Blockchain Revolution: Part Three
Blockchain Revolution: Part Three
All about consensus algorithms


Here’s the third post of the series ‘Blockchain Revolution’ where we will break down consensus protocol to help you understand the concept better. And in case you have missed the previous posts, here are the links to first and second articles.
Getting back to the topic, let’s start by understanding what is consensus. It means general agreement on a single value among participating parties. Achieving consensus implies that everyone accepts and supports a decision. That is why the name consensus algorithms in blockchain. It is used to achieve agreement on single data value among distributed systems.
The need for consensus algorithms
All transactions which occur on a blockchain are grouped into blocks. The nodes agree to add a block to a blockchain only when all the transactions within the block are valid. Being a decentralized network, there is no central authority that validates these transactions. So, all the nodes must collaborate and validate the transactions.
Let’s assume there is a fraudulent node that tries to spend coins twice — which is called double spend. For instance, it buys an item online and uses same coins for an exchange, this way they could have both the items as well as the money. To prevent this, the nodes need to verify and agree upon the validity of the transactions. Consensus algorithms help establish the agreement between the nodes.
The list of consensus algorithms
There are four types of consensus algorithms that we will elaborate and highlight their pros and cons.
1. Proof-of-Work (PoW)
In PoW algorithm, the nodes on blockchain network have to validate transactions on a block before adding it. The nodes that validate blocks are called minersand are required to solve mathematical puzzle. All the miners on a network compete with each other to solve the puzzle and add it to the blockchain. Whichever node solves the puzzle first, that miner’s block is added to the blockchain and miners earn rewards (as represented in image 1). In Bitcoin blockchain, reward is bitcoins. The whole process is called mining. Mining requires huge computation power and energy. Some of the common examples include Bitcoin blockchain, Ethereum and Litecoin.

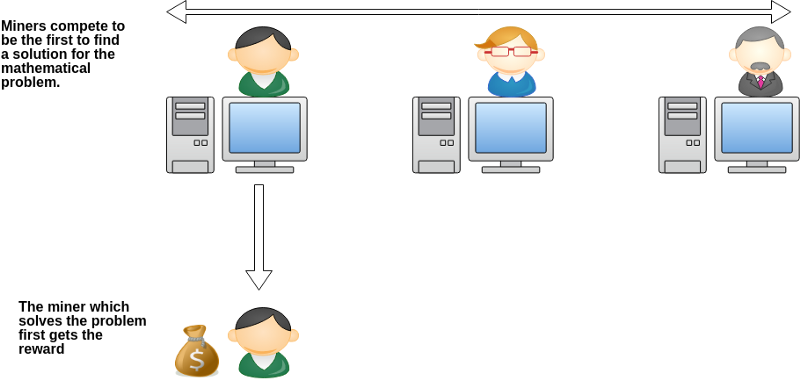
Pros: First blockchain technology to be developed.
Cons: The throughput is slow. In case of Bitcoin blockchain, it takes about 10 minutes to generate a new block, a significant amount of time compared to block generation time of other blockchains. It is not energy efficient as it consumes a lot of energy to mine.
It is also prone to 51% attacks — which means, an attack by a group of miners controlling more than 50% of the network’s mining hash rate or computing power. The attackers could prevent transactions from being validated, allowing them to stall transactions on the network.
2. Proof-of-Stake (PoS)
PoS is different from PoW, in that there are no miners in PoS and therefore no mining. PoS follows a process of validating blocks and adding the validated blocks to a blockchain.
In PoS protocol, nodes are called ‘validators’ instead of miners and the process of mining is replaced by ‘forging’ or ‘minting’. A node has to deposit certain amount of their coins as stake to the network in-order to become a validator. Think of it as, putting your coins in an account.
The PoS uses an election process to choose a random node which will validate the next block. If a node is chosen to validate the next block, it has to check whether all the transactions within the block are valid or not. The validator now places a bet on the block that he thinks is valid. If the block is valid, it gets added to the blockchain and the validator node receives the transaction fees as reward. If the validator tries committing a fraud and places a bet on an invalid block, the validator loses a certain amount of the stake and is barred from taking part in any validations in future. Examples of PoS are PeerCoin, Nxt, Decred, while Ethereum blockchain is working on shifting from PoW to PoS.
Pros: Less power consumption and higher throughput compared to PoW
Cons: Unlike PoW in PoS an attacker could stake 51% of the coins on the network.
3. Delegated Proof-of-Stake (DPoS)
DPoS is a more efficient form of PoS. DPoS uses voting mechanism to achieve consensus. In DPoS, the community members (or token holders) don’t vote on the validity of the blocks themselves. Instead, they vote to elect super representative (or Delegate Nodes) to validate on their behalf (as represented in image 2). It is then the super representative’s responsibility to secure the network and validate blocks and they are paid to validate transactions on the block. The voting in DPoS is a continuous process. There are generally 21–100 super representatives in DPoS system. And the representatives are shuffled periodically. So, if the super representative doesn’t perform well and validate the blocks correctly, members of the community can remove their votes and fire bad representatives and elect a new super representative. Some examples of blockchain on DPoS are EOS, Tron Protocol, Steem, Lisk.

