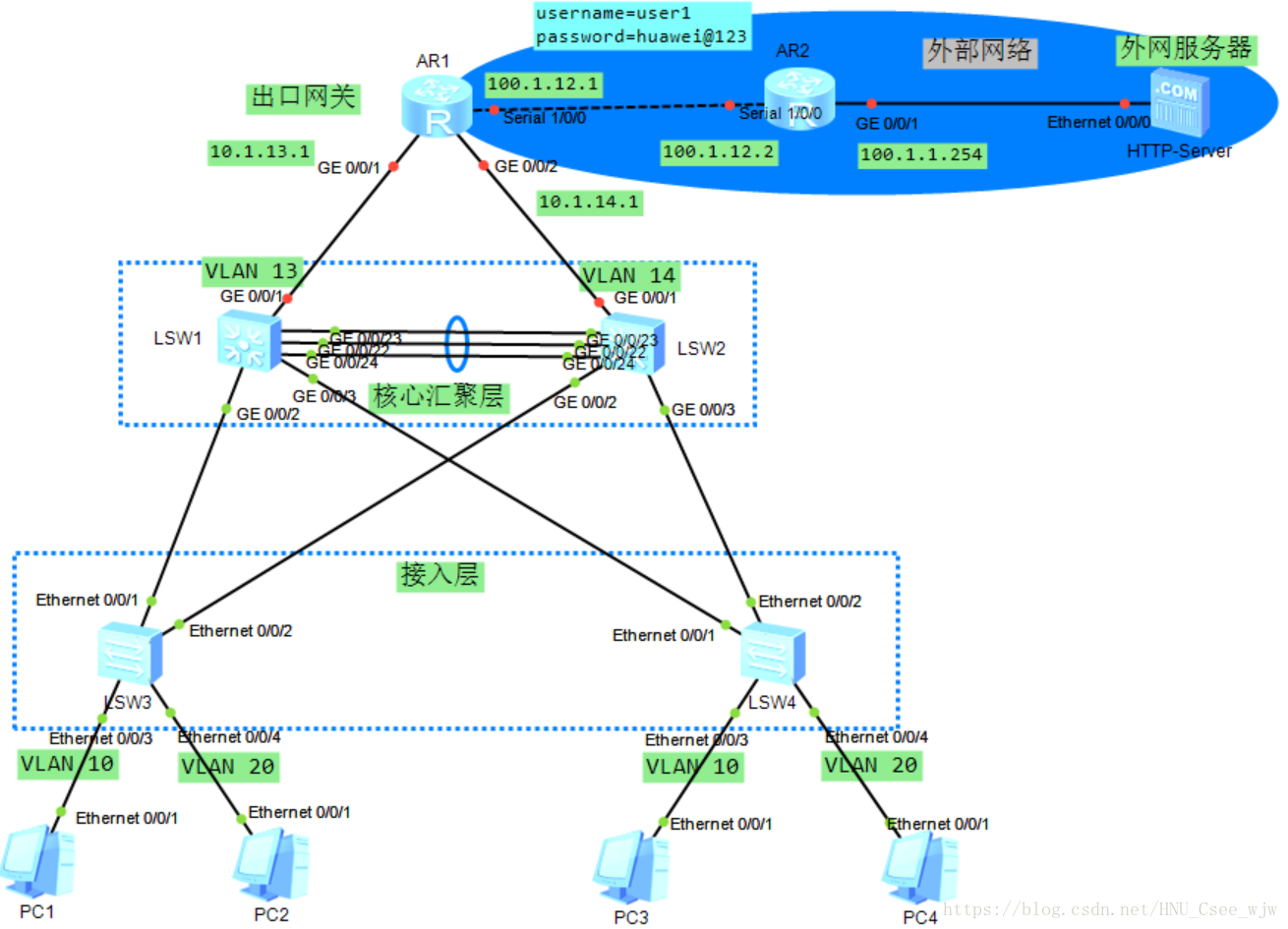
- 實驗拓撲圖
三、設計要求
1.鏈路聚合
2.VLAN
3.STP
4.IP地址規劃
根據表格為裝置配置IP地址以及閘道器。
|
裝置/埠 |
IP地址 |
閘道器 |
|
PC1 |
自動獲取 |
|
|
PC2 |
自動獲取 |
|
|
PC3 |
自動獲取 |
|
|
PC4 |
自動獲取 | |
|
HTTP-Server |
100.1.1.1/24 |
|
|
SW1-VLANIF 10 |
10.1.10.254/24 |
|
|
SW1-VLANIF 20 |
10.1.20.254/24 |
|
|
SW1-VLANIF 13 |
10.1.13.3/24 |
|
|
SW2-VLANIF 14 |
10.1.14.4/24 |
|
|
AR1-G0/0/0 |
100.1.12.1/24 |
|
|
AR1-G0/0/1 |
10.1.13.1/24 |
|
|
AR1-G0/0/2 |
10.1.14.1/24 |
|
|
AR2-G0/0/0 |
100.1.12.2/24 |
|
|
AR2-G0/0/1 |
100.1.1.254/24 |
注:所有VLAN內主機的閘道器都在SW1上。
5.PPP認證
6.DHCP服務
7.配置RIP協議
8.NAT技術
9.裝置登陸控制
10.流量控制
四、設計步驟
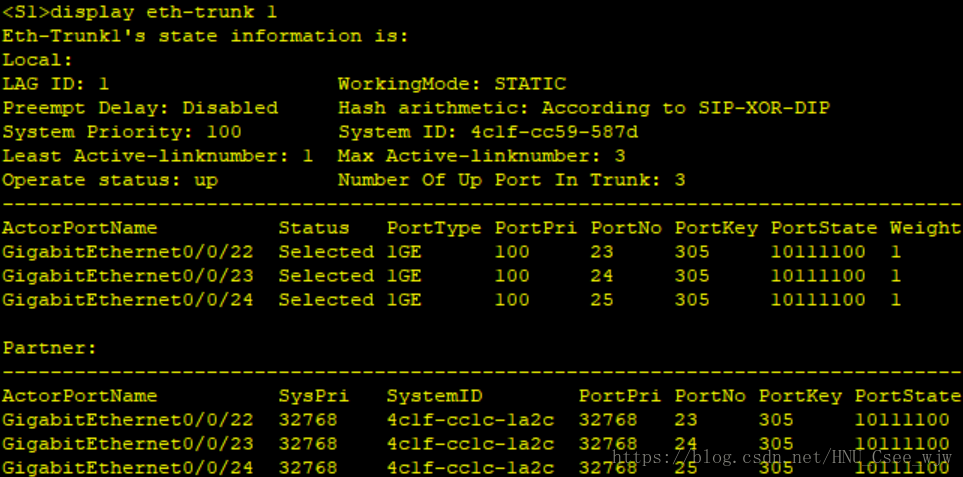
1.鏈路聚合
(1)SW1和SW2之間配置三條鏈路的LACP模式的鏈路聚合,其中SW1為主動端,SW2為被動端
//配置二層Eth-Trunk介面
[S1]interface Eth-Trunk 1
[S2]interface Eth-Trunk 1
//配置鏈路聚合模式為LACP模式
LACP模式下,需手工建立Eth-Trunk,手工加入Eth-Trunk成員介面,但活動介面的選擇是由LACP協商確定的,配置相對靈活。
[S1-Eth-Trunk1]mode lacp
[S2-Eth-Trunk1]mode lacp
//將成員介面加入聚合組
[S1-Eth-Trunk1]trunkport GigabitEthernet 0/0/22 to 0/0/24
[S2-Eth-Trunk1]trunkport GigabitEthernet 0/0/22 to 0/0/24
//在S1上配置優先順序為100,使其成為LACP主動端
[S1]lacp priority 100
(2)LACP的最大活躍鏈路為3條
//在S1,S2上配置活動介面上限閾值為3
[S1]interface Eth-Trunk 1
[S1-Eth-Trunk1]max active-linknumber 3
[S2-Eth-Trunk1]max active-linknumber 3
//在S1上配置介面優先順序確定活動鏈路
[S1-GigabitEthernet0/0/22]lacp priority 100
[S1-GigabitEthernet0/0/23]lacp priority 100
[S1-GigabitEthernet0/0/24]lacp priority 100
檢視鏈路聚合配置結果:
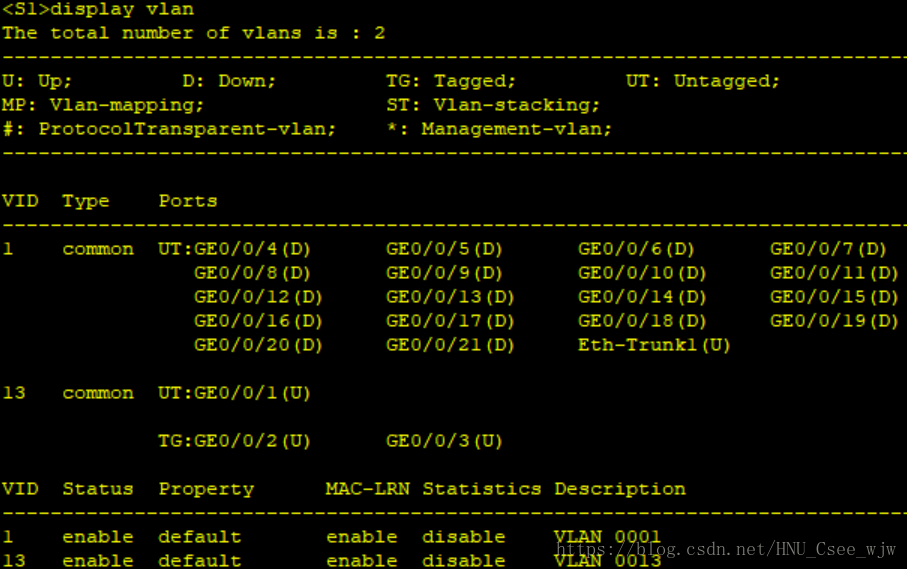
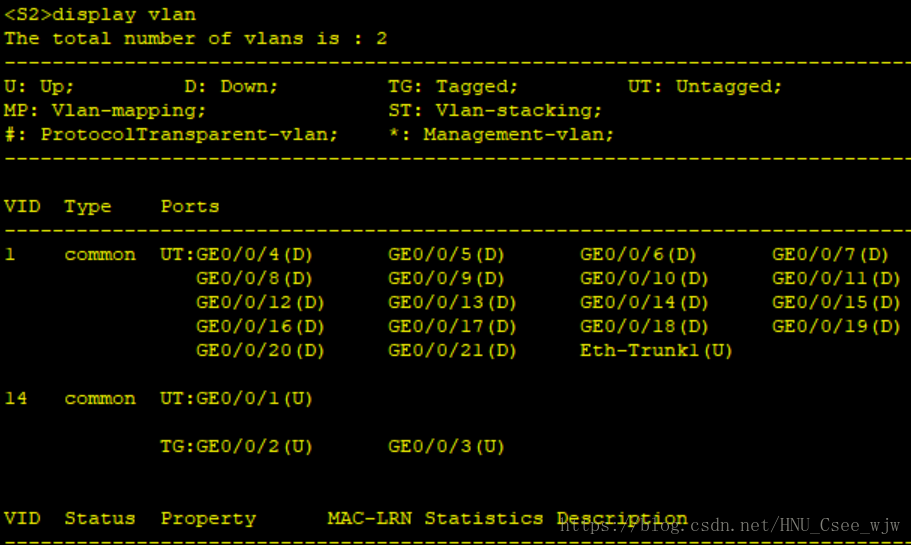
2.VLAN
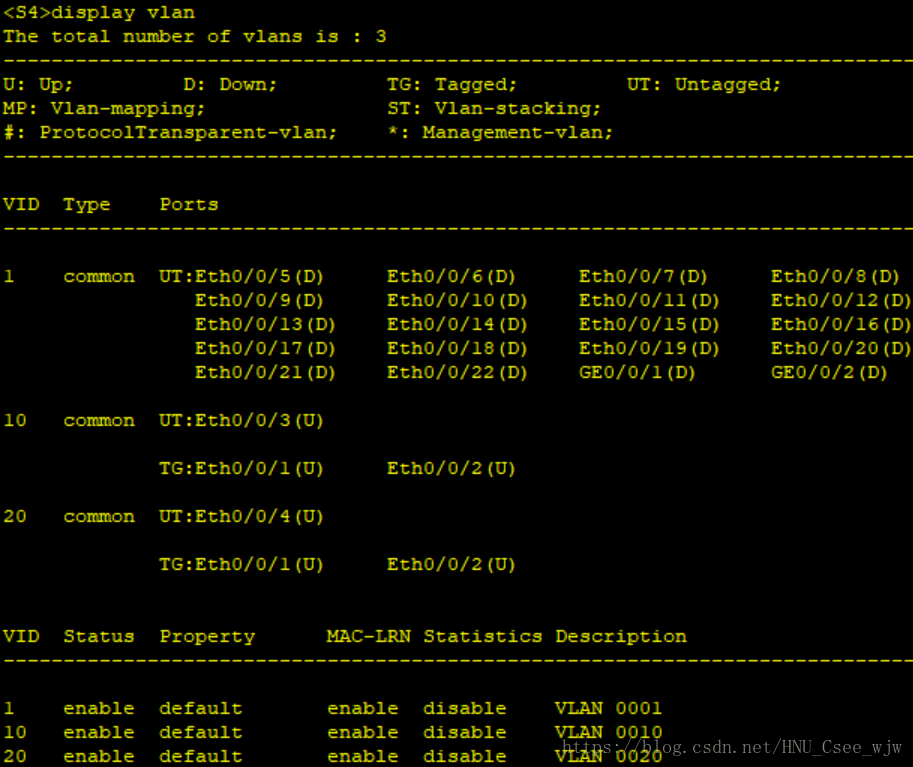
(1)按照拓撲要求將交換機連線PC和路由器的埠劃分進相應VLAN。
//在S3上,將埠E0/0/3和E0/0/4分別加入到VLAN 10和VLAN 20。
[S3-Ethernet0/0/3]port link-type access
[S3-Ethernet0/0/4]port link-type access
[S3]vlan 10
[S3]vlan 20
[S3-vlan10]port Ethernet 0/0/3
[S3-vlan20]port Ethernet 0/0/4
//在S4上,將埠E0/0/3和E0/0/4分別加入VLAN 10和VLAN 20。
[S4-Ethernet0/0/3]port link-type access
[S4-Ethernet0/0/4]port link-type access
