Kubernetes - - k8s - v1.12.3 openLDAP統一認證
阿新 • • 發佈:2018-12-17
1,基本概念
- 為了方便管理和整合jenkins,k8s、harbor、jenkins均使用openLDAP統一認證。
2,部署openLDAP
- 根據之前的文件,openLDAP使用GFS進行資料持久化。
- 下載對應的openLDAP檔案
git clone https://github.com/xiaoqshuo/k8s-cluster.git2.1 建立openLDAP
[[email protected] k8s-cluster]# kubectl apply -f openldap/ deployment.extensions/ldap created persistentvolumeclaim/openldap-data created secret/ldap-secret created service/ldap-service created deployment.extensions/phpldapadmin created service/phpldapadmin created
- 此處參考的是:https://github.com/osixia/docker-openldap,更新DN可以更改environment下的yaml檔案,預設的example.org
2.2 建立ldap-ui-ingress
[[email protected] openldap]# kubectl create -f traefik-ldap.yaml ingress.extensions/ldap-ui created [[email protected] openldap]# cat traefik-ldap.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: ldap-ui namespace: public-service annotations: kubernetes.io/ingress.class: traefik spec: rules: - host: ldap.k8s.net http: paths: - backend: serviceName: phpldapadmin servicePort: 8080
3, 檢視驗證
[[email protected] openldap]# kubectl get po,svc,pvc -n public-service | grep ldap pod/ldap-6c9fcc7446-r52r7 1/1 Running 0 4m19s pod/phpldapadmin-6784bf8db-gxqw2 1/1 Running 0 4m16s service/glusterfs-dynamic-openldap-data ClusterIP 10.96.177.154 <none> 1/TCP 3m29s service/ldap-service ClusterIP 10.111.36.109 <none> 389/TCP,636/TCP 4m16s service/phpldapadmin ClusterIP 10.103.142.162 <none> 8080/TCP 4m11s persistentvolumeclaim/openldap-data Bound pvc-252ac771-01da-11e9-b0c8-000c2927a0d0 1Gi RWX gluster-heketi 4m20s
3.1 訪問web
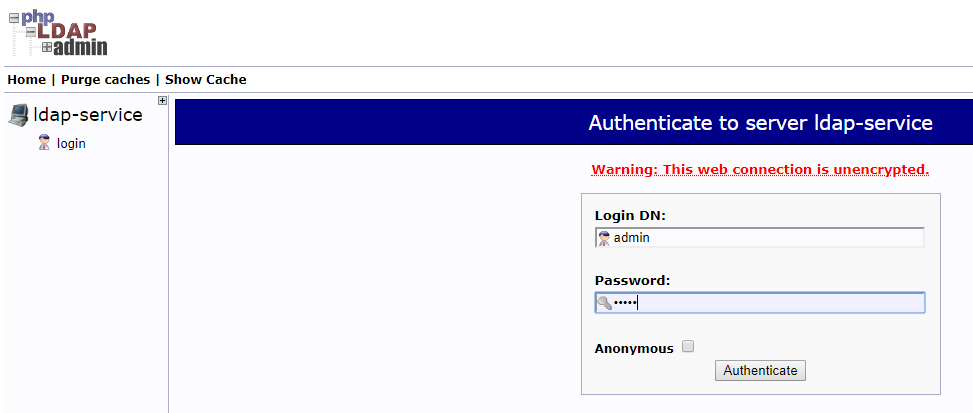
- 訪問phpldapadmin:ldap.k8s.net
預設DN:cn=admin,dc=example,dc=org,預設Password:admin(線上系統需自定義修改)
登入