簡單的ACL流量控制實驗
實驗拓撲:
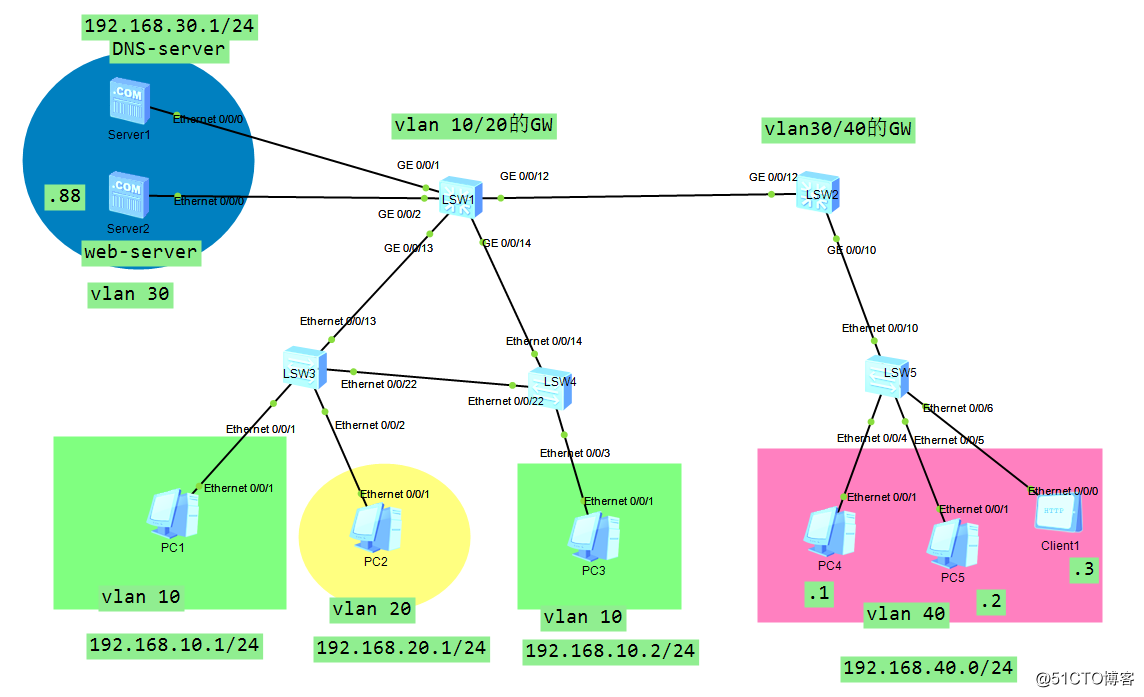
實驗要求:
sw1 是 vlan 10 20 網關
sw2 是 vlan 30 40 的網關
sw1與2 互相使用rip
DNS服務器中配置 www.abc.com(192.168.30.88)
確保每個設備互通,且每個終端可以訪問 www.abc.com(192.168.30.88)
之後:
1、pc-1與pc-2 之間的任何類型的流量都無法互通;
2、pC-3可以ping 192.168.30.88(web-server),但無法 ping www.abc.com
3、pc-4與pc-3之間的任何類型的流量都無法互通;
4、client-1 可以 ping www.abc.com , 但是無法通過自帶的瀏覽器打開 server-2
實驗配置:設備端按圖中的ip地址,網關地址為.254, dns:192.168.30.1
sw1
vlan batch 10 20 30 50
interface g0/0/1
port link-type access
port de vlan 30
interface g0/0/2
port link-type access
port de vlan 30
interface g0/0/12
port link-type trunk
port trunk a vlan 30 50
interface g0/0/13
port link-type trunk
port trunk a vlan 10 20
port link-type trunk
port trunk a vlan 10 20
interface vlan 10
ip add 192.168.10.254 255.255.255.0
interface vlan 20
ip add 192.168.20.254 255.255.255.0
interface vlan 50
ip add 192.168.50.1 255.255.255.0
rip
version 2
network 192.168.10.0
network 192.168.20.0
network 192.168.30.0sw2
vlan batch 30 40 50
interface g0/0/10
port de vlan 40
interface g0/0/12
port link-type trunk
port trunk a vlan 30 50
interface vlan 30
ip add 192.168.30.254 255.255.255.0
interface vlan 40
ip add 192.168.40.254 255.255.255.0
interface vlan 50
ip add 192.168.50.254 255.255.255.0
rip
version 2
network 192.168.40.0
sw3
vlan batch 10 20
interface e0/0/1
port link-type access
port de vlan 10
interface e0/0/2
port link-type access
port de vlan 20
interface e0/0/13
port link-type trunk
port trunk a vlan 10 20
interface e0/0/22
port link-type trunk
port trunk a vlan 10 20
SW4
vlan batch 10 20
interface e0/0/3
port link-type access
port de vlan 10
interface e0/0/14
port link-type trunk
port trunk a vlan 10 20
interface e0/0/22
port link-type trunk
port trunk a vlan 10 20
使所有設備互通,且都能訪問www.ntd1807.com
之後:
1、
sw3 :
acl 3000
rule 5 deny ip source 192.168.10.10.0.0.0 destination 192.168.20.1 0.0.0.0
interface e0/0/2
traffic-filter onbound acl 3000
2、
sw4:
acl 3000
rule 5 deny ip source 192.168.30.1 0.0.0.0 destination 192.168.10.2 0.0.0.0
interface e0/0/3
traffic-filter outbound acl 3000
3、
sw5:
acl 3000
rule 5 deny ip source 192.168.10.2 0.0.0.0 destination 192.168.40.1 0.0.0.0
interface e0/0/4
traffic-filter outbound acl 3000
4、
sw5:
acl 3001
rule 15 deny tcp source 192.168.30.88 0.0.0.0 destination 192.168.40.3 0.0.0.0 destination-port eq 80
traffic-filter outbound acl 3001簡單的ACL流量控制實驗