[S4-vlan10]port Ethernet 0/0/3
[S4-vlan20]port Ethernet 0/0/4
//在S1上,將埠G0/0/1加入VLAN 13。
[S1-GigabitEthernet0/0/1]port link-type access
[S1-vlan13]port GigabitEthernet 0/0/1
//在S2上,將埠G0/0/1加入VLAN 14。
[S2-GigabitEthernet0/0/1]port link-type access
[S2-vlan14]port GigabitEthernet 0/0/1
(2)交換機之間互聯埠配置為TRUNK埠並允許除VLAN 1以外其他所有VLAN通過。
[S1-GigabitEthernet0/0/2]port link-type trunk
[S1-GigabitEthernet0/0/2]port trunk allow-pass vlan all
[S1-GigabitEthernet0/0/2]undo port trunk allow-pass vlan 1
[S1-GigabitEthernet0/0/2]int g0/0/3
[S1-GigabitEthernet0/0/3]port link-type trunk
[S1-GigabitEthernet0/0/3]port trunk allow-pass vlan all
[S1-GigabitEthernet0/0/3]undo port trunk allow-pass vlan 1
[S2-GigabitEthernet0/0/2]port link-type trunk
[S2-GigabitEthernet0/0/2]port trunk allow-pass vlan all
[S2-GigabitEthernet0/0/2]undo port trunk allow-pass vlan 1
[S2-GigabitEthernet0/0/2]int g0/0/3
[S2-GigabitEthernet0/0/3]port link-type trunk
[S2-GigabitEthernet0/0/3]port trunk allow-pass vlan all
[S2-GigabitEthernet0/0/3]undo port trunk allow-pass vlan 1
[S3-Ethernet0/0/1]port link-type trunk
[S3-Ethernet0/0/1]port trunk allow-pass vlan all
[S3-Ethernet0/0/1]undo port trunk allow-pass vlan 1
[S3-Ethernet0/0/1]int e0/0/2
[S3-Ethernet0/0/2]port link-type trunk
[S3-Ethernet0/0/2]port trunk allow-pass vlan all
[S3-Ethernet0/0/2]undo port trunk allow-pass vlan 1
[S4]int e0/0/1
[S4-Ethernet0/0/1]port link-type trunk
[S4-Ethernet0/0/1]port trunk allow-pass vlan all
[S4-Ethernet0/0/1]undo port trunk allow-pass vlan 1
[S4-Ethernet0/0/1]int e0/0/2
[S4-Ethernet0/0/2]port link-type trunk
[S4-Ethernet0/0/2]port trunk allow-pass vlan all
[S4-Ethernet0/0/2]undo port trunk allow-pass vlan 1
檢視VLAN配置結果:
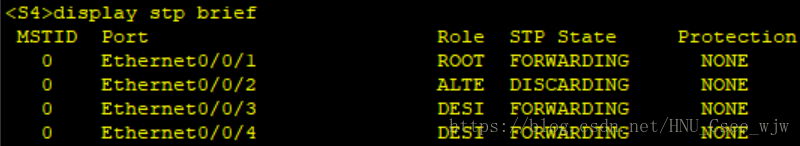
3.STP
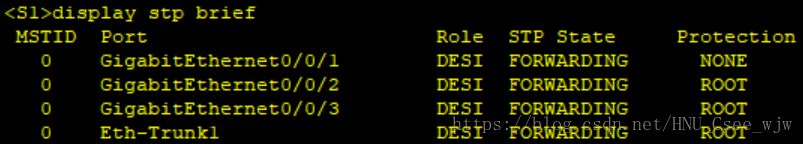
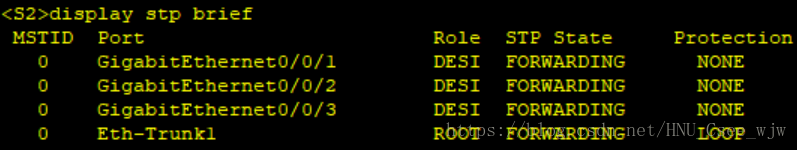
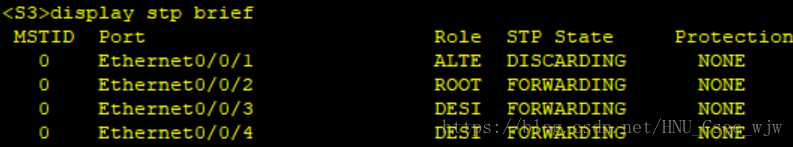
(1)所有交換機執行RSTP。
[S1]stp mode rstp
