Five ways to identify phishing emails
As phishing emails come in different shapes and formats, there is no silver bullet to identify a phishing email. However, there is a collection of red flags you should be looking for before clicking on a new message. Here is our up-to-date guide helping you identify the latest email-based scams.
What is phishing? Phishing is a cyber-attack typically carried out over email. In a nutshell, cybercriminals aim to trick their victims to click a link or attachment, to give their password away or to ask them for money by pretending to be a legitimate online service, client, friend or colleague.
Strong indicators that an email might be deceptive
Although other clues are also available, the following ones help you decide whether an email is genuine or not:
- The sender’s display name and/or email address is spoofed
- The IP address of the sending SMTP server does not belong to the sender’s organisation
- The clickable web links does not take to a trusted domain
- The email features an unsolicited file attachment
#1. Sender name and/or email address spoofing
There are two common sender spoofing methods cybercriminals may use. For illustrative purposes, let us say the person we wish to impersonate is Peter File
[email protected]:- Email Address Spoofing: Peter’s email address and his name are both spoofed on an incoming email so that the sender appears to be:
Peter File <[email protected]>. - Display Name Spoofing: Only Peter’s name is spoofed, but not the email address:
Peter File <[email protected]>.
To verify the sender of an email, you simply need to observe the sender’s name and email address in your email client. Both the sender’s name and the email address should be displayed by default. On the other hand, smartphones may not display the sender’s email address. In this case, you can reveal the underlying web link by tap-holding on the sender’s name.
#2. Sender Framework Policy (SPF) violations
If the sender’s domain name specifies the allowed SMTP hosts in an SPF record and the receiving email server supports SPF lookups, your email server will flag emails violating the SPF policy. Typically, these emails are either rejected or moved automatically into your spam folder.
The adoption rate of SPF records is around 50% according to a 2016 report. However, poorly configured email hosting providers may keep these emails in your Inbox folder.

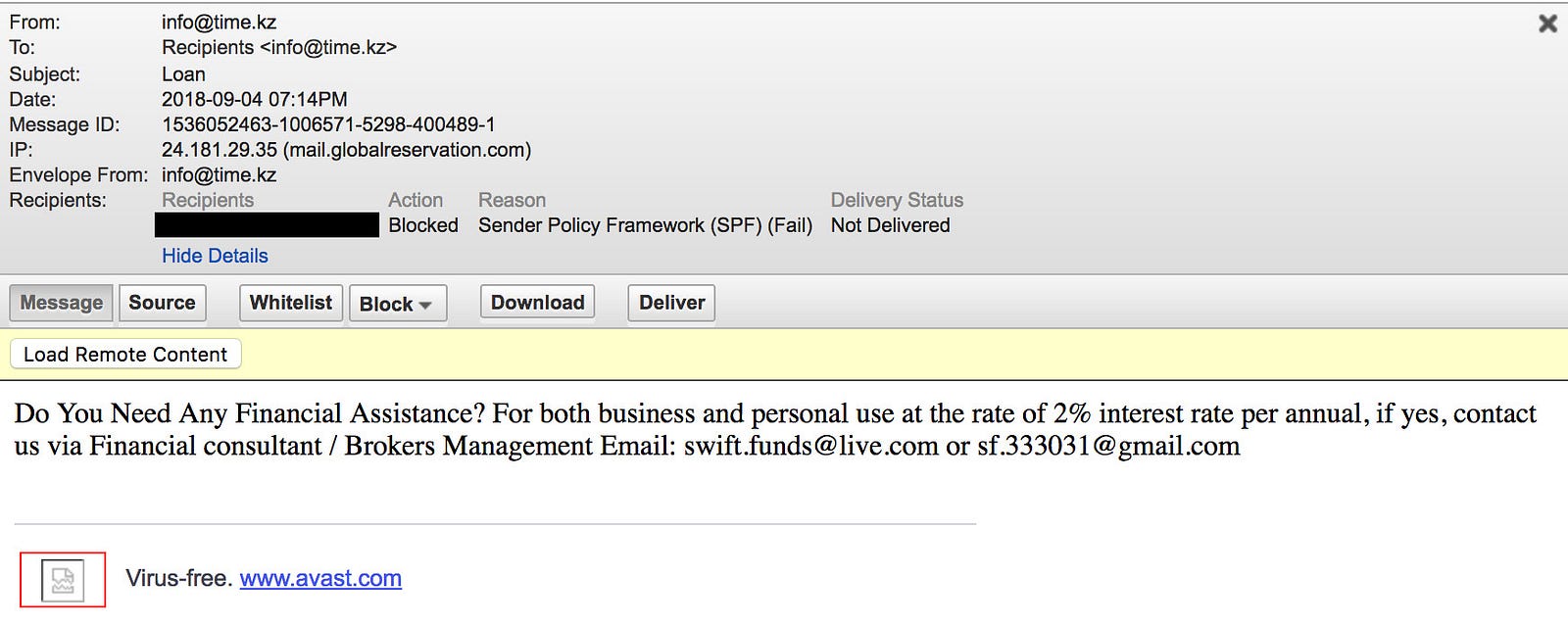
To find out whether a suspicious email has violated the SPF policy, view the message headers and look for the Received-SPF header. If the status is ‘fail’, the email might be a phishing attempt.
#3. The sending IP address does not belong to the sending organisation
Another indicator of a phishing email is the sending IP address (or hostname) of the sending SMTP email server.
If the email is sent from [email protected], it is safe to assume that the sending SMTP server is closely associated with the sending organisation (e.g. smtp01.brasseye.com), or a reputable email hosting providers such as Office 365 or G Suite. In case the email is sent from IP addresses or hostnames associated with unrelated countries and organisations, the email might be not genuine.
