How to intercept TOR hidden service requests with Burp
阿新 • • 發佈:2018-12-29
How to intercept TOR hidden service requests with Burp
My environment for this setup: MacOS, Burp Suite, Tor service, Firefox browser and brew.
- Install tor service(not the TorBrowser bundle). On Mac you can do it with “brew install tor”. If you don’t have brew installed run this command:
Here is the link in you need more information on brew: https://brew.sh/
- Run tor service with the following command:
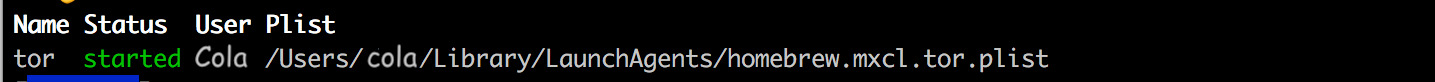
brew service start tor. If you dobrew service listyou should see tor running:
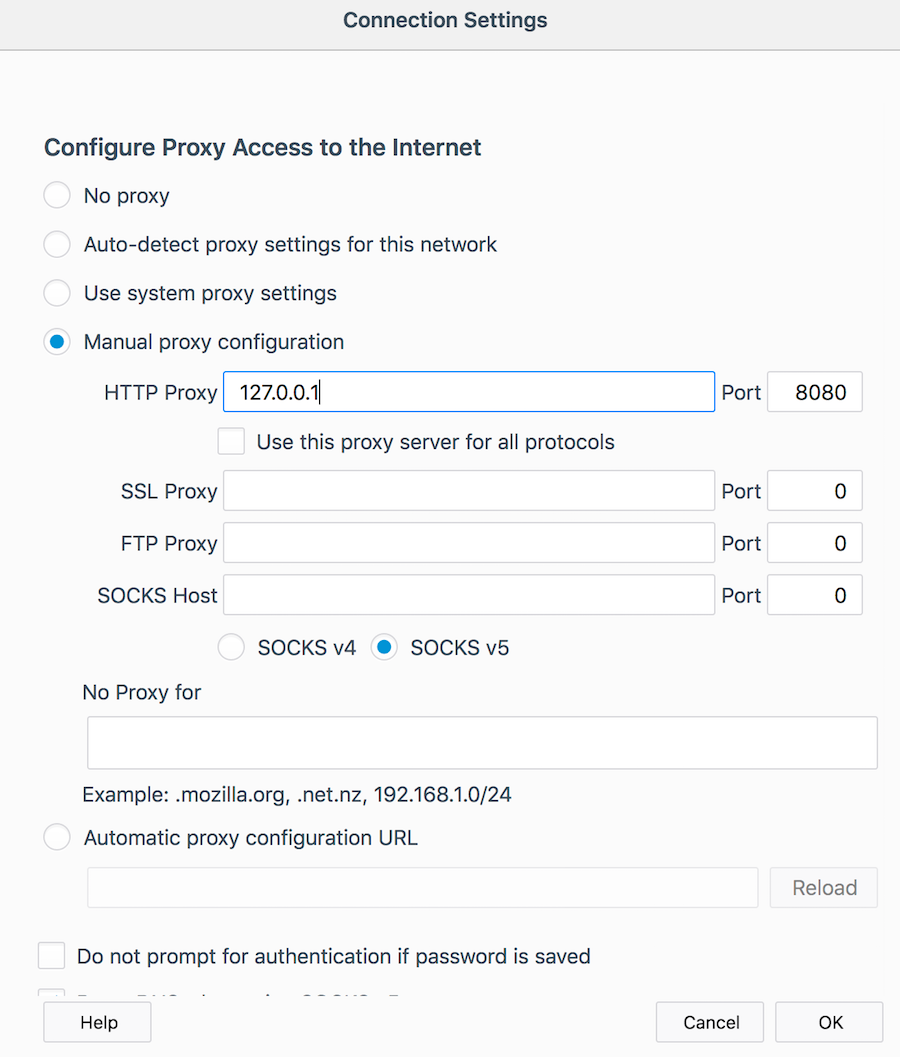
Configure Firefox:
- Set manual proxy configuration to 127.0.0.1 port 8080
- Make sure SOCKS is set to v5. V4 is not supported.