[S2]stp mode rstp
[S3]stp mode rstp
[S4]stp mode rstp
(2)指定SW1為根橋,SW2為備份根橋。
//配置根橋和備份根橋裝置
[S1]stp root primary
[S2]stp root secondary
//全域性使能RSTP
[S1]stp enable
[S2]stp enable
[S3]stp enable
[S4]stp enable
(3)交換機連線PC的埠配置為邊緣埠,並在開啟邊緣埠的交換機開啟BPDU保護
//S3,S4連線PC的埠配置為邊緣埠,並開啟BPDU保護
[S3]int e0/0/3
[S3-Ethernet0/0/3]stp edged-port enable
[S3-Ethernet0/0/3]stp bpdu-filter enable
[S3-Ethernet0/0/3]int e0/0/4
[S3-Ethernet0/0/4]stp edged-port enable
[S3-Ethernet0/0/4]stp bpdu-filter enable
[S4]int e0/0/3
[S4-Ethernet0/0/3]stp edged-port enable
[S4-Ethernet0/0/3]stp bpdu-filter enable
[S4-Ethernet0/0/3]int e0/0/4
[S4-Ethernet0/0/4]stp edged-port enable
[S4-Ethernet0/0/4]stp bpdu-filter enable
(4)在根橋的DP埠開啟根保護功能。
//在根橋的DP埠開啟根保護功能
[S1]int g0/0/2
[S1-GigabitEthernet0/0/2]stp root-protection
[S1-GigabitEthernet0/0/2]int g0/0/3
[S1-GigabitEthernet0/0/3]stp root-protection
[S1]int Eth-Trunk 1
[S1-Eth-Trunk1]stp root-protection
(5)在SW2的RP埠開啟環路保護功能
//在SW2的RP埠開啟環路保護功能
[S2]int Eth-Trunk 1
[S2-Eth-Trunk1]stp loop-protection
檢視STP配置結果:
4.IP地址規劃
|
裝置/埠 |
IP地址 |
裝置/埠 |
IP地址 |
|
PC1 |
自動獲取 |
SW1-VLANIF 13 |
10.1.13.3/24 |
|
PC2 |
自動獲取 |
SW2-VLANIF 14 |
10.1.14.4/24 |
|
PC3 |
自動獲取 |
AR1-S1/0/0 |
100.1.12.1/24 |
|
PC4 |
自動獲取 |
AR1-G0/0/1 |
10.1.13.1/24 |
|
HTTP-Server |
100.1.1.1/24 |
AR1-G0/0/2 |
10.1.14.1/24 |
|
SW1-VLANIF 10 |
10.1.10.254/24 |
AR2-S1/0/0 |
100.1.12.2/24 |
|
SW1-VLANIF 20 |
10.1.20.254/24 |
AR2-G0/0/1 |
100.1.1.254/24 |
[S1]vlan 10
[S1-vlan10]vlan 20
[S1-vlan20]vlan 14
[S1-Vlanif10]ip add 10.1.10.254 24
[S1-Vlanif20]ip add 10.1.20.254 24
[S1-Vlanif13]ip add 10.1.13.3 24
[S1-Vlanif14]ip add 10.1.14.4 24
[R1]int s1/0/0
[R1-Serial1/0/0]ip add 100.1.12.1 24
[R1-Serial1/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 10.1.13.1 24
[R1-GigabitEthernet0/0/1]int g0/0/2
[R1-GigabitEthernet0/0/2]ip add 10.1.14.1 24
[R2]int s1/0/0
[R2-Serial1/0/0]ip add 100.1.12.2 24
[R2-Serial1/0/0]int g0/0/1