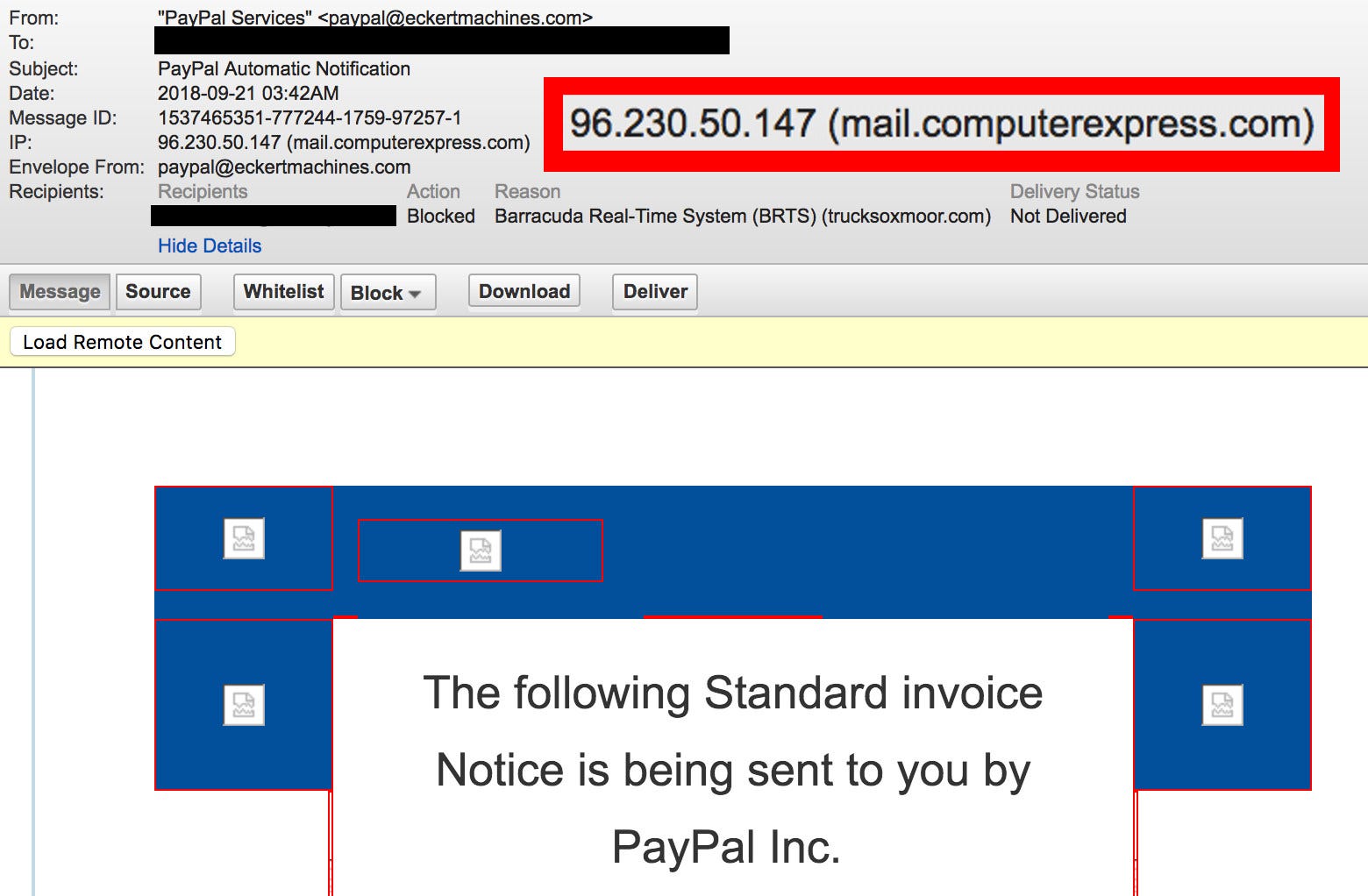
You can look up the sending SMTP server’s IP address and hostname with the combination of MX Toolbox Email Header Analyzer and a service such as ipinfo.io.
#4. Clickable links lead to unknown or unrelated domains
The embedded web links may lead to deceptive websites hosting fake login pages or web browser exploits. It is crucial to inspect the web link before clicking by either hovering over them (on a desktop computer), or tap-holding on them with a smartphone.
If the email is seemingly coming from a trusted provider like PayPal, the web link should be pointing to a domain name associated with the domain.
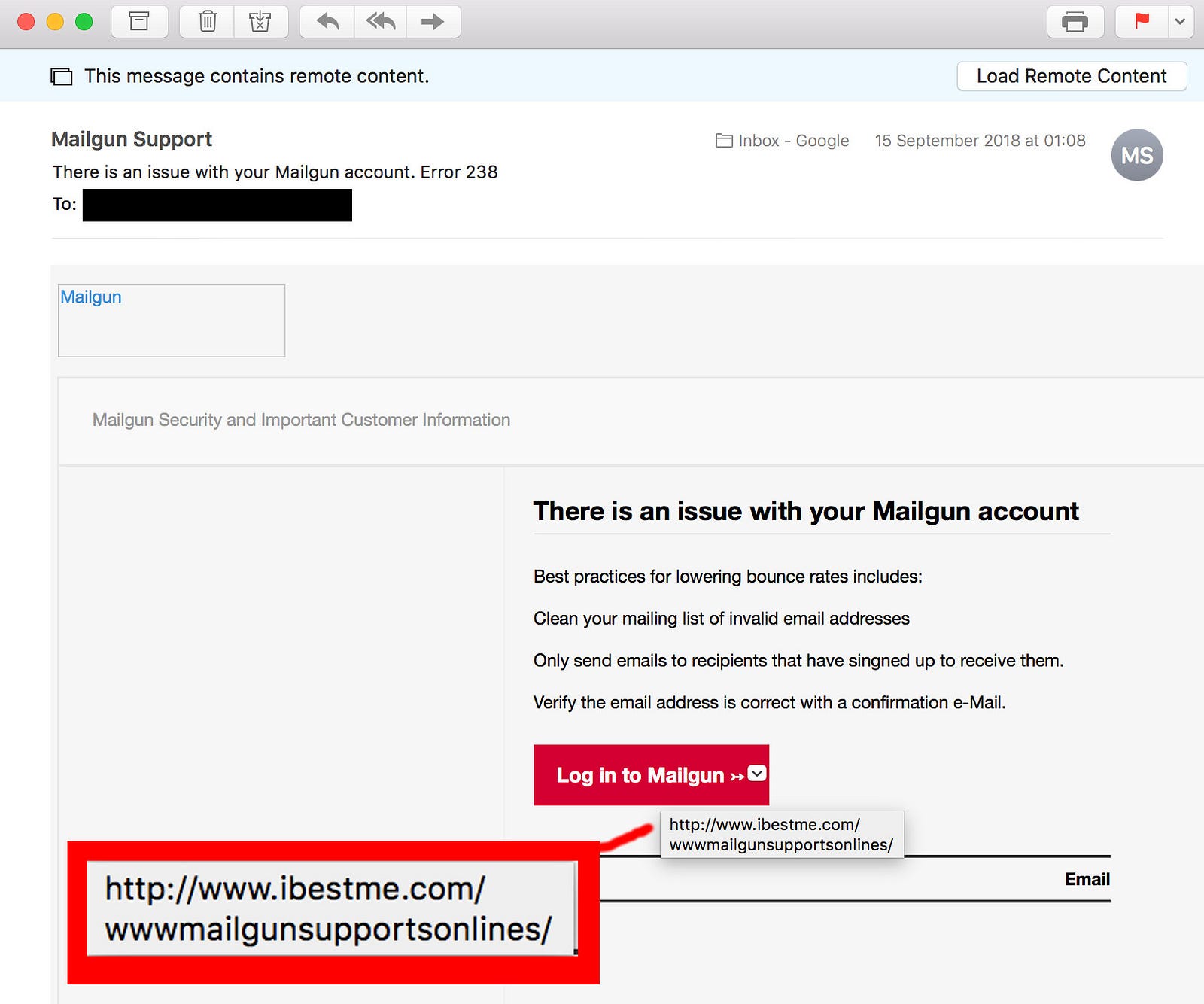
Sadly, big companies tend to register confusing domain variants of their brands. For example, [email protected][.]com is a legitimate email address belonging to the PayPal Merchant Tech Support team. Other domains like paypal-knowledge[.]com and paypal-community[.]com are also legitimate domains also used by PayPal.
#5. File attachments
Treat every email suspicious that comes with unexpected file attachments. Malicious file attachments can be disgused as resumes or tax invoices in Word or PDF formats.
If you receive an email with a file attachment you did not expect, you should either confirm with the sender on an out of band channel (like a phone call) that the file attachment is genuine or open it in a sandbox environment like a virtual machine.