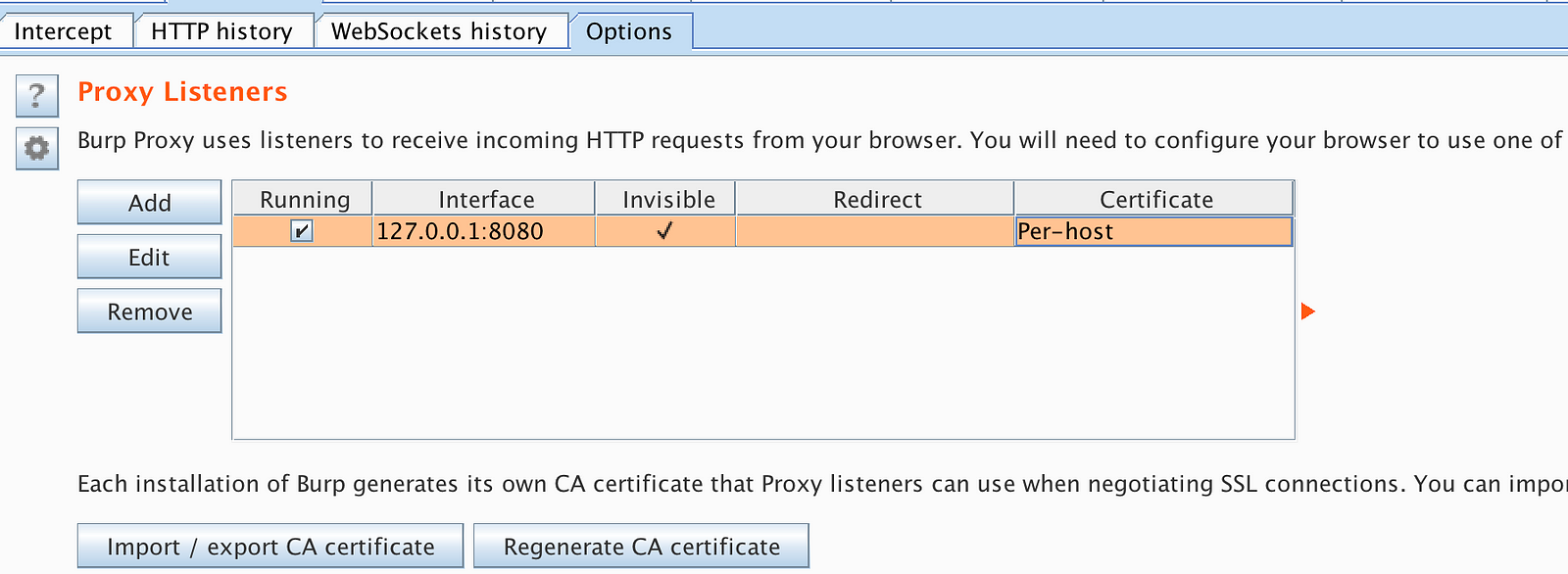
Configure Burp:
- In the Proxy option make sure it’s also running on 127.0.0.1 port 8080. It should be already set by default

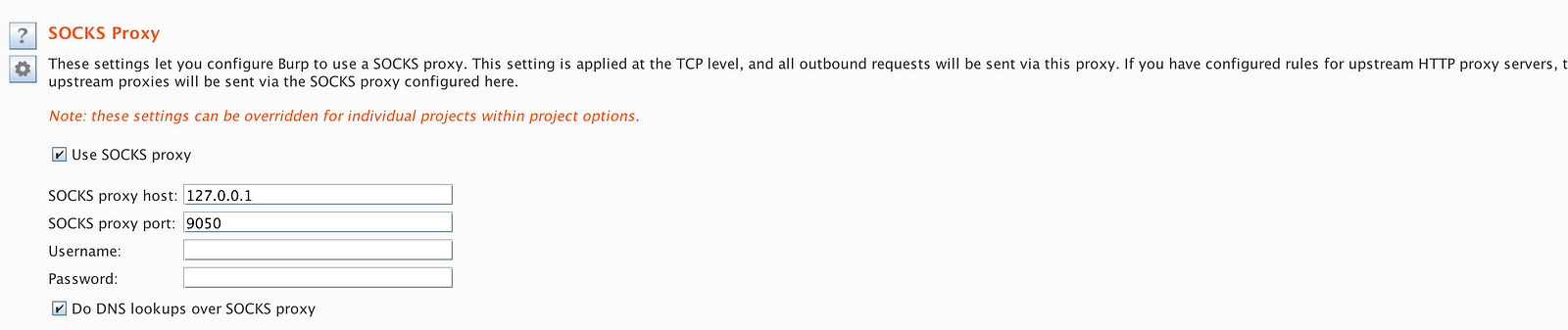
- Under User Option tag → Connections set SOCKS Proxy. Host — 127.0.0.1, port 9050 (or whatever port your tor service is running on. It could also be 9150).

Your nmap output for localhost should look like this:


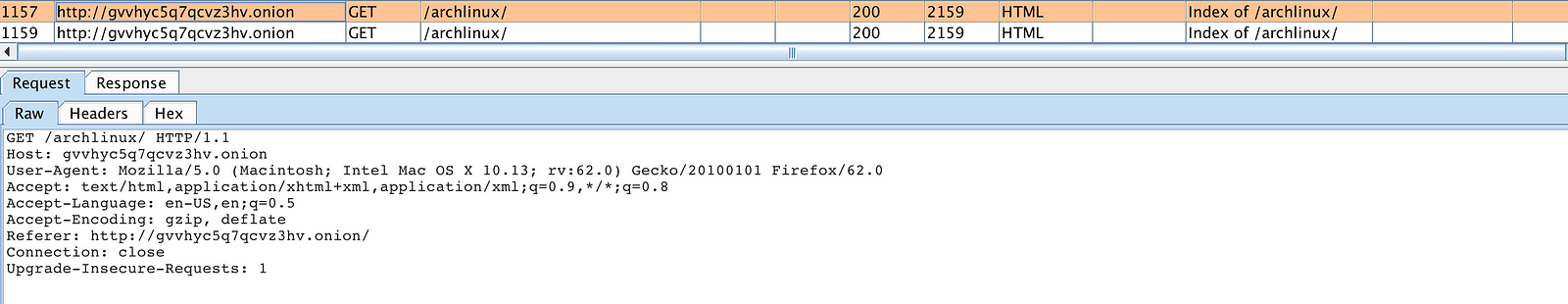
Great! Now you can intercept and modify onion traffic. In Burp Pro you can also set up Collaborator Everywhere and whenever an onion service is not configured properly it will ping back the Burp server revealing its original IP.
Happy hacking!