[R2-GigabitEthernet0/0/1]ip add 100.1.1.254 24
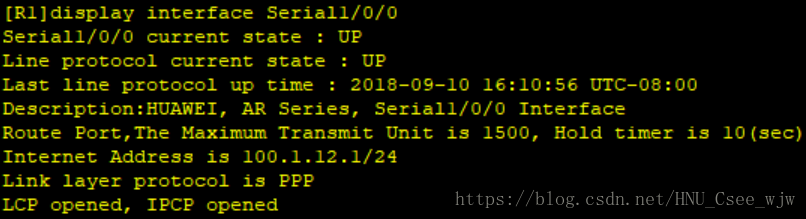
5.PPP
配置R1和R2之間PPP的CHAP認證,R1為認證方,R2為被認證方,認證使用者名稱為user1,密碼為[email protected]。
[R1]aaa
[R1-aaa]local-user user1 password cipher [email protected]
Info: Add a new user.
[R1-aaa]local-user user1 service-type ppp
[R1-aaa]int s1/0/0
[R1-Serial1/0/0]link-protocol ppp
[R1-Serial1/0/0]ppp authentication-mode chap
[R2]int s1/0/0
[R2-Serial1/0/0]link-protocol ppp
[R2-Serial1/0/0]ppp chap user user1
[R2-Serial1/0/0]ppp chap password cipher [email protected]
檢視PPP配置結果:
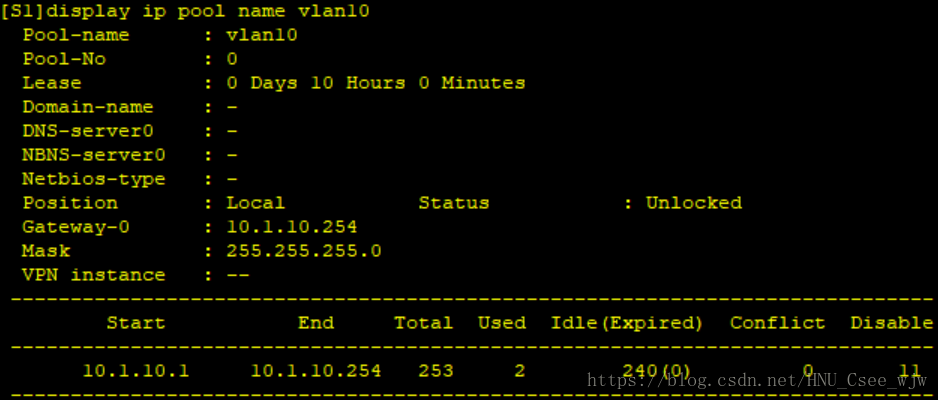
6.DHCP
(1)在SW1上部署DHCP伺服器,使用全域性地址池,為VLAN 10和VLAN 20分配IP地址
//在S1上部署DHCP伺服器,使用全域性地址池
[S1]dhcp enable
[S1]ip pool vlan10 //建立一個全域性地址池名為vlan10
[S1]ip pool vlan20 //建立一個全域性地址池名為vlan20
(2)VLAN 10分配網段為10.1.10.0/24,VLAN 20分配10.1.20.0/24網段
[S1-ip-pool-vlan10]network 10.1.10.0 mask 255.255.255.0
[S1-ip-pool-vlan20]net 10.1.20.0 mask 255.255.255.0
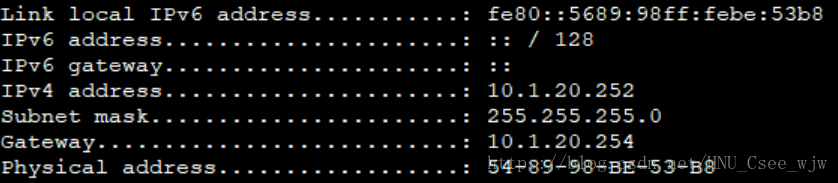
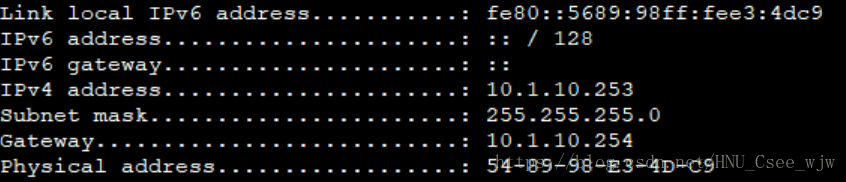
(3)指定VLAN 10獲取閘道器為10.1.10.254,VLAN 20獲取閘道器為10.1.20.254
[S1-ip-pool-vlan10]gateway-list 10.1.10.254
[S1-ip-pool-vlan20]gateway-list 10.1.20.254
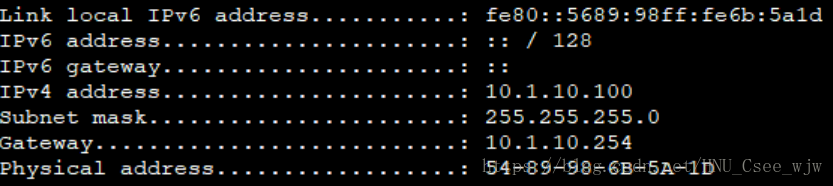
(4)指定PC1獲得10.1.10.100的IP地址
//檢視PC1的MAC地址為
static-bind ip-address 10.1.10.100 mac-address 5489-986B-5A1D
(5)地址分配租期為10 h
[S1-ip-pool-vlan10]lease day 0 hour 10
[S1-ip-pool-vlan20]lease day 0 hour 10
(6)保留10.1.10.200~10.1.10.210地址不能分配
[S1-ip-pool-vlan10]excluded-ip-address 10.1.10.200 10.1.10.210
[S1-Vlanif10]dhcp select global
[S1-Vlanif20]dhcp select global
檢視DHCP配置結果:
PC1
PC2
PC3
PC4
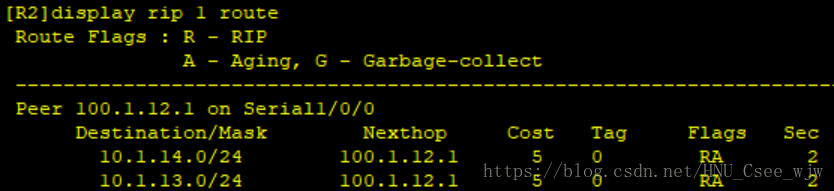
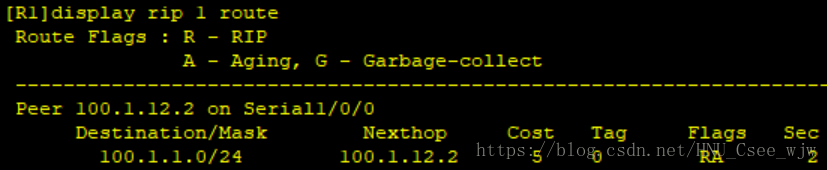
7.RIP
(1)在R1和R2之間互聯公網網段執行RIPv2,通告兩臺裝置直連網段
[R1]rip
[R1-rip-1]network 100.0.0.0
[R1-rip-1]network 10.0.0.0
[R1-rip-1]version 2
[R2]rip
[R2-rip-1]network 100.1.0.0
[R2-rip-1]version 2
(2)在R1上將連結SW1和SW2的埠配置為靜默埠
[R1]rip 1
