AWS Config Rules – Dynamic Compliance Checking for Cloud Resources
The flexible, dynamic nature of the AWS cloud gives developers and admins the flexibility to launch, configure, use, and terminate processing, storage, networking, and other resources as needed. In any fast-paced agile environment, security guidelines and policies can be overlooked in the race to get a new product to market before the competition.
Imagine that you had the ability to verify that existing and newly launched AWS resources conformed to your organization’s security guidelines and best practices without creating a bureaucracy or spending your time manually inspecting cloud resources.
Last year I announced that you could
New AWS Config Rules
Today we are extending Config with a powerful new rule system. You can use existing rules from AWS and from partners, and you can also define your own custom rules. Rules can be targeted at specific resources (by id), specific types of resources, or at resources tagged in a particular way. Rules are run when those resources are created or changed, and can also be evaluated on a periodic basis (hourly, daily, and so forth).
Rules can look for any desirable or undesirable condition. For example, you could:
- Ensure that EC2 instances launched in a particular VPC are properly tagged.
- Make sure that every instance is associated with at least one security group.
- Check to make sure that port 22 is not open in any production security group.
Each custom rule is simply an AWS Lambda function. When the function is invoked in order to evaluate a resource, it is provided with the resource’s Configuration Item. The function can inspect the item and can also make calls to other AWS API functions as desired (based on permissions granted via an IAM role, as usual). After the Lambda function makes its decision (compliant or not) it calls the PutEvaluations function to record the decision and returns.
The results of all of these rule invocations (which you can think of as compliance checks) are recorded and tracked on a per-resource basis and then made available to you in the AWS Management Console. You can also access the results in a report-oriented form, or via the Config API.
Let’s take a quick tour of AWS Config Rules, with the proviso that some of what I share with you will undoubtedly change as we progress toward general availability. As usual, we will look forward to your feedback and will use it to shape and prioritize our roadmap.
Using an Existing Rule
Let’s start by using one of the rules that’s included with Config. I open the Config Console and click on Add Rule:
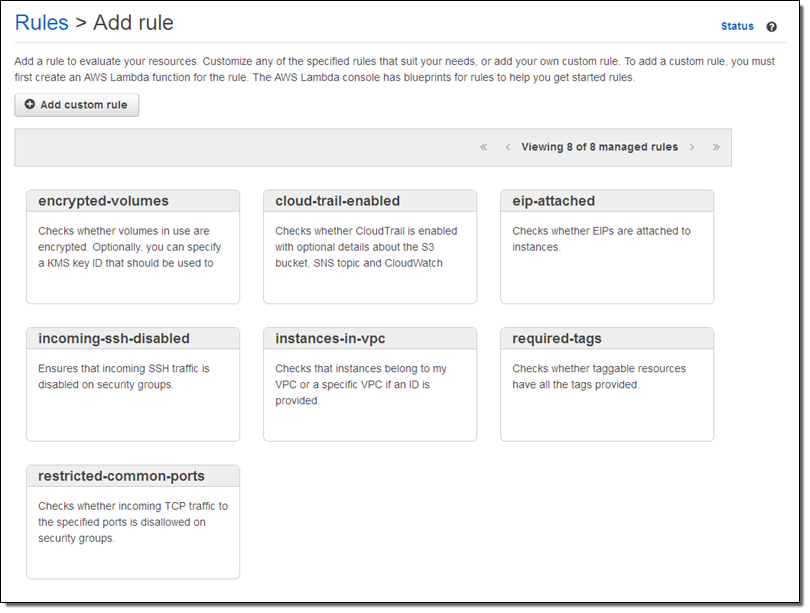
I browse through the rules and decide to start with instances-in-vpc. This rule verifies that an EC2 instance belong to a VPC, with the option to check that it belongs to a specific VPC. I click on the rule and customize it as needed:
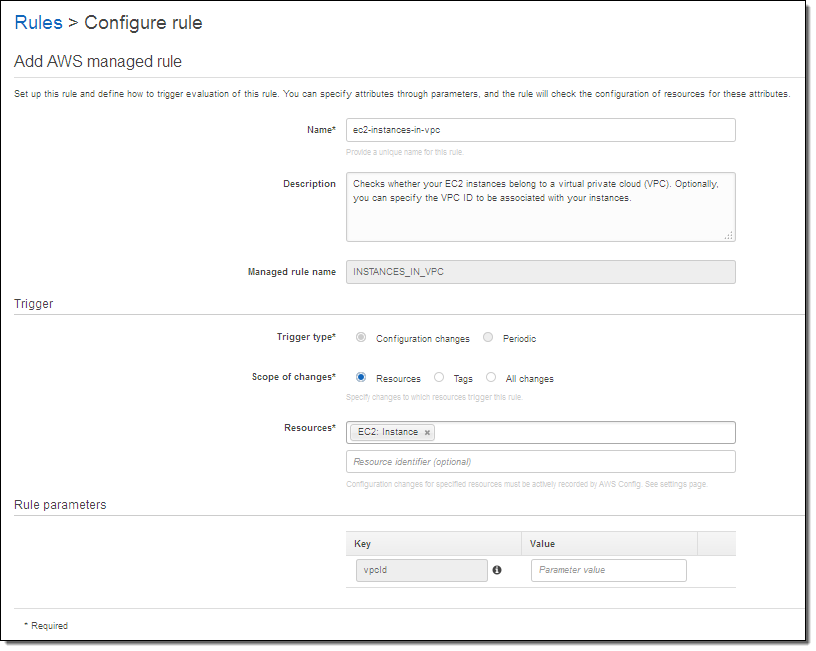
I have a lot of choices here. The Trigger type tells Config to run the rule when the resource is changed, or periodically. The Scope of changes tells Config which resources are of interest. The scope can be specified by resource type (with an optional identifier) by tag name, or by a combination of tag name and value. If I am checking EC2 instances, I can trigger on any of the following:
- All EC2 instances.