The online PDF and Word document viewers embedded in Gmail can also neutralise any harmful content as these viewers are not supporting frequently-abused active content like JavaScript and Office macros.
Weak indicators that an email might be a phishing attempt
These tips are circulating on the internet, but sadly, these tips are likely to be ineffective as the level of sophistication of cybercriminals has grown over time:
- Poorly written emails — Cybercriminals can rely on proofreading services such as Fiverr to get the grammar right, or in what has become a common practice in phishing, attackers will simply clone common email notifications of well-known brands and businesses.
- Non-personalised greetings — ‘Dear Sir’ instead of ‘Dear Peter’. Even legitimate newsletters often do not get the greeting right.
- Sense of urgency and far-reaching consequences if a specific action is not taken — For example, we get locked out from an account if we are not logging in the next 24 hours.
In summary, treat every email with a suspicion that comes with a web link, file attachment or a request to take action. If you are still in doubt, reach out to your friends or colleagues for a second opinion, or leave the email unanswered.
About Iron Bastion
Iron Bastion is Australia’s phishing and cybersecurity experts. We provide cybersecurity consulting with specialised solutions to combat phishing. Our team are qualified cybersecurity professionals, and all our staff and operations are based in Australia.
Contact us for a free cybersecurity consultation or sign up to our managed services today.