[R1-rip-1]silent-interface GigabitEthernet 0/0/1
[R1-rip-1]silent-interface GigabitEthernet 0/0/2
(3)將R1和R2之間開銷值配置為5跳。(注意來回一致)
[R1-Serial1/0/0]rip metricout 5
[R2-Serial1/0/0]rip metricout 5
檢視RIP配置結果:
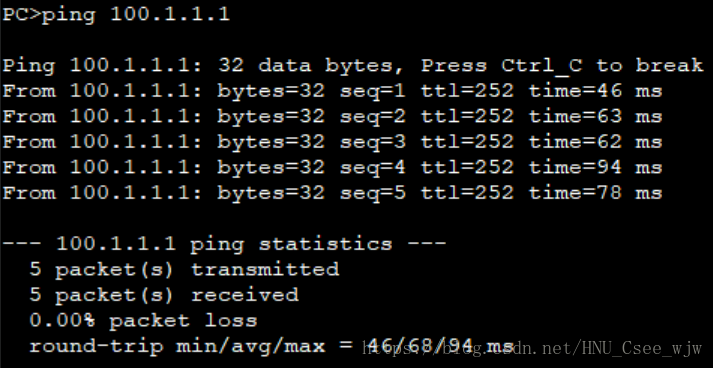
8.NAT
(1)在R1上部署地址池NAPT技術,使得內網只有10.1.10.0/24和10.1.20.0/24網段可以通過地址池訪問外網伺服器
(2)地址池範圍為100.1.2.1~100.1.2.10
//在R1上配置NAT Outbound
[R1]nat address-group 1 100.1.2.1 100.1.2.10
[R1]acl 2000
[R1-acl-basic-2000]rule 5 permit source 10.1.10.0 0.0.0.255
[R1-acl-basic-2000]rule 10 permit source 10.1.20.0 0.0.0.255
[R1-Serial1/0/0]nat outbound 2000 address-group 1
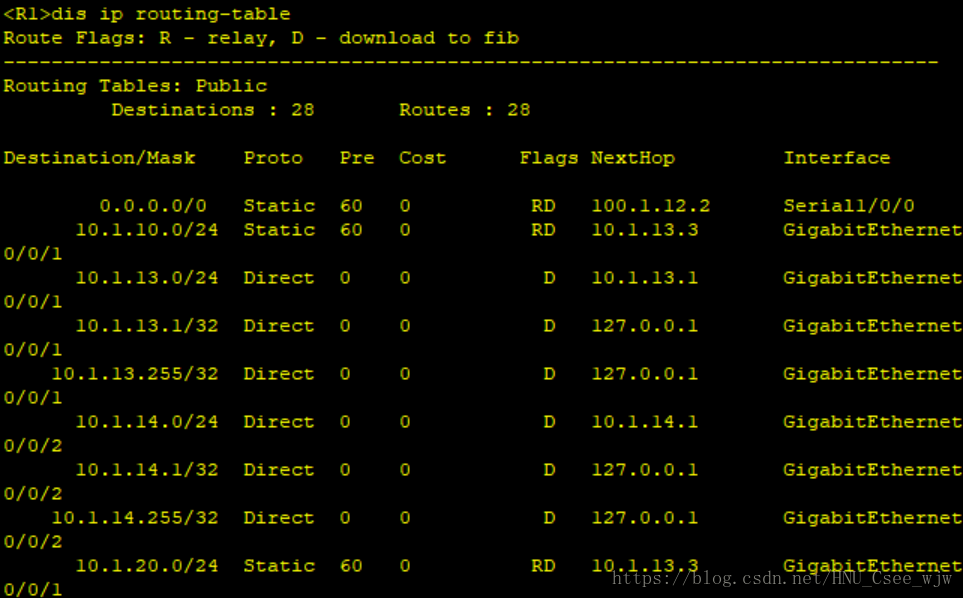
(3)在SW1,SW2,R1合理配置靜態路由使得內網可以通過NAT訪問外網
[S1]ip route-static 100.1.1.0 24 10.1.13.1
[S1]ip route-static 100.1.12.0 24 10.1.13.1
[S2]ip route-static 100.1.1.0 24 10.1.14.1
[S2]ip route-static 100.1.12.0 24 10.1.14.1
[R1]ip route-static 10.1.10.0 24 10.1.13.3
[R1]ip route-static 10.1.20.0 24 10.1.13.3
[R2]ip route-static 100.1.2.0 24 100.1.12.1
檢視NAT配置結果:
內網可以ping通外網
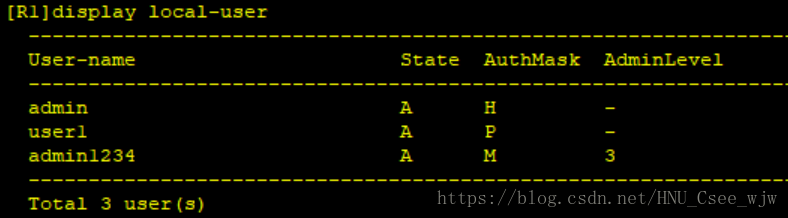
9.裝置登入控制
(1)配置R1可以通過密碼[email protected]進行Console登陸
[R1]user-interface console 0
[R1-ui-console0]authentication-mode aaa
[R1-ui-console0]user privilege level 15
[R1]aaa
[R1-aaa]local-user admin1234 password cipher [email protected]
Info: Add a new user.
[R1-aaa]local-user admin1234 privilege level 3
[R1-aaa]local-user admin1234 service-type terminal
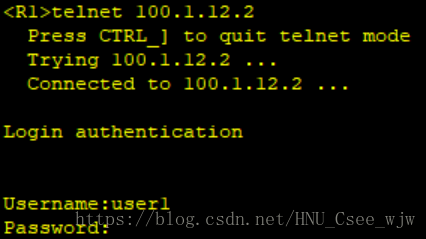
(2)配置R2可以通過使用者名稱user1以及密碼[email protected]進行Telnet登陸,使用者登陸後的許可權為3級許可權。配置完成後可以在R1上進行Telnet測試
[R2]aaa
[R2-aaa]local-user user1 password cipher [email protected] privilege level 3
[R2-aaa]local-user user1 service-type telnet
[R2]user-interface vty 0 4
[R2-ui-vty0-4]authentication-mode aaa
檢視登入控制配置結果:
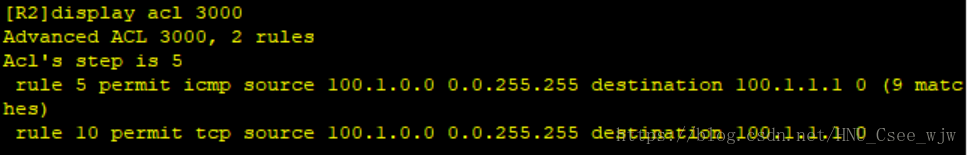
10.流量控制
在R2的G0/0/1介面通過配置流量控制,只允許內網使用者通過NAT訪問HTTP-Server的HTTP流量和ICMP流量,其他流量不能通過該介面。
[R2]acl 3000
[R2-acl-adv-3000]rule 5 permit icmp source 100.1.0.0 0.0.255.255 destination 100.1.1.1 0.0.0.0