- Specific EC2 instances, identified by a resource identifier.
- All resources tagged with the key “Department.”
- All resources tagged with the key “Stage” and the value “Prod.”
The Rule parameters allows me to pass additional key/value pairs to the Lambda function. The parameter names, and their meaning, will be specific to the function. In this case, supplying a value for the vpcid parameter tells the function to verify that the EC2 instance is running within the specified VPC.
The rule goes in to effect after I click on Save. When I return to the Rules page I can see that my AWS configuration is now noncompliant:
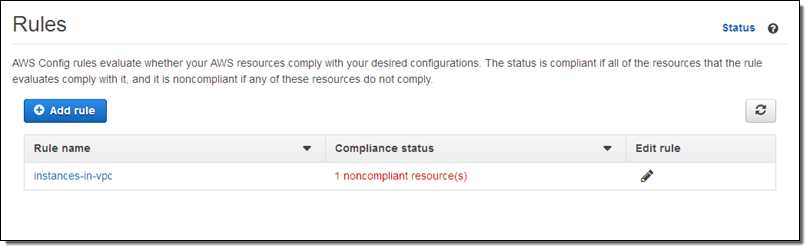
I can investigate the issue by examining the Config timeline for the instance in question:
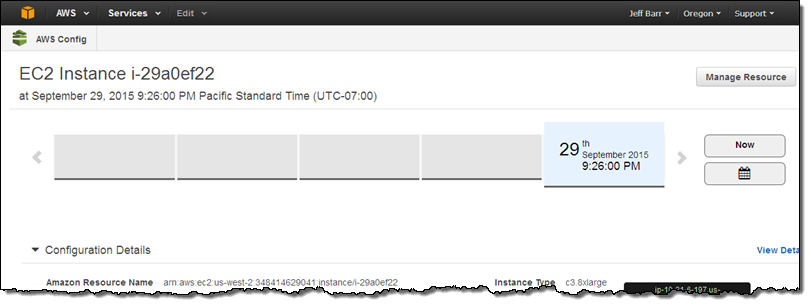
It turns out that this instance has been sitting around for a while (truth be told I forgot about it). This is a perfect example of how useful the new Config Rules can be!
I can also use the Config Console to look at the compliance status of all instances of a particular type:
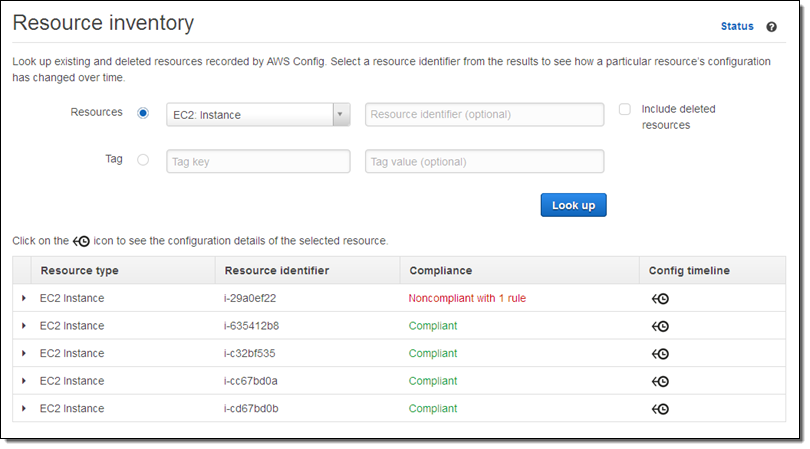
Creating a New Rule
I can create a new rule using any language supported by Lambda. The rule receives the Configuration Item and the rule parameters that I mentioned above, and can implement any desired logic.