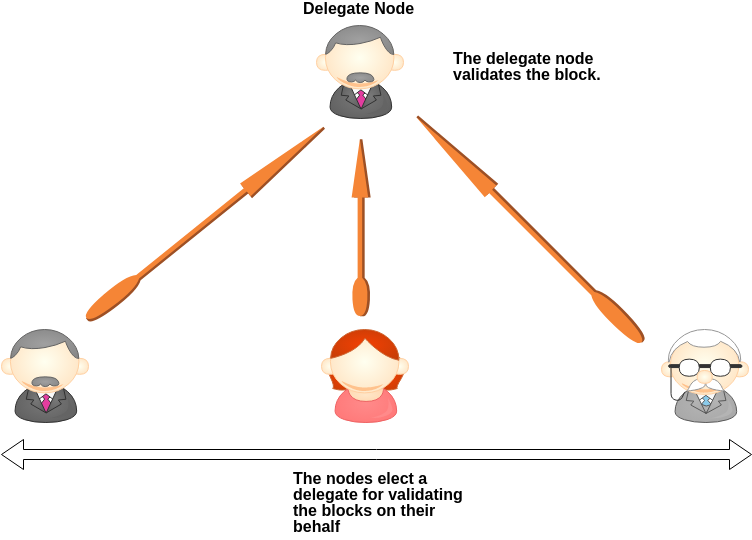
Pros: Energy efficient, cost-effective transactions, higher throughput compared to PoS and scalable.
Cons: An attacker could stake 51% of the coins on the network. This network is also partially centralized.
4. Byzantine Fault Tolerance (BFT) Protocols
A system is said to be byzantine fault tolerant (BFT) when it can continue to operate even if certain participants drop out. In blockchain terms, BFT means the nodes on the network are able to reach consensus even if some of the nodes drop out or there are fraudulent nodes on the network. BFT protocol algorithms follow what we generally see in voting system. Similar to a situation where citizens of a country vote and select delegates who work for the welfare of the citizens. Now one of these delegates is selected randomly as a speaker. Let’s say the speaker promises to execute a lot of things. The delegates validate if the speaker was true to his/her words and delivered on the promise. Minimum 66% of the delegates need to approve. In case the speaker fails, a new delegate is elected.
Now let’s understand this in terms of blockchain. The nodes are the citizens and all the nodes vote to elect a delegate whose job is to validate the block. One of the delegates is selected asspeaker. The speaker validates the block and its transactions. The validated block is re-verified by the delegates to check if what the speaker validated was correct or not. Let’s assume a fraudulent speaker validated a block which is then sent to three delegates. Now two out of the three delegates found out that it was an invalid block and disapproves, while the third one approves it. It doesn’t go through. Since there is a conflict and consensus has not been reached, the fraudulent speaker is removed and new speaker is elected (as represented in image 3).
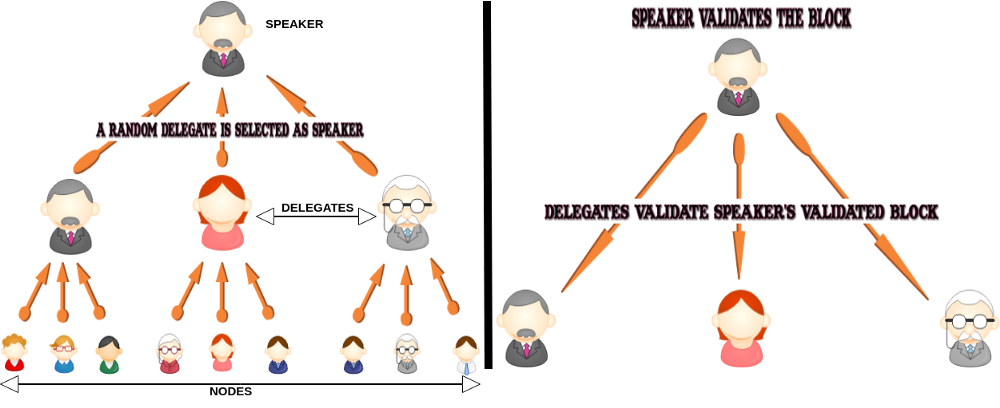
BFT consists many algorithms, these are some of the commonly used.
a) Practical Byzantine Fault Tolerance (PBFT)
In PBFT, the speaker is chosen from a pre-selected number of delegates. Blockchain project using this algorithm is Hyperledger.
b) Federated Byzantine Fault Tolerance (FBFT)
FBFT is a modification of PBFT in which there are no pre-selected delegates. FBFT tries to solve the byzantine fault tolerance problem by creating smaller groups of trusted nodes which in-turn select other trusted nodes and try to reach consensus between their own trusted group. These trusted groups combine to form a cluster which validates transactions on the blocks. Ripple and Stellar are two blockchain projects using this algorithm.
Pros: Higher throughput and scalable.
Cons: Partially centralized.
The above mentioned four consensus algorithms are the most commonly used. There are other consensus algorithms like Proof-of-Burn (PoB) and Proof-of-Authority (PoA). Next up in the series, is the sample blockchain project that uses Proof-of-Work algorithm.