[R2-acl-adv-3000]rule 10 permit tcp source 100.1.0.0 0.0.255.255 destination 100.1.1.1 0.0.0.0
[R2-GigabitEthernet0/0/1]traffic-filter outbound acl 3000
檢視流量控制配置結果:
五、配置
AR1:
<R1>display current-configuration
[V200R003C00]
#
sysname R1
#
board add 0/1 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 10.1.10.0 0.0.0.255
rule 10 permit source 10.1.20.0 0.0.0.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
local-user user1 password cipher %$%$u,nJS!4!kMJ1r^+FO-:J+lQn%$%$
local-user user1 service-type ppp
local-user admin1234 password cipher %$%$3gpcV_DG'Fa>t}0~oFZG/{C"%$%$
local-user admin1234 privilege level 3
local-user admin1234 service-type terminal
#
firewall zone Local
priority 15
#
nat address-group 1 100.1.2.1 100.1.2.10
#
interface Serial1/0/0
link-protocol ppp
ppp authentication-mode chap
ip address 100.1.12.1 255.255.255.0
rip metricout 5
nat outbound 2000 address-group 1
#
interface Serial1/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
ip address 10.1.13.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.1.14.1 255.255.255.0
#
interface NULL0
#
rip 1
version 2
network 100.0.0.0
network 10.0.0.0
silent-interface GigabitEthernet0/0/1
silent-interface GigabitEthernet0/0/2
#
ip route-static 0.0.0.0 0.0.0.0 100.1.12.2
ip route-static 10.1.10.0 255.255.255.0 10.1.13.3
ip route-static 10.1.20.0 255.255.255.0 10.1.13.3
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
AR2:
<R2>display current-configuration
[V200R003C00]
#
sysname R2
#
board add 0/1 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
acl number 3000
rule 5 permit icmp source 100.1.0.0 0.0.255.255 destination 100.1.1.1 0
rule 10 permit tcp source 100.1.0.0 0.0.255.255 destination 100.1.1.1 0
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
local-user user1 password cipher %$%$fFf3J'f)SJ+wwuP3(uTW/5U#%$%$
local-user user1 privilege level 3