Let’s look at a couple of excerpts from a sample rule. The rule applies to EC2 instances, so it checks to see if was invoked on one:
function evaluateCompliance(configurationItem, ruleParameters) {
if (configurationItem.resourceType !== 'AWS::EC2::Instance') {
return 'NOT_APPLICABLE';
} else {
var securityGroups = configurationItem.configuration.securityGroups;
var expectedSecurityGroupId = ruleParameters.securityGroupId;
if (hasExpectedSecurityGroup(expectedSecurityGroupId, securityGroups)) {
return 'COMPLIANT';
} else {
return 'NON_COMPLIANT';
}
}
}If the rule was invoked on an EC2 instance, it checks to see if any one of a list of expected security groups is attached to the instance:
function hasExpectedSecurityGroup(expectedSecurityGroupId, securityGroups) {
for (var i = 0; i < securityGroups.length; i++) {
var securityGroup = securityGroups[i];
if (securityGroup.groupId === expectedSecurityGroupId) {
return true;
}
}
return false;
}Finally, the rule stores the result of the compliance check by calling the Config API’s putEvaluations function:
config.putEvaluations(putEvaluationsRequest, function (err, data) {
if (err) {
context.fail(err);
} else {
context.succeed(data);
}
});
The rule can record results for the item being checked or for any related item. Let’s say you are checking to make sure that an Elastic Load Balancer is attached only to a specific kind of EC2 instance. You could decide to report compliance (or noncompliance) for the ELB or for the instance, depending on what makes the most sense for your organization and your compliance model. You can do this for any resource type that is supported by Config.
Here’s how I create a rule that references my Lambda function:
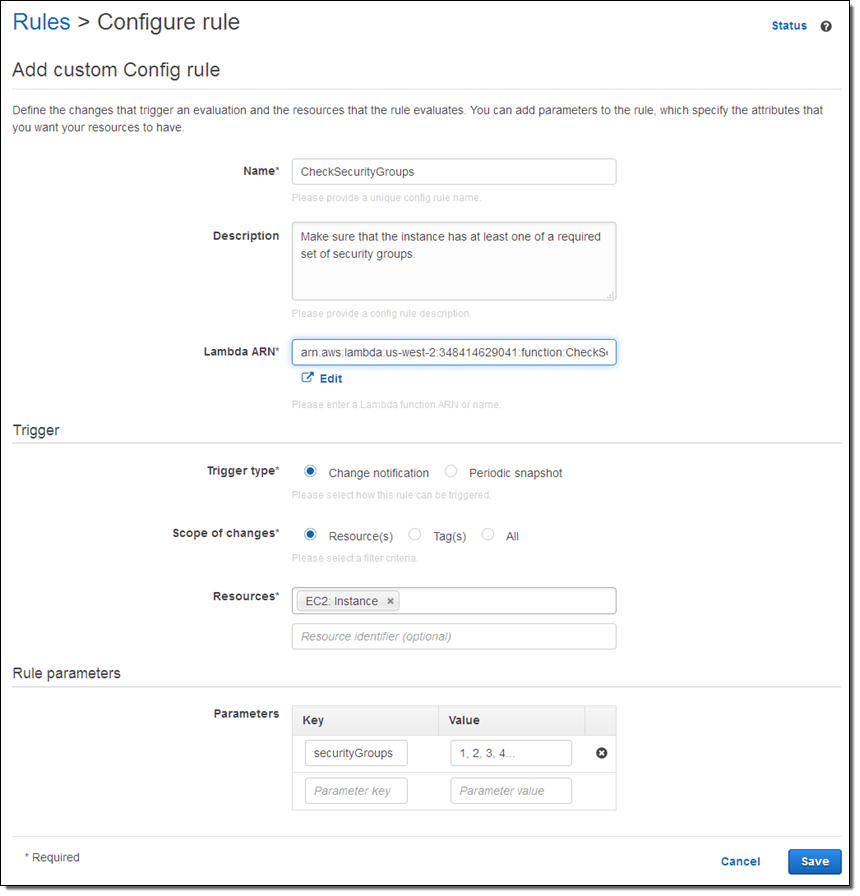
On the Way
AWS Config Rules are being launched in preview form today and you can sign up now. Stay tuned for additional information!