local-user user1 service-type telnet
#
firewall zone Local
priority 15
#
interface Serial1/0/0
link-protocol ppp
ppp chap user user1
ppp chap password cipher %$%[email protected]&>4l:a`N%TV[:,"q,%$%$
ip address 100.1.12.2 255.255.255.0
rip metricout 5
#
interface Serial1/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
ip address 100.1.1.254 255.255.255.0
traffic-filter outbound acl 3000
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
rip 1
version 2
network 100.0.0.0
#
ip route-static 100.1.1.0 255.255.255.0 100.1.1.1
ip route-static 100.1.2.0 255.255.255.0 100.1.12.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
authentication-mode aaa
user privilege level 3
user-interface vty 16 20
#
wlan ac
#
return
<R2>
LSW1:
<S1>display current-configuration
#
sysname S1
#
vlan batch 10 13 to 14 20
#
stp mode rstp
stp instance 0 root primary
#
lacp priority 100
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
dhcp enable
#
diffserv domain default
#
drop-profile default
#
ip pool vlan10
gateway-list 10.1.10.254
network 10.1.10.0 mask 255.255.255.0
static-bind ip-address 10.1.10.100 mac-address 5489-986b-5a1d
excluded-ip-address 10.1.10.200 10.1.10.210
lease day 0 hour 10 minute 0
#
ip pool vlan20
gateway-list 10.1.20.254
network 10.1.20.0 mask 255.255.255.0
lease day 0 hour 10 minute 0
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif10
ip address 10.1.10.254 255.255.255.0
dhcp select global
#
interface Vlanif13
ip address 10.1.13.3 255.255.255.0
#
interface Vlanif14
ip address 10.1.14.4 255.255.255.0
#
interface Vlanif20
ip address 10.1.20.254 255.255.255.0
dhcp select global
#
interface MEth0/0/1
#
interface Eth-Trunk1
stp root-protection
mode lacp-static
max active-linknumber 3
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 13
#
interface GigabitEthernet0/0/2
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 2 to 4094
stp root-protection