— Jeff;
相關推薦
AWS Config Rules – Dynamic Compliance Checking for Cloud Resources
The flexible, dynamic nature of the AWS cloud gives developers and admins the flexibility to launch, configure, use, and terminate processing, sto
AWS Marketplace: Tibero 5 Enterprise Edition for Cloud
Amazon EC2 running Red Hat Enterprise Linux provides a dependable
Dynamic iTerm profiles for AWS autoscaling groups
Autoscaling groups. Ahhh…they are so AWS-ome!. But as I grew fond of being able to access my servers easily and fast using iTerm profiles with my old VDC,
AWS Amplify Announces Vue.js Support for Building Cloud
Vue.js is a popular open source JavaScript framework which enables building user interfaces with Web technologies. AWS Amplify provides Vue.js
AWS Compliance Center for financial services now available
On Tuesday, September 4, AWS announced the launch of an AWS Compliance Center for our Financial Services (FS) customers. This addition to our comp
AWS Marketplace: OnCommand Cloud Manager (for Cloud Volumes ONTAP, formerly ONTAP Cloud)
Product Overview Start Your Free Trial of Cloud Volumes ONTAP Here! NetApp OnC
AWS Marketplace: Symantec Protection Engine for Cloud Services on Linux
Symantec Protection Engine for Cloud Services 8.0 is a flexible and feature-rich client/server application that allows customers to incorporate ma
AWS Config Update – New Managed Rules to Secure S3 Buckets
AWS Config captures the state of your AWS resources and the relationships between them. Among other features, it allows you to select a resource a
解決安裝Apache中出現checking for APR... no configure: error: APR not found. Please read the documentation的問題
cef ... clas apr-util 完成 usr 安裝apache make pre Linux中安裝Apache 編譯出現問題: 解決辦法: 1、下載所需要的軟件包 wget http://archive.apache.org/dist/apr/apr-1.4.
《Dynamic Mode Decomposition for Real-Time Background/Foreground Separation in Video》讀書筆記
題目:Dynamic Mode Decomposition for Real-Time Background/Foreground Separation in Video 作者:J.Grosek and J.Nathan Kutz 連結:https://pdfs.semanticschola
《Randomized Low-Rank Dynamic Mode Decomposition for Motion Detection》讀書筆記(下)
謝絕任何不標註出處的轉載 如有問題請聯絡作者 原文連結:https://arxiv.org/abs/1512.03526 上文說了dmd的大概構建過程,這裡複習DMD在背景提取上的應用。RPCA中對於背景提取已經有了成果,對於一個視訊矩陣A,我們可以將其拆分成L和S兩個矩陣。其中L是一個低
《Randomized Low-Rank Dynamic Mode Decomposition for Motion Detection》讀書筆記(中)
謝絕任何不標註出處的轉載 如有問題請聯絡作者 原文連結:https://arxiv.org/abs/1512.03526 上一篇讀書筆記大致介紹了svd和rsvd,這一篇來學習一下dmd和rdmd。 DMD是一個合併了PCA和時間序列(傅立葉模式)的資料驅動型方法。 DMD起源於流體力學,
《Randomized Low-Rank Dynamic Mode Decomposition for Motion Detection》讀書筆記(上)
謝絕任何不標註出處的轉載 如有問題請聯絡作者 原文連結:https://arxiv.org/abs/1512.03526 這篇文章介紹了一種使用隨機動態模式分解(Randomized Dynamic Mode Decomposition, rDMD)來進行矩陣低秩計算的快速演算法。動態模式
yum安裝錯誤:CRITICAL:yum.cli:Config Error: Error accessing file for config file:///home/linux/+
出現原因:yum可能沒有,或者損壞 解決: 第一步:下載 wget http://yum.baseurl.org/download/3.2/yum-3.2.28.tar.gz 第二步:下載完成之後解壓 tar -zxvf
安裝PostGIS 2.1.1 時遇到checking for library containing GDALAllRegister... no
在postgis中執行./configure時,遇到 checking for library containing GDALAllRegister... no 的錯誤資訊[[email protected] postgis-2.1.1]# ./configure.........checking
Android Studio啟動後一直 Checking for updated SDK components
Android Studio 安裝後啟動後一直停止在 Checking for updated SDK components。 選擇取消後,再啟動 Android Studio 還是一樣的問題。 原因是安裝完成後,啟動過程需要檢測SDK路徑和最新版本,因為 Google 被牆
論文解讀:A Focused Dynamic Attention Model for Visual Question Answering
這是關於VQA問題的第四篇系列文章。本篇文章將介紹論文:主要思想;模型方法;主要貢獻。有興趣可以檢視原文:A Focused Dynamic Attention Model for Visual Question Answering。 1,主要思想: Focused Dynami
【目標跟蹤】MemTrack:Learning Dynamic Memory Networks for Object Tracking
ECCV2018一篇用LSTM做tracking的文章,文章連結:MemTrack Motivation: 作者主要是想解決基於模板匹配類演算法對目標形變的適應性問題。 典型的模板匹配演算法比如Sia
A dynamic balanced flow for filtering point-sampled geometry
Abstract Introduction Related work Well-posed anisotropic flow Covariance analysis Curvature flow Well-posed an
Checking for a null int value from a Java ResultSet
好神奇的 check 方式。 The default for ResultSet.getInt when the field value is NULL is to return 0, which is also the default value for your iVal declaration. In