#
interface GigabitEthernet0/0/3
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 2 to 4094
stp root-protection
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
eth-trunk 1
lacp priority 100
#
interface GigabitEthernet0/0/23
eth-trunk 1
lacp priority 100
#
interface GigabitEthernet0/0/24
eth-trunk 1
lacp priority 100
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0/1
ip route-static 10.1.13.1 255.255.255.255 GigabitEthernet0/0/1
ip route-static 100.1.1.0 255.255.255.0 10.1.13.1
ip route-static 100.1.12.0 255.255.255.0 10.1.13.1
#
user-interface con 0
user-interface vty 0 4
#
return
LSW2:
<S2>display current-configuration
#
sysname S2
#
vlan batch 10 13 to 14 20
#
stp mode rstp
stp instance 0 root secondary
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface Eth-Trunk1
stp loop-protection
mode lacp-static
max active-linknumber 3
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 14
#
interface GigabitEthernet0/0/2
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/3
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
eth-trunk 1
#
interface GigabitEthernet0/0/23
eth-trunk 1
#
interface GigabitEthernet0/0/24
eth-trunk 1
#
interface NULL0
#
ip route-static 100.1.1.0 255.255.255.0 10.1.14.1
ip route-static 100.1.12.0 255.255.255.0 10.1.14.1
#
user-interface con 0
user-interface vty 0 4
#
return
LSW3:
[S3]dis current-configuration
#
sysname S3
#
vlan batch 10 20
#
stp mode rstp
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 2 to 4094
#
interface Ethernet0/0/2
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 2 to 4094
#
interface Ethernet0/0/3
port link-type access
port default vlan 10
stp bpdu-filter enable
stp edged-port enable
#
interface Ethernet0/0/4
port link-type access
port default vlan 20
stp bpdu-filter enable
stp edged-port enable
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 Ethernet0/0/1
ip route-static 10.1.1